The new age of layered security from supply chains to endpoints – TechRadar
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The new age of layered security from supply chains to endpoints – TechRadar
1. BLUF (Bottom Line Up Front)
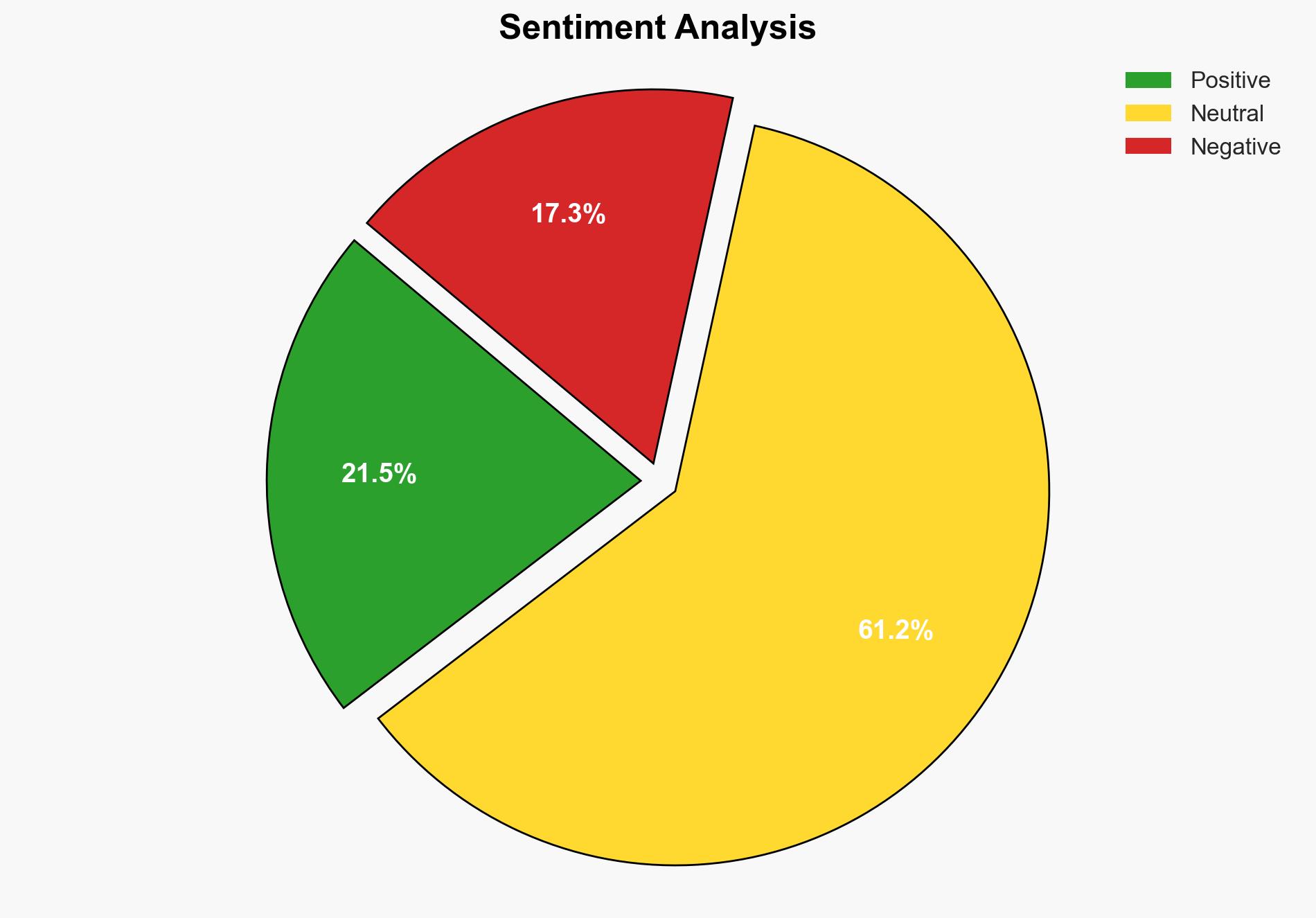
The most supported hypothesis is that organizations must adopt a comprehensive, layered security approach from supply chains to endpoints to mitigate rising cyber threats effectively. Confidence Level: Moderate. Recommended action includes enhancing supply chain security protocols and investing in endpoint protection technologies to ensure resilience against sophisticated cyber-attacks.
2. Competing Hypotheses
Hypothesis 1: The increase in cyber threats necessitates a comprehensive, layered security strategy from supply chains to endpoints to protect against sophisticated attacks.
Hypothesis 2: The current rise in cyber threats can be managed with existing security measures, focusing primarily on endpoint protection without significant changes to supply chain security.
Hypothesis 1 is more likely due to the increasing complexity and sophistication of cyber threats, which often exploit vulnerabilities at the supply chain level before reaching endpoints. The evidence suggests that traditional endpoint-focused security measures are insufficient against these advanced threats.
3. Key Assumptions and Red Flags
Assumptions: Organizations have the capability and resources to implement comprehensive security strategies. The threat landscape will continue to evolve, requiring adaptive security measures.
Red Flags: Potential over-reliance on technology without adequate human expertise. The possibility of underestimating the sophistication of supply chain attacks.
Deception Indicators: Overstated efficacy of certain security technologies without empirical evidence.
4. Implications and Strategic Risks
The failure to adopt a layered security approach could lead to significant data breaches, resulting in financial losses and reputational damage. In critical sectors like healthcare and utilities, the implications of a breach could be catastrophic, affecting public safety and national security. Escalation scenarios include increased geopolitical tensions if state actors exploit these vulnerabilities.
5. Recommendations and Outlook
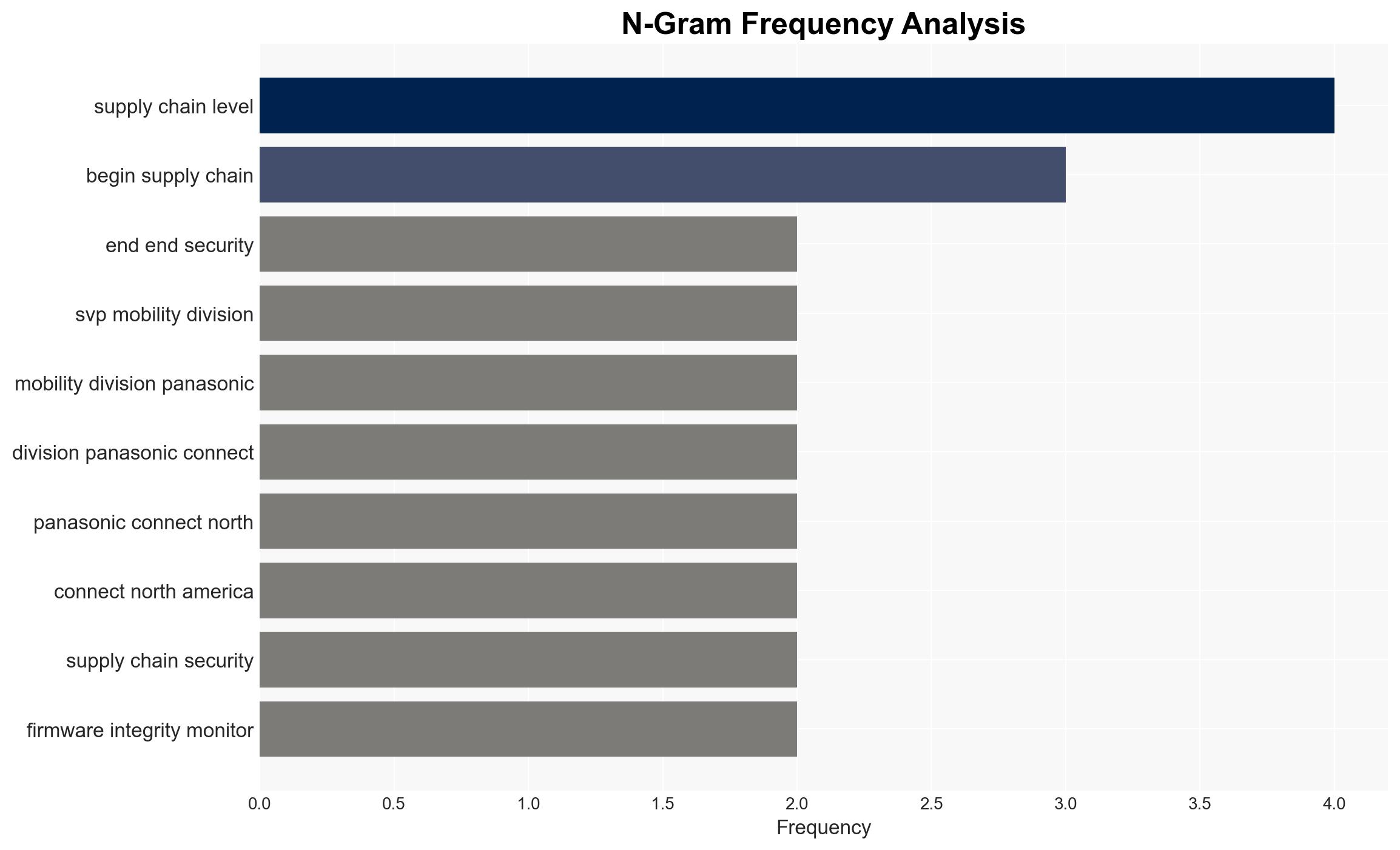
- Organizations should conduct thorough risk assessments of their supply chains and implement robust security protocols at every stage.
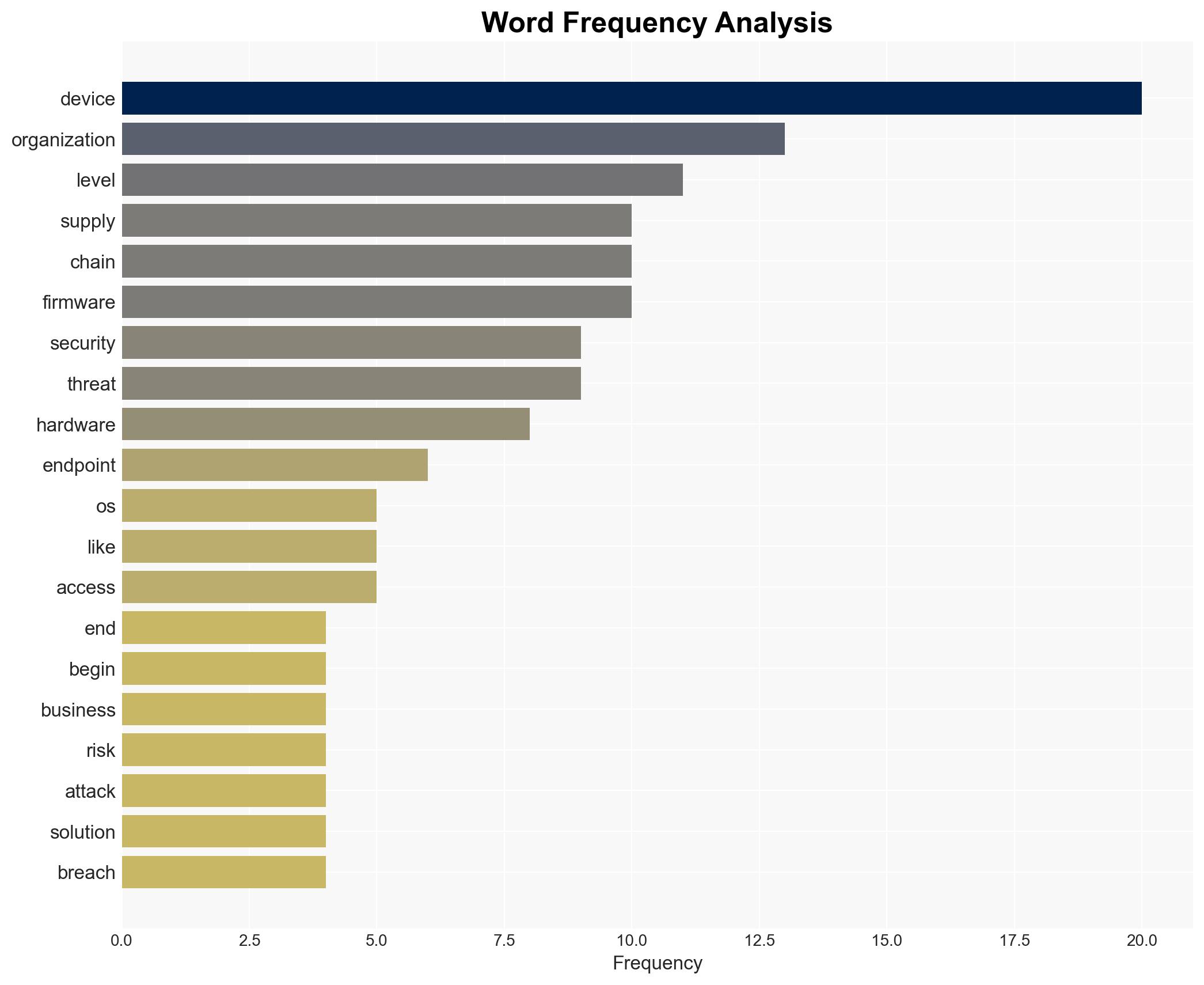
- Invest in advanced endpoint protection technologies that include hardware and firmware integrity monitoring.
- Enhance cybersecurity training programs to address the skill gap and ensure personnel are equipped to handle emerging threats.
Best-case scenario: Organizations successfully implement layered security strategies, reducing the incidence of breaches and enhancing overall resilience.
Worst-case scenario: A major supply chain breach leads to widespread disruption and significant economic and political fallout.
Most-likely scenario: Incremental improvements in security measures lead to a gradual reduction in successful cyber-attacks, but challenges persist due to the evolving threat landscape.
6. Key Individuals and Entities
SVP Mobility Division, Panasonic Connect North America.
7. Thematic Tags
Cybersecurity, Supply Chain Security, Endpoint Protection, Risk Management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·