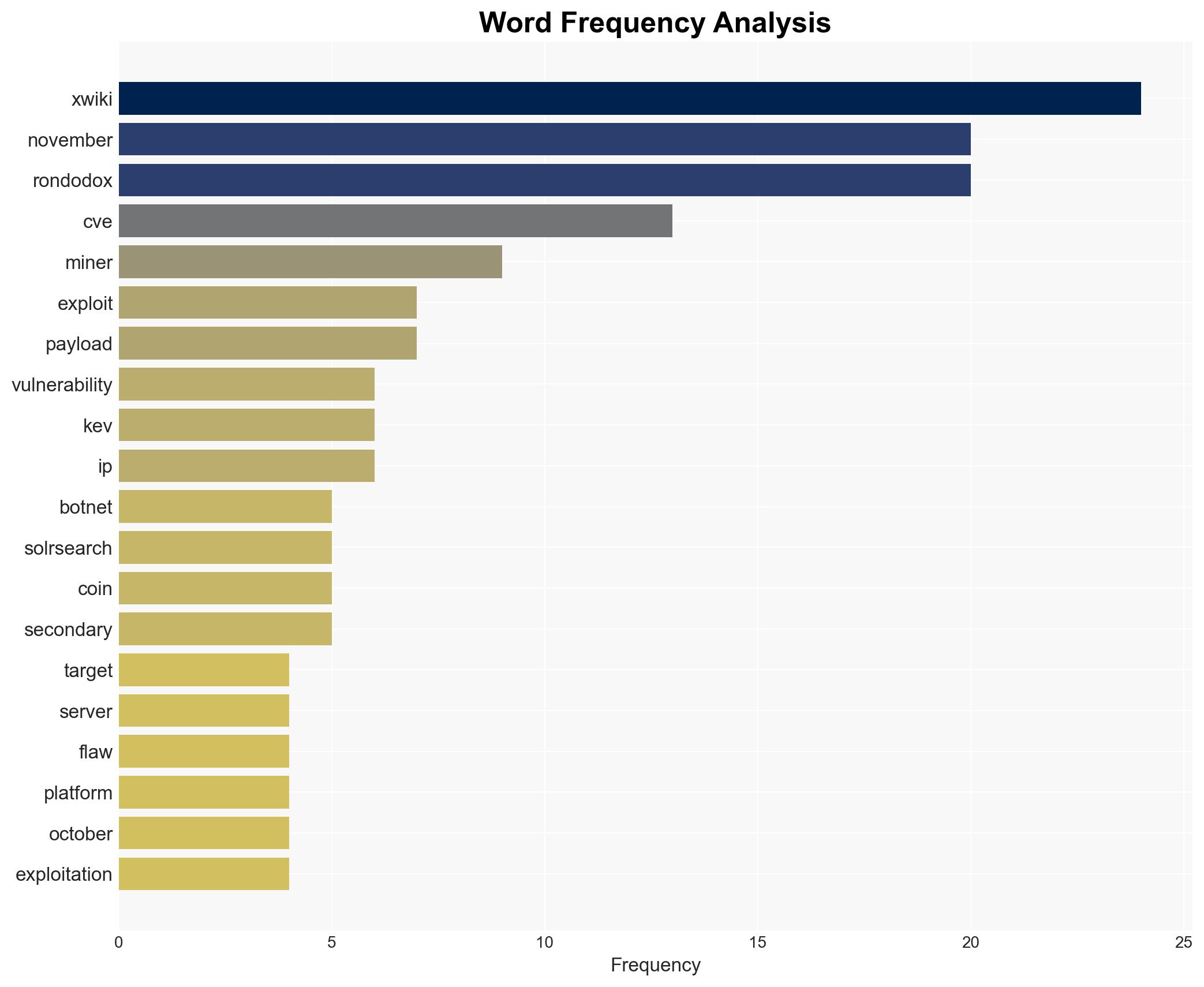
RondoDox expands botnet by exploiting XWiki RCE bug left unpatched since February 2025 – Securityaffairs.com
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: RondoDox Botnet Exploitation of XWiki RCE Vulnerability
1. BLUF (Bottom Line Up Front)
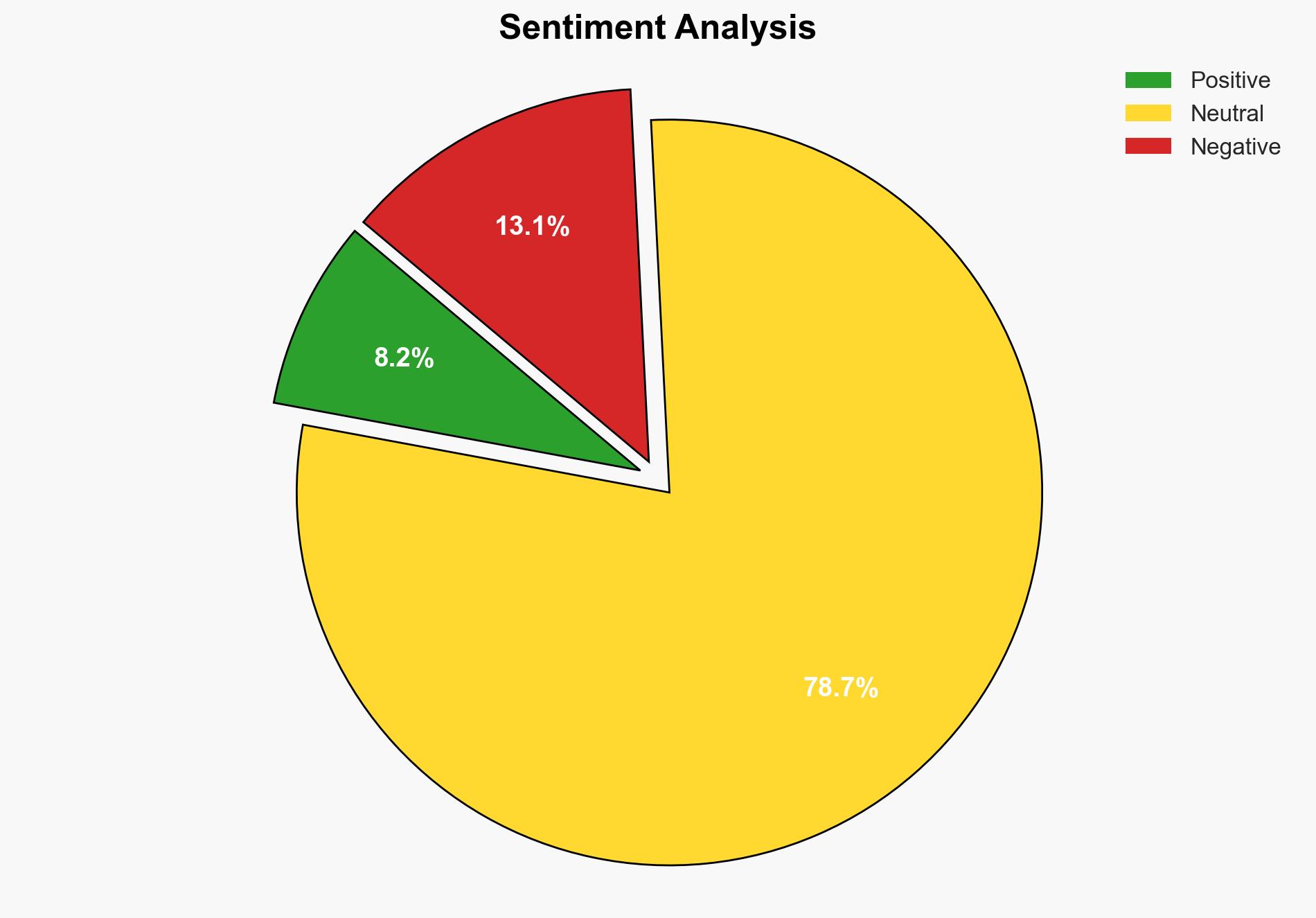
The RondoDox botnet has significantly expanded its capabilities by exploiting an unpatched Remote Code Execution (RCE) vulnerability in the XWiki platform. The most supported hypothesis is that RondoDox is leveraging this vulnerability to deploy coin miners and potentially other malicious payloads. The recommended action is to prioritize patching vulnerable XWiki installations and enhance monitoring for unusual network activity. Confidence Level: Moderate.
2. Competing Hypotheses
Hypothesis 1: RondoDox is primarily exploiting the XWiki RCE vulnerability to expand its botnet for cryptocurrency mining.
Hypothesis 2: RondoDox is using the XWiki RCE vulnerability as a vector for broader cyber-espionage or disruptive activities, with cryptocurrency mining as a secondary objective.
Hypothesis 1 is more likely given the observed deployment of coin miners and the historical behavior of botnets focusing on financial gain through resource exploitation. However, the presence of obfuscated payloads and attempts to avoid detection suggest that broader objectives cannot be ruled out.
3. Key Assumptions and Red Flags
Assumptions include the belief that RondoDox’s primary motivation is financial gain through mining. A red flag is the lack of comprehensive visibility into the botnet’s full capabilities and intentions, which could indicate deception or a more complex operational strategy. The rapid adoption of the vulnerability suggests a potential underestimation of RondoDox’s adaptability and resourcefulness.
4. Implications and Strategic Risks
The exploitation of the XWiki RCE vulnerability poses significant risks to organizations using the platform, potentially leading to data breaches, service disruptions, and financial losses. If RondoDox’s objectives extend beyond mining, there could be broader implications for cyber-espionage or infrastructure sabotage. The vulnerability’s presence in the CISA KEV catalog indicates a high likelihood of continued exploitation, potentially by other threat actors.
5. Recommendations and Outlook
- Immediate patching of XWiki installations to mitigate the RCE vulnerability.
- Enhanced network monitoring for signs of exploitation, such as unusual outbound connections or resource usage spikes.
- Collaboration with cybersecurity agencies for intelligence sharing and threat hunting.
- Best-case scenario: Rapid patch deployment and increased awareness reduce exploitation incidents.
- Worst-case scenario: RondoDox or other actors leverage the vulnerability for widespread cyber-attacks beyond mining.
- Most-likely scenario: Continued exploitation for cryptocurrency mining with sporadic attempts at broader cyber operations.
6. Key Individuals and Entities
Pierluigi Paganini (report author), RondoDox (botnet entity), U.S. Cybersecurity and Infrastructure Security Agency (CISA).
7. Thematic Tags
Cybersecurity, Botnet, Vulnerability Exploitation, Cryptocurrency Mining, XWiki
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·