Logitech confirms data breach – Help Net Security
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Logitech Data Breach Incident
1. BLUF (Bottom Line Up Front)
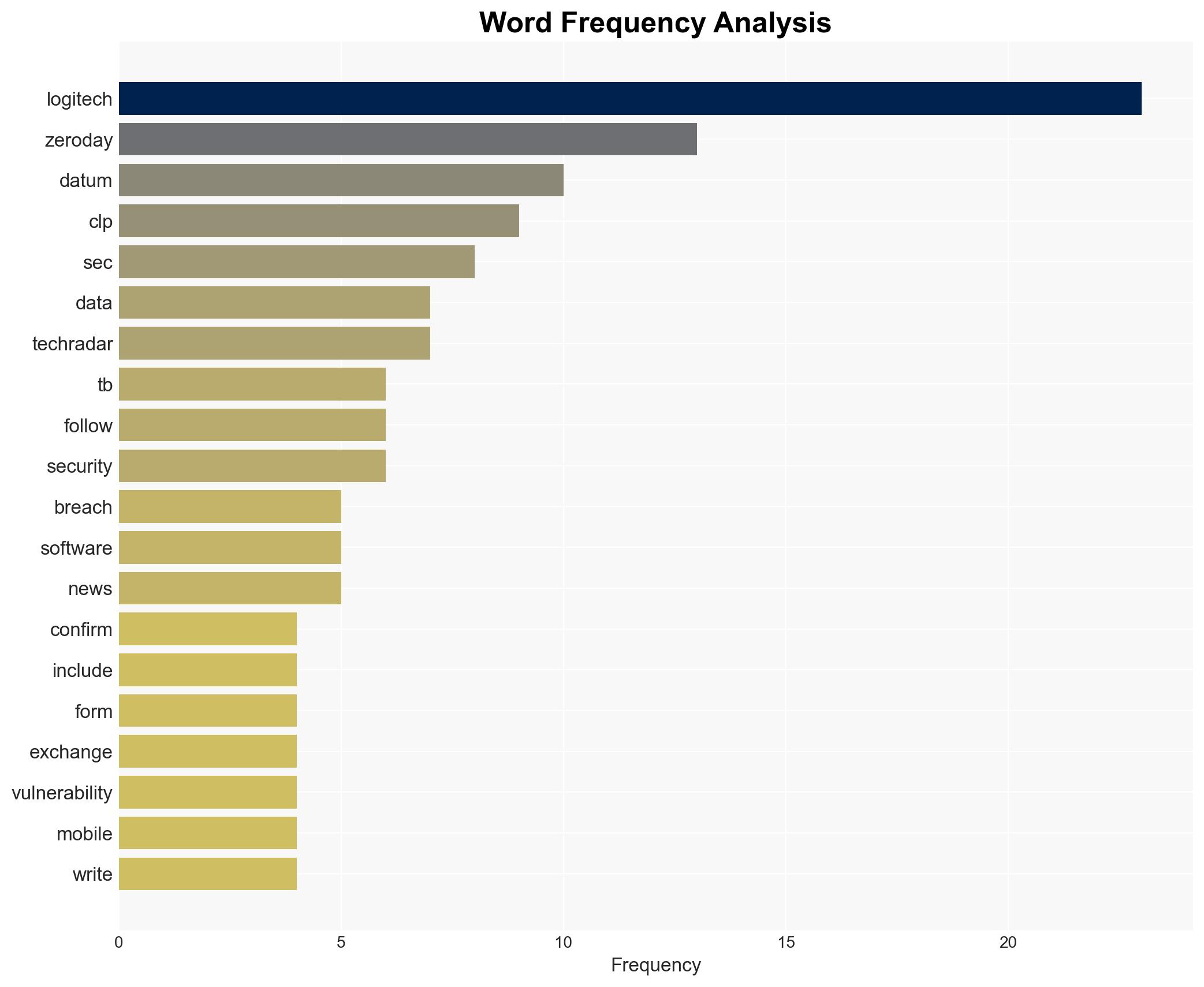
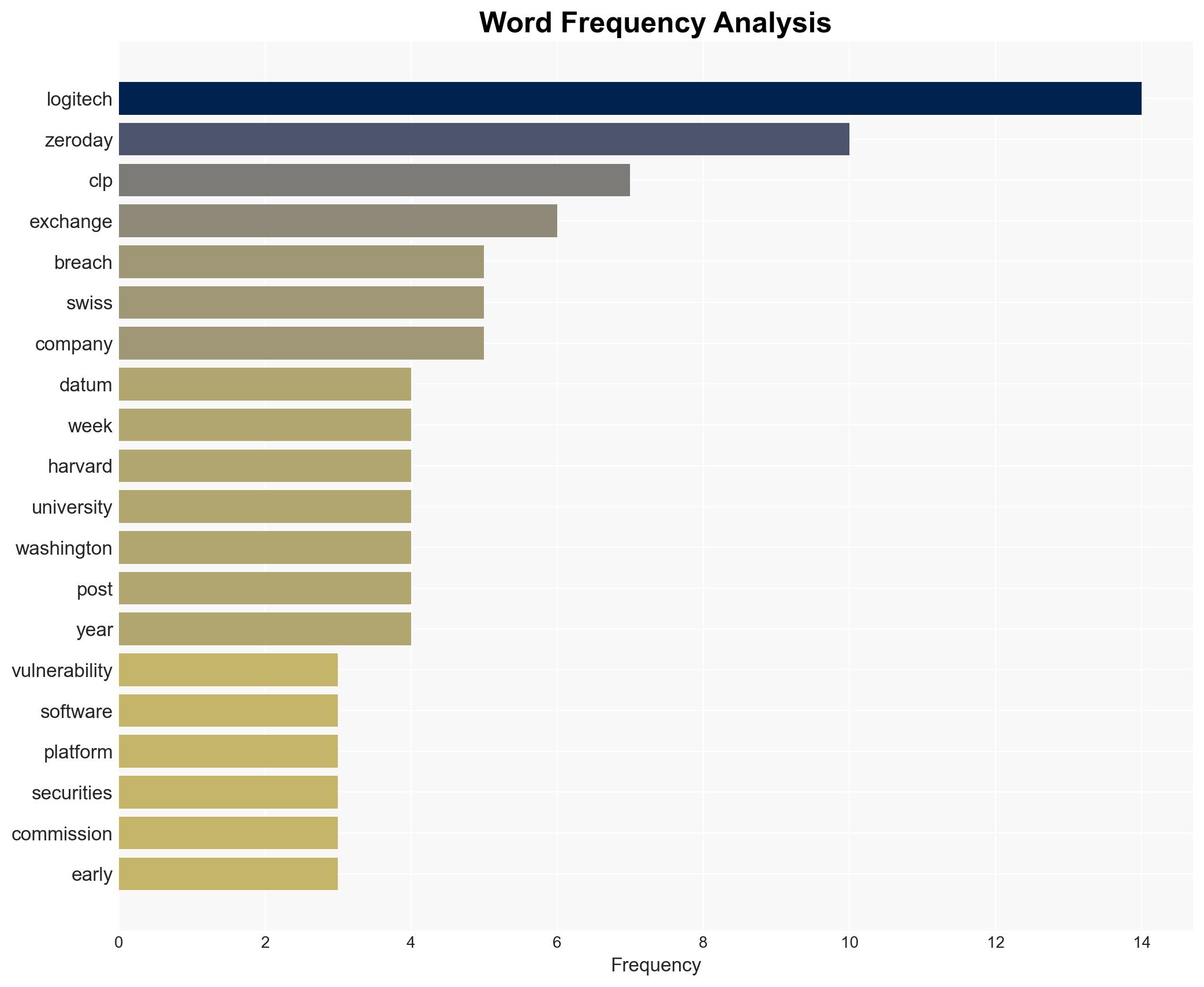
The most supported hypothesis is that the data breach at Logitech was primarily facilitated through a zero-day vulnerability in a third-party software platform, potentially exploited by the Cl0p cyber extortion gang. This hypothesis is supported by the evidence of similar breaches and the gang’s modus operandi. The confidence level in this assessment is moderate due to ongoing investigations and limited public disclosures. Recommended actions include immediate patching of vulnerabilities, enhanced monitoring, and collaboration with cybersecurity agencies.
2. Competing Hypotheses
Hypothesis 1: The breach was executed by the Cl0p cyber extortion gang exploiting a zero-day vulnerability in a third-party software platform used by Logitech. This is supported by the gang’s history of similar attacks and their claims on the dark web.
Hypothesis 2: The breach was conducted by an unaffiliated cybercriminal group using a zero-day vulnerability, with Cl0p’s involvement being a false flag operation to mislead investigators. This hypothesis considers the possibility of deception and misattribution.
The first hypothesis is more likely due to the pattern of Cl0p’s activities and their public claims, although the possibility of deception cannot be entirely dismissed.
3. Key Assumptions and Red Flags
Assumptions include the accuracy of Logitech’s initial assessments and the integrity of the information released by Cl0p. Red flags include the lack of detailed information on the third-party software and the potential for Cl0p to exaggerate their involvement for notoriety. Deception indicators include the timing of the ransom demand and the public nature of the claims.
4. Implications and Strategic Risks
The breach poses significant risks, including potential financial losses from legal actions and regulatory fines, reputational damage, and increased scrutiny from cybersecurity agencies. There is a risk of cascading threats if the vulnerability is not promptly patched, potentially affecting other companies using the same software. Politically, this incident could lead to increased regulatory pressure on technology firms to enhance cybersecurity measures.
5. Recommendations and Outlook
- Immediate steps include conducting a comprehensive forensic investigation, patching all identified vulnerabilities, and enhancing threat detection capabilities.
- Engage with cybersecurity experts and law enforcement to track the perpetrators and prevent future incidents.
- Best-case scenario: Quick resolution with minimal financial and reputational impact.
- Worst-case scenario: Prolonged legal battles, significant financial losses, and damage to brand reputation.
- Most-likely scenario: Moderate financial impact with increased cybersecurity measures and temporary reputational damage.
6. Key Individuals and Entities
No specific individuals are named in the report. Entities involved include Logitech, Cl0p cyber extortion gang, and the unidentified third-party software vendor.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·