CISA warns exploited Cisco flaws are a serious risk so patch now – TechRadar
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA warns exploited Cisco flaws are a serious risk so patch now – TechRadar
1. BLUF (Bottom Line Up Front)
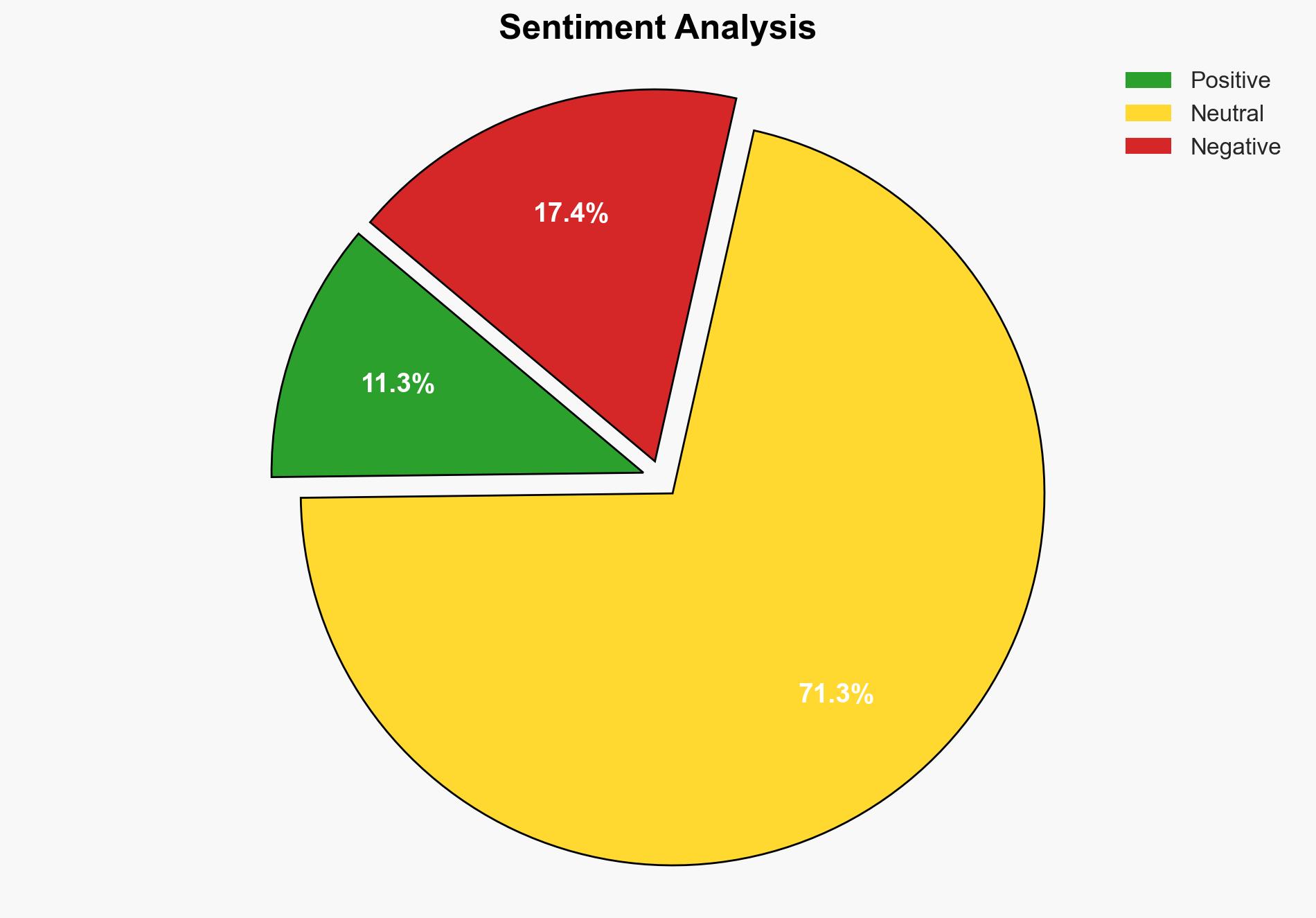
The most supported hypothesis is that the failure to patch Cisco vulnerabilities promptly poses a significant risk to federal agencies, potentially leading to severe cyber incidents like ransomware attacks. Confidence Level: High. Recommended action includes immediate compliance with CISA’s directives to patch vulnerabilities and enhance monitoring of network traffic for signs of exploitation.
2. Competing Hypotheses
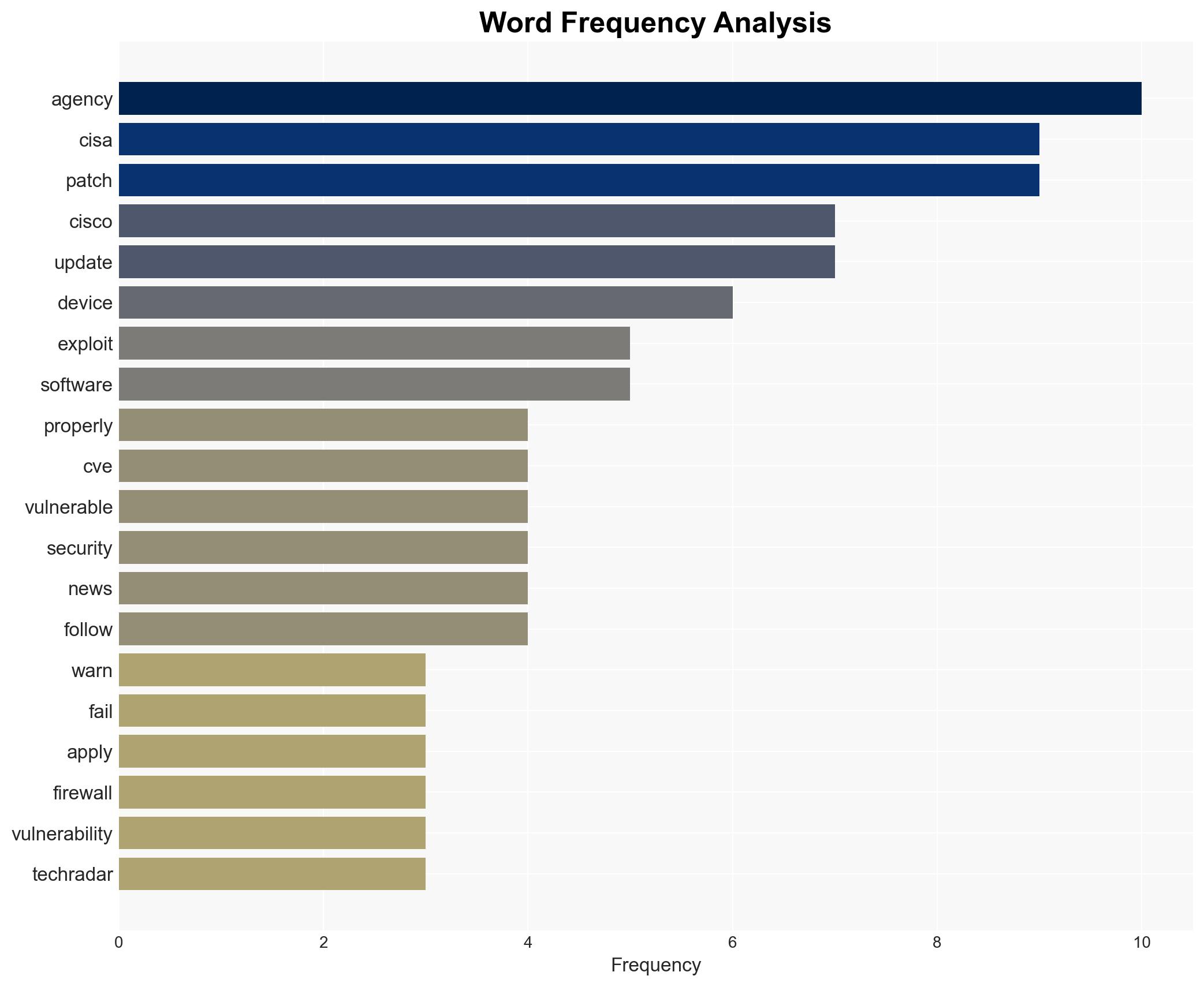
Hypothesis 1: The primary risk stems from a lack of compliance with CISA’s patch directives, leading to vulnerabilities being exploited by known campaigns like Arcanedoor.
Hypothesis 2: The vulnerabilities are being exploited due to sophisticated threat actors leveraging zero-day exploits, indicating a broader systemic issue in cybersecurity defense mechanisms beyond patch compliance.
Hypothesis 1 is more likely due to the explicit mention of non-compliance with patching directives and the urgency in CISA’s communications. Hypothesis 2, while plausible, lacks direct evidence in the provided data.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that all agencies have the capability to apply patches promptly and that the vulnerabilities are the sole entry point for attackers.
Red Flags: The urgency and specificity of CISA’s directive may indicate undisclosed intelligence about imminent threats. The mention of the Arcanedoor campaign suggests ongoing, targeted attacks.
Deception Indicators: There is no direct evidence of deception, but the reliance on self-reported compliance by agencies could mask the true extent of vulnerability.
4. Implications and Strategic Risks
The failure to patch vulnerabilities could lead to significant cyber incidents, including data breaches and ransomware attacks, affecting government operations and national security. Escalation scenarios include increased geopolitical tensions if state-sponsored actors are involved, economic impacts from disrupted services, and informational risks from potential data leaks.
5. Recommendations and Outlook
- Ensure immediate compliance with CISA’s patch directives across all agencies.
- Enhance network monitoring and incident response capabilities to detect and mitigate exploitation attempts.
- Conduct a comprehensive review of cybersecurity protocols to identify and address systemic vulnerabilities.
- Best-case scenario: Agencies comply with directives, and vulnerabilities are mitigated without incident.
- Worst-case scenario: Exploitation leads to significant cyber incidents, causing operational disruptions and data breaches.
- Most-likely scenario: Partial compliance leads to isolated incidents, prompting further directives and scrutiny.
6. Key Individuals and Entities
Cybersecurity and Infrastructure Security Agency (CISA), Federal Civilian Executive Branch Agencies (FCEB), Cisco Systems.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·