Holy bleep Charlie Kirks security leader makes stunning revelation about cops before assassination – Wnd.com
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
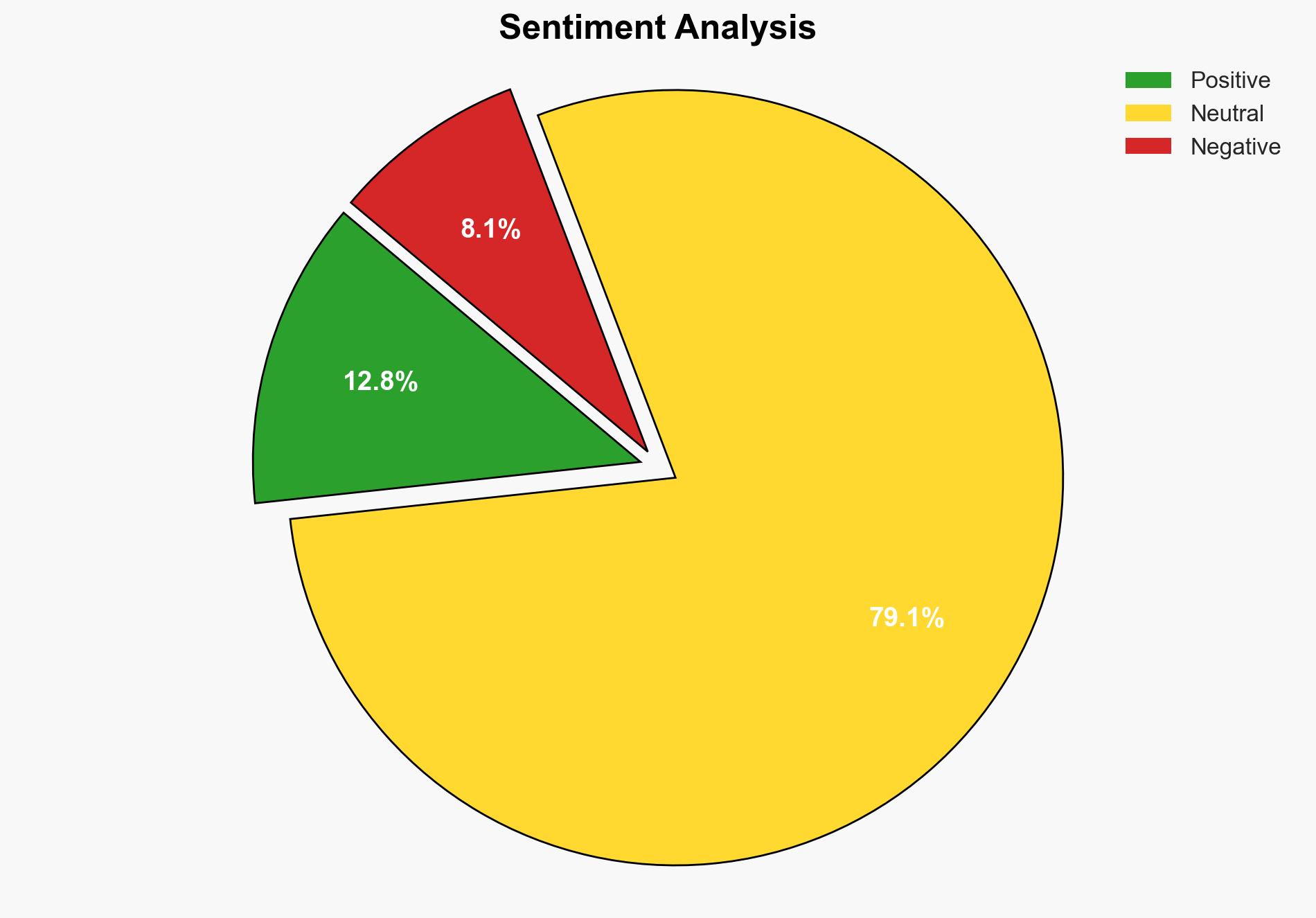
There is a moderate confidence level that the alleged security breach involving rooftop access at Utah Valley University (UVU) was due to either a failure in security protocols or a deliberate act of negligence. The most supported hypothesis is a failure in security protocols. Recommended actions include a thorough investigation into UVU’s security measures and a review of communication channels between event organizers and security personnel.
2. Competing Hypotheses
Hypothesis 1: The security breach was due to a failure in security protocols at UVU, leading to unauthorized rooftop access.
Hypothesis 2: The breach was a result of deliberate negligence or complicity by individuals within the UVU police department.
Hypothesis 1 is more likely due to the complexity and potential risk involved in orchestrating a deliberate act of negligence, which would require significant coordination and motive. The evidence suggests a lack of proper control and communication rather than intentional malfeasance.
3. Key Assumptions and Red Flags
Assumptions include the reliability of the source reporting the incident and the accuracy of the communication logs presented. Red flags include the sensational nature of the report and potential bias from the source, Wnd.com, known for its controversial reporting. The lack of official statements from UVU or law enforcement raises concerns about information gaps and possible deception.
4. Implications and Strategic Risks
The incident could lead to increased scrutiny of security protocols at educational institutions, potentially impacting public trust and event planning. Politically, it may fuel narratives of institutional incompetence or corruption. Informational risks include the spread of misinformation or conspiracy theories, potentially exacerbating tensions among stakeholders.
5. Recommendations and Outlook
- Conduct an independent investigation into the security protocols and communication failures at UVU.
- Enhance training and oversight for security personnel at events involving high-profile individuals.
- Best-case scenario: The investigation reveals procedural gaps that are addressed, restoring confidence in institutional security.
- Worst-case scenario: Evidence of deliberate negligence emerges, leading to legal and reputational consequences for UVU.
- Most-likely scenario: Procedural improvements are implemented, but public skepticism remains due to the initial sensationalism of the incident.
6. Key Individuals and Entities
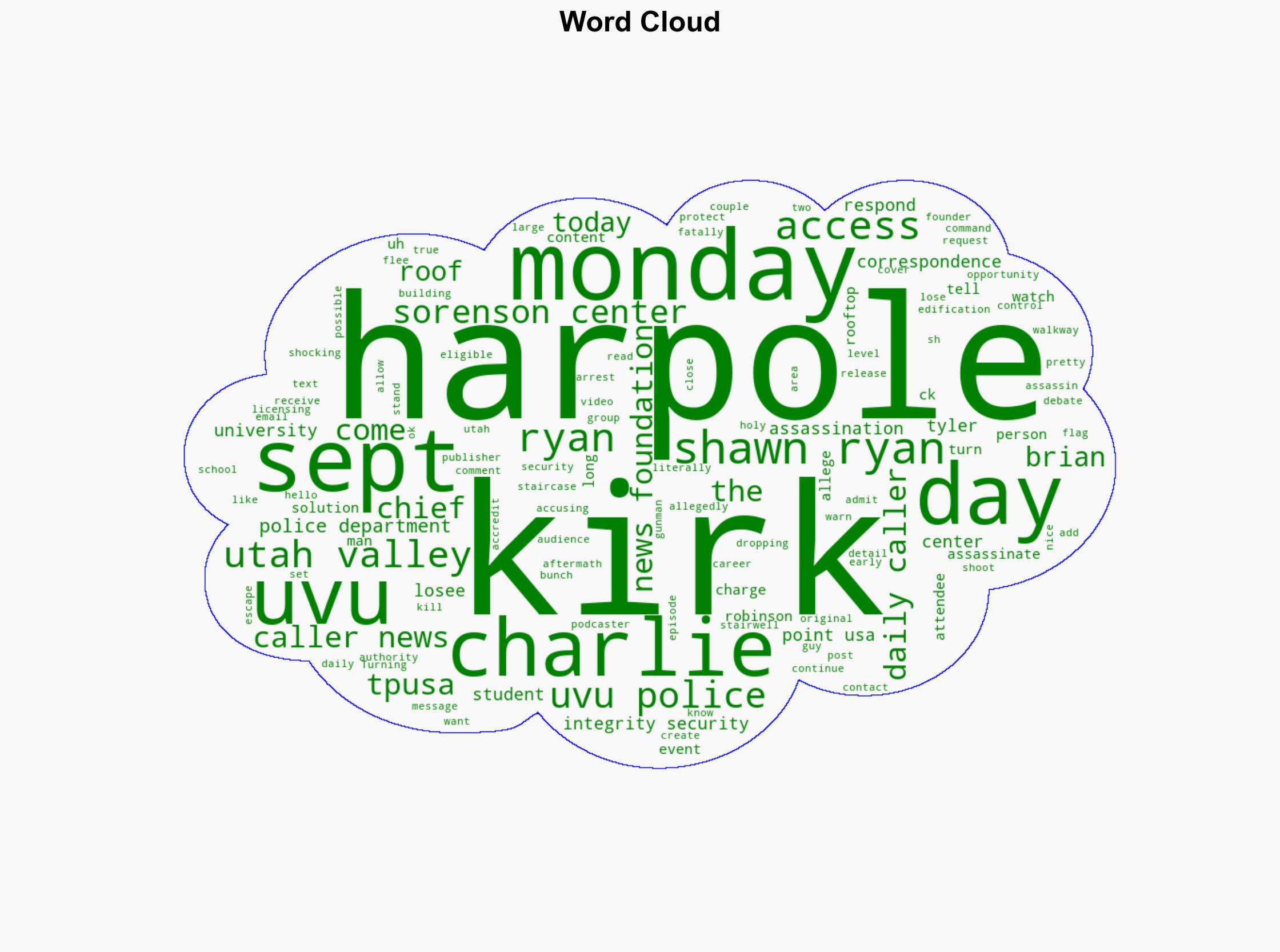
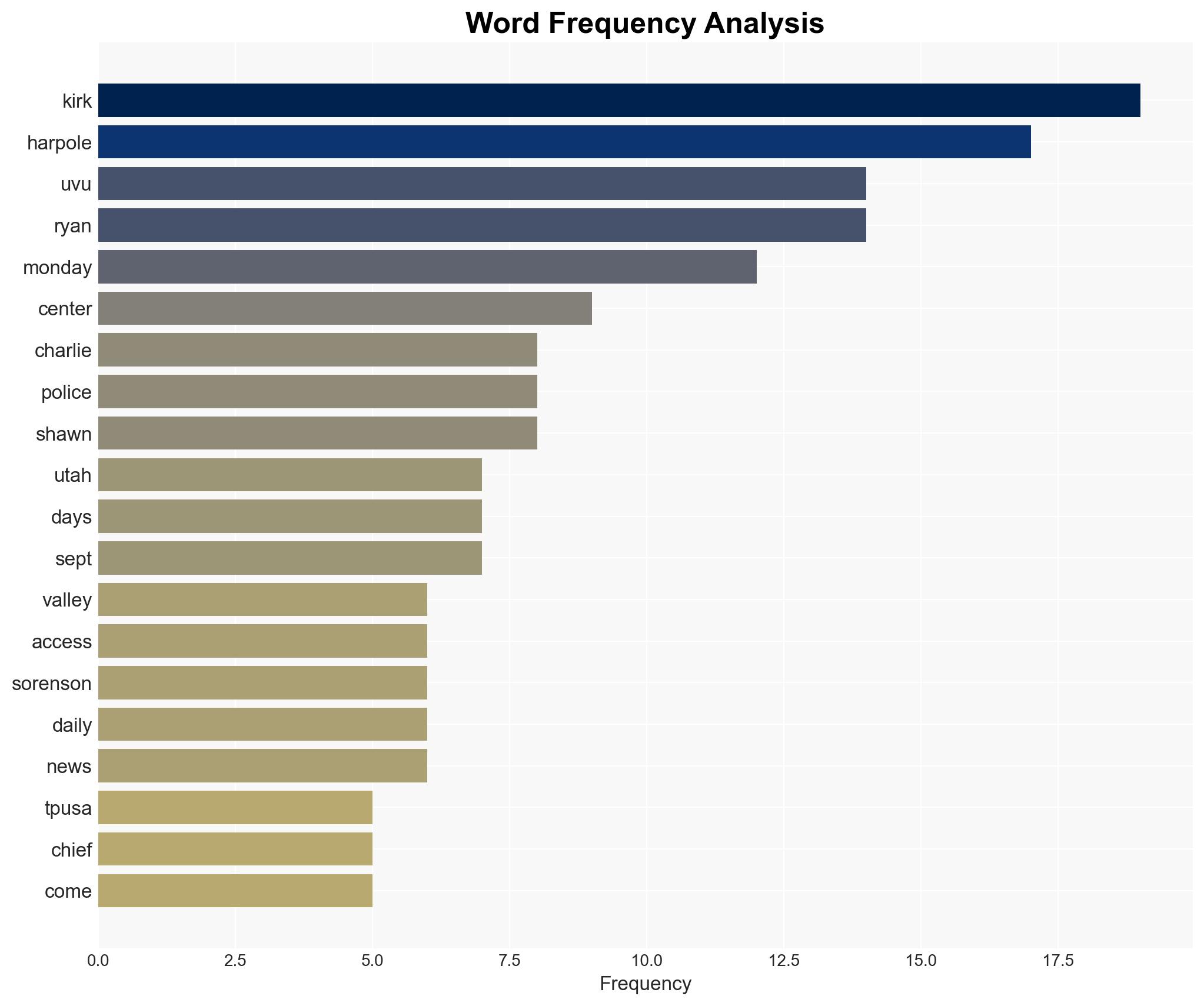
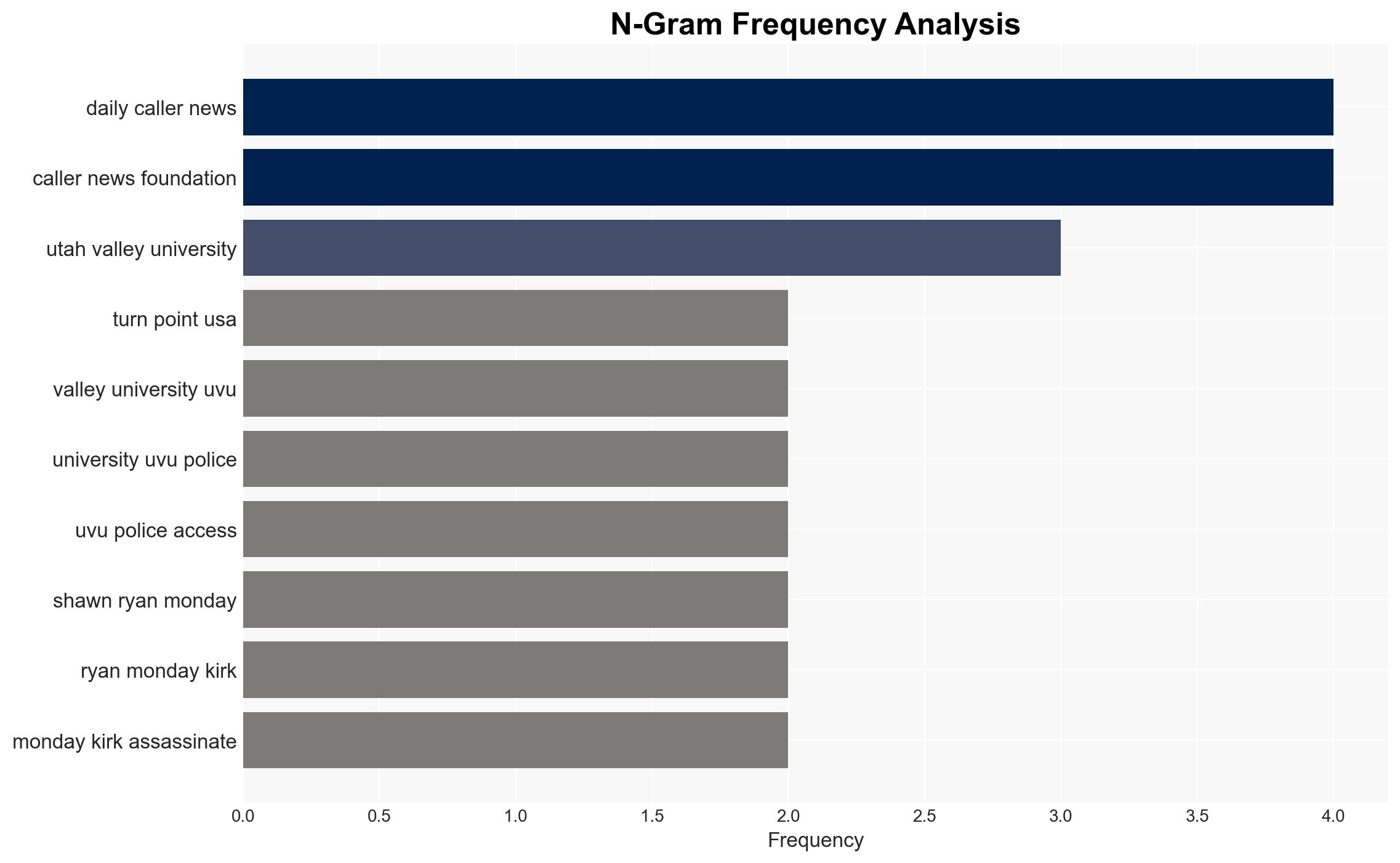
Charlie Kirk, Shawn Ryan, Brian Harpole, Tyler Robinson, Utah Valley University Police Department
7. Thematic Tags
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us