Complete list Child pornography exploitation suspects arrested in Operation Firewall – Boston Herald
Published on: 2025-11-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Complete list Child pornography exploitation suspects arrested in Operation Firewall – Boston Herald
1. BLUF (Bottom Line Up Front)
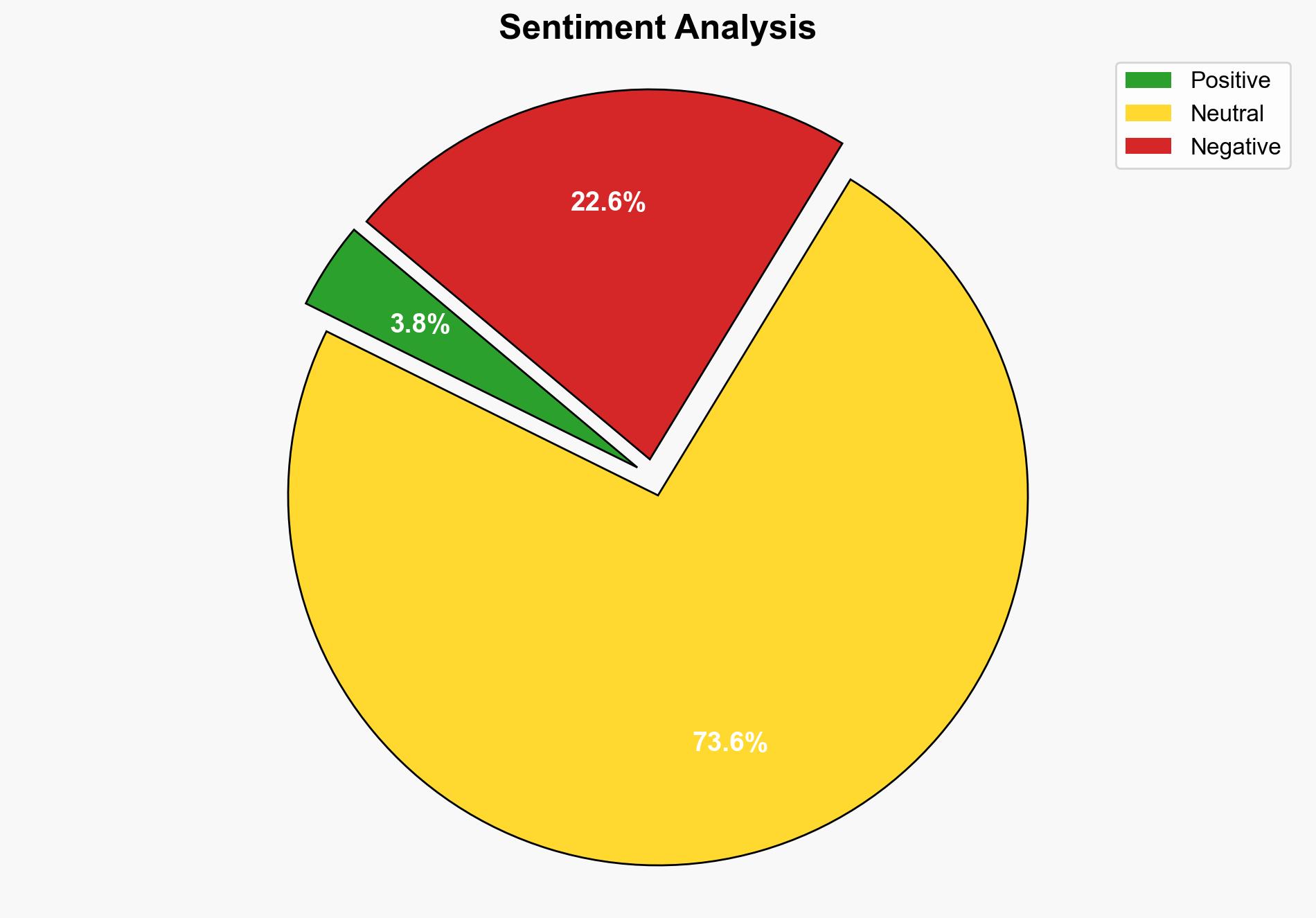
The most supported hypothesis is that Operation Firewall represents a significant law enforcement effort to dismantle a network of individuals involved in child pornography and exploitation across Massachusetts. The operation’s success highlights the effectiveness of coordinated law enforcement actions but also underscores the persistent threat of child exploitation networks. Confidence Level: Moderate. Recommended action includes enhancing inter-agency collaboration and public awareness campaigns to prevent future exploitation.
2. Competing Hypotheses
Hypothesis 1: Operation Firewall is a targeted and successful law enforcement initiative that has effectively disrupted a significant network of child exploitation offenders in Massachusetts. This hypothesis is supported by the comprehensive list of arrests across multiple jurisdictions, indicating a coordinated and extensive operation.
Hypothesis 2: Operation Firewall, while successful in making arrests, may not significantly impact the broader network of child exploitation due to the decentralized and adaptive nature of these networks. This hypothesis considers the possibility that these arrests are only a fraction of a larger, more resilient network.
Hypothesis 1 is more likely given the scale and coordination of the operation, but Hypothesis 2 cannot be discounted due to the inherent challenges in dismantling such networks completely.
3. Key Assumptions and Red Flags
Assumptions: The operation was based on reliable intelligence that accurately identified individuals involved in child exploitation. The legal process will result in convictions that deter future offenses.
Red Flags: Potential for misidentification or wrongful arrests. The possibility of operational leaks or insider threats that could compromise future operations.
4. Implications and Strategic Risks
The operation may lead to temporary disruption of child exploitation activities in the region, but there is a risk of networks adapting and relocating. Politically, successful operations can bolster public trust in law enforcement but also raise concerns about privacy and civil liberties. Cyber risks include potential retaliation by offenders through hacking or data breaches. Economically, increased resources may be required for ongoing surveillance and prosecution efforts.
5. Recommendations and Outlook
- Enhance inter-agency collaboration and intelligence sharing to maintain pressure on child exploitation networks.
- Implement public awareness campaigns to educate communities about the signs of exploitation and how to report it.
- Best-case scenario: Sustained law enforcement efforts lead to a significant reduction in child exploitation cases.
- Worst-case scenario: Networks adapt and continue operations, potentially increasing their sophistication and reach.
- Most-likely scenario: Continued arrests and prosecutions with gradual impact on reducing exploitation activities.
6. Key Individuals and Entities
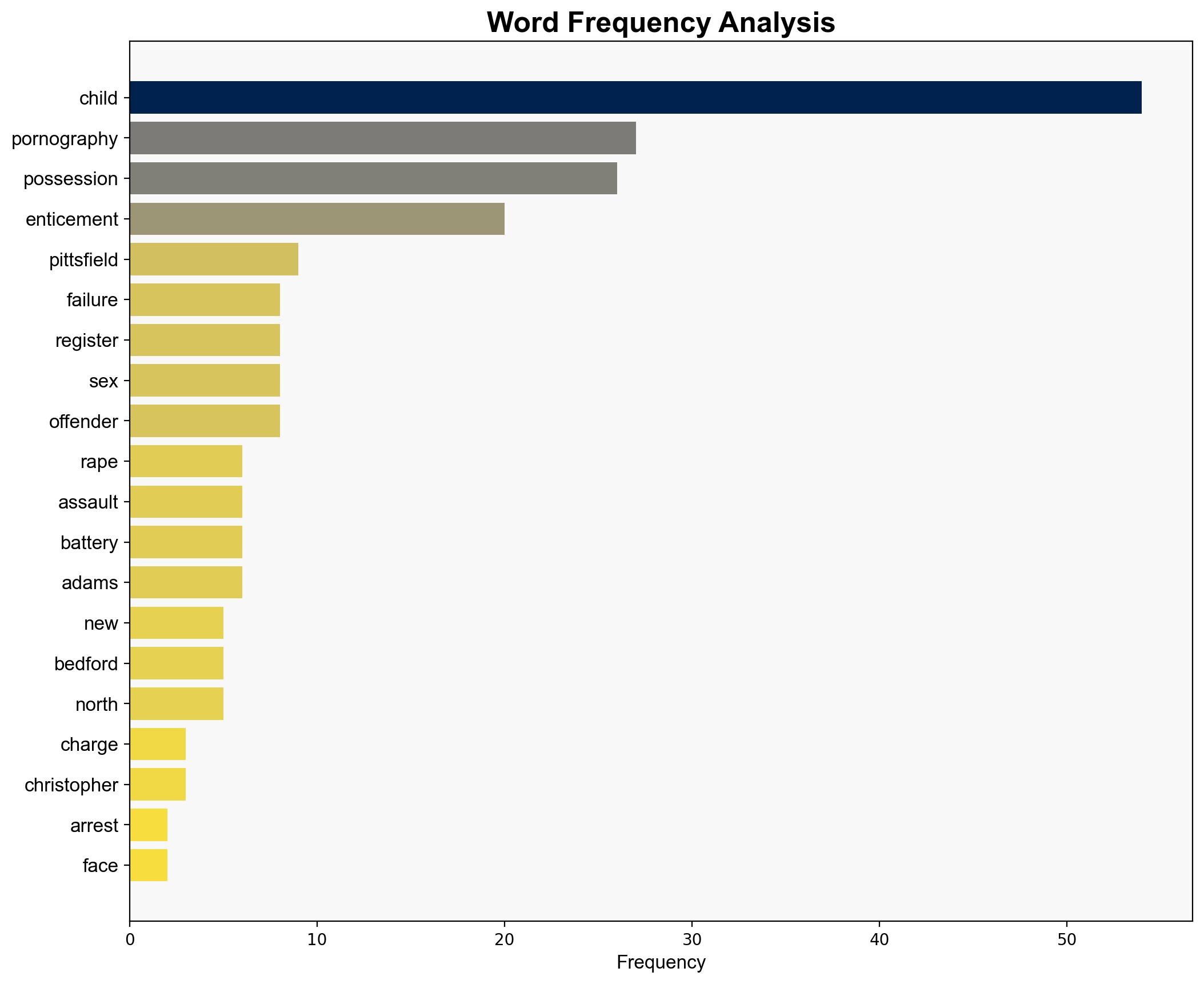
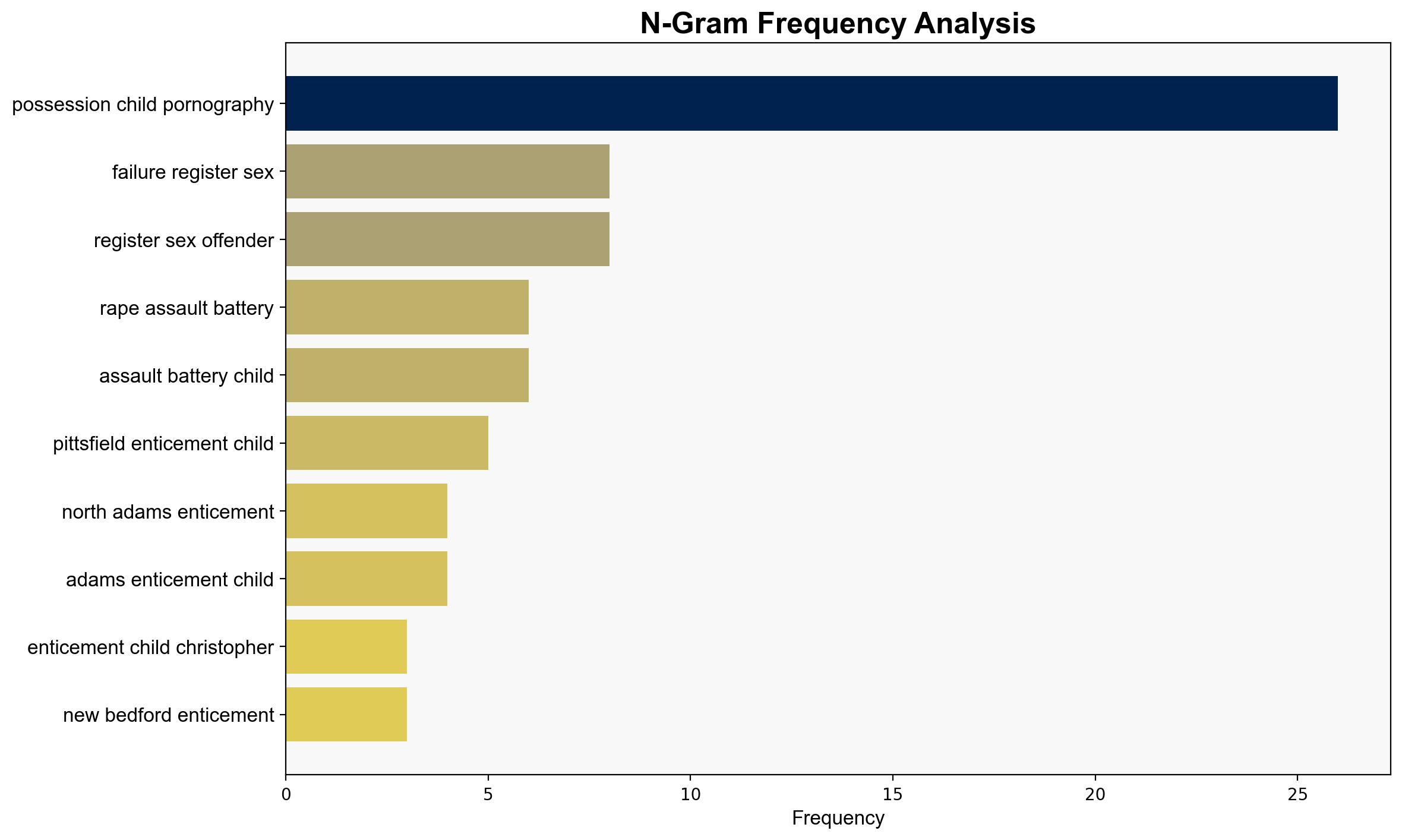
Alejandro Busby Bosch, Ronald Aman, William Connors, Brian Lindelof, Tyler Steven, Orlando Bernier, Matheus Kennedy Menese Bicalho, Elliot Oullette Cormier, Alexander Ventura, Daniel Torre, William McNeil, Rebekah McCoy, Joseph Constantino, Tony Leng, Griffen Larkin, Noah Adams, Graham Symon, Jarod Chmielewski, Matthew Thompson, Trent Kelley, Keith Cheverie, Parker Huggins, Daniel Cruz, Christian Deschene, Kevin Dorvilien, Thomas Dolan, Christopher Coleman, Manuel Lopez Santiago, Kevin Derosa, James Gevry, Jar Tracey, Fabio Deamaral, Theron Carmean, Jhon Tafur, Joseph Gagnon, Zack Comstock, Christopher Tague, Dononeil Nebar, Thomas Kushi, Michael Reu, Jason Hadsell, Robert Sabin, Bernard Jordon, Zachary Grchan, Christopher Morin, Henry Glazi, Draw Kelly, Raymond Martin, Michael Page, Wayne Bingle, George Wetherell.
7. Thematic Tags
Cybersecurity, Law Enforcement, Child Exploitation, Public Safety
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology