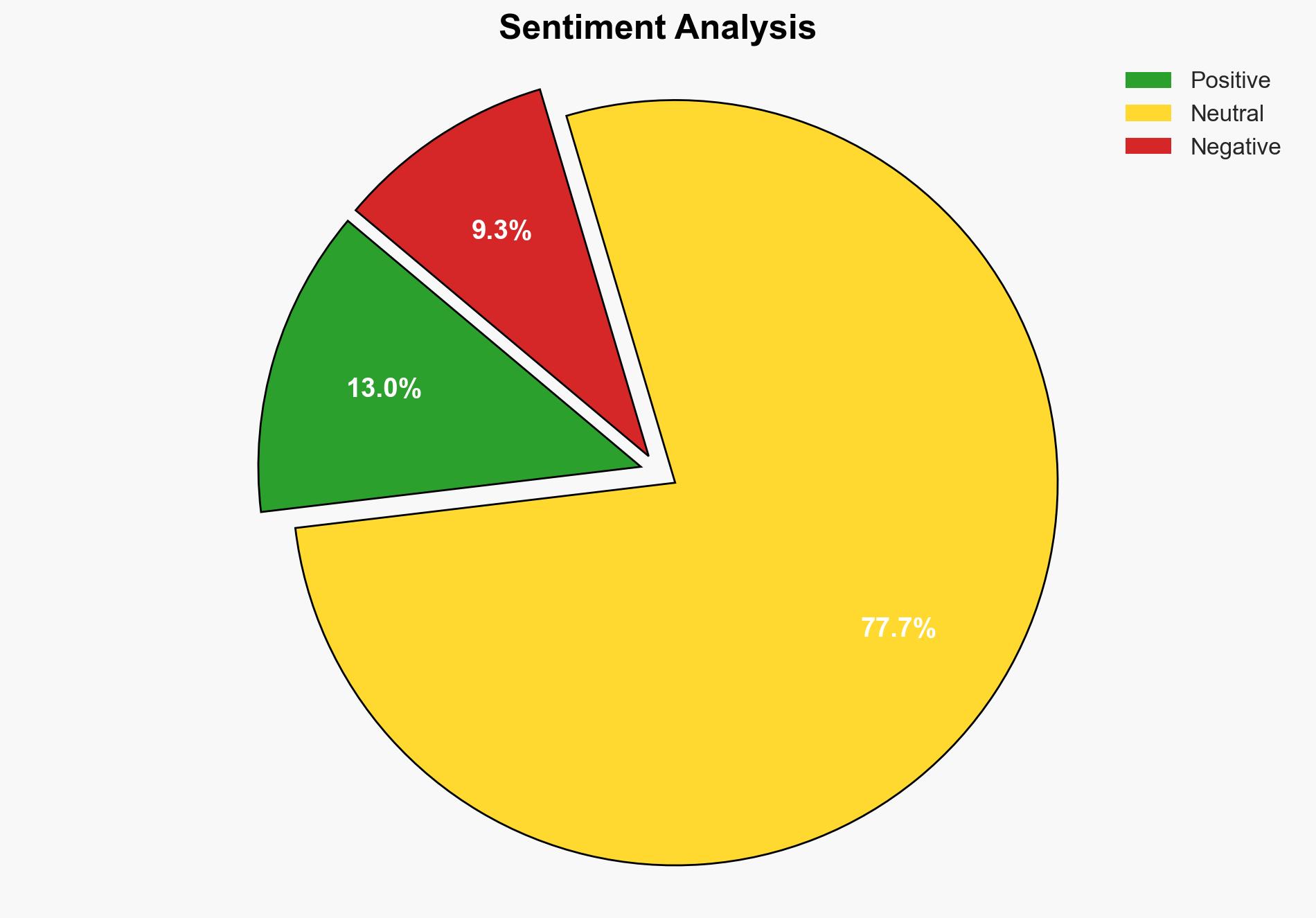
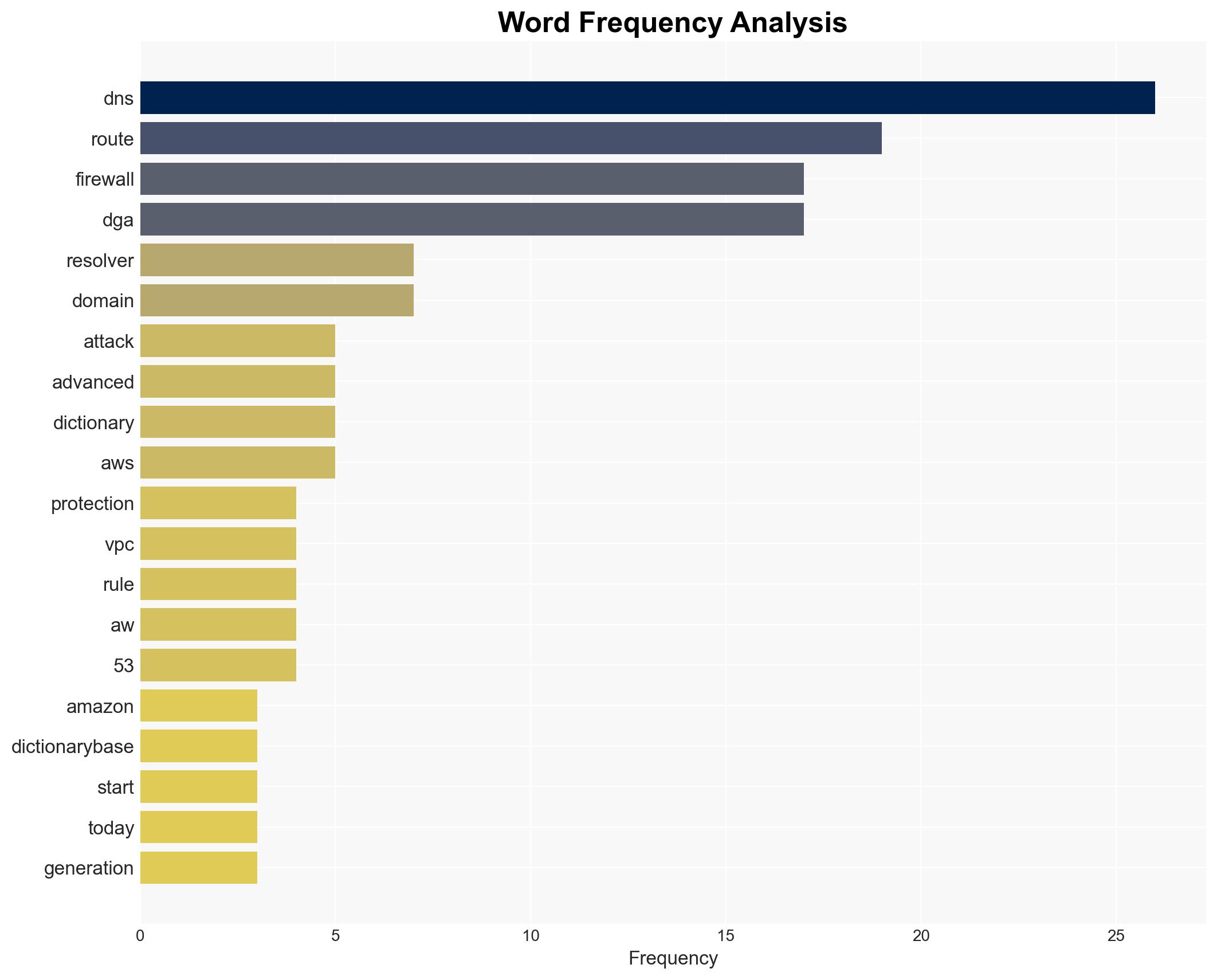
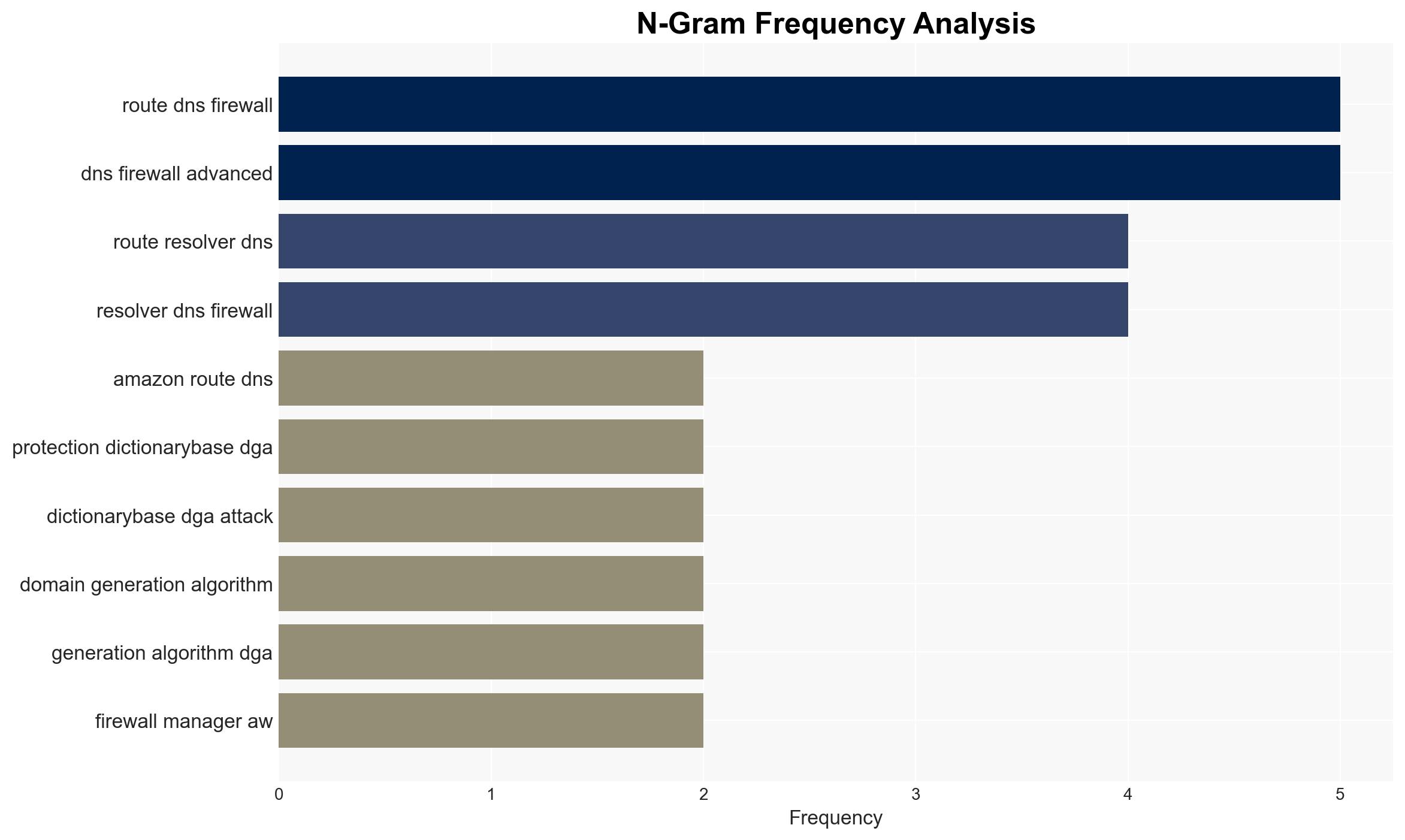
Amazon Route 53 DNS Firewall adds protection against Dictionary-based DGA attacks – Amazon.com
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
Amazon’s enhancement of Route 53 DNS Firewall to protect against dictionary-based Domain Generation Algorithm (DGA) attacks represents a significant advancement in cybersecurity measures. The most supported hypothesis is that this development will improve the security posture of AWS users by mitigating a common attack vector. Confidence level: High. Recommended action: Organizations using AWS should integrate this feature into their security protocols to enhance protection against DGA attacks.
2. Competing Hypotheses
Hypothesis 1: The enhancement of Amazon Route 53 DNS Firewall will significantly reduce the effectiveness of dictionary-based DGA attacks on AWS-hosted services.
Hypothesis 2: The enhancement will have limited impact due to potential evasion tactics by attackers and the need for comprehensive user adoption and configuration.
Hypothesis 1 is more likely due to the technical capabilities of the DNS Firewall to monitor and block suspicious queries in real-time, coupled with AWS’s extensive reach and influence in the cloud services market, which can drive widespread adoption.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that AWS users will promptly adopt and correctly configure the new DNS Firewall features. It is also assumed that attackers will not quickly develop new evasion techniques that bypass these protections.
Red Flags: Potential over-reliance on AWS’s security measures by users, leading to complacency in other areas of cybersecurity. Additionally, rapid development of new DGA techniques by adversaries could undermine the effectiveness of the firewall.
4. Implications and Strategic Risks
The enhancement of Route 53 DNS Firewall could lead to a decrease in successful DGA attacks, thereby strengthening the security of AWS-hosted services. However, adversaries may escalate efforts to develop more sophisticated DGA techniques or shift focus to other vulnerabilities within the AWS ecosystem. This could result in a temporary lull in DGA attacks but potentially increase the complexity and sophistication of future threats.
5. Recommendations and Outlook
- Organizations should integrate the enhanced DNS Firewall into their security strategies and ensure proper configuration and monitoring.
- Conduct regular security audits to identify and mitigate potential vulnerabilities beyond DGA attacks.
- Best-case scenario: Significant reduction in successful DGA attacks on AWS-hosted services, leading to improved overall cybersecurity posture.
- Worst-case scenario: Rapid adaptation by attackers results in new evasion techniques, diminishing the effectiveness of the DNS Firewall.
- Most-likely scenario: Initial reduction in DGA attacks with gradual adaptation by attackers, necessitating ongoing updates and enhancements to security measures.
6. Key Individuals and Entities
No specific individuals are identified in the source text. Key entities include Amazon Web Services (AWS) and its customers utilizing the Route 53 DNS Firewall.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·