Credentials and Misconfigurations Behind Most Cloud Breaches Says AWS – HackRead
Published on: 2025-11-05
Intelligence Report: Credentials and Misconfigurations Behind Most Cloud Breaches Says AWS – HackRead
1. BLUF (Bottom Line Up Front)
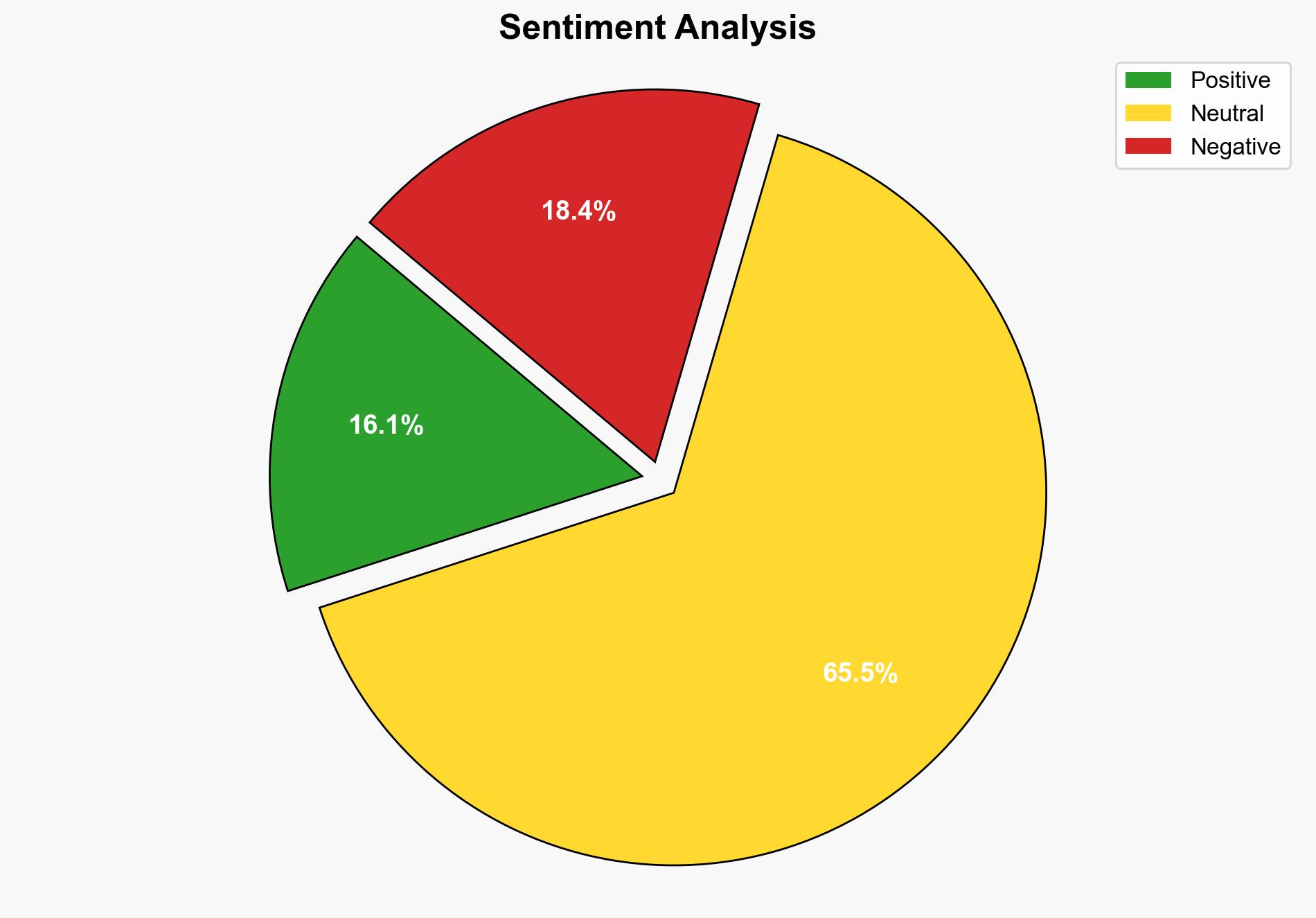
The most supported hypothesis is that human factors, particularly credential mismanagement and misconfigurations, are the primary drivers of cloud breaches. This is supported by the AWS report’s emphasis on these issues as central security failure points. Confidence level: Moderate. Recommended action includes enhancing user training and implementing stricter access controls.
2. Competing Hypotheses
Hypothesis 1: Human factors, such as credential mismanagement and misconfigurations, are the primary causes of cloud breaches. This hypothesis is supported by the AWS report, which highlights these as significant security failure points.
Hypothesis 2: Technological vulnerabilities and sophisticated cyber-attacks are the main causes of cloud breaches. This is supported by the mention of vulnerability exploitation and advanced techniques like adversary-in-the-middle phishing.
Using ACH 2.0, Hypothesis 1 is better supported due to the consistent emphasis on human errors across multiple sections of the report, whereas technological vulnerabilities are mentioned but not as prominently highlighted as the primary cause.
3. Key Assumptions and Red Flags
Assumptions:
– Human error is inherently more prevalent than technological flaws in cloud security breaches.
– Organizations have not fully adapted to the complexities of cloud systems.
Red Flags:
– Potential underestimation of the role of advanced persistent threats (APTs) in cloud breaches.
– Lack of detailed statistical data on the proportion of breaches caused by each factor.
4. Implications and Strategic Risks
The persistence of human errors in cloud security could lead to increased operational downtime and reputational damage for organizations. The evolving nature of cyber threats, such as the use of legitimate tools for undetected operations, poses a risk of more sophisticated attacks. Economically, this could increase costs related to breach recovery and insurance.
5. Recommendations and Outlook
- Implement comprehensive training programs focused on cloud security best practices.
- Adopt multi-factor authentication (MFA) and regular audits of access credentials.
- Scenario Projections:
- Best Case: Enhanced security measures significantly reduce breach incidents.
- Worst Case: Continued human errors lead to major breaches and financial losses.
- Most Likely: Incremental improvements in security with occasional breaches due to evolving threats.
6. Key Individuals and Entities
– Elad Luz, head of research at OASIS Security, anticipates a shift in attacker focus.
– Amazon Web Services (AWS) and Vanson Bourne are central to the report findings.
7. Thematic Tags
national security threats, cybersecurity, cloud security, human error, technological vulnerabilities