GitHub Rolls Out Post-Quantum SSH Security to Protect Code from Future Threats – InfoQ.com
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: GitHub Rolls Out Post-Quantum SSH Security to Protect Code from Future Threats – InfoQ.com
1. BLUF (Bottom Line Up Front)
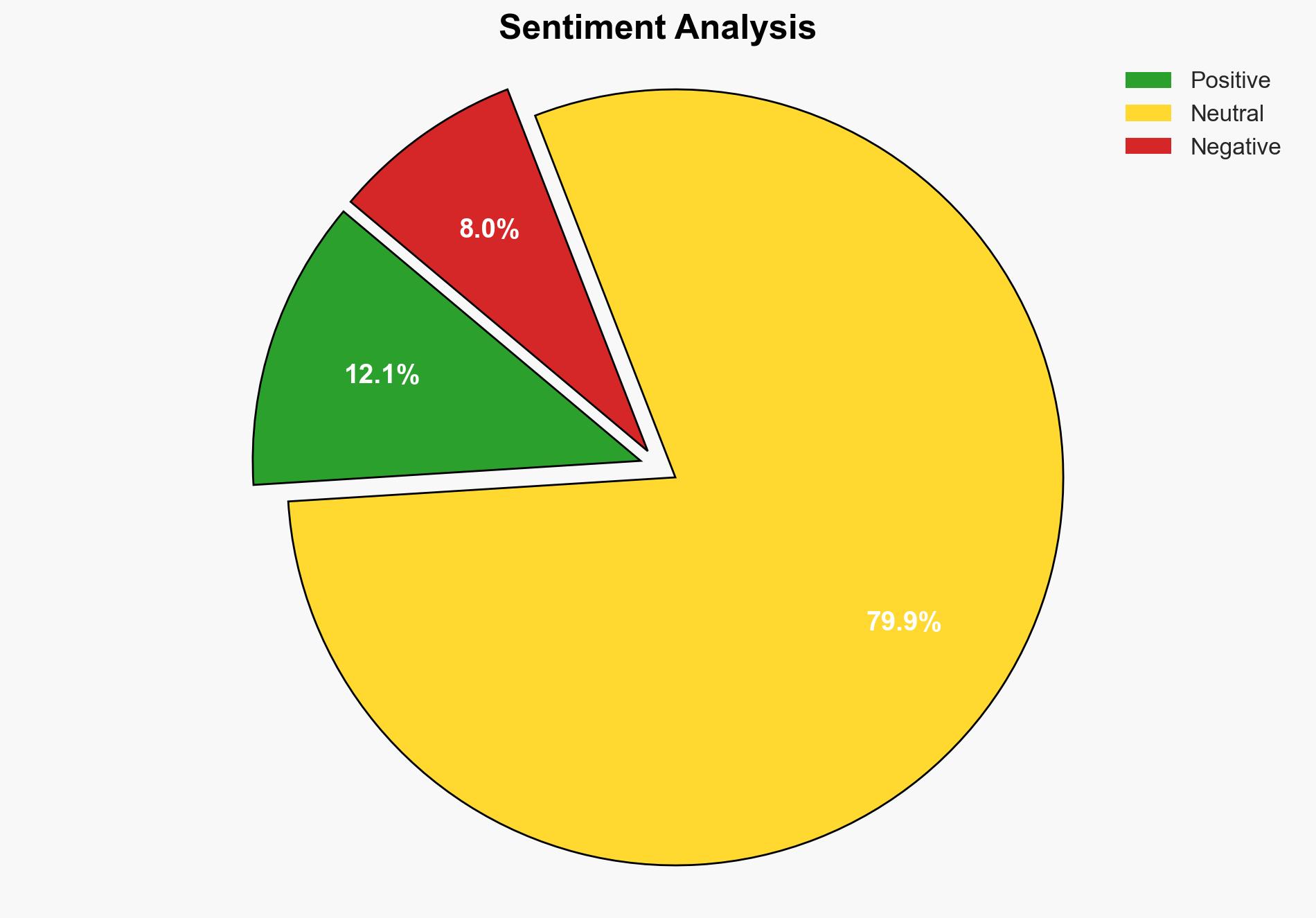
With a moderate confidence level, it is assessed that GitHub’s implementation of post-quantum SSH security is a proactive measure to safeguard against future quantum computing threats. The most supported hypothesis is that GitHub aims to maintain its competitive edge by ensuring the security of its platform against evolving cryptographic threats. Recommended actions include monitoring the adoption and effectiveness of post-quantum cryptography across the industry and preparing for potential shifts in cybersecurity standards.
2. Competing Hypotheses
Hypothesis 1: GitHub is implementing post-quantum SSH security primarily as a proactive measure to protect against future quantum computing threats, ensuring long-term security for its users.
Hypothesis 2: GitHub’s rollout of post-quantum SSH security is largely a marketing strategy to position itself as a leader in cybersecurity innovation, rather than a response to an imminent threat.
Hypothesis 1 is more likely due to the technical nature of the rollout and the emphasis on future-proofing against quantum threats, which aligns with industry trends and expert warnings about the potential for quantum computing to break current encryption methods.
3. Key Assumptions and Red Flags
Assumptions:
– Quantum computing will advance to a point where it can break current encryption methods within the next few decades.
– GitHub’s user base values enhanced security measures and will adopt the new SSH protocol without significant resistance.
Red Flags:
– Lack of immediate quantum computing threats could lead to complacency in adopting post-quantum measures.
– Over-reliance on hybrid models without full understanding of their limitations could create vulnerabilities.
4. Implications and Strategic Risks
The implementation of post-quantum cryptography by GitHub could set a precedent for other tech companies, accelerating the transition to quantum-resistant security measures. Failure to adopt such measures could leave organizations vulnerable to future quantum attacks. Additionally, the shift towards quantum-resistant protocols may drive changes in cybersecurity regulations and standards, impacting compliance requirements globally.
5. Recommendations and Outlook
- Encourage organizations to conduct risk assessments to evaluate their exposure to potential quantum threats and consider adopting quantum-resistant protocols.
- Monitor advancements in quantum computing to ensure timely updates to security measures.
- Best-case scenario: Industry-wide adoption of quantum-resistant protocols strengthens global cybersecurity resilience.
- Worst-case scenario: Slow adoption leads to significant vulnerabilities once quantum computing becomes a practical threat.
- Most-likely scenario: Gradual adoption of quantum-resistant measures with increased regulatory pressure and industry collaboration.
6. Key Individuals and Entities
GitHub, KPMG, Open Quantum Safe Project
7. Thematic Tags
Cybersecurity, Quantum Computing, Cryptography, Technology Innovation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·