I finally understand Cloudflare Zero Trust tunnels – David.coffee
Published on: 2025-11-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
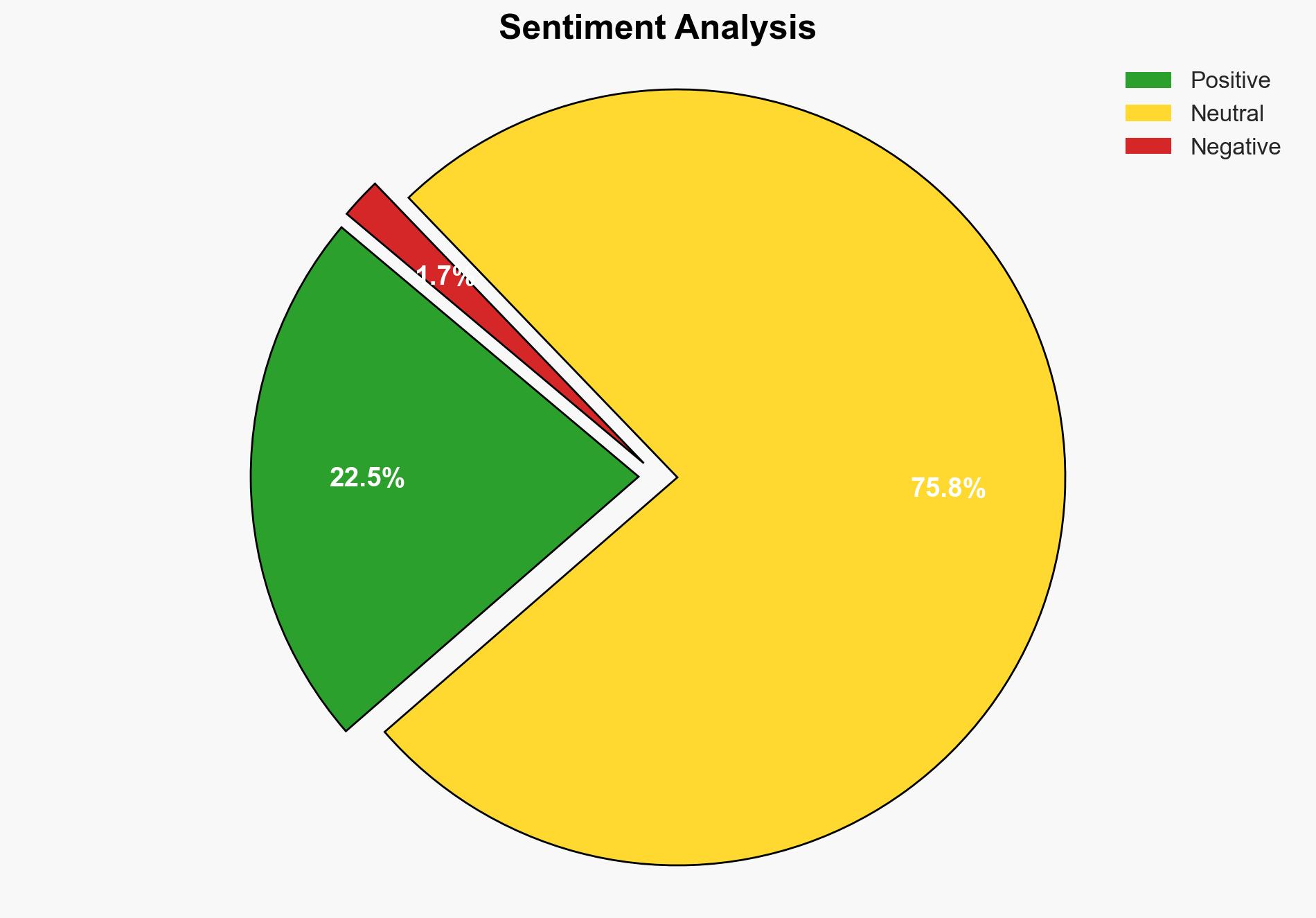
1. BLUF (Bottom Line Up Front)
With a moderate confidence level, the most supported hypothesis is that Cloudflare Zero Trust tunnels offer a robust solution for secure network connectivity, particularly for environments that require private network access without exposing services to public internet threats. The recommended action is to evaluate and potentially integrate Cloudflare Zero Trust solutions into organizational cybersecurity strategies, especially where traditional VPNs or peer-to-peer solutions like Tailscale are insufficient.
2. Competing Hypotheses
Hypothesis 1: Cloudflare Zero Trust tunnels provide a superior method for secure network connectivity compared to traditional VPNs and Tailscale, due to their ability to manage access policies and reduce latency through direct connections.
Hypothesis 2: Cloudflare Zero Trust tunnels are not significantly better than existing solutions like Tailscale, as they introduce complexity and potential latency through reliance on Cloudflare’s infrastructure.
Hypothesis 1 is more likely due to the structured access policies and the ability to create private networks without exposing services to the public internet, which is a significant advantage in cybersecurity contexts.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that Cloudflare’s infrastructure is reliable and secure, and that the complexity of setting up Zero Trust tunnels can be managed effectively by organizations.
Red Flags: Potential over-reliance on Cloudflare’s infrastructure could be a single point of failure. Additionally, the complexity of configuration might lead to misconfigurations that could expose vulnerabilities.
4. Implications and Strategic Risks
Adopting Cloudflare Zero Trust tunnels could mitigate risks associated with public exposure of services, but it also introduces dependency on a third-party provider. This could lead to strategic risks if Cloudflare’s services are disrupted. Furthermore, misconfigurations or improper policy settings could inadvertently expose sensitive data.
5. Recommendations and Outlook
- Actionable Steps: Conduct a thorough risk assessment of current network security infrastructure and evaluate the integration of Cloudflare Zero Trust tunnels. Train IT staff on proper configuration and management of these tunnels.
- Best Case Scenario: Seamless integration of Cloudflare Zero Trust tunnels enhances security posture without significant latency or configuration issues.
- Worst Case Scenario: Misconfigurations lead to security breaches, or reliance on Cloudflare results in service disruptions.
- Most-likely Scenario: Cloudflare Zero Trust tunnels provide improved security with manageable complexity, but require ongoing management and oversight.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The primary entity involved is Cloudflare.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·