Norton Crack Midnight Ransomware Release Free Decryptor – HackRead
Published on: 2025-11-05
Intelligence Report: Norton Crack Midnight Ransomware Release Free Decryptor – HackRead
1. BLUF (Bottom Line Up Front)
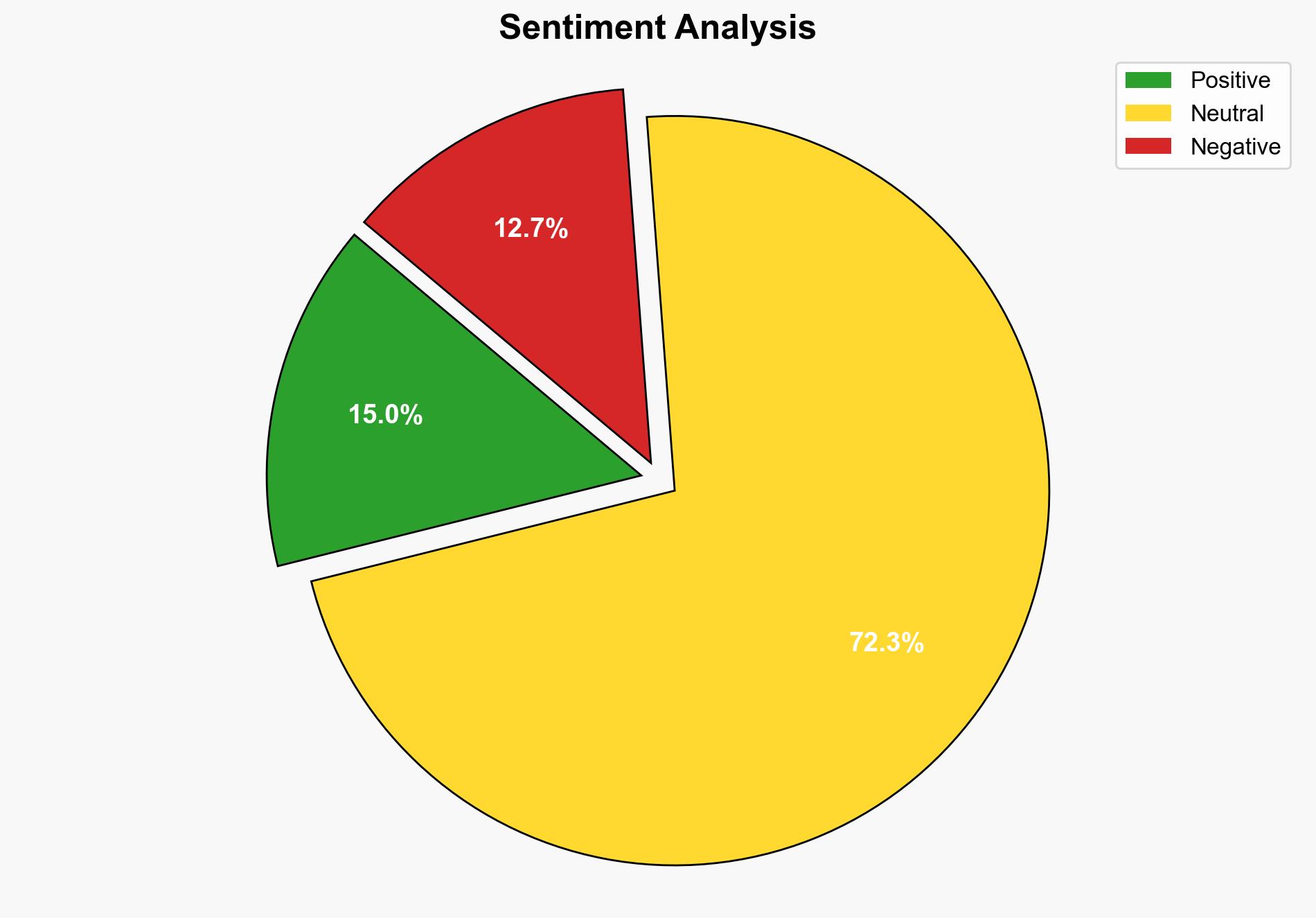
The most supported hypothesis is that the Midnight ransomware, derived from the Babuk source code, inadvertently weakened its encryption, allowing Norton to develop a free decryptor. This reflects a strategic opportunity to mitigate ransomware threats. Confidence level: Moderate. Recommended action: Promote the use of the decryptor and enhance monitoring of ransomware evolution.
2. Competing Hypotheses
1. **Hypothesis A**: Midnight ransomware, based on Babuk’s leaked source code, introduced a flaw in its encryption, which Norton exploited to develop a decryptor. This flaw was unintentional, resulting from attempts to enhance encryption speed and strength.
2. **Hypothesis B**: The flaw in Midnight ransomware was intentionally introduced by its developers as a deceptive tactic to mislead cybersecurity efforts, with the decryptor’s effectiveness being temporary or limited.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the detailed technical analysis provided by Norton, indicating genuine cryptographic errors rather than deliberate sabotage.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Norton’s analysis is accurate and unbiased. There is also an assumption that the Midnight developers did not anticipate the flaw.
– **Red Flags**: The rapid development of a decryptor suggests potential undisclosed collaboration or prior knowledge. The lack of direct evidence from the ransomware developers leaves room for alternative interpretations.
4. Implications and Strategic Risks
The emergence of Midnight ransomware highlights the persistent threat of ransomware evolution using leaked source codes. The potential for other groups to exploit similar leaks poses a significant cybersecurity risk. Economically, widespread ransomware attacks could disrupt critical infrastructure and businesses. Geopolitically, state-sponsored actors might leverage such vulnerabilities for strategic advantage.
5. Recommendations and Outlook
- Promote the use of Norton’s decryptor among potential victims to mitigate immediate threats.
- Enhance monitoring and intelligence-sharing on ransomware developments to anticipate future threats.
- Scenario Projections:
- Best Case: Widespread adoption of the decryptor reduces ransomware impact significantly.
- Worst Case: Ransomware developers adapt quickly, rendering the decryptor obsolete.
- Most Likely: The decryptor provides temporary relief, but new ransomware variants emerge.
6. Key Individuals and Entities
– Norton (Gen Digital)
– Midnight ransomware developers
– Babuk ransomware source code contributors
7. Thematic Tags
national security threats, cybersecurity, ransomware, data protection, cyber defense