Shadow IT is threatening businesses from within – and todays security tools simply cant keep up – TechRadar
Published on: 2025-11-01
Intelligence Report: Shadow IT is threatening businesses from within – and today’s security tools simply can’t keep up – TechRadar
1. BLUF (Bottom Line Up Front)
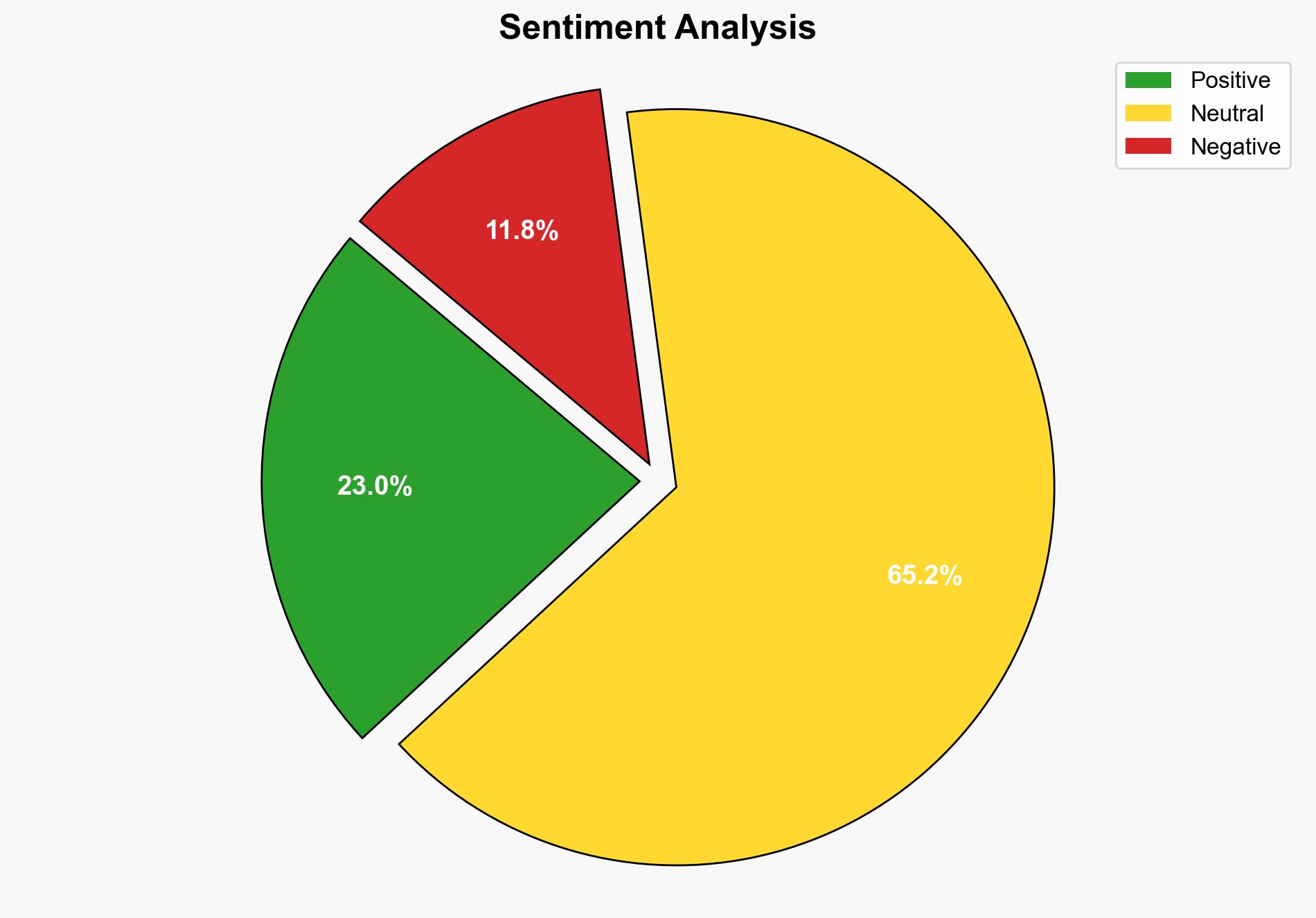
Shadow IT poses a significant internal threat to businesses, exacerbated by inadequate security tools. The most supported hypothesis is that employees, driven by productivity needs, bypass official channels, creating vulnerabilities. Confidence level: Moderate. Recommended action: Enhance security protocols and employee training to mitigate risks.
2. Competing Hypotheses
Hypothesis 1: Employees use unauthorized IT tools primarily to enhance productivity, inadvertently increasing security risks due to inadequate governance and oversight.
Hypothesis 2: Employees intentionally bypass security protocols due to a lack of trust in corporate IT solutions, perceiving them as inefficient or restrictive.
Using ACH 2.0, Hypothesis 1 is better supported by the evidence, as the primary motivation appears to be productivity enhancement rather than intentional subversion of security protocols.
3. Key Assumptions and Red Flags
– Assumption: Employees are primarily motivated by productivity gains rather than malicious intent.
– Red Flag: Lack of comprehensive data on the extent of shadow IT usage and its direct impact on security breaches.
– Cognitive Bias: Potential underestimation of employee dissatisfaction with existing IT solutions.
4. Implications and Strategic Risks
The proliferation of shadow IT can lead to increased cyberattacks, data breaches, and loss of customer trust. Economically, this could result in financial losses and reputational damage. Psychologically, it may erode employee trust in corporate governance, leading to further non-compliance.
5. Recommendations and Outlook
- Implement comprehensive employee training on the risks of shadow IT and the importance of following security protocols.
- Enhance IT governance frameworks to include more flexible and efficient tools that meet employee needs.
- Best-case scenario: Improved security posture and employee satisfaction through better tools and training.
- Worst-case scenario: Continued rise in security breaches and employee dissatisfaction, leading to financial and reputational damage.
- Most likely scenario: Gradual improvement in security with targeted interventions and policy adjustments.
6. Key Individuals and Entities
– Dave Lewis
– Mark Hazleton
– Mark Hillick
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus