Real Estate Giant Redfin Exposed Users Personal Info on Listing Contact Forms – The Intercept
Published on: 2025-11-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Real Estate Giant Redfin Exposed Users Personal Info on Listing Contact Forms – The Intercept
1. BLUF (Bottom Line Up Front)
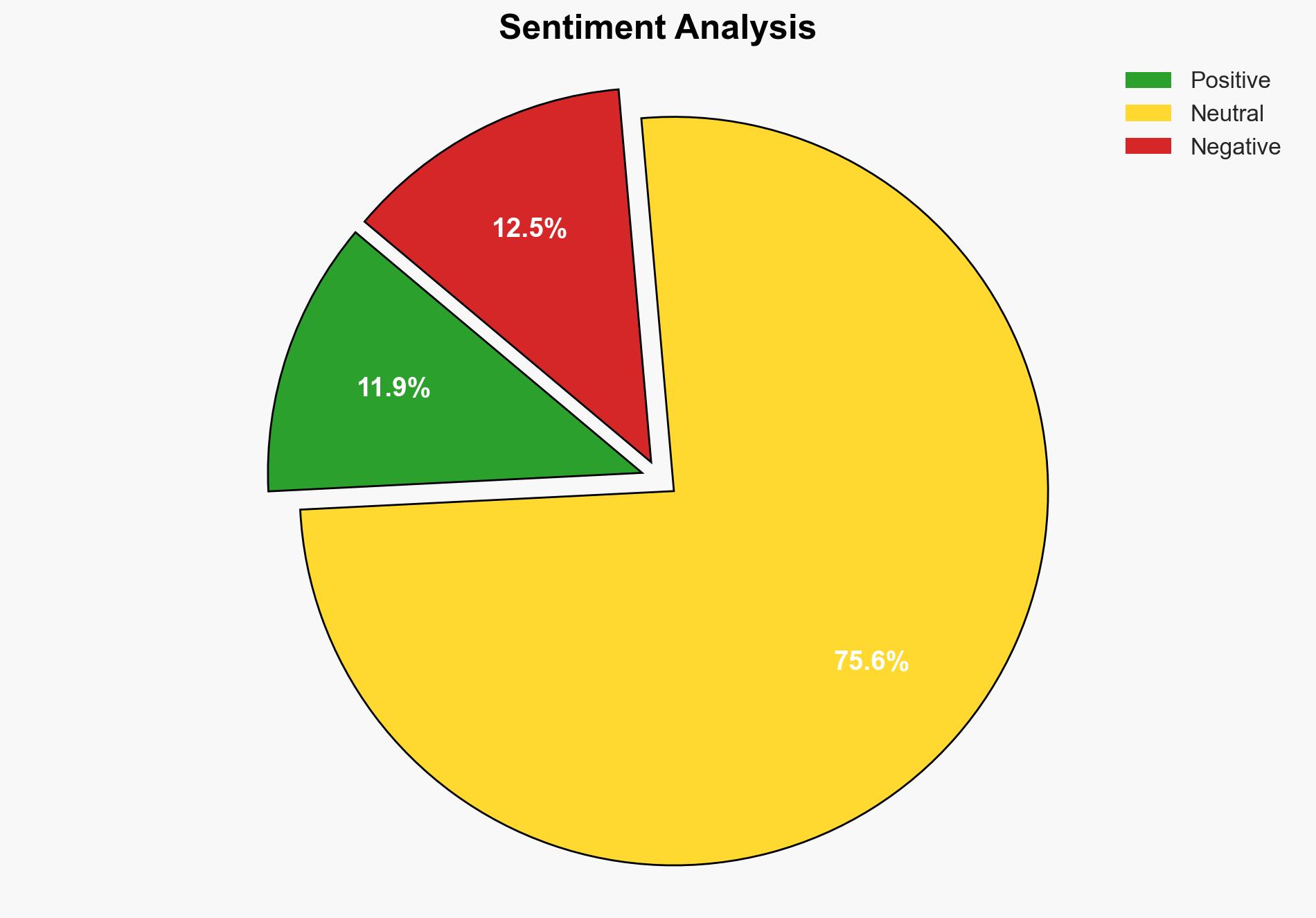
With moderate confidence, the most supported hypothesis is that the exposure of user data on Redfin’s platform was due to a technical oversight rather than a deliberate act of negligence or malicious intent. Immediate action is recommended to enhance Redfin’s cybersecurity protocols and transparency with users to mitigate reputational damage and prevent future vulnerabilities.
2. Competing Hypotheses
Hypothesis 1: The exposure of user data was due to a technical error in Redfin’s website design, specifically related to the handling of JavaScript and contact forms.
Hypothesis 2: The exposure resulted from a systemic issue within Redfin’s cybersecurity practices, potentially indicating broader vulnerabilities or negligence.
Hypothesis 1 is more likely due to the specificity of the error described (JavaScript handling) and the rapid response by Redfin to address the issue. Hypothesis 2 cannot be entirely ruled out but lacks direct evidence of systemic negligence or broader security failures.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that Redfin’s response to the issue was timely and effective based on the spokesperson’s statement. It is also assumed that the exposure was not exploited on a large scale.
Red Flags: The lack of detailed information on the scope of data exposure and the potential for further undisclosed vulnerabilities within Redfin’s systems.
Deception Indicators: The possibility that Redfin may underreport the extent of the issue to minimize reputational damage.
4. Implications and Strategic Risks
The primary risk is reputational damage to Redfin, which could lead to a loss of user trust and a decline in user engagement. There is also a potential for legal and regulatory scrutiny, particularly if user data was exploited. Cybersecurity threats could escalate if similar vulnerabilities exist across other parts of Redfin’s platform or if malicious actors target the platform following this exposure.
5. Recommendations and Outlook
- Conduct a comprehensive security audit of Redfin’s platform to identify and remediate any additional vulnerabilities.
- Enhance transparency with users by providing detailed updates on the incident and measures taken to prevent future occurrences.
- Implement regular cybersecurity training for Redfin’s development and IT teams to prevent similar issues.
- Best-case scenario: Redfin successfully mitigates the issue, restoring user trust and avoiding significant legal repercussions.
- Worst-case scenario: Further vulnerabilities are discovered, leading to widespread data breaches and significant reputational and financial damage.
- Most-likely scenario: Redfin addresses the immediate issue, but faces ongoing scrutiny and the need for continued investment in cybersecurity improvements.
6. Key Individuals and Entities
Alina Ptaszynski (Redfin spokesperson)
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology