US House votes to force release of Epstein files after Republican feud – CNA
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
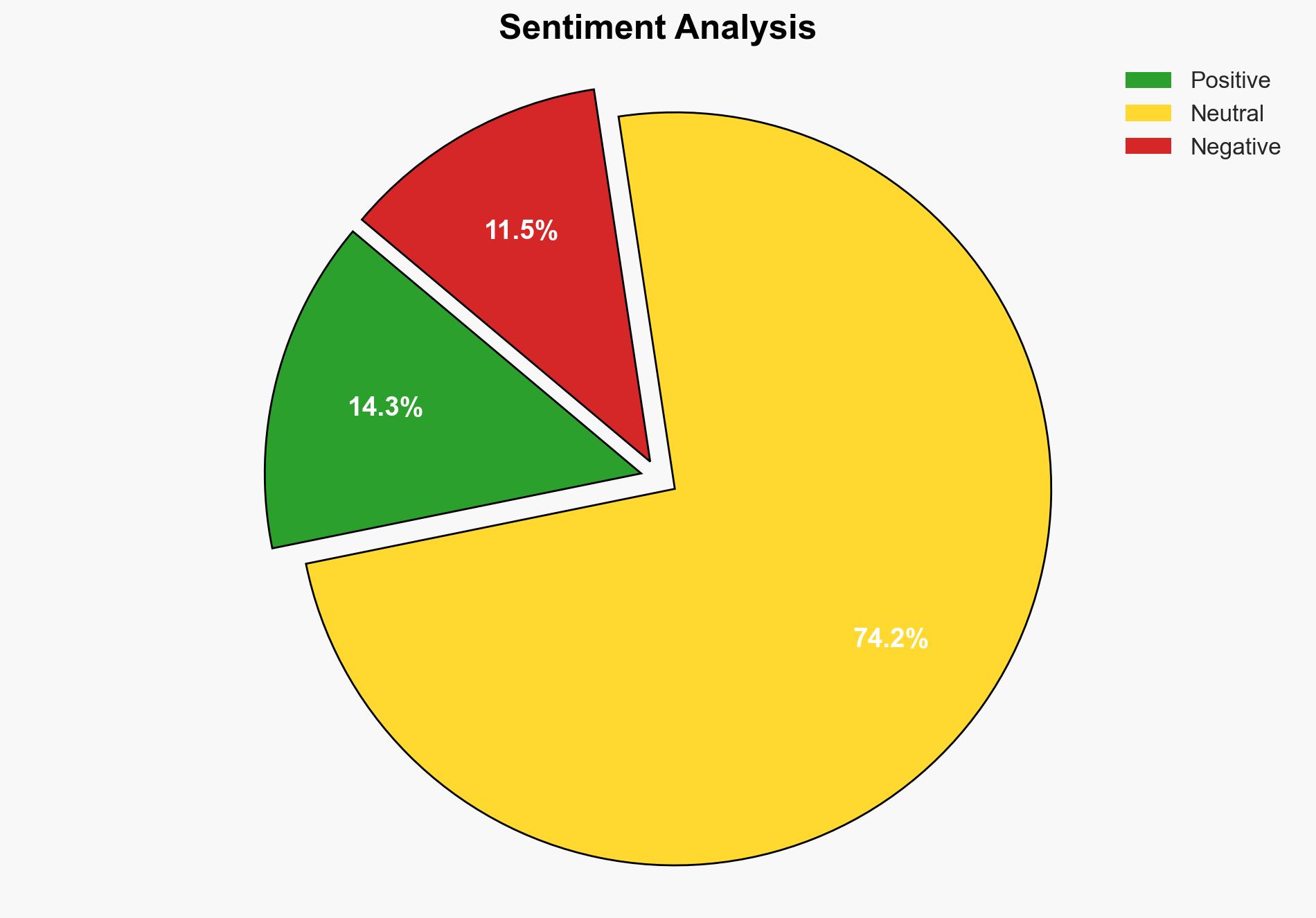
The strategic judgment is that the release of the Epstein files is primarily driven by internal political dynamics within the Republican Party, with a medium confidence level. The most supported hypothesis is that the release is a tactical move to manage internal dissent and public perception rather than a genuine push for transparency. Recommended action includes monitoring political fallout and preparing for potential misinformation campaigns.
2. Competing Hypotheses
Hypothesis 1: The release of the Epstein files is a strategic move by the Republican Party to address internal dissent and manage public perception, particularly among Trump supporters who are concerned about transparency and accountability.
Hypothesis 2: The release of the Epstein files is primarily a bipartisan effort driven by a genuine desire for transparency and justice for Epstein’s victims, with political considerations being secondary.
Hypothesis 1 is more likely due to the timing of the release, the internal Republican dynamics, and the emphasis on managing public perception and approval ratings, as indicated by the swift legislative process and the involvement of key Republican figures.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the release of the files will provide significant new information that could impact public opinion and political dynamics. It is also assumed that the internal Republican dynamics are a primary driver of this decision.
Red Flags: The abrupt change in position by President Trump and the swift legislative process may indicate a reactive rather than proactive strategy, suggesting potential underlying issues or pressures.
Deception Indicators: The framing of the release as a bipartisan effort may obscure the primary political motivations, and there may be attempts to control the narrative around the release to minimize damage to key political figures.
4. Implications and Strategic Risks
The release of the Epstein files could lead to significant political fallout, particularly if new information implicates high-profile individuals. This could exacerbate existing political divisions and lead to increased scrutiny of political figures. There is also a risk of misinformation campaigns aimed at shaping public perception and deflecting blame. The situation could escalate into a broader political crisis if not managed carefully.
5. Recommendations and Outlook
- Monitor the release of the files and subsequent media coverage to identify emerging narratives and misinformation campaigns.
- Engage in proactive communication strategies to manage public perception and mitigate potential political fallout.
- Prepare for potential legal and political challenges that may arise from the release of the files.
- Best-case scenario: The release leads to increased transparency and accountability, with minimal political fallout.
- Worst-case scenario: The release triggers a major political crisis, with significant damage to public trust and political stability.
- Most-likely scenario: The release results in moderate political fallout, with ongoing efforts to manage public perception and internal party dynamics.
6. Key Individuals and Entities
Donald Trump, Marjorie Taylor Greene, Thomas Massie, Ro Khanna, Jeffrey Epstein
7. Thematic Tags
Cybersecurity, Political Dynamics, Transparency, Misinformation, Public Perception
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us