Nigerias new terror threat JNIM is spreading but its not too late to act – The Conversation Africa
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Nigerias new terror threat JNIM is spreading but its not too late to act – The Conversation Africa
1. BLUF (Bottom Line Up Front)
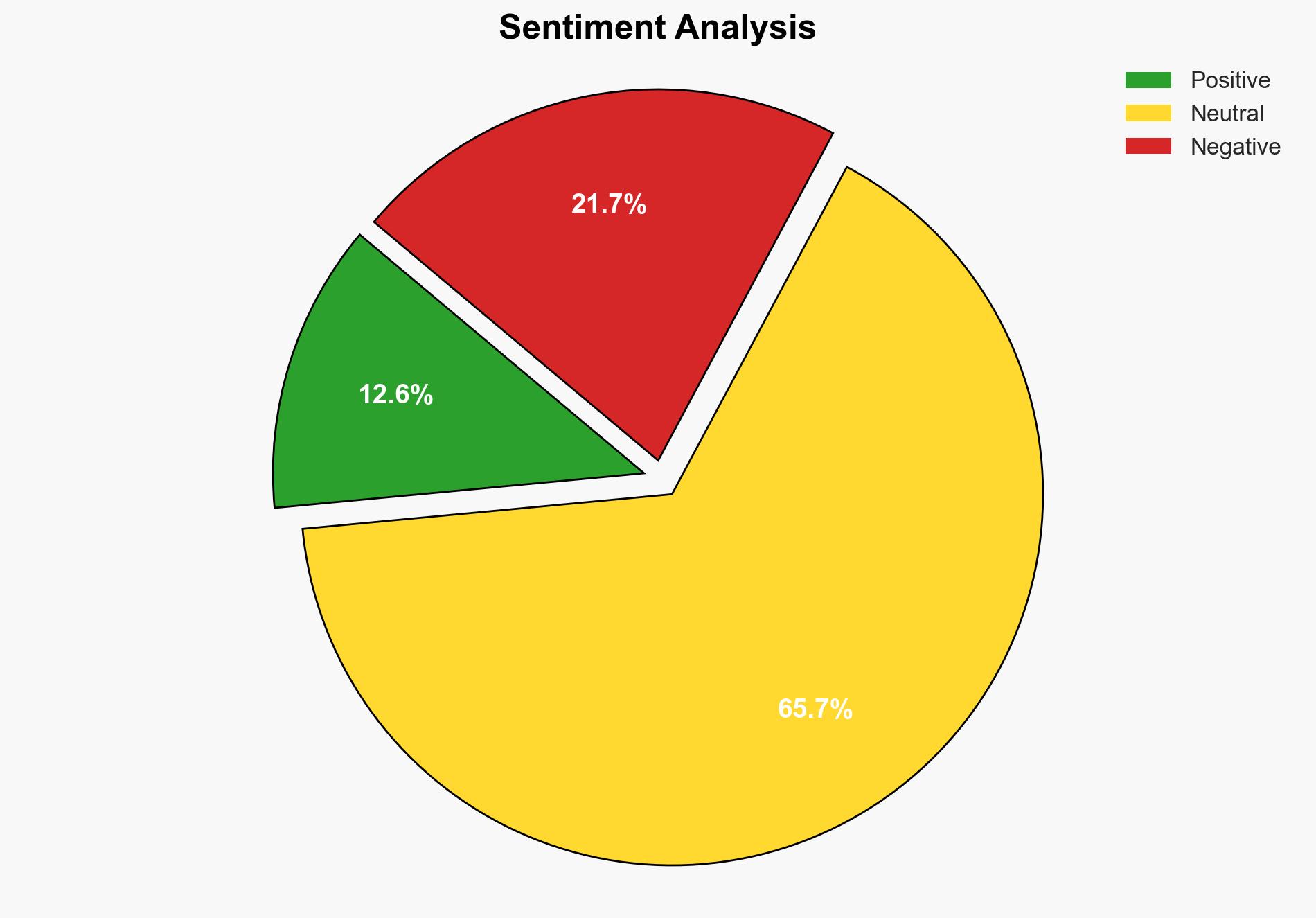
JNIM’s expansion into Nigeria represents a significant security threat, with a high likelihood of further destabilization if not addressed promptly. The most supported hypothesis is that JNIM is exploiting Nigeria’s porous borders and socio-political vulnerabilities to establish a foothold. Immediate, coordinated counter-terrorism measures are recommended to prevent further entrenchment. Confidence Level: High.
2. Competing Hypotheses
Hypothesis 1: JNIM is strategically expanding into Nigeria to exploit its socio-political vulnerabilities and establish a permanent operational base.
Hypothesis 2: JNIM’s activities in Nigeria are opportunistic, driven by short-term gains such as resource exploitation and are not indicative of a long-term strategic plan.
Assessment: Hypothesis 1 is more likely due to JNIM’s historical patterns of establishing control in regions with weak governance and leveraging local grievances. The strategic location of Kwara State and recent attacks support this hypothesis.
3. Key Assumptions and Red Flags
Assumptions: JNIM’s strategic intentions are aligned with its historical patterns; Nigeria’s current security measures are insufficient to counter this threat.
Red Flags: Increased attacks in border regions, evidence of coordination with local extremist groups, and exploitation of local resources.
Deception Indicators: Potential misinformation about JNIM’s capabilities or intentions to mislead Nigerian security forces.
4. Implications and Strategic Risks
The expansion of JNIM into Nigeria could lead to increased regional instability, affecting political stability and economic development. There is a risk of JNIM forming alliances with local extremist groups, exacerbating existing security challenges. Cyber and informational threats may also increase as JNIM adopts hybrid warfare tactics.
5. Recommendations and Outlook
- Enhance border security and intelligence-sharing with neighboring countries to prevent JNIM’s infiltration.
- Strengthen local governance and address socio-economic grievances to reduce JNIM’s appeal.
- Coordinate with international partners for counter-terrorism support and capacity building.
- Best-case scenario: Successful disruption of JNIM’s operations and prevention of further expansion.
- Worst-case scenario: JNIM establishes a stronghold, leading to increased attacks and regional destabilization.
- Most-likely scenario: Continued sporadic attacks with gradual entrenchment unless countered effectively.
6. Key Individuals and Entities
No specific individuals are identified in the provided text. Focus remains on JNIM as the primary entity.
7. Thematic Tags
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us
·