Pennsylvania Office of the Attorney General OAG confirms data breach after August attack – Securityaffairs.com
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pennsylvania Office of the Attorney General Data Breach
1. BLUF (Bottom Line Up Front)
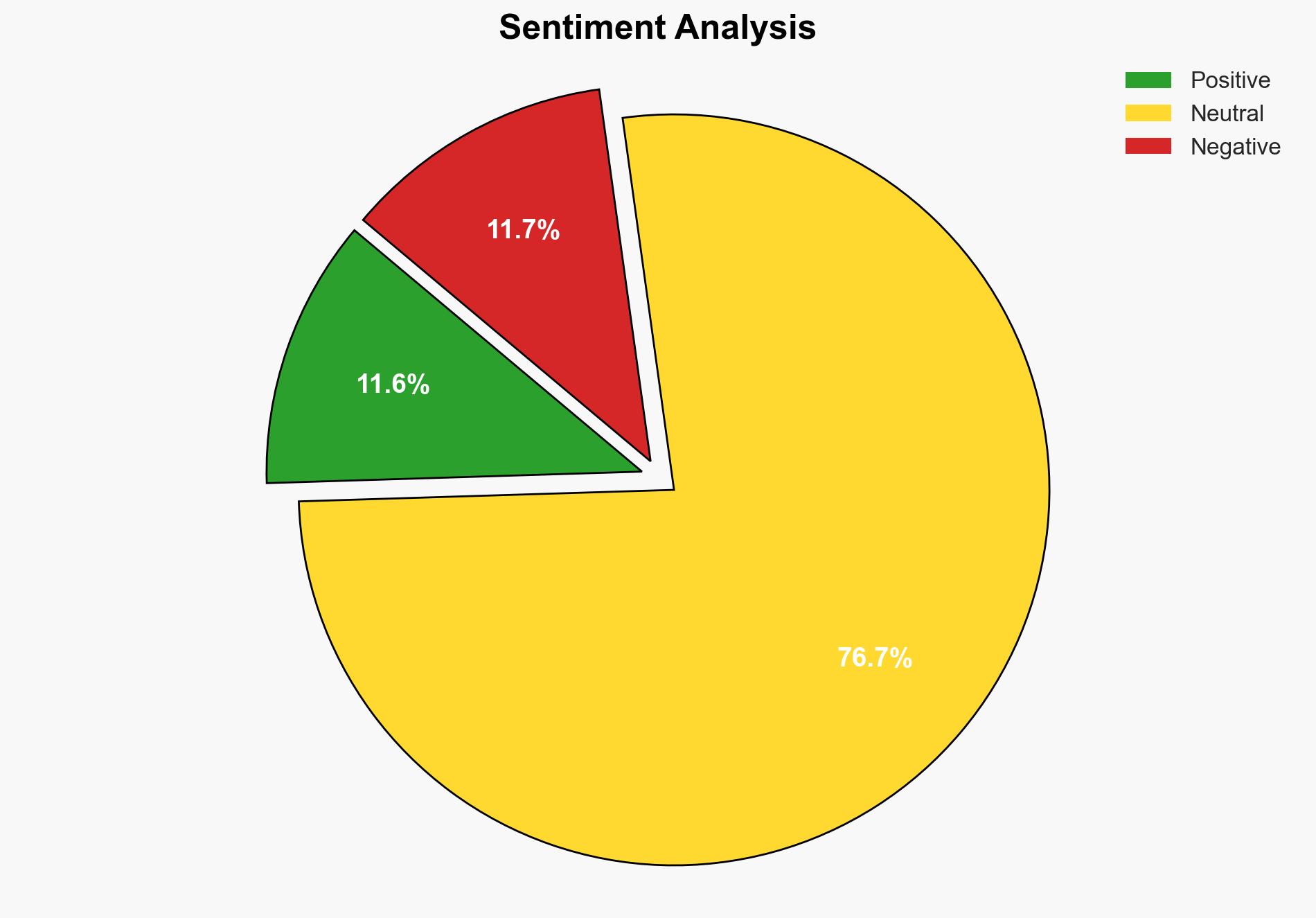
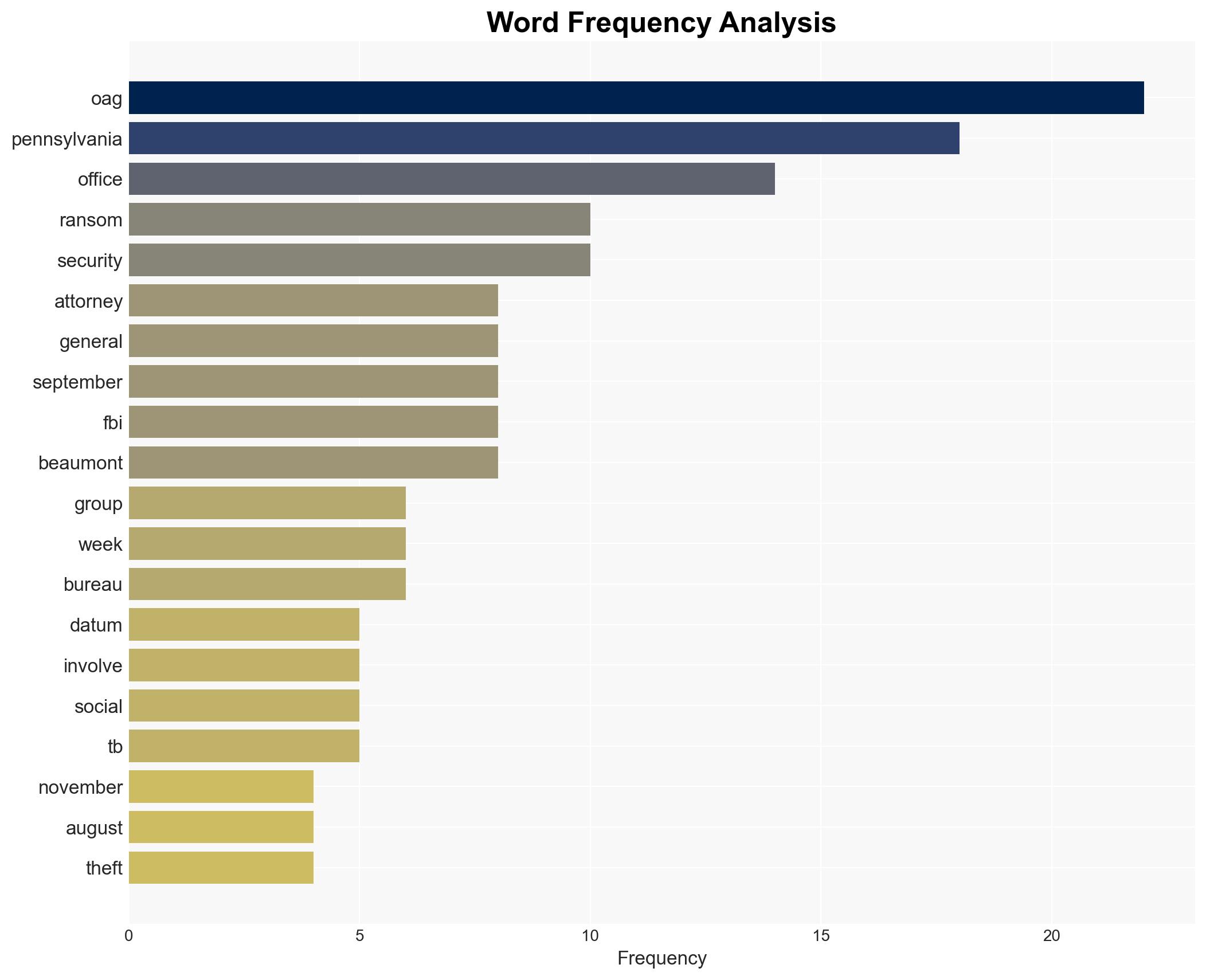
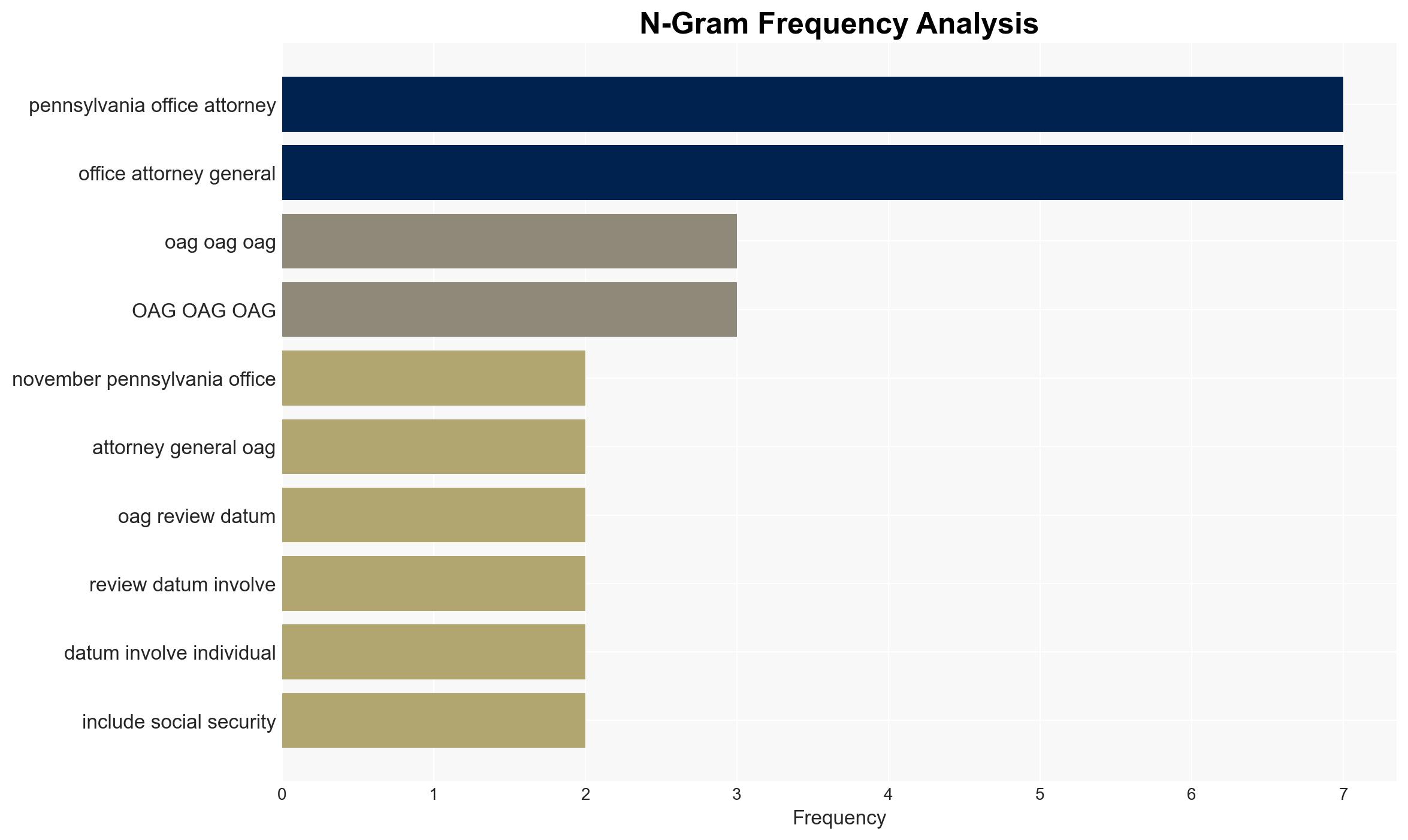
The Pennsylvania Office of the Attorney General (OAG) suffered a data breach following a ransomware attack attributed to a ransom group exploiting a Citrix NetScaler vulnerability. The breach involved sensitive data, including social security numbers and medical information, affecting numerous individuals. The most supported hypothesis is that the attack was conducted by a financially motivated cybercriminal group exploiting known vulnerabilities. Confidence Level: Moderate. Recommended actions include enhancing cybersecurity measures, particularly around known vulnerabilities, and improving incident response protocols.
2. Competing Hypotheses
Hypothesis 1: The attack was conducted by a financially motivated cybercriminal group exploiting the Citrix NetScaler vulnerability (CitrixBleed) to obtain sensitive data for extortion purposes.
Hypothesis 2: The attack was a state-sponsored operation aimed at gathering intelligence on law enforcement activities and capabilities within the Pennsylvania OAG.
Assessment: Hypothesis 1 is more likely due to the nature of the attack (ransomware) and the public claim of responsibility by a known ransom group. The exploitation of a known vulnerability aligns with typical cybercriminal behavior rather than sophisticated state-sponsored tactics. Hypothesis 2 lacks supporting evidence and is less consistent with the observed attack pattern.
3. Key Assumptions and Red Flags
Assumptions: The attribution to a ransom group is accurate based on their claims and the exploitation method. The data breach was primarily financially motivated.
Red Flags: The possibility of misattribution due to false flag operations. The ransom group’s public claim could be a deception tactic to mask a more strategic espionage operation.
4. Implications and Strategic Risks
The breach poses significant risks, including potential identity theft and financial fraud for affected individuals. It also undermines public trust in the OAG’s ability to protect sensitive information. Politically, the breach could lead to increased scrutiny and pressure on state cybersecurity policies. Economically, it may result in increased costs for cybersecurity enhancements and potential legal liabilities. Cyber risks include further exploitation of vulnerabilities if not addressed promptly.
5. Recommendations and Outlook
- Enhance cybersecurity measures, focusing on patching known vulnerabilities such as Citrix NetScaler.
- Improve incident response protocols and conduct regular cybersecurity training for staff.
- Engage in public communication to restore trust and provide support to affected individuals.
- Best-case scenario: The breach is contained, and no further exploitation occurs, with minimal impact on individuals.
- Worst-case scenario: Further breaches occur due to unaddressed vulnerabilities, leading to significant financial and reputational damage.
- Most-likely scenario: The breach results in moderate financial and reputational impact, with increased cybersecurity measures preventing future incidents.
6. Key Individuals and Entities
Kevin Beaumont (Cybersecurity Researcher), Citrix (Technology Company), Pennsylvania Office of the Attorney General, FBI (Federal Bureau of Investigation).
7. Thematic Tags
Cybersecurity, Data Breach, Ransomware, Vulnerability Exploitation, Information Security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us