Australia’s spy chief accuses China of targeting key infrastructure – BBC News
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Australia’s spy chief accuses China of targeting key infrastructure – BBC News
1. BLUF (Bottom Line Up Front)
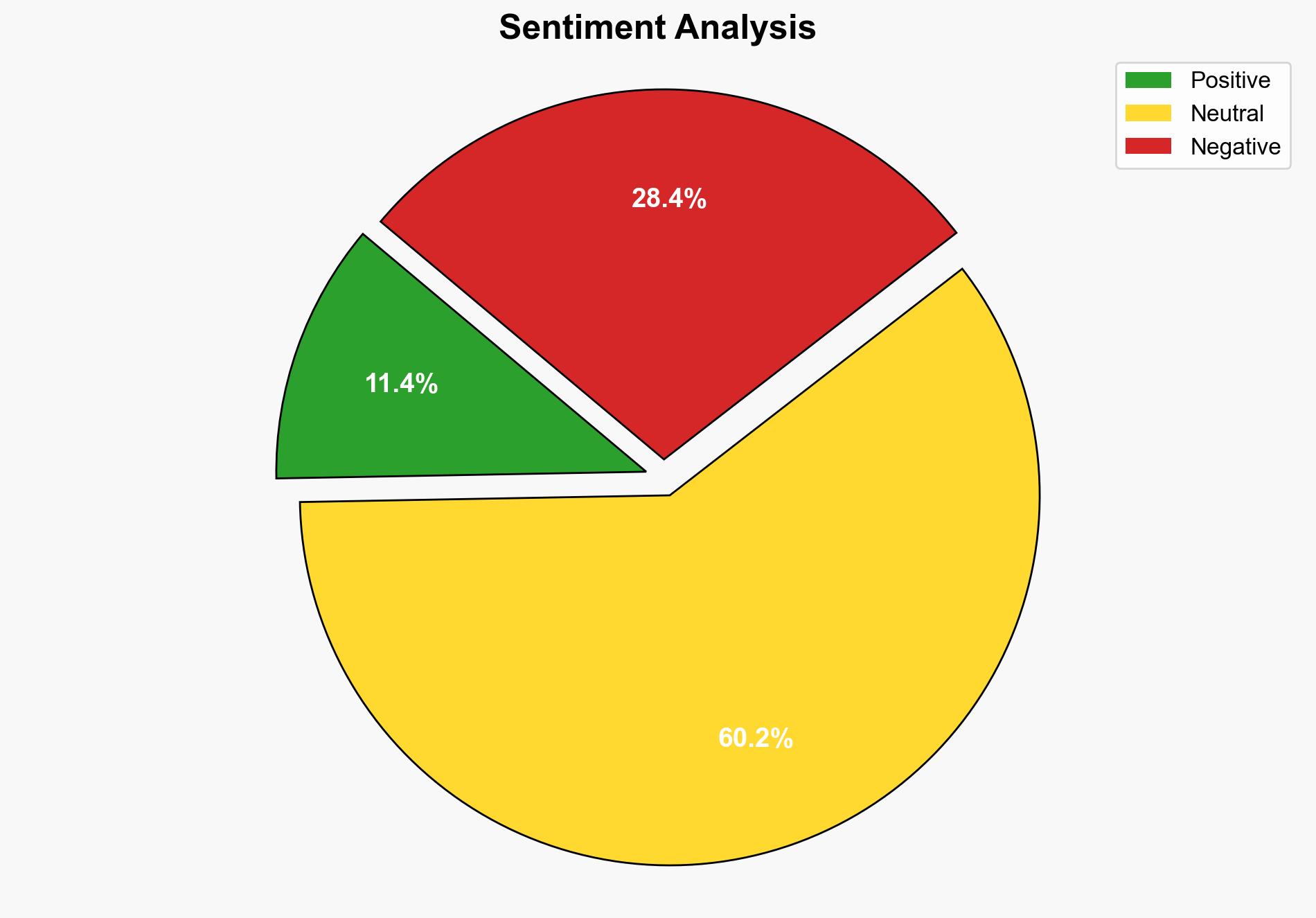
There is a high likelihood that China is engaging in cyber operations targeting Australia’s critical infrastructure, posing a significant national security threat. The most supported hypothesis is that these actions are part of a broader strategic effort by China to undermine Australia’s economic stability and national security. Confidence Level: High. Recommended action includes enhancing cybersecurity defenses, increasing intelligence sharing with allies, and diplomatic engagement with China to address these concerns.
2. Competing Hypotheses
Hypothesis 1: China is actively targeting Australia’s critical infrastructure as part of a strategic campaign to weaken Australia’s national security and economic stability. This is supported by the pattern of cyber intrusions, the sophistication of the attacks, and the strategic value of the targeted sectors.
Hypothesis 2: The cyber activities attributed to China are the actions of independent hacker groups with loose affiliations to the Chinese government, acting out of self-interest rather than state-directed strategy. This hypothesis considers the possibility of non-state actors leveraging state-level tools for personal gain.
Hypothesis 1 is more likely given the consistent attribution of these activities to Chinese state-linked groups and the strategic alignment with China’s broader geopolitical objectives.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the attribution to China is accurate and that the cyber activities are state-sponsored. It is also assumed that the Australian spy chief’s statements are based on credible intelligence.
Red Flags: Potential bias in attributing all cyber activities to China without considering other actors. The possibility of misattribution due to sophisticated false flag operations.
Deception Indicators: The lack of direct evidence linking the Chinese government to specific incidents could indicate an attempt to obfuscate the true source of the attacks.
4. Implications and Strategic Risks
The targeting of critical infrastructure poses significant risks, including potential disruption of essential services, economic damage, and heightened political tensions. Escalation scenarios include retaliatory cyber operations by Australia or its allies, increased diplomatic friction, and potential economic sanctions. The strategic risk extends to undermining public trust in government and critical systems, potentially sowing social discord.
5. Recommendations and Outlook
- Enhance cybersecurity measures across critical infrastructure sectors, including regular penetration testing and threat intelligence sharing.
- Strengthen diplomatic channels with China to address cyber concerns and establish norms for state behavior in cyberspace.
- Increase collaboration with international allies to develop a coordinated response to cyber threats.
- Best-case scenario: Diplomatic engagement leads to a reduction in cyber activities and improved bilateral relations.
- Worst-case scenario: Continued cyber operations lead to significant infrastructure disruption and economic damage, escalating into broader geopolitical conflict.
- Most-likely scenario: Persistent low-level cyber activities continue, requiring ongoing vigilance and adaptation of defensive measures.
6. Key Individuals and Entities
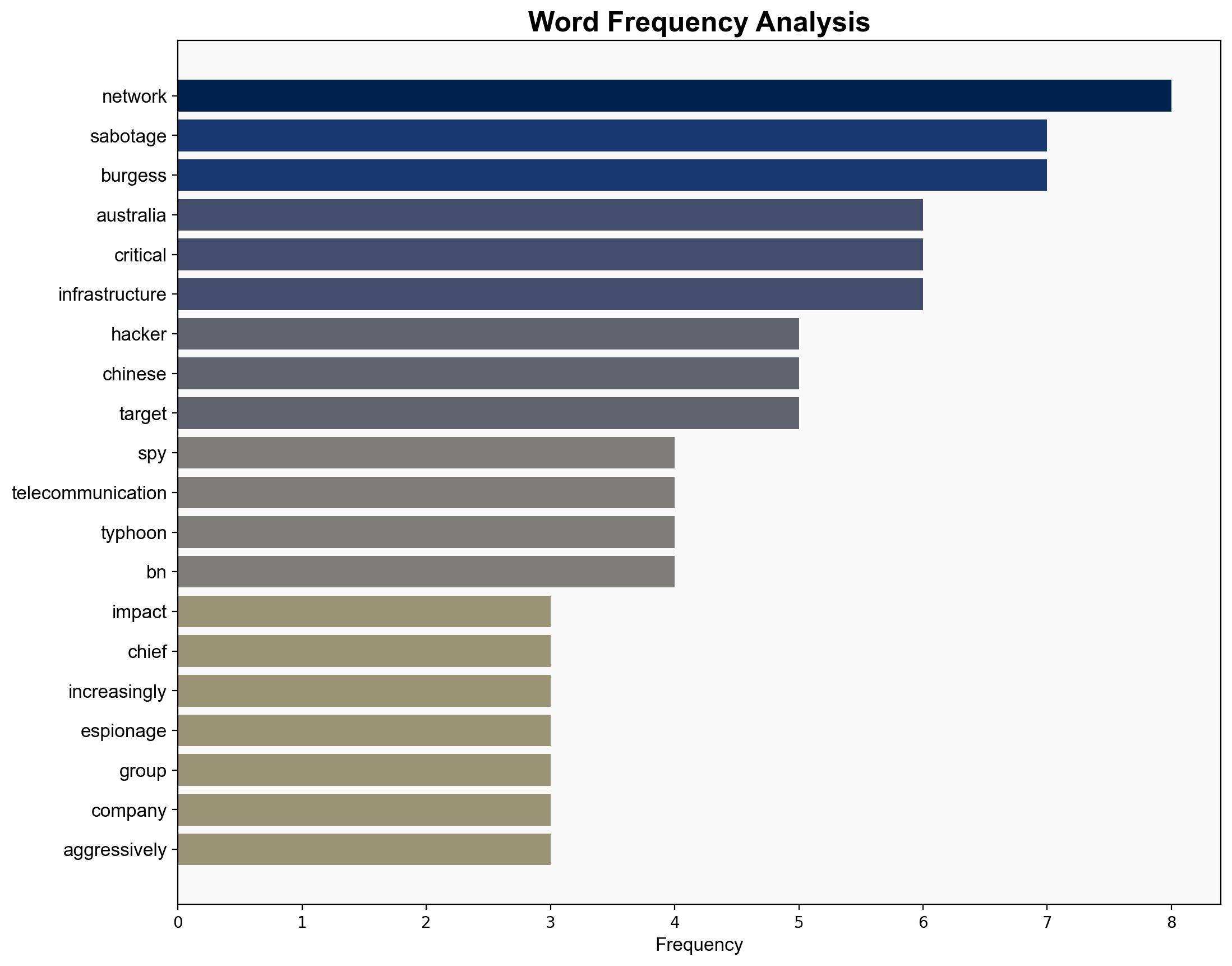
Mike Burgess – Head of the Australian Security Intelligence Organisation (ASIO)
Chinese hacker groups – Salt Typhoon, Volt Typhoon
7. Thematic Tags
National Security Threats
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Methodology