Call Me Maybe Eavesdropping encrypted LTE calls with ReVoLTE 2020 – Montsecure.com
Published on: 2025-11-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
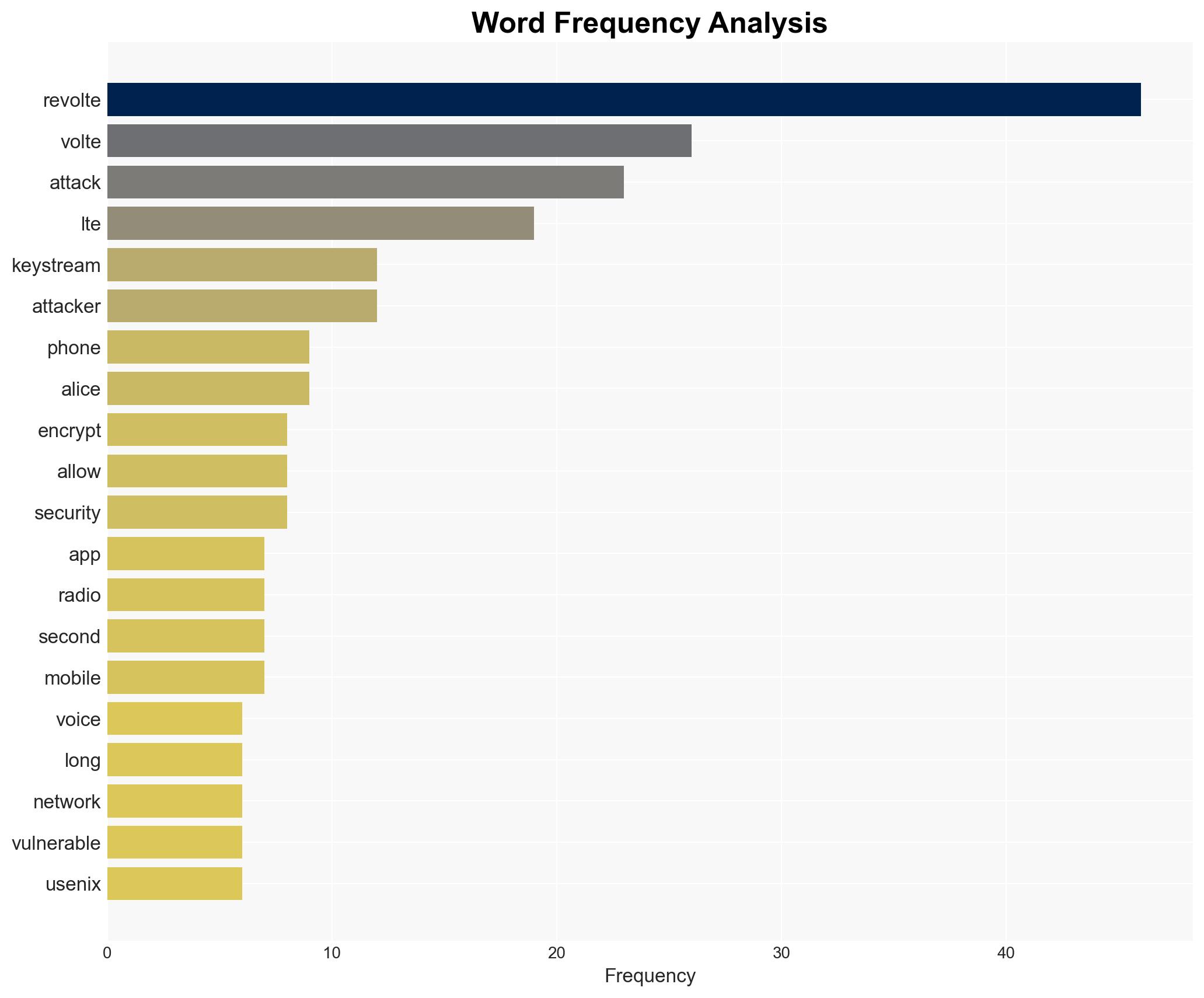
The ReVoLTE attack presents a significant vulnerability in LTE networks, allowing potential eavesdropping on encrypted VoLTE calls. The most supported hypothesis is that the vulnerability stems from a widespread implementation flaw in LTE base stations, which has not been uniformly addressed by telecom operators. Confidence Level: Moderate. Recommended action includes urgent patching of affected systems and increased awareness among telecom operators globally.
2. Competing Hypotheses
Hypothesis 1: The ReVoLTE vulnerability is primarily due to a widespread implementation flaw in LTE base stations that has not been adequately addressed by telecom operators. This hypothesis is supported by the evidence of the vulnerability affecting multiple base stations, particularly in Germany, and the need for vendor patches.
Hypothesis 2: The ReVoLTE vulnerability is a result of targeted exploitation by sophisticated adversaries who are leveraging specific weaknesses in particular network configurations. This hypothesis is less supported due to the broad nature of the vulnerability and the lack of evidence pointing to targeted attacks.
The first hypothesis is more likely given the evidence of widespread vulnerability and the ongoing efforts to patch affected systems.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerability is not yet fully exploited on a large scale, and that telecom operators are capable of implementing the necessary patches.
Red Flags: The potential for delayed patch implementation due to the large number of providers and the complexity of LTE networks. Additionally, the possibility of adversaries developing more sophisticated methods to exploit this vulnerability.
Deception Indicators: None identified in the current analysis, but vigilance is required for misinformation regarding patch effectiveness or scope of vulnerability.
4. Implications and Strategic Risks
The ReVoLTE vulnerability poses significant cyber risks, including unauthorized eavesdropping on sensitive communications. This could lead to political and economic repercussions if exploited by state or non-state actors. The vulnerability could also undermine public trust in telecom security, leading to reputational damage for operators and potential regulatory scrutiny.
5. Recommendations and Outlook
- Immediate action is required by telecom operators to implement patches and secure vulnerable base stations.
- Increase awareness and training for telecom operators on the ReVoLTE vulnerability and potential mitigation strategies.
- Best-case scenario: Rapid patch implementation and minimal exploitation of the vulnerability.
- Worst-case scenario: Widespread exploitation leading to significant data breaches and loss of trust in telecom security.
- Most-likely scenario: Gradual patch implementation with isolated incidents of exploitation.
6. Key Individuals and Entities
David Rupprecht, Katharina Kohls, Thorsten Holz, Christina Bochum.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·