The Most Critical Linux Kernel Breaches of 2025 So Far – Linuxjournal.com
Published on: 2025-11-04
Intelligence Report: The Most Critical Linux Kernel Breaches of 2025 So Far – Linuxjournal.com
1. BLUF (Bottom Line Up Front)
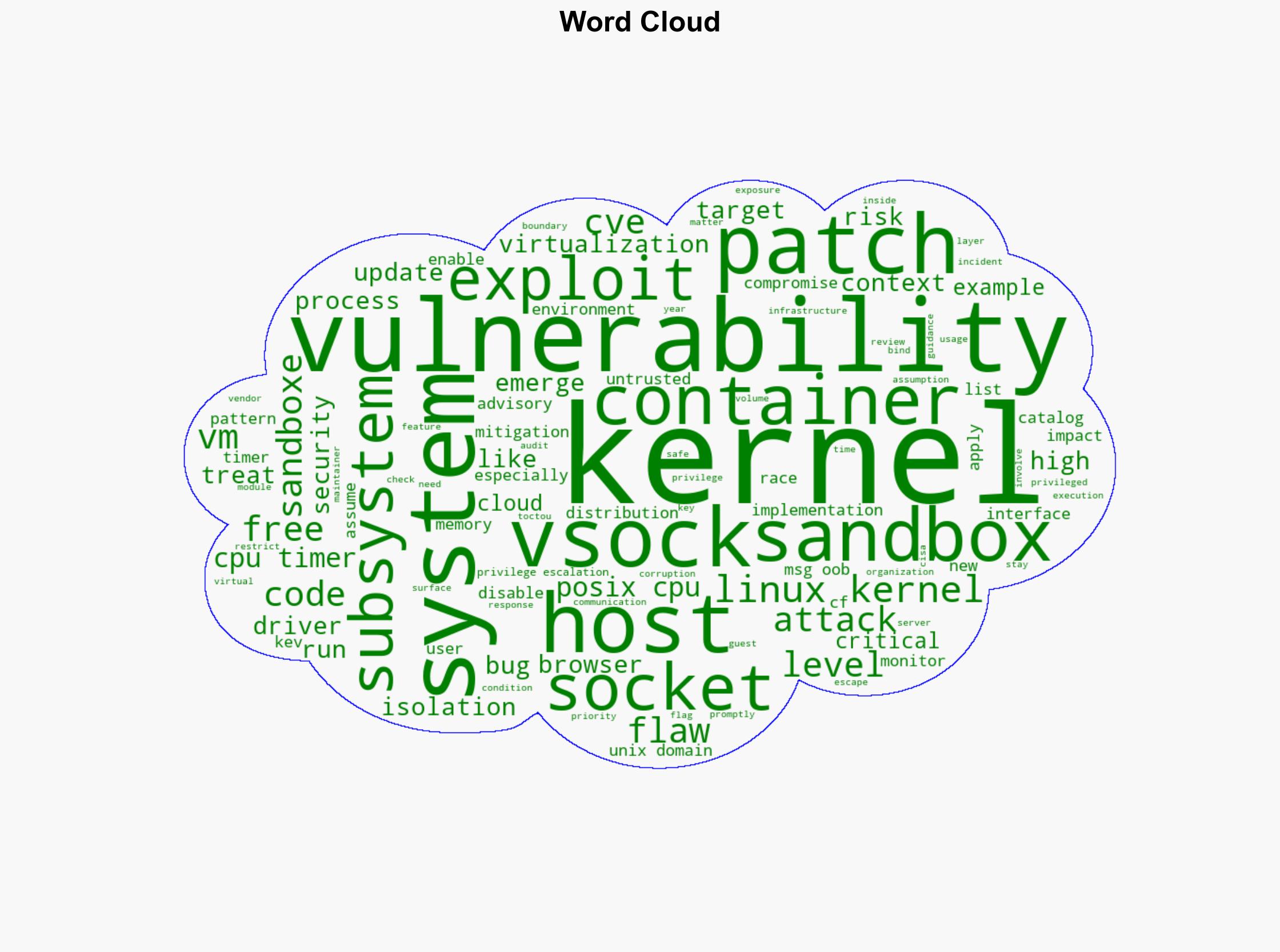
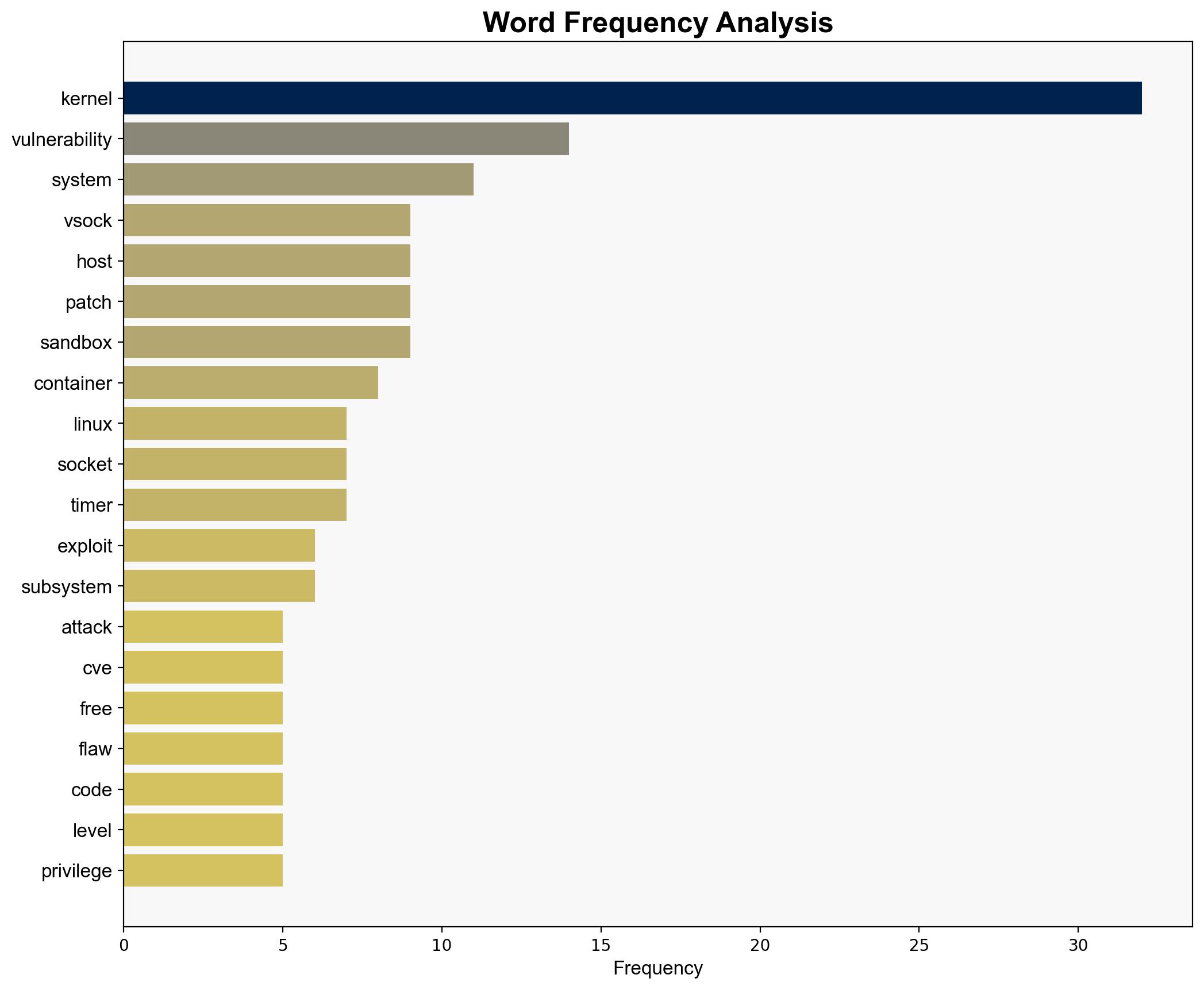
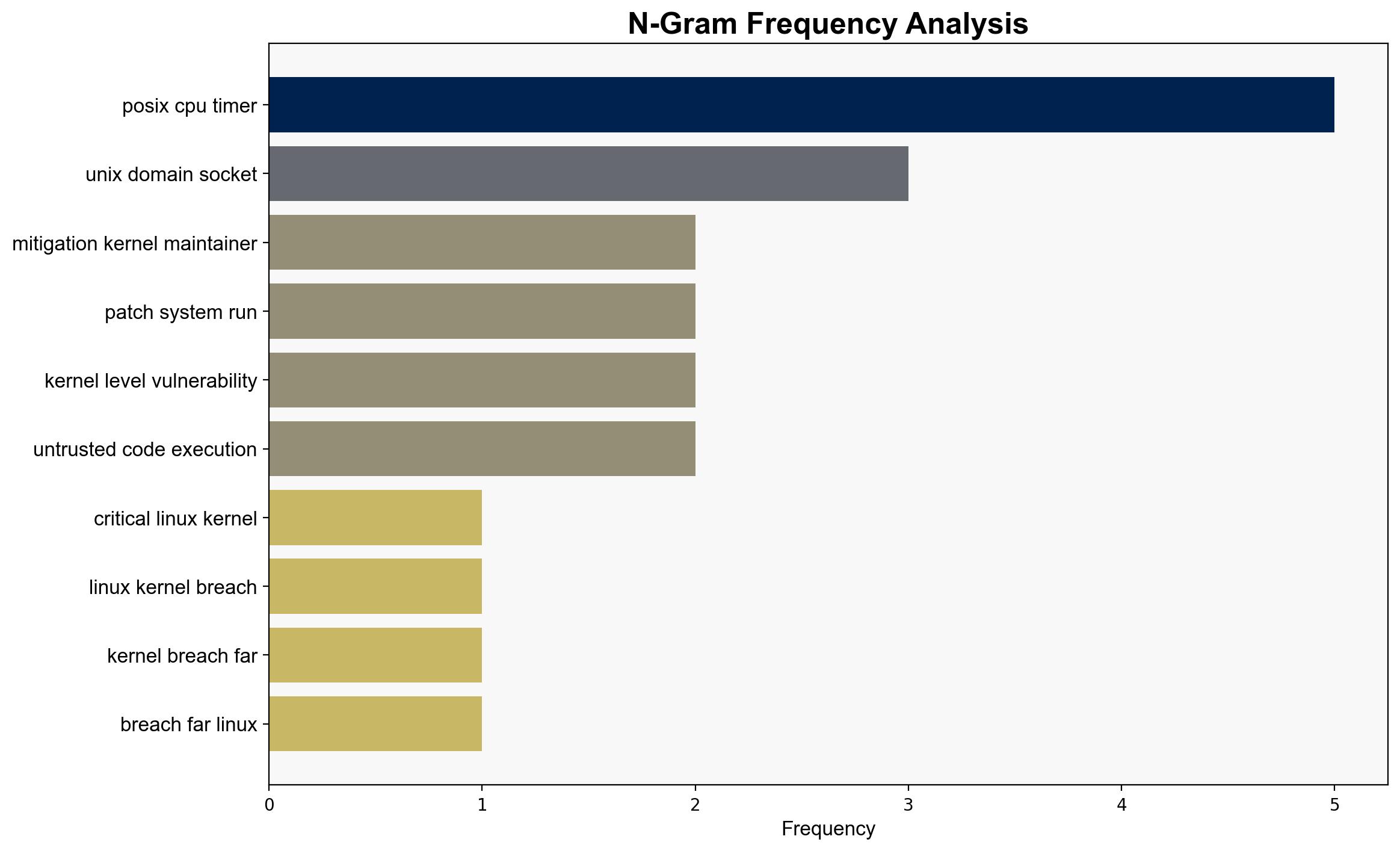
The most supported hypothesis suggests that the recent Linux kernel vulnerabilities represent a strategic shift in cyber threats towards exploiting isolation layers and boundary conditions in multi-tenant cloud environments. Confidence Level: High. Recommended action includes immediate patch application and enhanced monitoring of virtualization and sandbox environments.
2. Competing Hypotheses
Hypothesis 1: The vulnerabilities are part of a coordinated effort by state-sponsored actors to undermine cloud infrastructure security, targeting isolation layers to gain unauthorized access to sensitive data.
Hypothesis 2: The vulnerabilities result from increased complexity and rapid development cycles in Linux kernel updates, leading to exploitable flaws that are opportunistically targeted by various threat actors.
Using ACH 2.0, Hypothesis 1 is better supported due to the strategic targeting of isolation layers and the potential for high-value data breaches, which align with state-sponsored objectives.
3. Key Assumptions and Red Flags
Assumptions include the belief that all vulnerabilities are equally likely to be exploited by state actors. A red flag is the lack of specific attribution to any threat actor, which could indicate either a lack of intelligence or deliberate obfuscation by the attackers. The assumption that patching alone will mitigate risks may overlook the need for broader security architecture reviews.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant data breaches, impacting economic stability and national security. The focus on isolation layers suggests a potential escalation in cyber warfare tactics, with broader geopolitical implications if state actors are involved. The psychological impact on public trust in cloud services could be profound, affecting market dynamics.
5. Recommendations and Outlook
- Immediate application of available patches across all affected systems.
- Conduct a comprehensive security audit of virtualization and sandbox environments.
- Develop scenario-based training for IT security teams to respond to potential breaches.
- Best Case: Rapid patch deployment and increased vigilance prevent further exploitation.
- Worst Case: Delayed response leads to widespread data breaches and geopolitical tensions.
- Most Likely: Continued exploitation attempts with varying degrees of success, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Entities involved include Linux kernel maintainers, cloud service providers, and cybersecurity agencies.
7. Thematic Tags
national security threats, cybersecurity, cloud infrastructure, state-sponsored cyber activities