Hackers Use KakaoTalk and Google Find Hub in Android Spyware Attack – HackRead
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers Use KakaoTalk and Google Find Hub in Android Spyware Attack – HackRead
1. BLUF (Bottom Line Up Front)
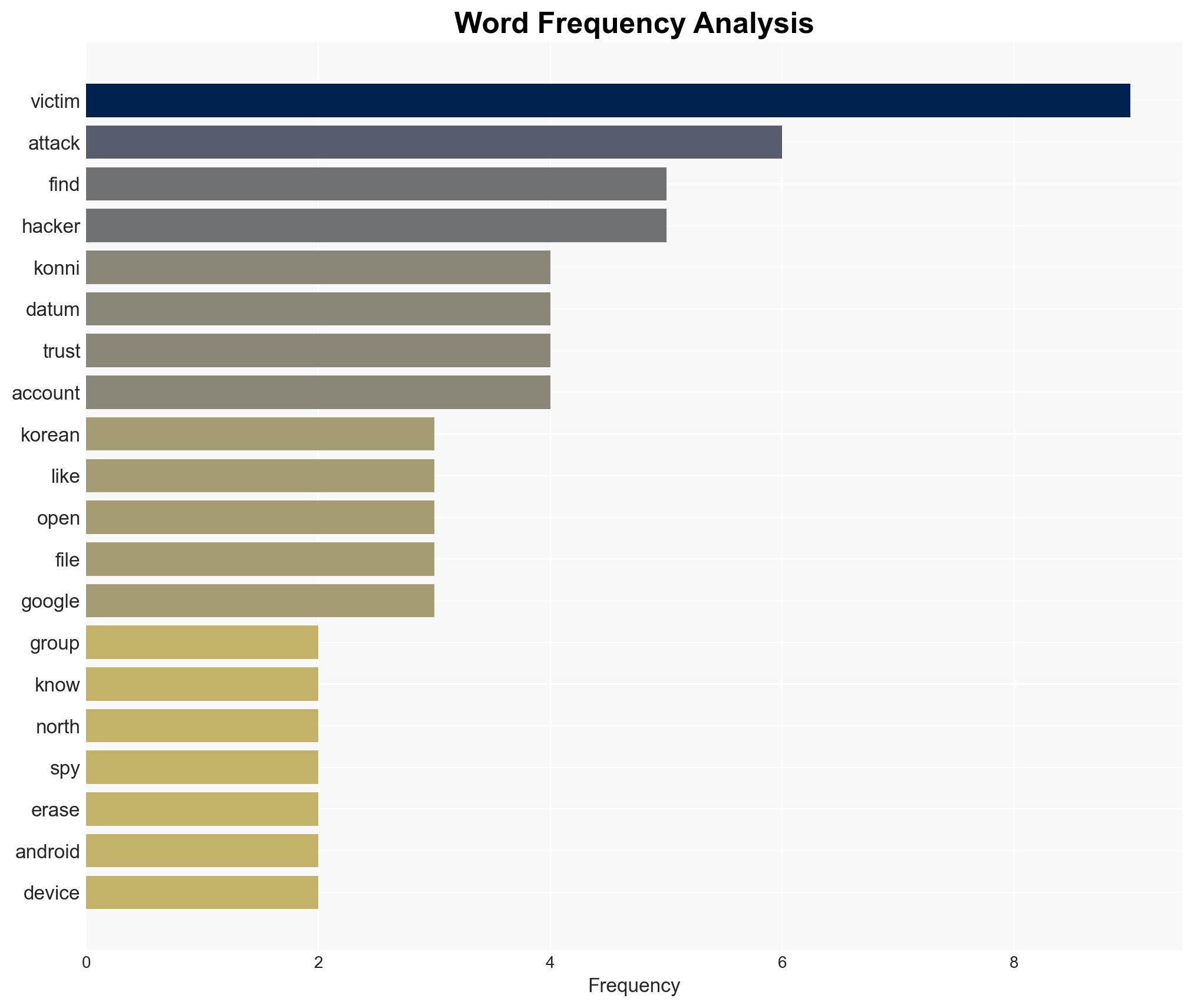
There is a high likelihood that the hacking group known as Konni, suspected to be linked to the North Korean regime, is conducting a sophisticated cyber-espionage campaign targeting South Korean individuals and entities. The campaign leverages trusted platforms like KakaoTalk and Google Find Hub to execute spyware attacks. Strategic recommendations include enhancing cybersecurity measures, particularly focusing on user education and implementing multi-factor authentication.
2. Competing Hypotheses
Hypothesis 1: The Konni group, with ties to North Korea, is behind the cyber-espionage campaign targeting South Korean users via KakaoTalk and Google Find Hub.
Hypothesis 2: An independent cybercriminal group, unaffiliated with any state actor, is exploiting the geopolitical tensions between North and South Korea to conduct financially motivated attacks.
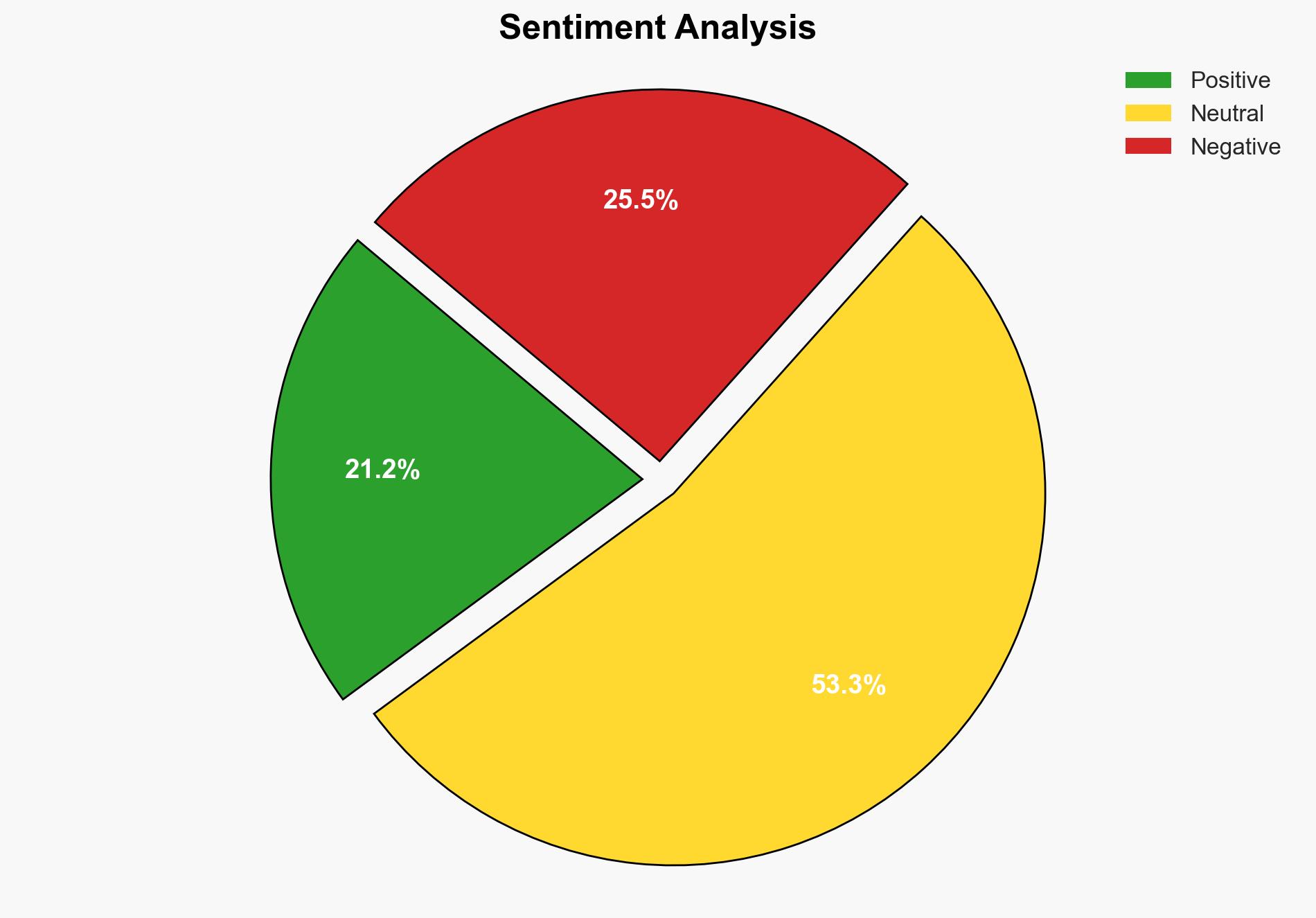
Assessment: Hypothesis 1 is more likely due to the sophisticated nature of the attack, the strategic targeting of South Korean entities, and the historical pattern of North Korean cyber operations. Hypothesis 2 is less likely given the lack of direct financial gain and the complexity of the operation.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the Konni group has the capability and intent to conduct such operations. The use of local platforms like KakaoTalk suggests a deep understanding of the regional digital landscape.
Red Flags: The impersonation of trusted roles such as psychological counselors and tax service staff indicates a high level of social engineering skill, which is a hallmark of state-sponsored operations.
Deception Indicators: The potential for false flag operations exists, where another actor could mimic North Korean tactics to mislead attribution.
4. Implications and Strategic Risks
The attack could escalate cyber tensions between North and South Korea, potentially leading to retaliatory cyber operations. Economically, compromised data could impact businesses and governmental operations, leading to financial losses. Informationally, the attack undermines trust in digital communications and platforms, which could have broader societal impacts.
5. Recommendations and Outlook
- Actionable Steps: Increase awareness and training on phishing and social engineering tactics. Implement multi-factor authentication for all sensitive accounts. Regularly update and patch systems to mitigate vulnerabilities.
- Best Scenario: Enhanced security measures prevent further breaches, and diplomatic channels reduce cyber tensions.
- Worst Scenario: Continued attacks lead to significant data breaches and escalate into broader cyber conflict.
- Most-likely Scenario: Sporadic attacks continue, with incremental improvements in cybersecurity posture mitigating some risks.
6. Key Individuals and Entities
Konni Group: Suspected North Korean-linked hacking group.
Genians Security Center (GSC): The research firm that identified the attack chain.
7. Thematic Tags
Regional Focus: South Korea, North Korea
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
Explore more:
Regional Focus Briefs ·
Daily Summary ·
Methodology