Kansas Woman Pleads Guilty To Falsely Claiming Astronaut Ex-Wife Hacked Her Bank Account From Space – BroBible
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
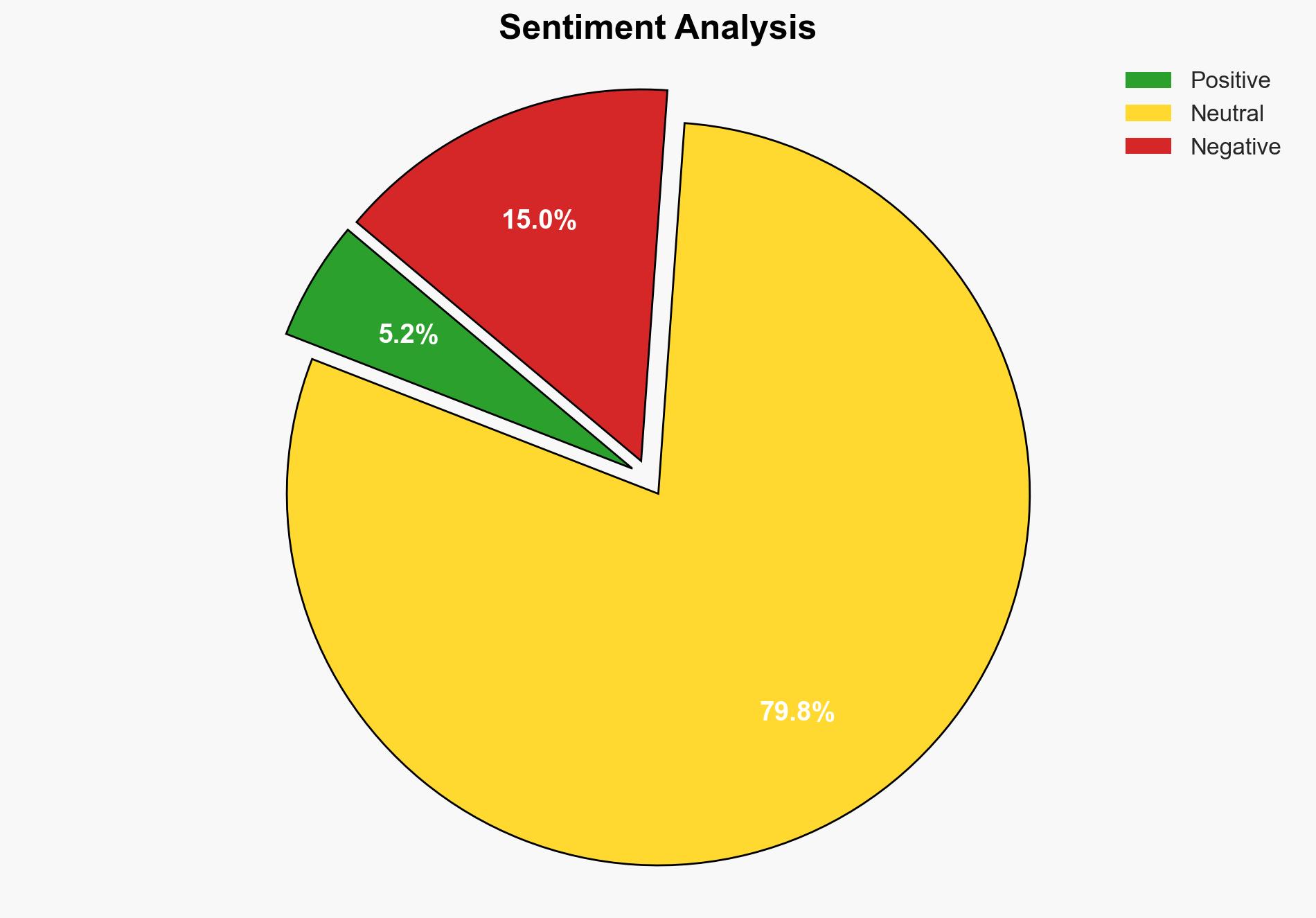
With moderate confidence, the most supported hypothesis is that Summer Worden’s accusations against Anne McClain were motivated by personal conflict rather than substantive evidence of cybercrime. The strategic recommendation is to enhance cybersecurity awareness and protocols, especially in high-profile custody disputes, to prevent misuse of legal and cyber channels.
2. Competing Hypotheses
Hypothesis 1: Summer Worden’s accusations were primarily driven by personal vendetta amidst a custody battle, lacking credible evidence of hacking from space.
Hypothesis 2: There was a genuine belief by Worden that her accounts were compromised, possibly due to misinterpretation of account activities or external influences.
Hypothesis 1 is more likely due to the absence of technical evidence supporting the hacking claim, Worden’s guilty plea, and the context of an acrimonious custody dispute.
3. Key Assumptions and Red Flags
Assumptions: The legal system’s decision reflects the actual events; Worden’s plea indicates acknowledgment of falsehood.
Red Flags: The complexity of hacking from the ISS and the improbability of such an event without detection.
Deception Indicators: Worden’s initial public claims contrasted with her guilty plea suggest potential manipulation of narrative for personal gain.
4. Implications and Strategic Risks
The case highlights the risk of cyber accusations being weaponized in personal disputes, potentially leading to misuse of legal resources and reputational damage. It underscores the need for robust verification mechanisms in cybercrime allegations to prevent escalation and misinformation.
5. Recommendations and Outlook
- Enhance cybersecurity education for individuals involved in high-stakes personal disputes.
- Develop protocols for rapid assessment and verification of cybercrime claims, especially involving high-profile individuals.
- Best-case scenario: Improved awareness and protocols reduce false claims and misuse of cyber allegations.
- Worst-case scenario: Continued misuse of cybercrime allegations leads to legal system overload and public mistrust.
- Most-likely scenario: Incremental improvements in verification processes and public awareness reduce similar incidents.
6. Key Individuals and Entities
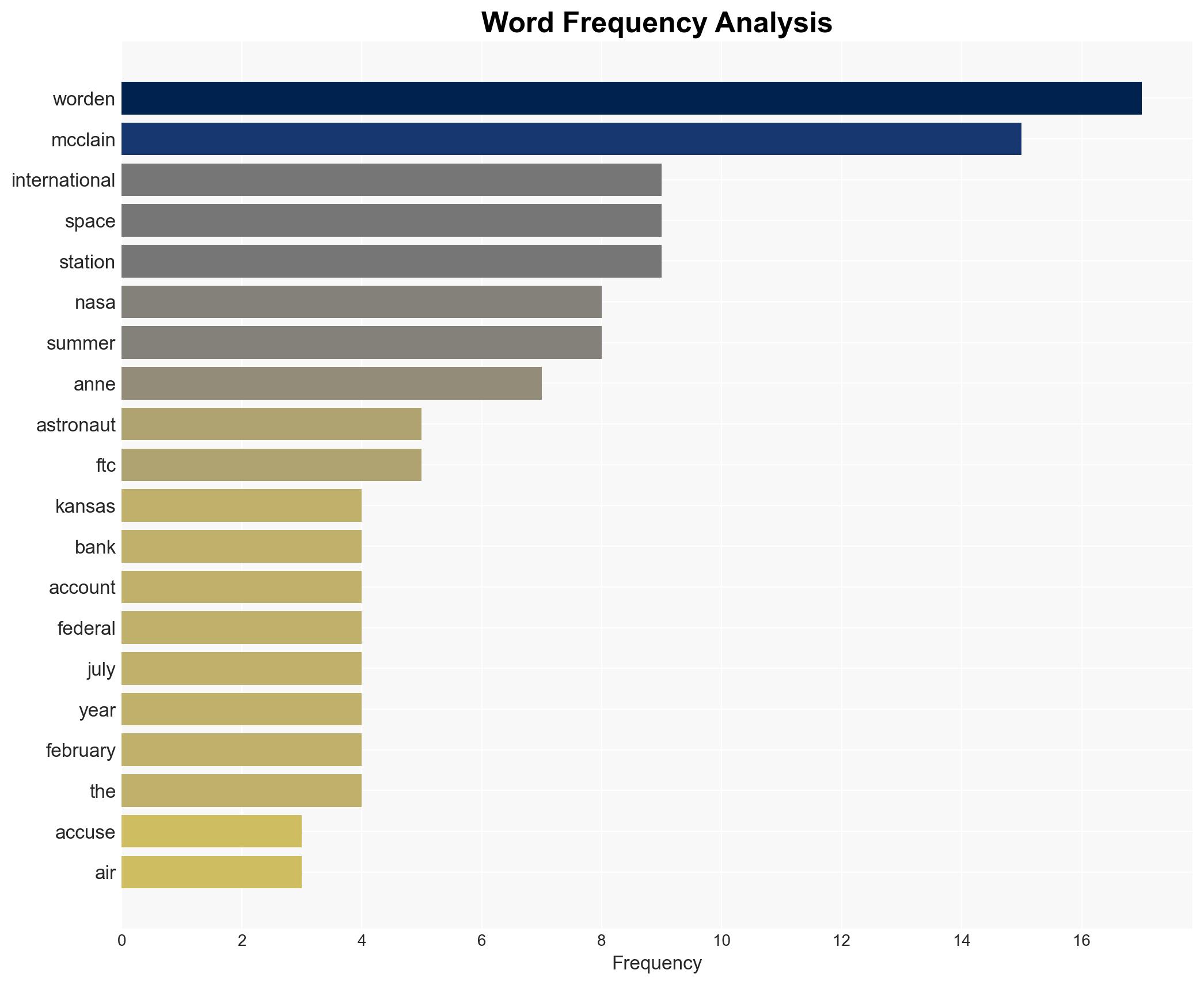
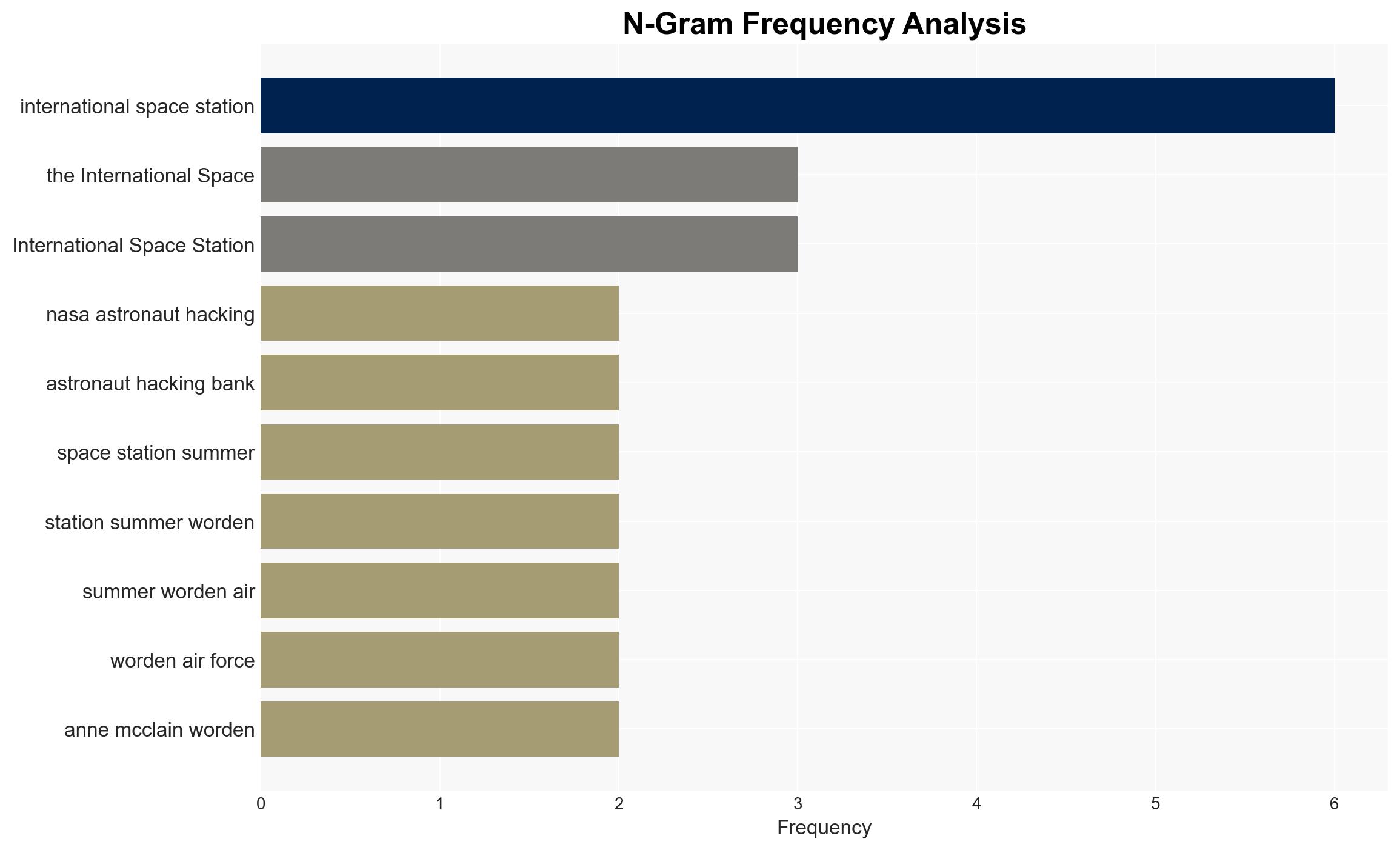
Summer Worden, Anne McClain
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·