Conduent January 2025 breach impacts 10M people – Securityaffairs.com
Published on: 2025-11-03
Intelligence Report: Conduent January 2025 breach impacts 10M people – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
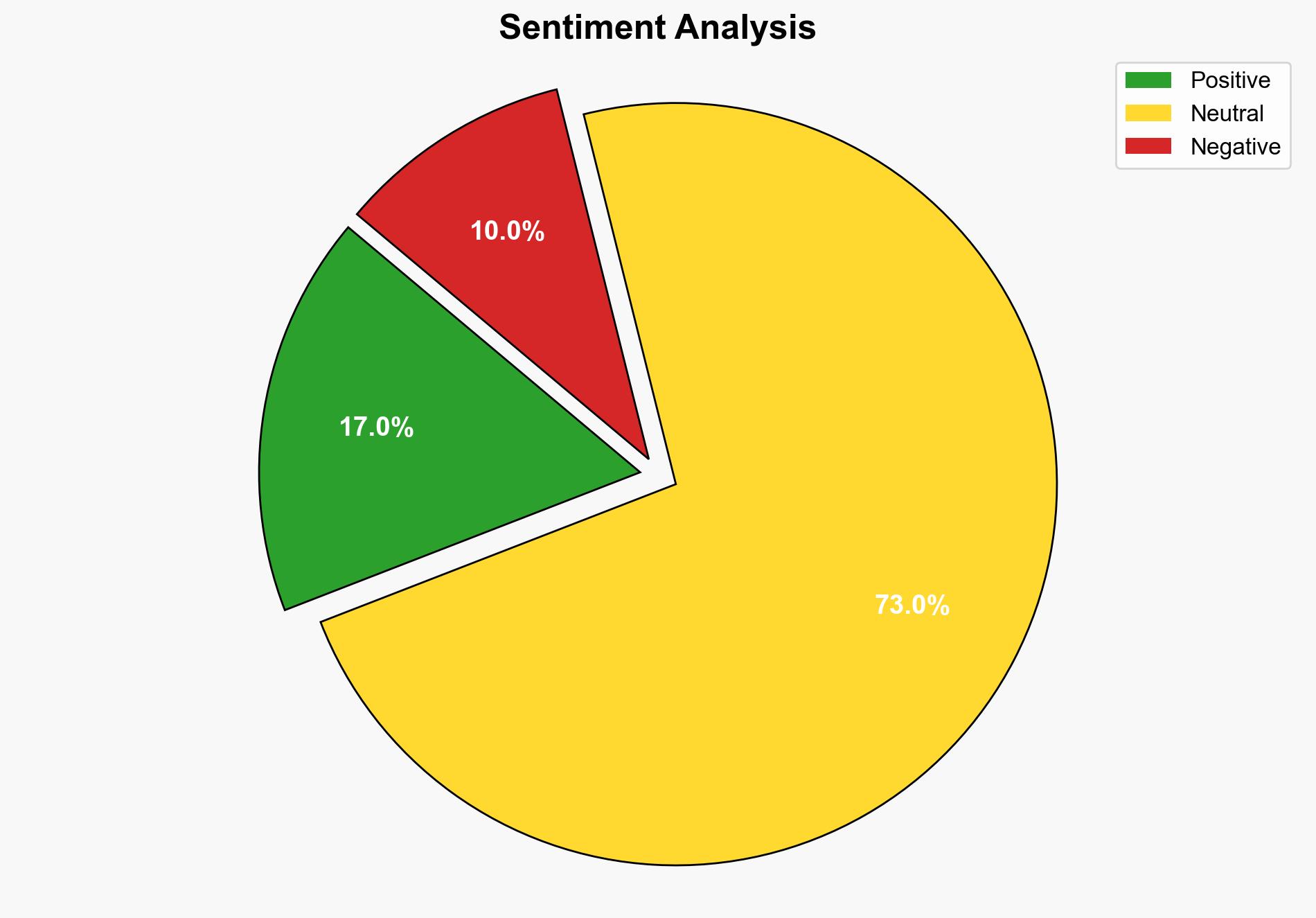
The Conduent data breach, impacting 10 million individuals, suggests significant vulnerabilities in the company’s cybersecurity infrastructure. The most supported hypothesis is that the breach was a result of sophisticated cybercriminal activity exploiting systemic weaknesses. Confidence level: Moderate. Recommended action: Immediate enhancement of cybersecurity protocols and comprehensive forensic analysis to prevent future breaches.
2. Competing Hypotheses
1. **Hypothesis A**: The breach was orchestrated by a sophisticated cybercriminal group targeting Conduent’s systemic vulnerabilities over several months.
2. **Hypothesis B**: The breach resulted from an insider threat, possibly involving collusion with external actors to exploit internal access for data theft.
Using ACH 2.0, Hypothesis A is better supported due to the prolonged access period (October to January) and the complexity of the data stolen, which suggests external expertise and resources. Hypothesis B lacks direct evidence but remains plausible given the potential for insider facilitation in such breaches.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes external actors had the capability and intent to exploit Conduent’s vulnerabilities. Hypothesis B assumes potential insider collusion.
– **Red Flags**: Lack of detailed information on how the breach was detected and specifics of the exploited vulnerabilities. The timeline of detection versus breach duration raises questions about internal monitoring efficacy.
– **Blind Spots**: Potential underestimation of internal security lapses or insider involvement.
4. Implications and Strategic Risks
The breach could lead to significant financial losses for Conduent due to regulatory fines, litigation, and reputational damage. There is a risk of cascading effects if similar vulnerabilities exist in other companies within the sector. Geopolitically, the breach could escalate tensions if linked to state-sponsored actors, impacting international relations and cybersecurity policies.
5. Recommendations and Outlook
- Conduct a thorough forensic investigation to identify the breach’s origin and exploited vulnerabilities.
- Enhance cybersecurity measures, including employee training and advanced threat detection systems.
- Engage with cybersecurity experts to develop a robust incident response plan.
- Scenario Projections:
- Best Case: Rapid identification and rectification of vulnerabilities, restoring stakeholder confidence.
- Worst Case: Further breaches occur due to unresolved vulnerabilities, leading to severe financial and reputational damage.
- Most Likely: Gradual improvement in cybersecurity posture with ongoing risks of attempted breaches.
6. Key Individuals and Entities
– Conduent (affected entity)
– Unnamed cybercriminal group (potential perpetrator)
7. Thematic Tags
national security threats, cybersecurity, data breach, corporate security