Identity Is Now the Top Source of Cloud Risk – Infosecurity Magazine
Published on: 2025-11-04
Intelligence Report: Identity Is Now the Top Source of Cloud Risk – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
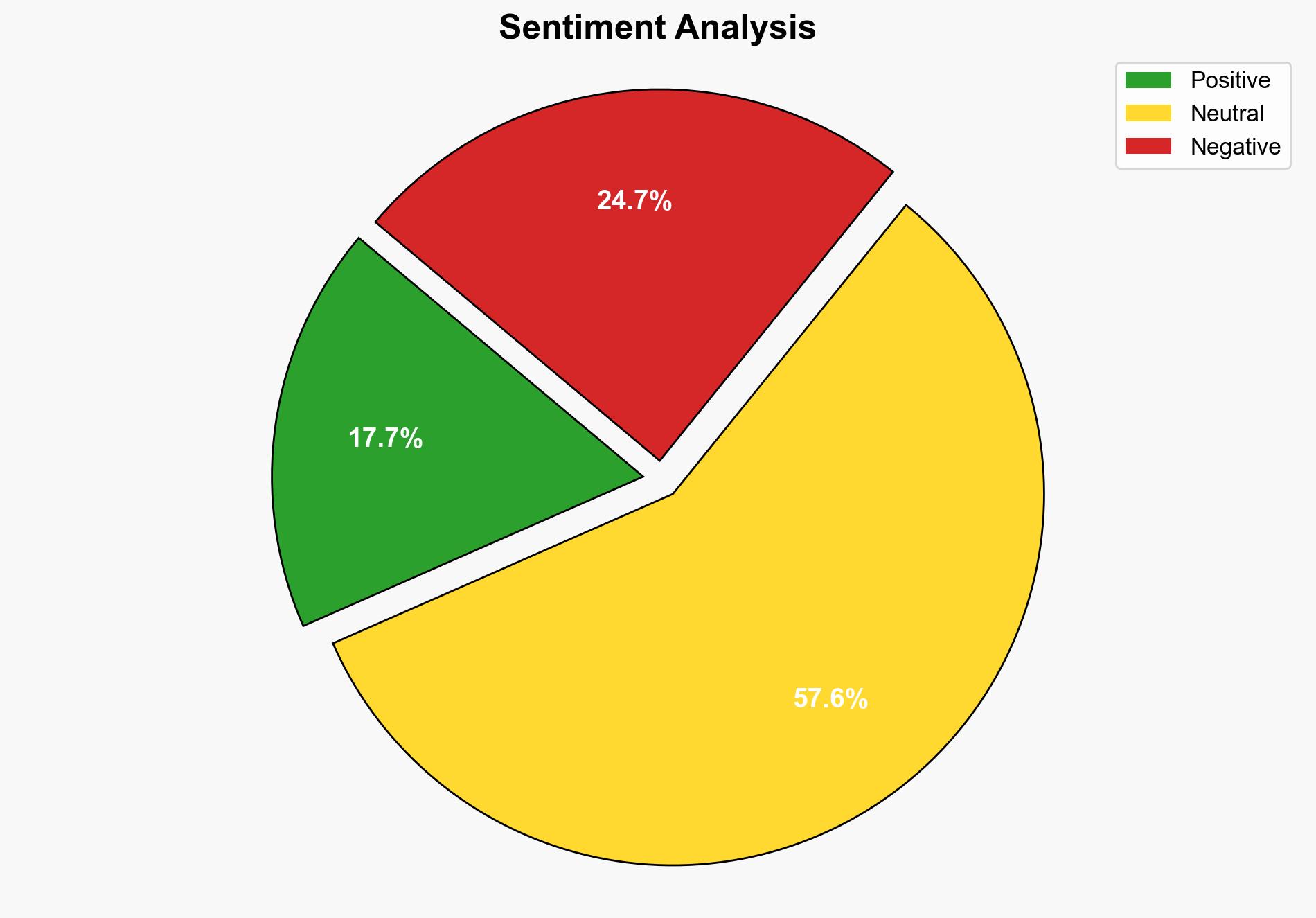
The most supported hypothesis is that identity vulnerabilities, particularly excessive permissions and misconfigured roles, are the primary drivers of increased cloud attacks. This is supported by evidence of threat actors exploiting these weaknesses to gain unauthorized access. The recommended action is to enhance identity management practices and automate security checks to mitigate these risks. Confidence Level: High.
2. Competing Hypotheses
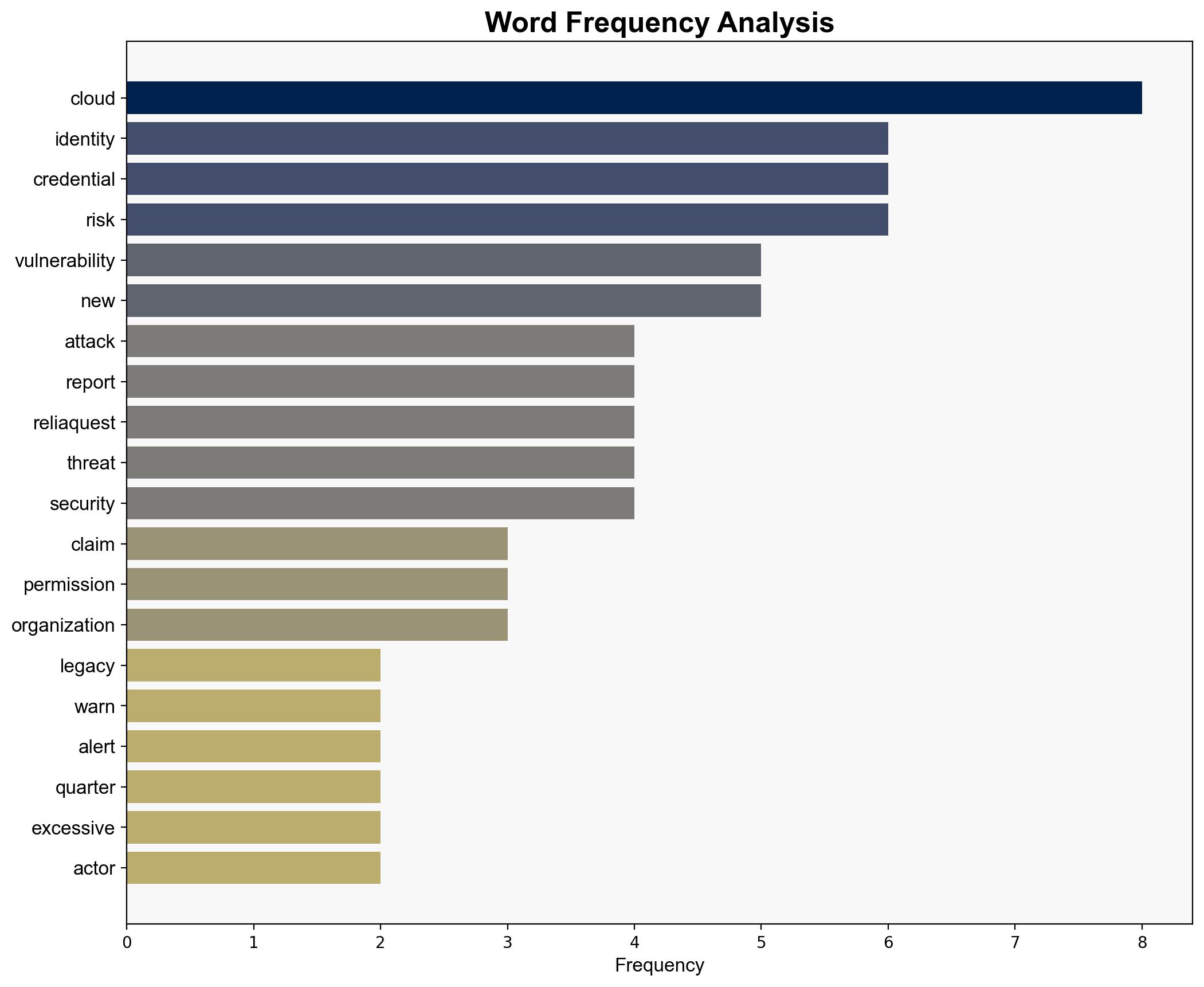
Hypothesis 1: Identity vulnerabilities, such as excessive permissions and misconfigured roles, are the primary drivers of increased cloud attacks. This is supported by the report’s emphasis on these factors as key weaknesses exploited by threat actors.
Hypothesis 2: The surge in cloud attacks is primarily driven by poor DevOps practices and the rapid deployment of infrastructure, which perpetuates legacy vulnerabilities. This is supported by the report’s mention of systematic redeployment of flawed templates and the creation of new assets that expand the attack surface.
Using ACH 2.0, Hypothesis 1 is better supported due to the direct correlation between identity weaknesses and the ability of threat actors to escalate privileges and bypass alarms. Hypothesis 2, while plausible, lacks direct evidence linking it as the primary driver over identity vulnerabilities.
3. Key Assumptions and Red Flags
Assumptions include the belief that identity management improvements will significantly reduce cloud risks and that current security measures are insufficient. A potential red flag is the reliance on reports from a single source, which may introduce bias. There is also a blind spot regarding the role of insider threats and their impact on cloud security.
4. Implications and Strategic Risks
The persistence of identity vulnerabilities could lead to increased data breaches and financial losses. Organizations may face reputational damage and regulatory penalties. If poor DevOps practices continue, the attack surface will expand, increasing the likelihood of successful attacks. This could have cascading effects on supply chains and critical infrastructure.
5. Recommendations and Outlook
- Implement comprehensive identity management solutions, such as CIEM tools, to monitor and manage permissions effectively.
- Automate security checks in CI/CD pipelines to prevent misconfigurations from reaching production.
- Scenario Projections:
- Best Case: Organizations adopt robust identity management practices, significantly reducing cloud attack incidents.
- Worst Case: Failure to address identity vulnerabilities leads to widespread data breaches and financial losses.
- Most Likely: Incremental improvements in identity management reduce some risks, but challenges persist due to rapid infrastructure deployment.
6. Key Individuals and Entities
The report does not mention specific individuals by name. Key entities include ReliaQuest, AWS, Azure, Google Cloud, and various SaaS applications.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus