Talk about geriatric – This devious Android malware escapes detection by typing like an old person – TechRadar
Published on: 2025-10-29
Intelligence Report: Talk about geriatric – This devious Android malware escapes detection by typing like an old person – TechRadar
1. BLUF (Bottom Line Up Front)
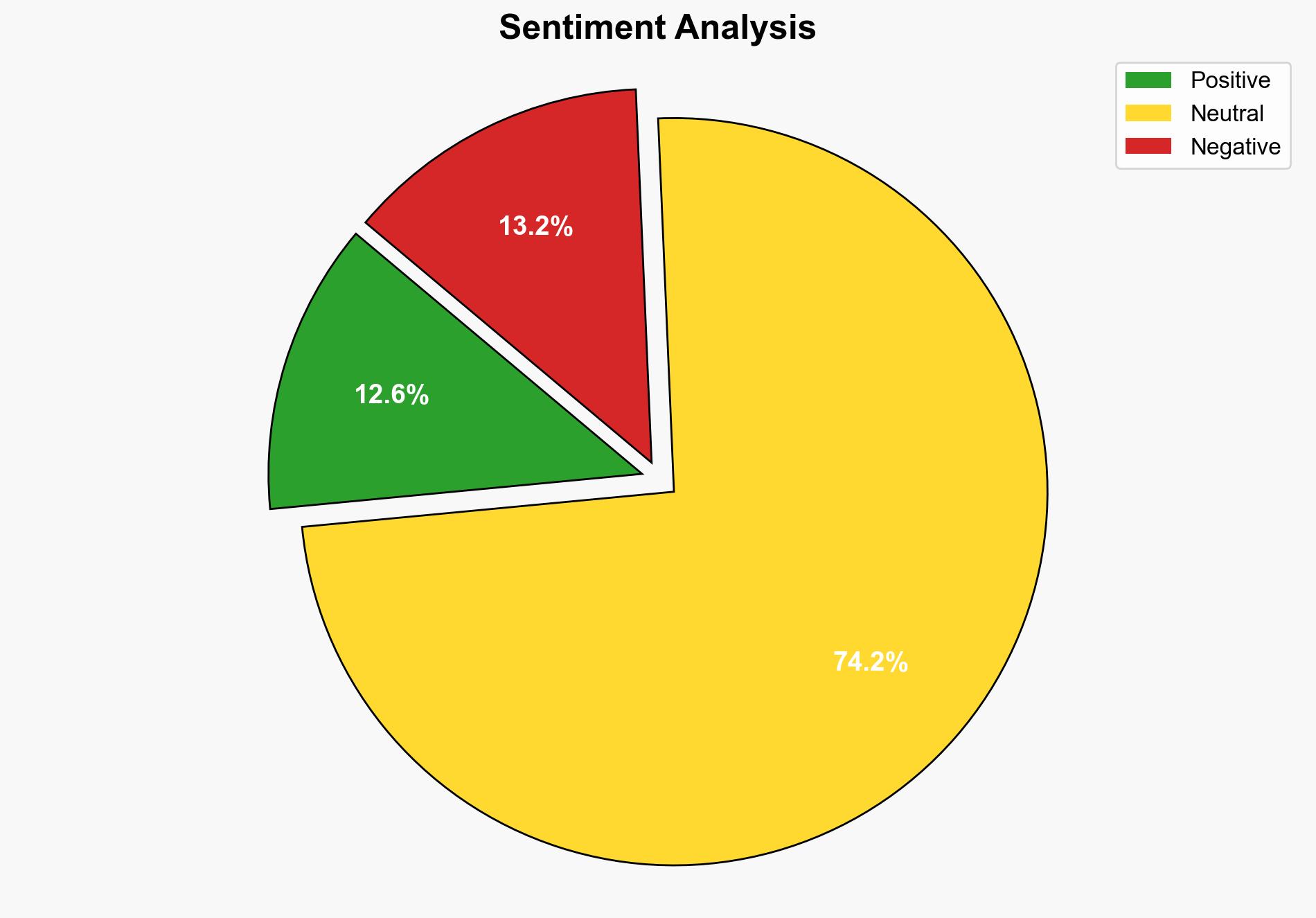
The Herodotus malware employs a novel technique to evade detection by mimicking human typing patterns, posing a significant threat to Android users. The most supported hypothesis is that this malware represents an evolution in cybercriminal tactics, specifically designed to bypass advanced security measures. Confidence level: High. Recommended action: Enhance detection algorithms to identify human-like behavior in malware and increase awareness about downloading apps from trusted sources.
2. Competing Hypotheses
1. **Hypothesis A**: Herodotus malware is primarily an evolution in malware design aimed at bypassing timing-based detection systems by simulating human typing behavior.
2. **Hypothesis B**: The malware’s human-like typing feature is a secondary characteristic, with the primary focus being on exploiting accessibility permissions for broader control over infected devices.
Using ACH 2.0, Hypothesis A is better supported due to the detailed description of the malware’s typing mimicry and its direct mention as a method to evade detection. Hypothesis B lacks specific evidence in the source text, focusing more on permissions rather than the typing behavior.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that timing-based detection is a prevalent method among antivirus programs, and that mimicking human typing is a novel and effective evasion technique.
– **Red Flags**: The source lacks detailed technical analysis of how the malware’s typing mimicry is implemented, which could indicate an overemphasis on this feature without substantial evidence.
– **Blind Spots**: The report does not address how widespread the malware’s impact is or its potential for adaptation to other platforms.
4. Implications and Strategic Risks
The Herodotus malware could signal a shift in cybercriminal strategies towards more sophisticated evasion techniques, potentially leading to increased difficulty in malware detection. This evolution may prompt a cybersecurity arms race, with antivirus developers needing to innovate rapidly. Economically, this could increase costs for cybersecurity measures. Psychologically, it may erode user trust in mobile security.
5. Recommendations and Outlook
- **Mitigation**: Develop and deploy advanced detection algorithms that can identify human-like behavior in malware.
- **Awareness**: Launch campaigns to educate users on the risks of downloading apps from unofficial sources.
- **Scenario Projections**:
– **Best Case**: Rapid adaptation by security firms neutralizes the threat, maintaining user trust.
– **Worst Case**: Malware spreads widely, leading to significant data breaches and financial losses.
– **Most Likely**: Gradual adaptation by security firms mitigates the threat over time, with some initial impact.
6. Key Individuals and Entities
– **Herodotus**: The malware named in the report.
– **Threat Fabric**: The security research group that discovered the malware.
– **Sead**: A journalist mentioned in the source text.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus