Social Engineering Scams Top Crypto Threats in 2025 WhiteBit – CoinDesk
Published on: 2025-10-30
Intelligence Report: Social Engineering Scams Top Crypto Threats in 2025 WhiteBit – CoinDesk
1. BLUF (Bottom Line Up Front)
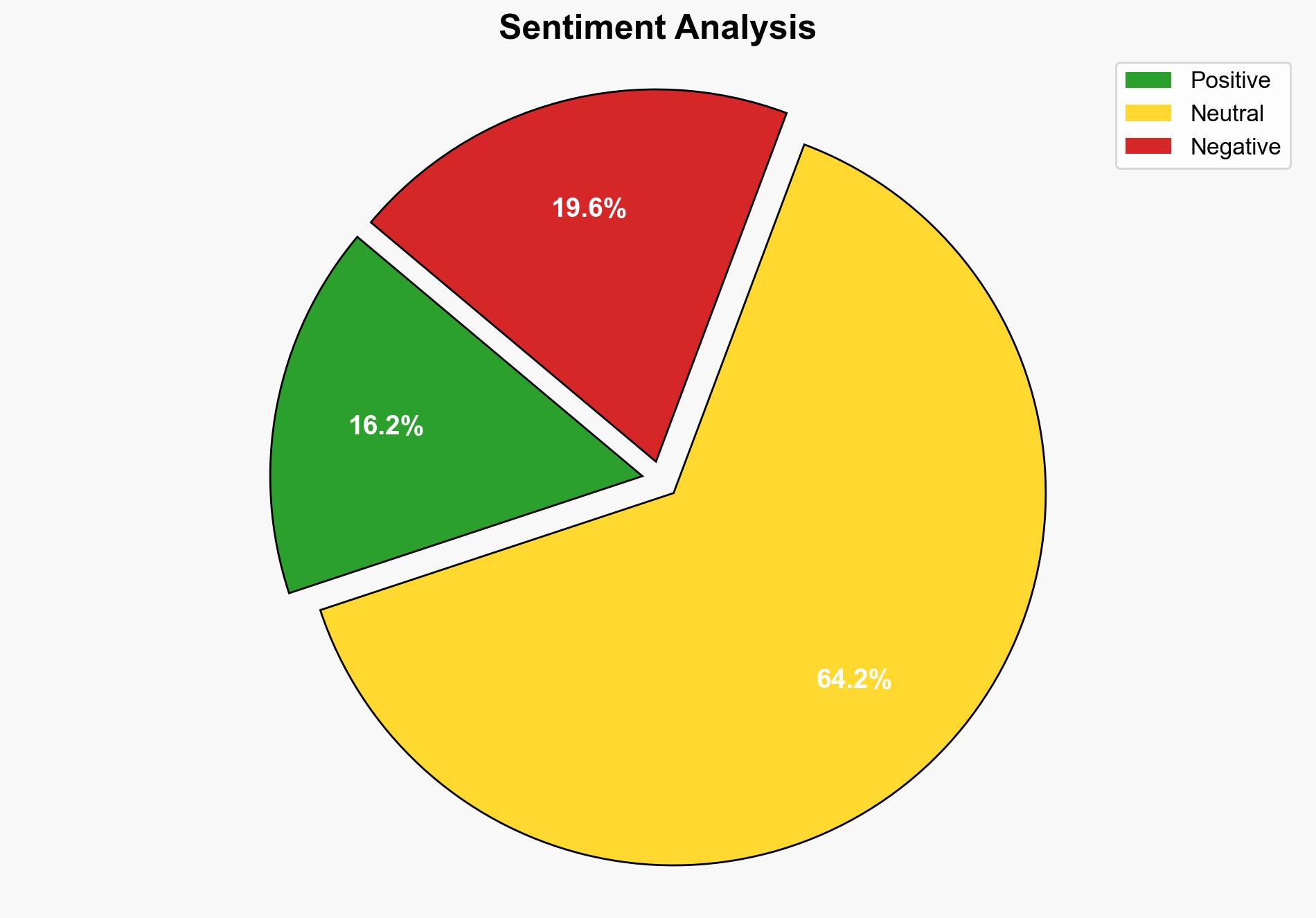
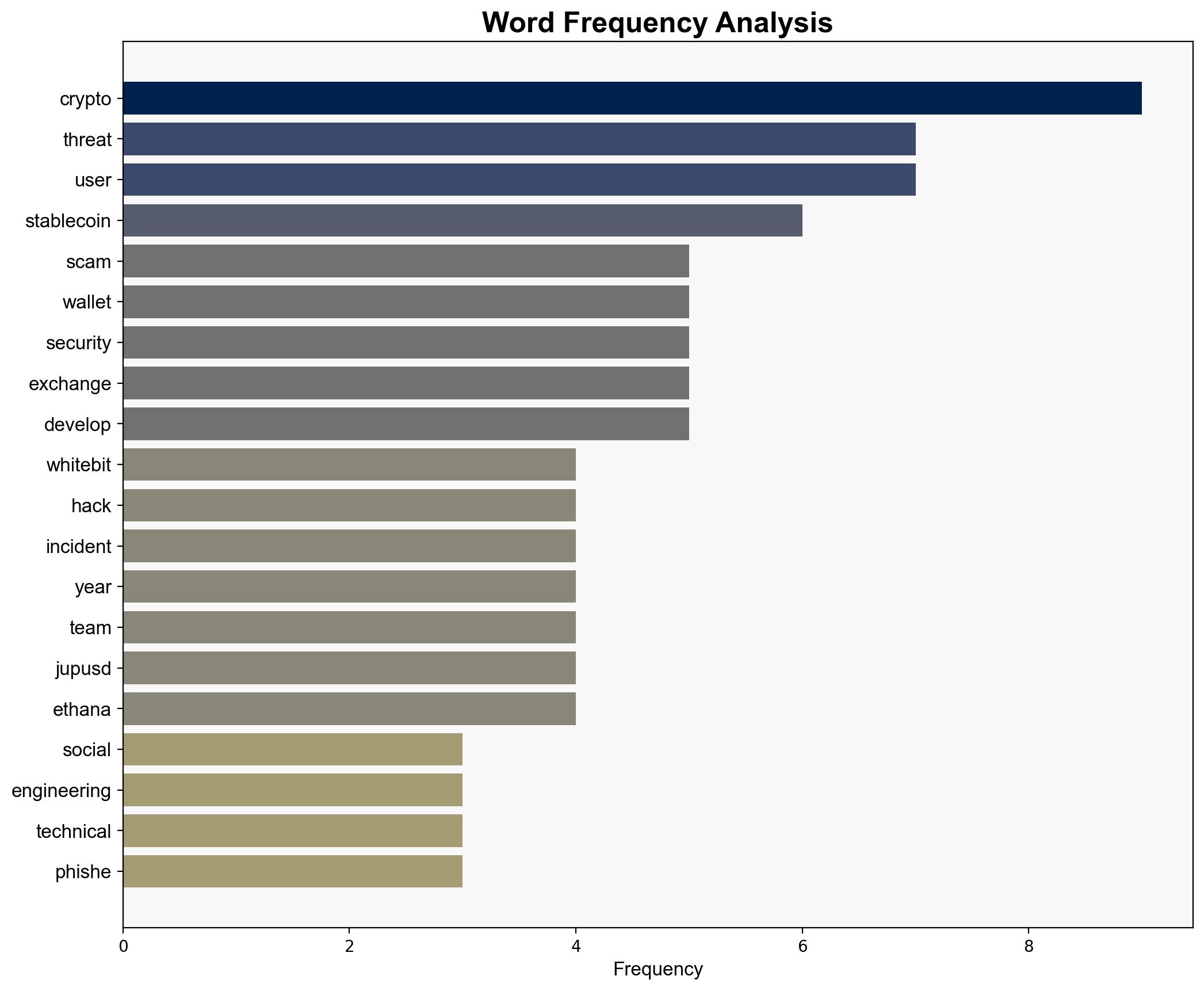
Social engineering scams are projected to continue as the primary threat to cryptocurrency users in 2025, with technical wallet hacks as a secondary concern. The most supported hypothesis suggests that human-targeted scams will remain prevalent due to their adaptability and low-cost execution. Confidence level: High. Recommended action: Enhance user education and implement robust security protocols across platforms.
2. Competing Hypotheses
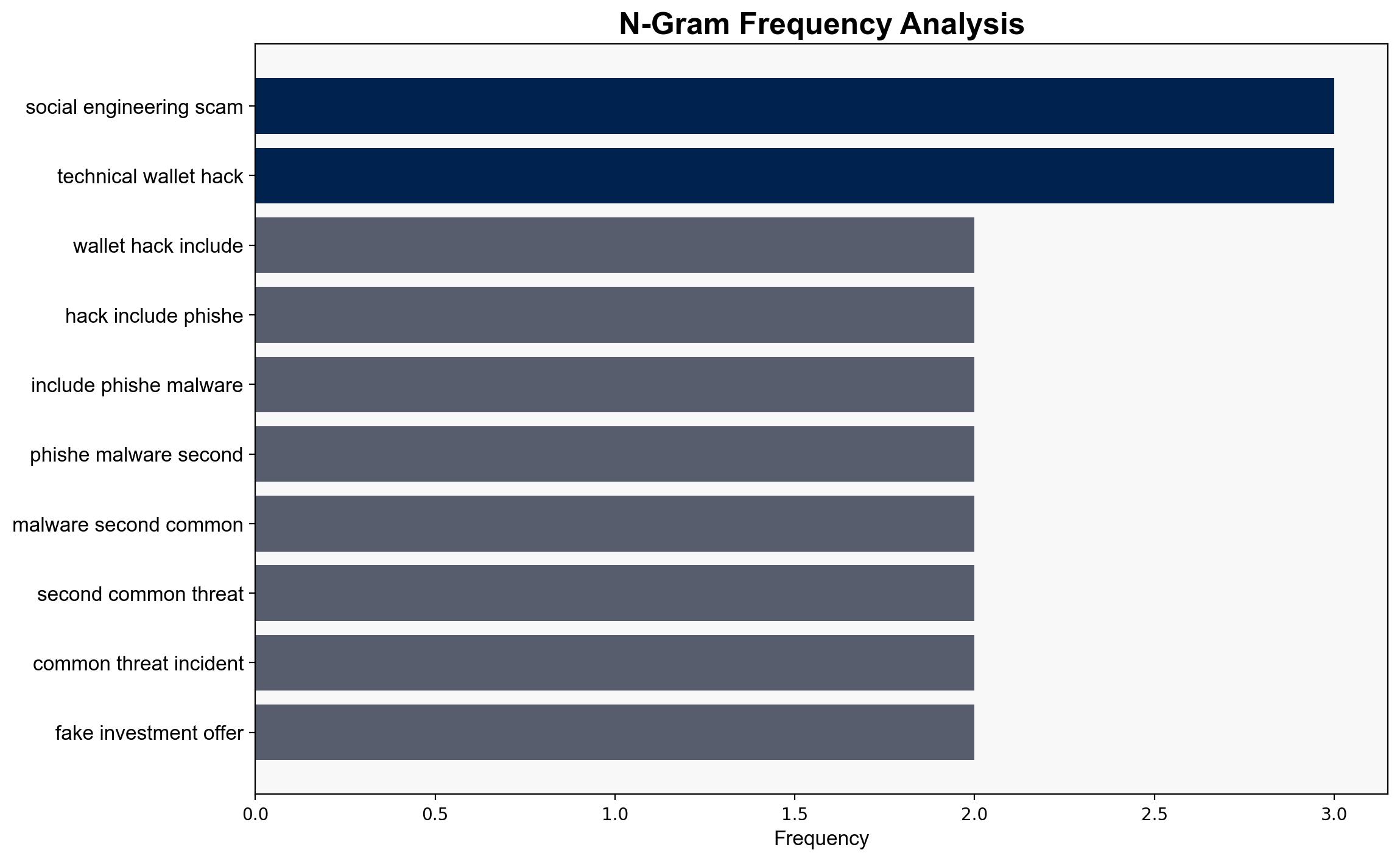
Hypothesis 1: Social engineering scams will remain the leading threat due to their reliance on exploiting human behavior, which is less costly and more adaptable than technical hacks.
Hypothesis 2: Technical wallet hacks, including phishing and malware, will surpass social engineering scams as the primary threat due to advancements in hacking techniques and increased targeting of high-value accounts.
Using ACH 2.0, Hypothesis 1 is better supported by the data, given the consistent emphasis on human-targeted scams in the report and the historical prevalence of such incidents.
3. Key Assumptions and Red Flags
Assumptions:
– Users will continue to be the weakest link in cybersecurity, making social engineering effective.
– Technical defenses will improve, potentially reducing the success rate of technical hacks.
Red Flags:
– Lack of detailed data on the success rates of technical hacks versus social engineering.
– Potential bias in reporting from WhiteBit, as they may emphasize threats that align with their security measures.
4. Implications and Strategic Risks
The persistence of social engineering scams poses a significant risk to the cryptocurrency ecosystem, potentially undermining user trust and market stability. If technical hacks increase, they could lead to larger-scale financial losses and regulatory scrutiny. Geopolitically, state-sponsored hacking groups could exploit these vulnerabilities to destabilize financial systems.
5. Recommendations and Outlook
- Enhance user education on recognizing and avoiding scams.
- Develop and enforce industry-wide security standards for exchanges and wallets.
- Scenario Projections:
- Best Case: User education and security measures significantly reduce scam incidents.
- Worst Case: A major technical hack leads to widespread financial loss and regulatory backlash.
- Most Likely: Social engineering remains the primary threat, with technical hacks as a persistent secondary concern.
6. Key Individuals and Entities
– WhiteBit
– CoinDesk
– CertiK
– Chainalysis
– Bybit
– North Korea’s Lazarus Group
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus