6 ways to level up your home network’s privacy – for free – ZDNet
Published on: 2025-11-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 6 ways to level up your home network’s privacy – for free – ZDNet
1. BLUF (Bottom Line Up Front)
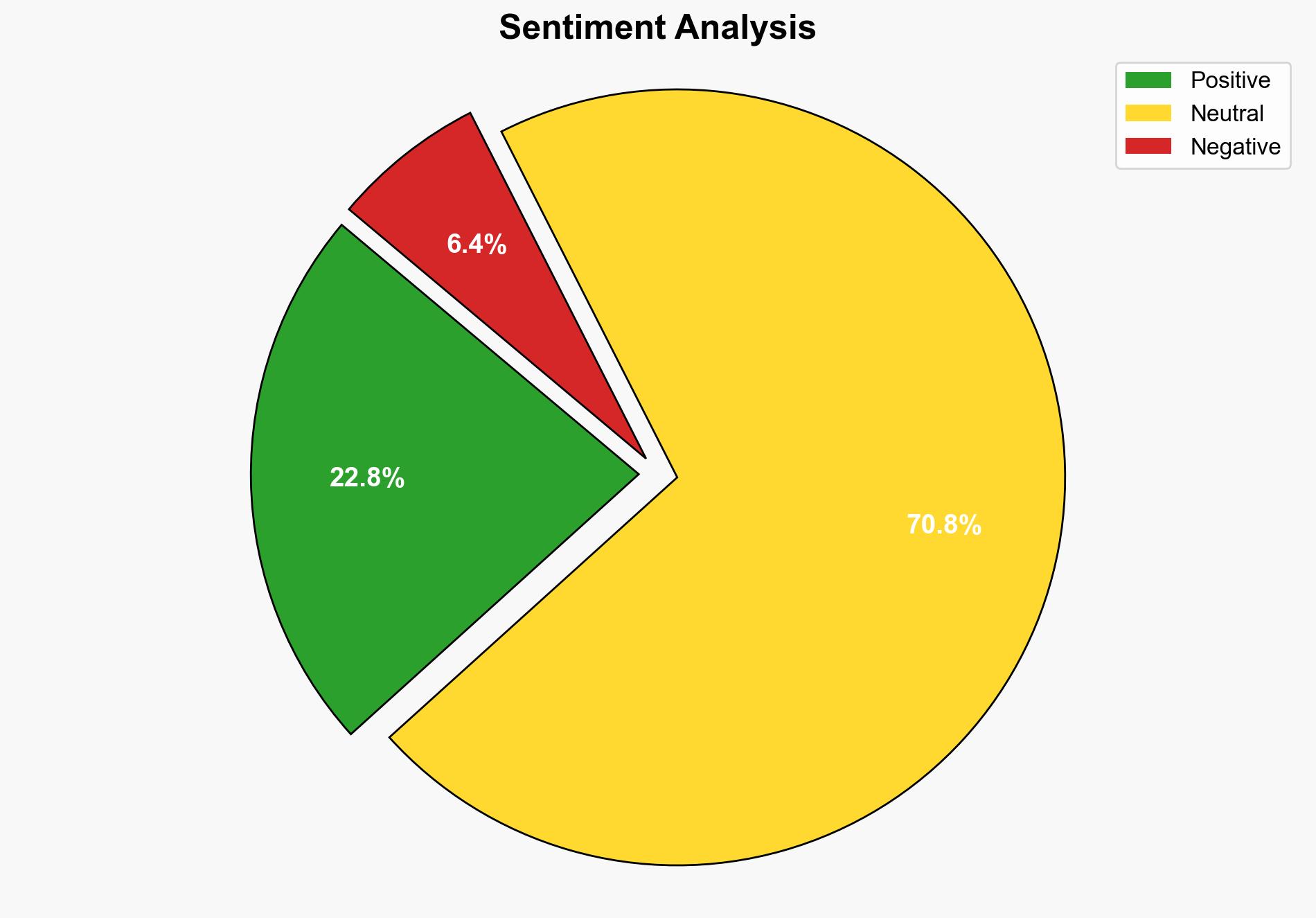
The most supported hypothesis is that the article’s recommendations are primarily aimed at enhancing individual user privacy through accessible and cost-free methods, with a moderate confidence level. The recommended action is to adopt a comprehensive approach to network security by implementing multiple layers of privacy-enhancing tools and practices.
2. Competing Hypotheses
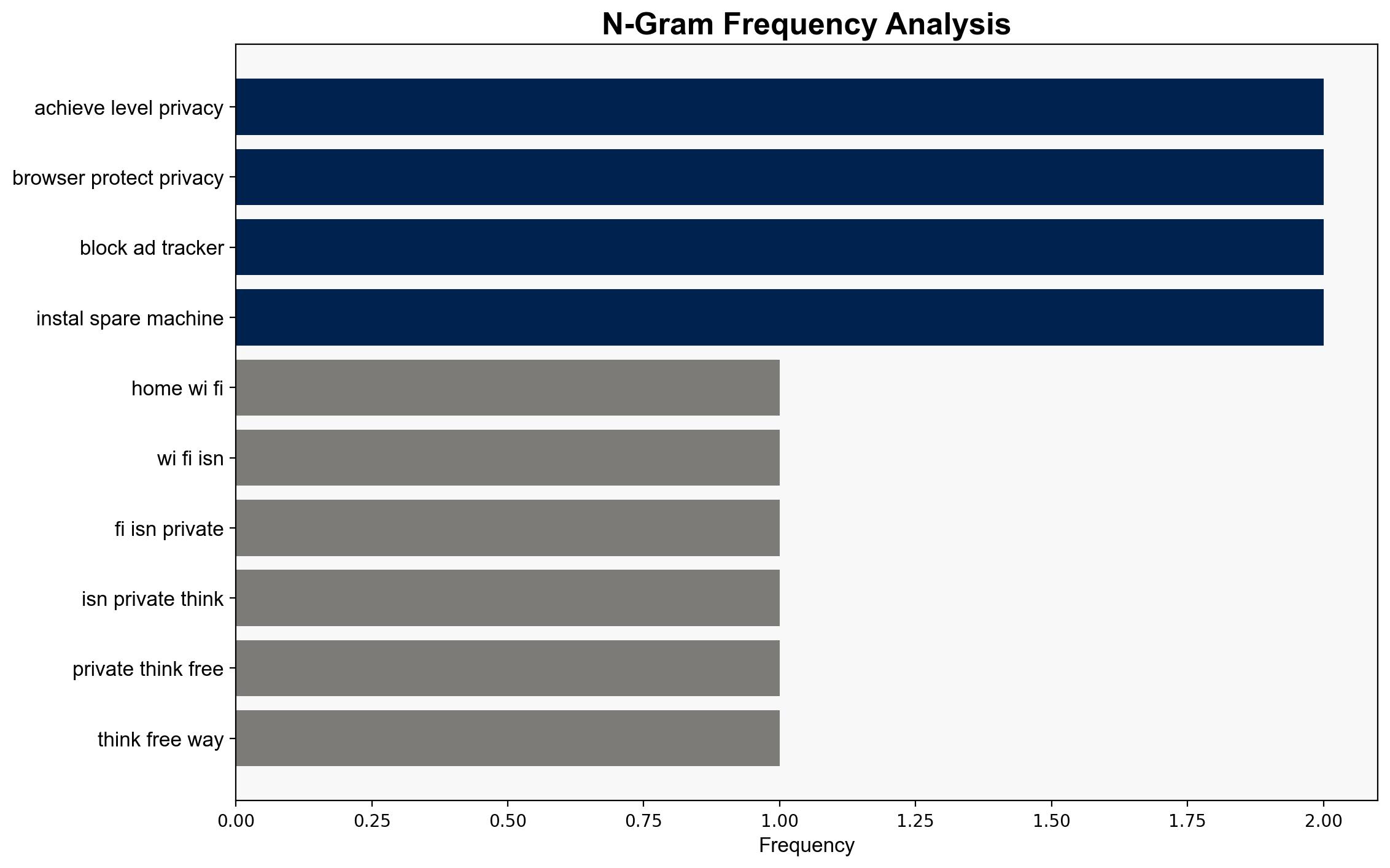
Hypothesis 1: The article provides effective, free methods to significantly enhance home network privacy by leveraging existing tools and practices.
Hypothesis 2: The article’s recommendations, while useful, offer limited privacy improvements due to inherent vulnerabilities in consumer-grade networks and devices.
Hypothesis 1 is more likely, as the article outlines practical steps that, if implemented correctly, can improve privacy. However, the effectiveness is contingent on user diligence and the inherent limitations of consumer technology.
3. Key Assumptions and Red Flags
Assumptions: Users have the technical capability to implement the suggested measures. The tools and practices mentioned are compatible with users’ existing devices and networks.
Red Flags: Over-reliance on free tools may lead to a false sense of security. The article does not address potential vulnerabilities in the tools themselves or evolving cyber threats.
4. Implications and Strategic Risks
While the recommendations can enhance privacy, they may not fully protect against sophisticated cyber threats. Users may face risks from evolving malware, phishing attacks, and zero-day vulnerabilities. Additionally, the reliance on free tools could expose users to data collection practices by the tool providers themselves.
5. Recommendations and Outlook
- Actionable Steps: Users should implement a layered security approach, combining the article’s recommendations with paid, professional-grade security solutions where feasible.
- Best Scenario: Users achieve enhanced privacy and security, reducing exposure to common cyber threats.
- Worst Scenario: Users experience a breach due to over-reliance on free tools and lack of comprehensive security measures.
- Most-likely Scenario: Users see moderate improvements in privacy but remain vulnerable to advanced threats without additional security investments.
6. Key Individuals and Entities
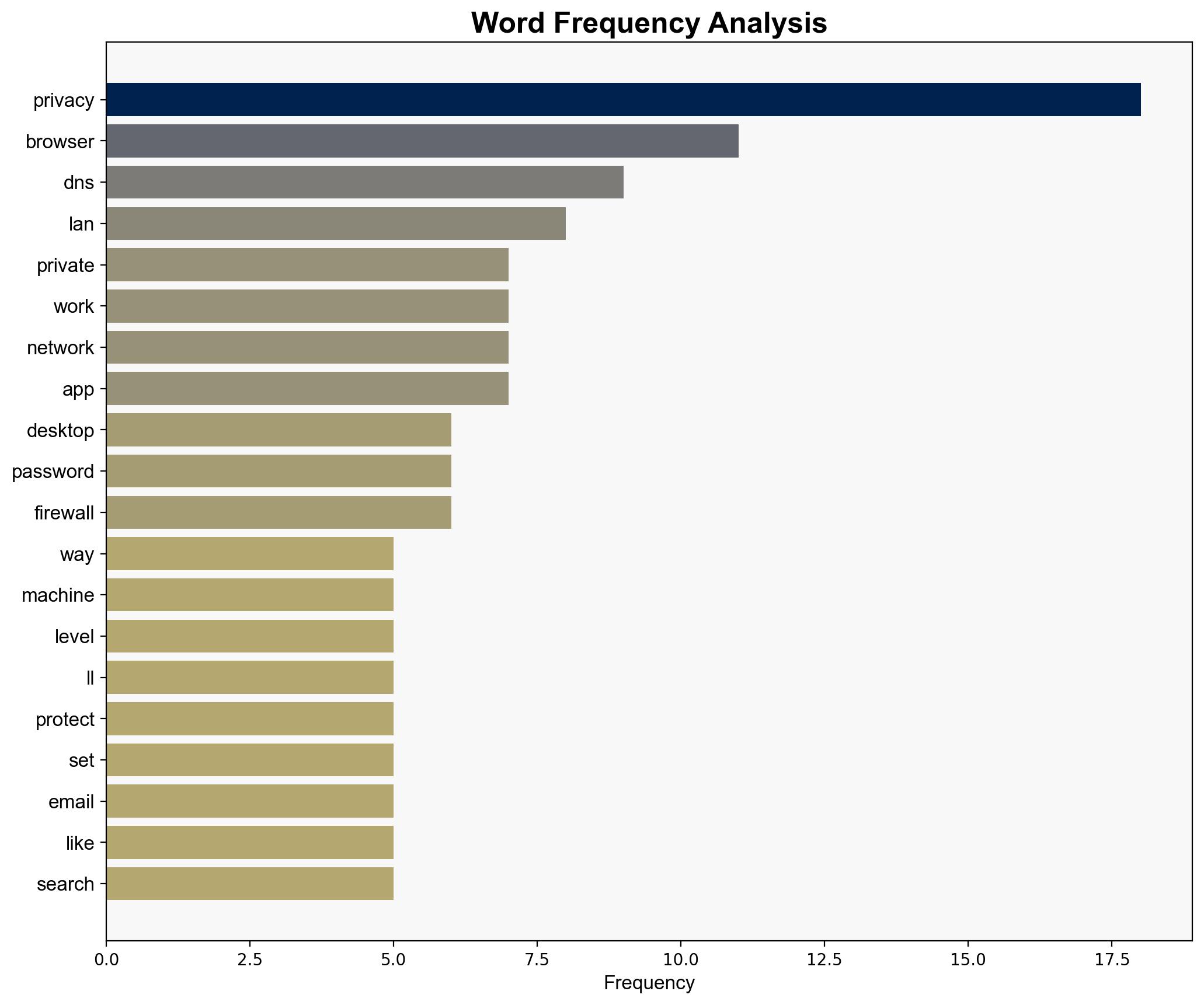
The article does not mention specific individuals. Entities include ZDNet as the source and various privacy-focused tools such as Brave, DuckDuckGo, Tor, Signal, and ProtonMail.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology