PHP Servers and IoT Devices Face Growing Cyber-Attack Risks – Infosecurity Magazine
Published on: 2025-10-29
Intelligence Report: PHP Servers and IoT Devices Face Growing Cyber-Attack Risks – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
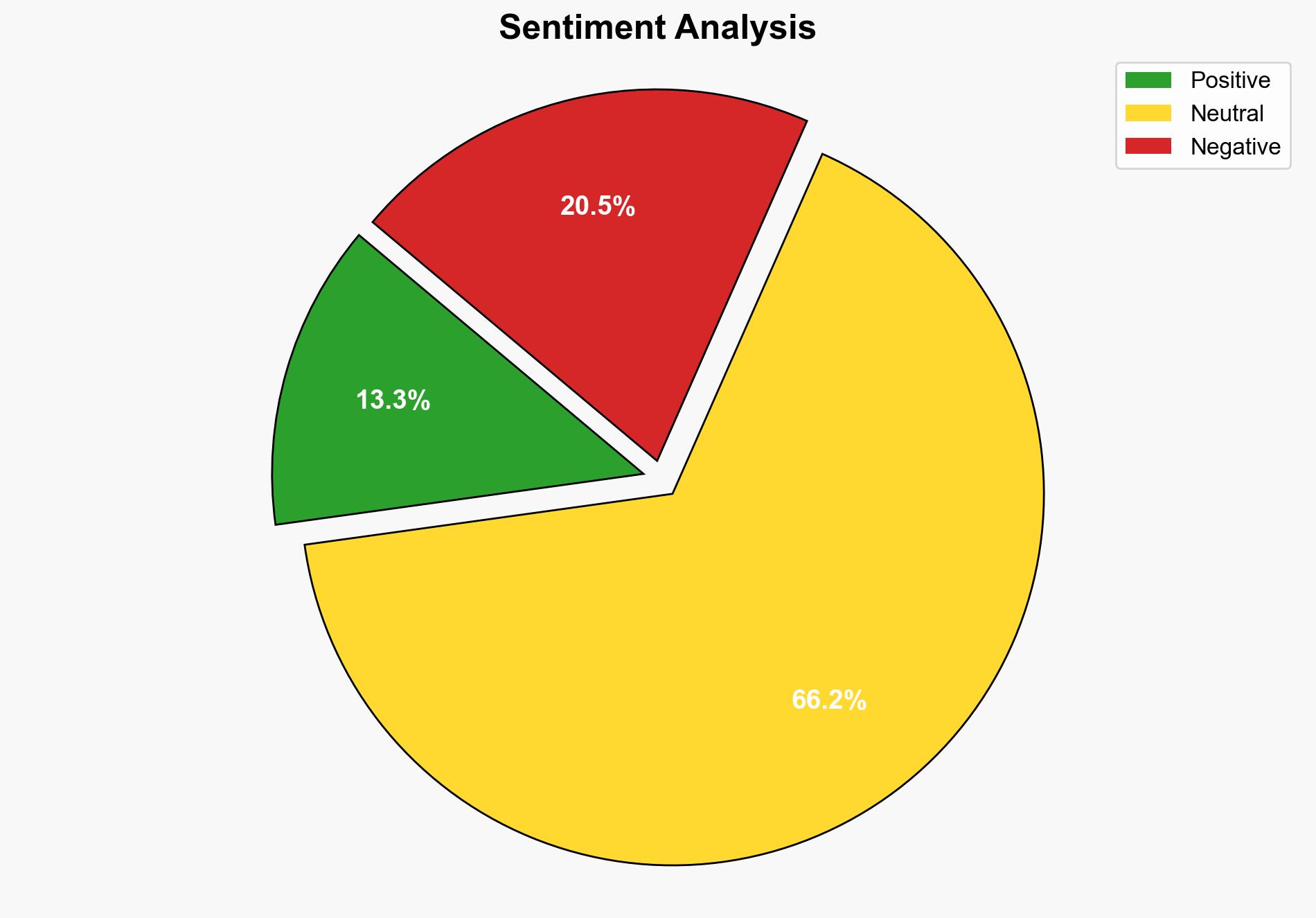
The most supported hypothesis is that the rise in cyber-attacks on PHP servers and IoT devices is primarily driven by the exploitation of known vulnerabilities and misconfigurations, particularly by botnets like Mirai, Gafgyt, and Mozi. The confidence level is moderate due to the complexity and evolving nature of cyber threats. Recommended actions include implementing robust patch management, securing configurations, and enhancing monitoring capabilities to mitigate these risks.
2. Competing Hypotheses
Hypothesis 1: The increase in cyber-attacks on PHP servers and IoT devices is primarily due to the exploitation of known vulnerabilities and misconfigurations, facilitated by botnets such as Mirai, Gafgyt, and Mozi.
Hypothesis 2: The surge in attacks is driven by a new wave of sophisticated threat actors leveraging advanced techniques beyond traditional botnets, aiming to exploit emerging vulnerabilities in cloud-native environments.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes that existing vulnerabilities are the primary entry points for attackers.
– Hypothesis 2 assumes the presence of advanced threat actors with capabilities beyond current detection methods.
Red Flags:
– Lack of detailed attribution to specific threat actors.
– Potential underestimation of emerging threats in cloud-native environments.
– Incomplete data on the full scope of vulnerabilities being exploited.
4. Implications and Strategic Risks
The continued exploitation of PHP servers and IoT devices could lead to significant disruptions in digital infrastructure, affecting both enterprises and consumers. The economic impact could be substantial, with increased costs for cybersecurity measures and potential losses from data breaches. Geopolitically, these attacks could strain international relations if state-sponsored actors are involved. Psychologically, the persistent threat may erode trust in digital services and IoT devices.
5. Recommendations and Outlook
- Implement a robust patch management strategy to address known vulnerabilities promptly.
- Enhance security configurations and disable unnecessary services in production environments.
- Increase monitoring and logging to detect and respond to unauthorized access attempts.
- Best Case: Organizations successfully mitigate risks through proactive measures, reducing the impact of attacks.
- Worst Case: Failure to address vulnerabilities leads to widespread disruptions and data breaches.
- Most Likely: Continued attacks with variable impact, prompting gradual improvements in cybersecurity practices.
6. Key Individuals and Entities
– James Maude
– Trey Ford
– Scott Schneider
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus