Active Directory Under Siege Why Critical Infrastructure Needs Stronger Security – Internet
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Active Directory Under Siege Why Critical Infrastructure Needs Stronger Security – Internet
1. BLUF (Bottom Line Up Front)
With a high confidence level, the most supported hypothesis is that the complexity and hybrid nature of modern Active Directory (AD) environments significantly increase the vulnerability of critical infrastructure to cyberattacks. It is recommended that organizations implement comprehensive security measures, including enhanced authentication protocols and regular audits, to mitigate these risks.
2. Competing Hypotheses
Hypothesis 1: The complexity and hybrid nature of AD environments are the primary factors making them vulnerable to cyberattacks.
Hypothesis 2: The vulnerabilities in AD are primarily due to inadequate security practices and outdated protocols rather than the complexity of the infrastructure.
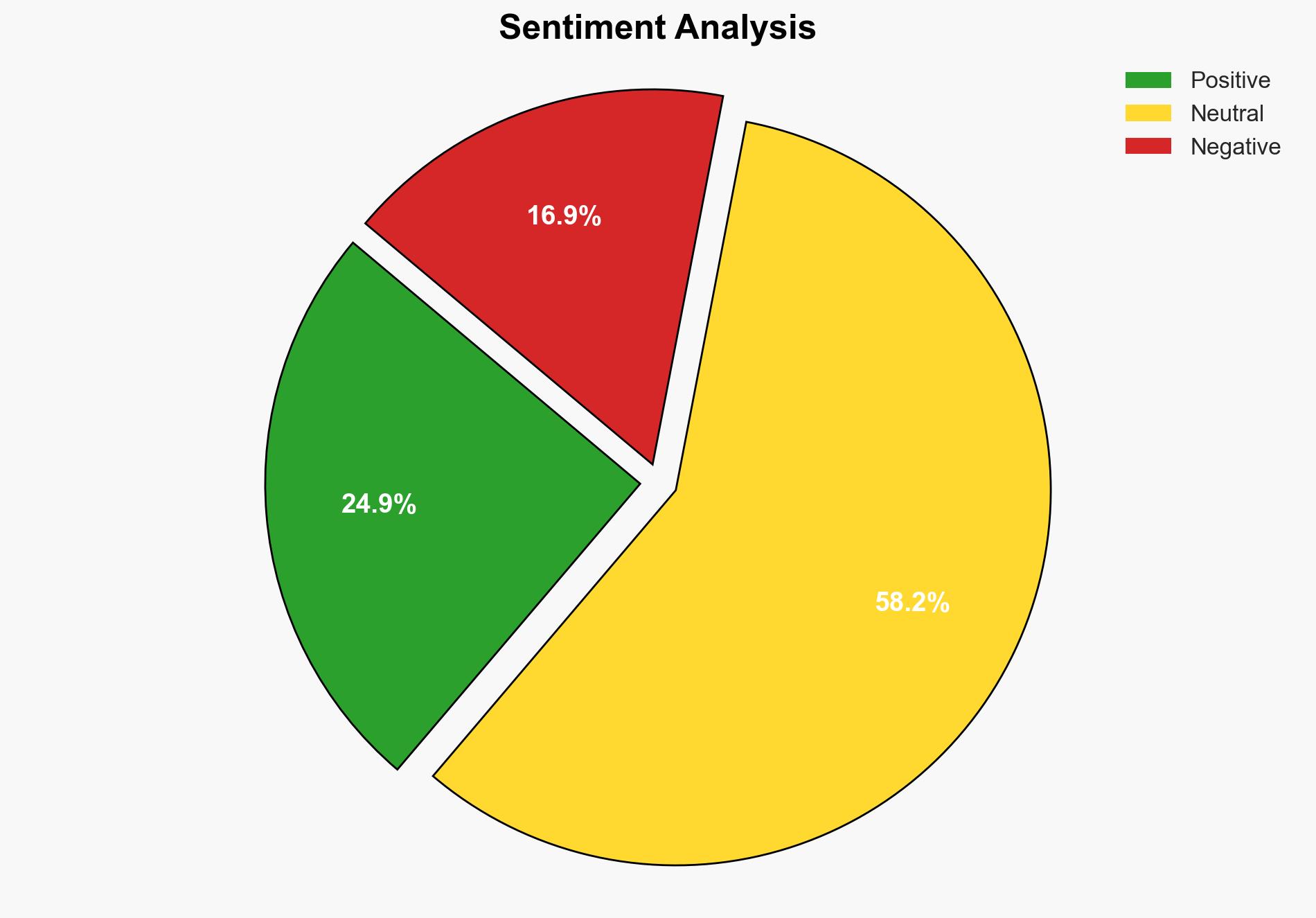
Hypothesis 1 is more likely due to the evidence of increased attack surfaces and synchronization challenges in hybrid environments, as well as the exploitation of legacy protocols. However, Hypothesis 2 cannot be entirely dismissed, as poor security practices and weak password policies also contribute significantly to vulnerabilities.
3. Key Assumptions and Red Flags
Assumptions include the belief that organizations are not fully aware of the vulnerabilities inherent in their hybrid AD environments. A red flag is the potential underestimation of the threat posed by legacy protocols and synchronization mechanisms. Deception indicators could include attackers using legitimate-looking operations to mask their activities.
4. Implications and Strategic Risks
The primary strategic risk is the potential for widespread disruption of critical infrastructure services, such as healthcare, due to AD compromises. This could lead to economic losses, reputational damage, and increased regulatory scrutiny. Escalation scenarios include coordinated cyberattacks targeting multiple sectors simultaneously, leveraging compromised AD systems.
5. Recommendations and Outlook
- Implement multi-factor authentication and regularly update security protocols to mitigate risks.
- Conduct regular audits and penetration testing to identify and address vulnerabilities.
- Best-case scenario: Organizations successfully strengthen their AD security, reducing the risk of major breaches.
- Worst-case scenario: A major cyberattack on critical infrastructure leads to significant service disruptions and financial losses.
- Most-likely scenario: Incremental improvements in AD security reduce the frequency and impact of breaches over time.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Key entities include organizations with hybrid AD environments, cybersecurity teams, and threat actors targeting AD systems.
7. Thematic Tags
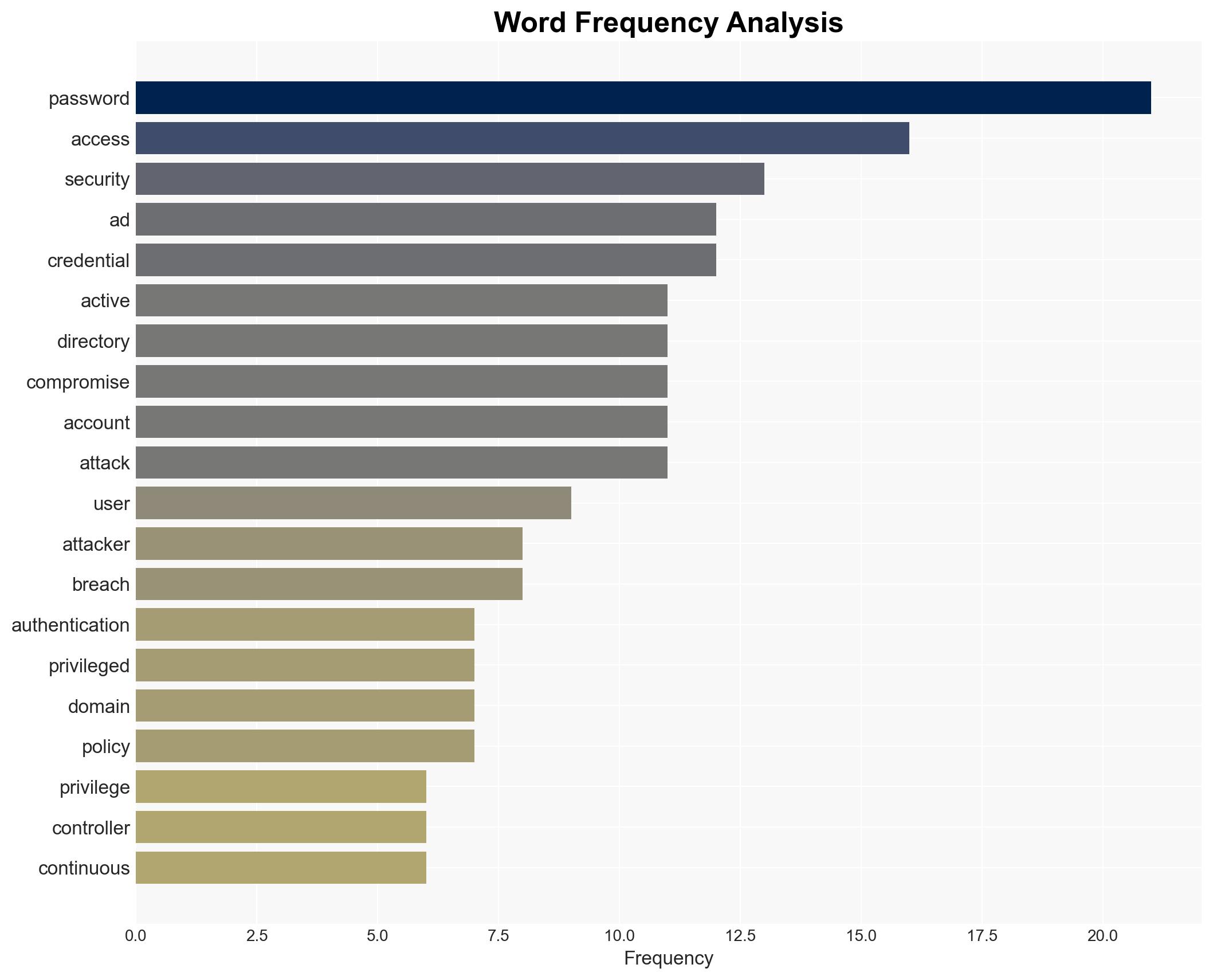
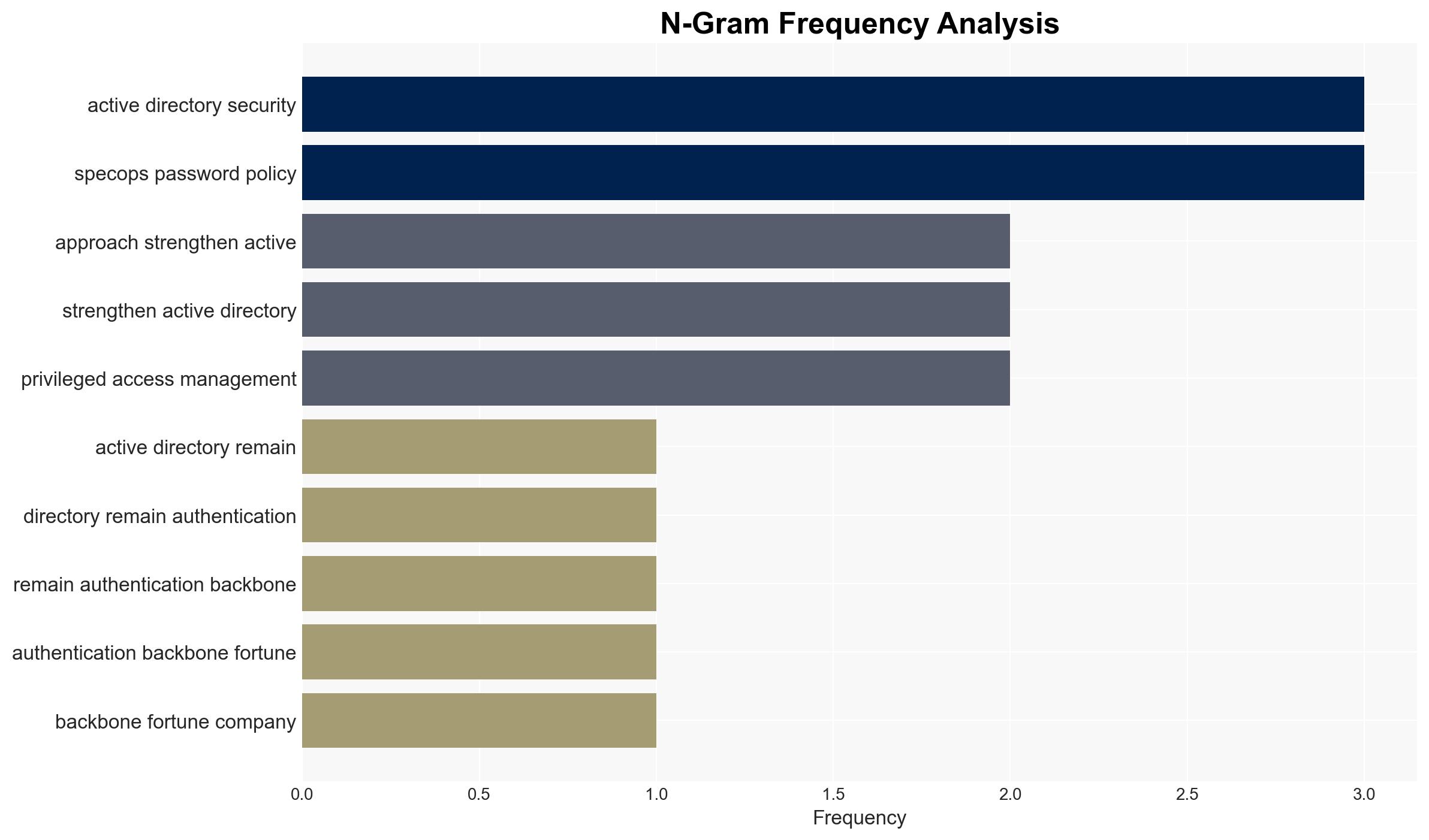
Cybersecurity, Active Directory, Critical Infrastructure, Hybrid Cloud, Authentication
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology