Linux on the Fujitsu Lifebook U729 – Borretti.me
Published on: 2025-11-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
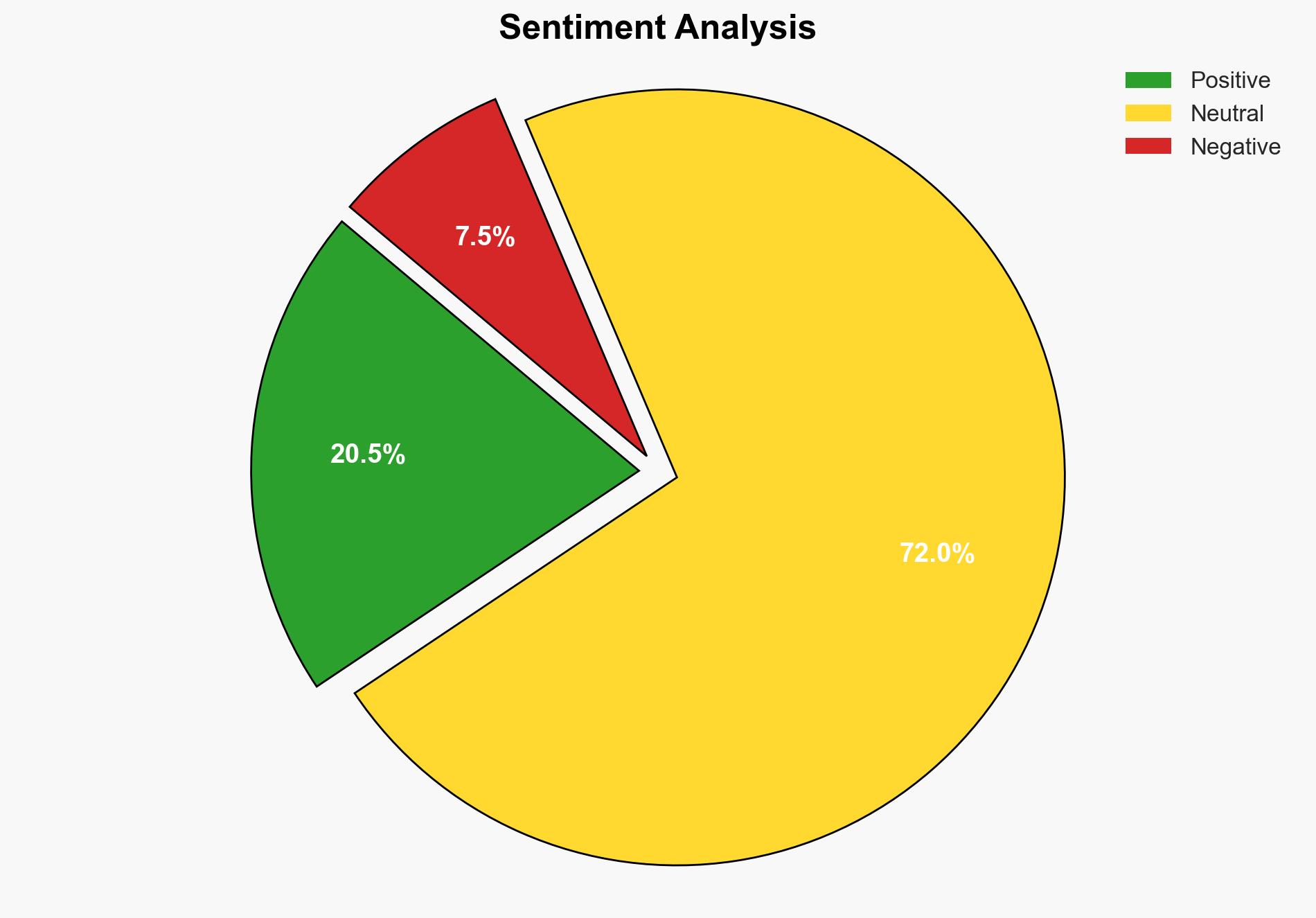
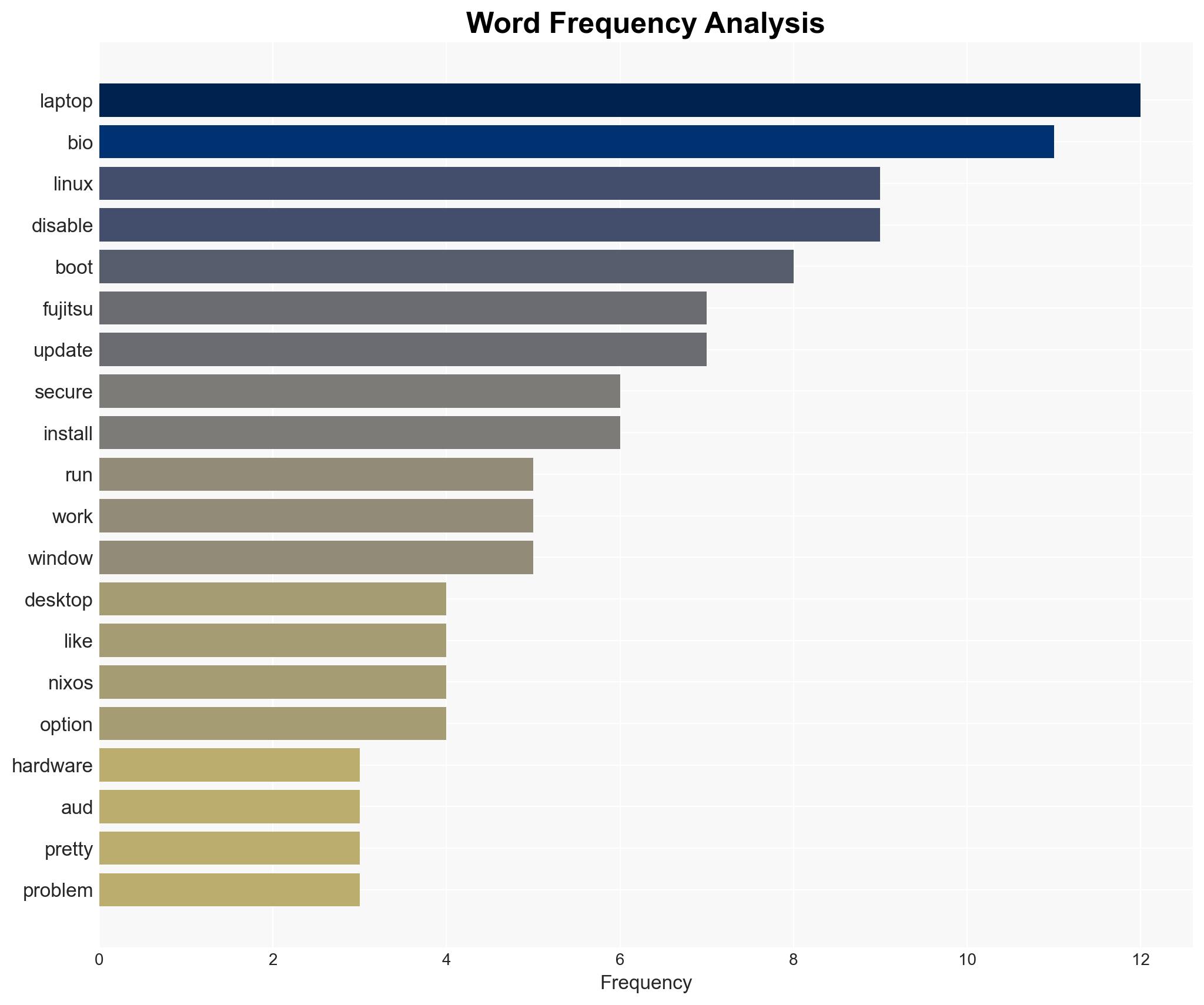
The Fujitsu Lifebook U729 is a viable option for Linux users seeking a lightweight and affordable laptop, but it presents challenges related to secure boot and potential embedded spyware. The most supported hypothesis is that the Lifebook U729, while technically competent, poses cybersecurity risks due to its enterprise-focused features. Confidence Level: Moderate. Recommended action is to proceed with caution, ensuring robust security measures are in place when using such devices.
2. Competing Hypotheses
Hypothesis 1: The Fujitsu Lifebook U729 is a cost-effective and efficient laptop for Linux users, with minor technical hurdles that can be overcome with user intervention.
Hypothesis 2: The Fujitsu Lifebook U729, while technically capable, poses significant cybersecurity risks due to embedded enterprise features like Absolute Persistence, which could be exploited for unauthorized tracking or data access.
The second hypothesis is more likely given the presence of enterprise-focused features that are difficult to disable and could represent a security vulnerability.
3. Key Assumptions and Red Flags
Assumptions: The user has the technical capability to navigate BIOS settings and perform necessary updates. The Absolute Persistence feature is not actively exploited by malicious actors.
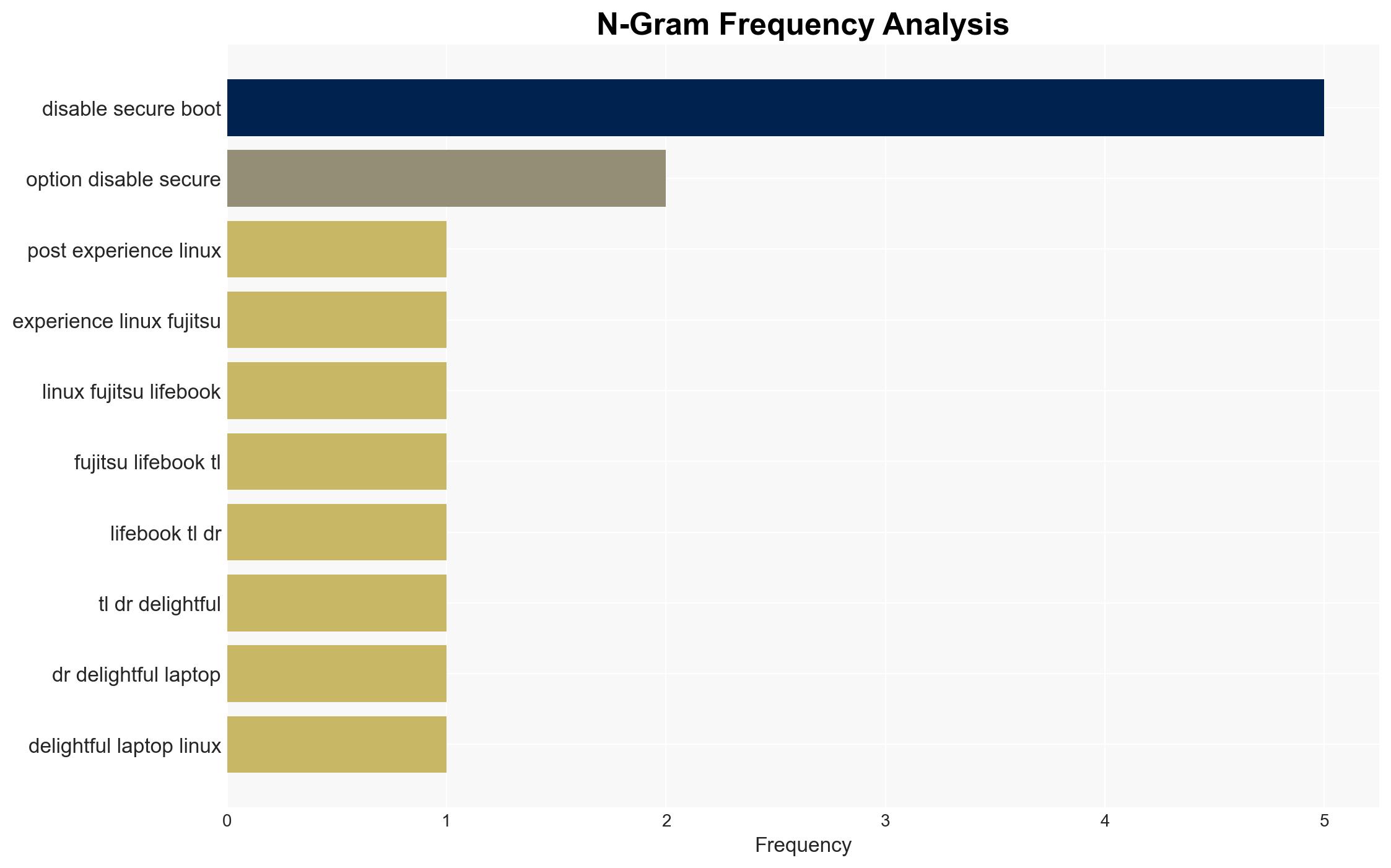
Red Flags: The inability to easily disable secure boot and the presence of embedded tracking software are significant concerns. The reliance on Windows-based tools to update BIOS and firmware is a potential vulnerability.
4. Implications and Strategic Risks
The presence of embedded tracking software could lead to unauthorized data access or surveillance, posing a cybersecurity threat. If exploited, this could result in data breaches or privacy violations. Additionally, the difficulty in disabling secure boot may deter users from adopting Linux, impacting market dynamics in favor of proprietary systems.
5. Recommendations and Outlook
- Conduct a thorough security audit of the Lifebook U729 to identify and mitigate potential vulnerabilities.
- Advocate for transparency and user control over embedded enterprise features in consumer devices.
- Best Scenario: Users successfully disable unwanted features and secure their devices, leading to increased adoption of Linux on enterprise hardware.
- Worst Scenario: Exploitation of embedded features results in widespread data breaches, damaging user trust and market reputation.
- Most-likely Scenario: Users face ongoing challenges with secure boot and embedded features, leading to cautious adoption with a focus on security measures.
6. Key Individuals and Entities
Fujitsu (Manufacturer), Microsoft (Software Provider for BIOS updates), Linux Community (Potential User Base)
7. Thematic Tags
Cybersecurity, Enterprise Hardware, Linux Adoption, Data Privacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·