Stealth-patched FortiWeb vulnerability under active exploitation CVE-2025-58034 – Help Net Security
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Stealth-patched FortiWeb Vulnerability Under Active Exploitation CVE-2025-58034
1. BLUF (Bottom Line Up Front)
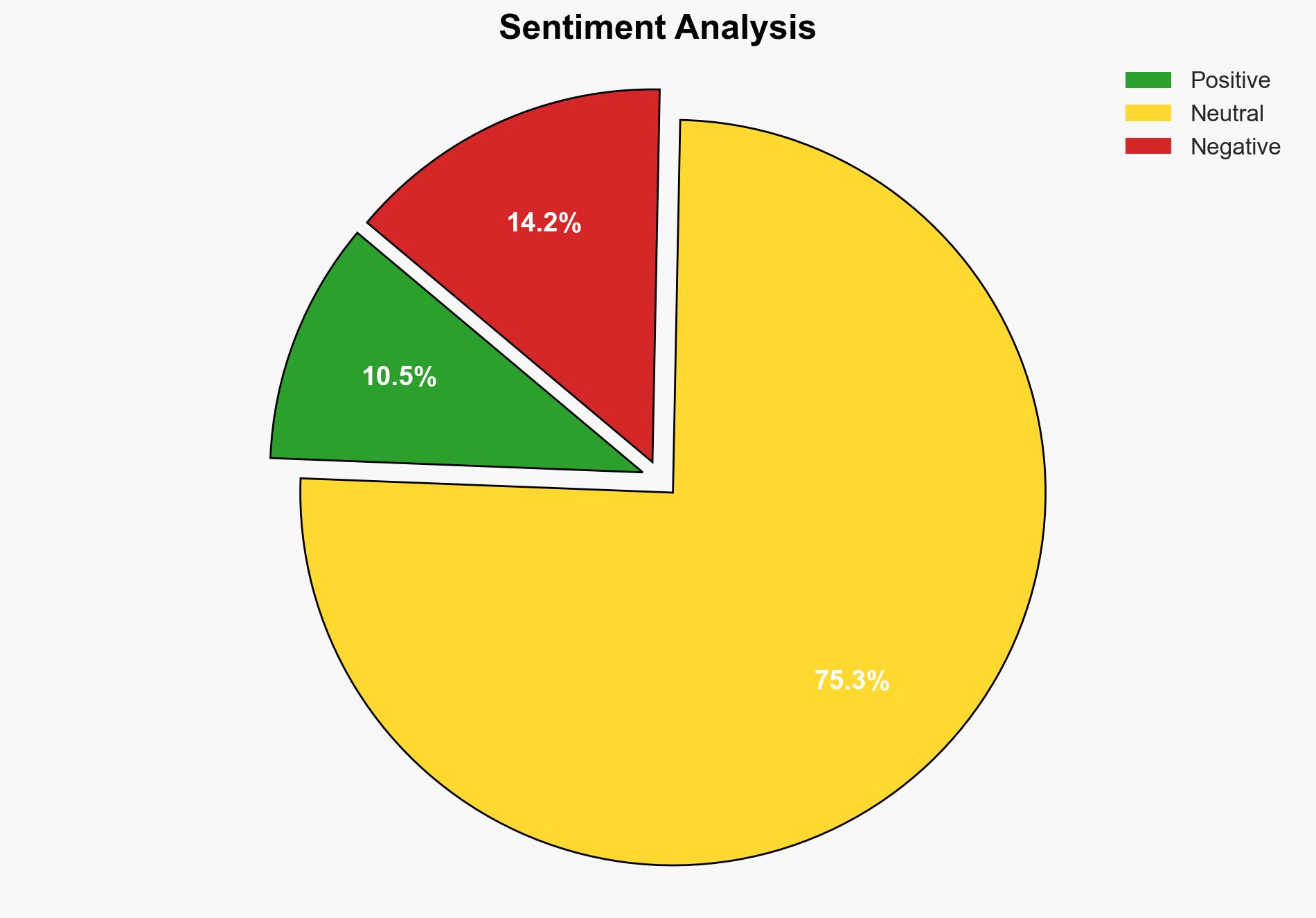
There is a high confidence level that the FortiWeb vulnerability CVE-2025-58034 is being actively exploited, posing significant risks to organizations using affected versions. The most supported hypothesis is that the vulnerability was stealth-patched without public disclosure, leading to increased exploitation risks. Immediate action is recommended for organizations to upgrade to patched versions and implement temporary mitigations.
2. Competing Hypotheses
Hypothesis 1: The vulnerability was stealth-patched by Fortinet without public disclosure, leading to active exploitation due to lack of awareness.
Hypothesis 2: The vulnerability was publicly disclosed, but organizations failed to act promptly, resulting in exploitation.
Hypothesis 1 is more likely due to the evidence of Fortinet’s delayed public acknowledgment and the subsequent rapid increase in exploitation reports, suggesting a lack of initial awareness among users.
3. Key Assumptions and Red Flags
Assumptions include the accuracy of the reported exploitation and the effectiveness of the patch. Red flags include potential underreporting of exploitation incidents and the possibility of a coordinated misinformation campaign to downplay the vulnerability’s impact. Deception indicators could involve false claims of patch effectiveness or exploitation severity.
4. Implications and Strategic Risks
The primary risk is cyber, with potential political and economic implications if critical infrastructure or government systems are compromised. Escalation scenarios include widespread data breaches, financial loss, and reputational damage to Fortinet and affected organizations. The release of a proof-of-concept exploit could exacerbate these risks.
5. Recommendations and Outlook
- Organizations should immediately upgrade to the patched FortiWeb versions and apply temporary mitigations, such as disabling vulnerable interfaces.
- Monitor for signs of compromise and subscribe to threat intelligence updates.
- Best-case scenario: Rapid patch adoption mitigates exploitation risks.
- Worst-case scenario: Widespread exploitation leads to significant data breaches and financial losses.
- Most-likely scenario: Continued exploitation at a moderate level until patch adoption increases.
6. Key Individuals and Entities
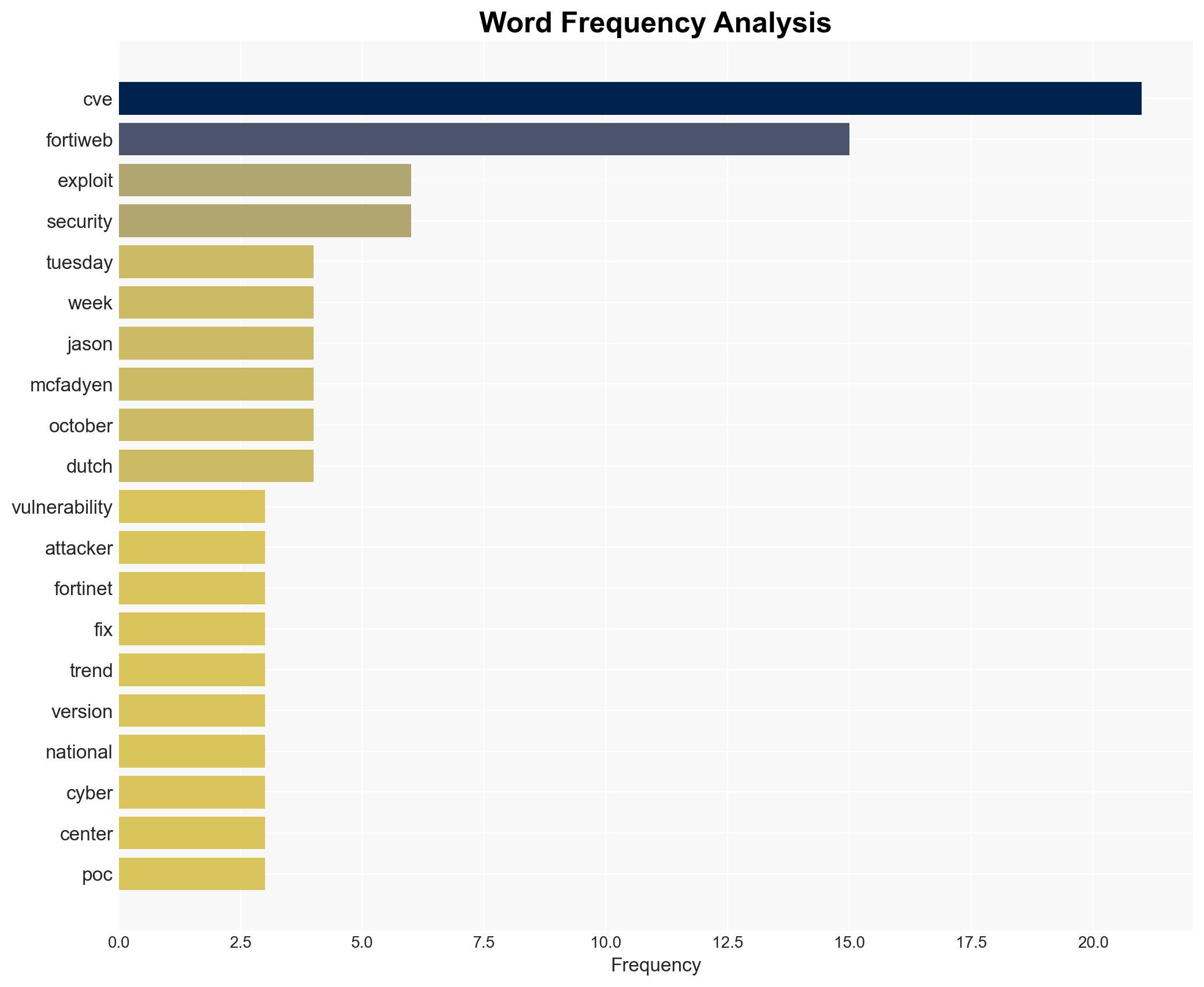
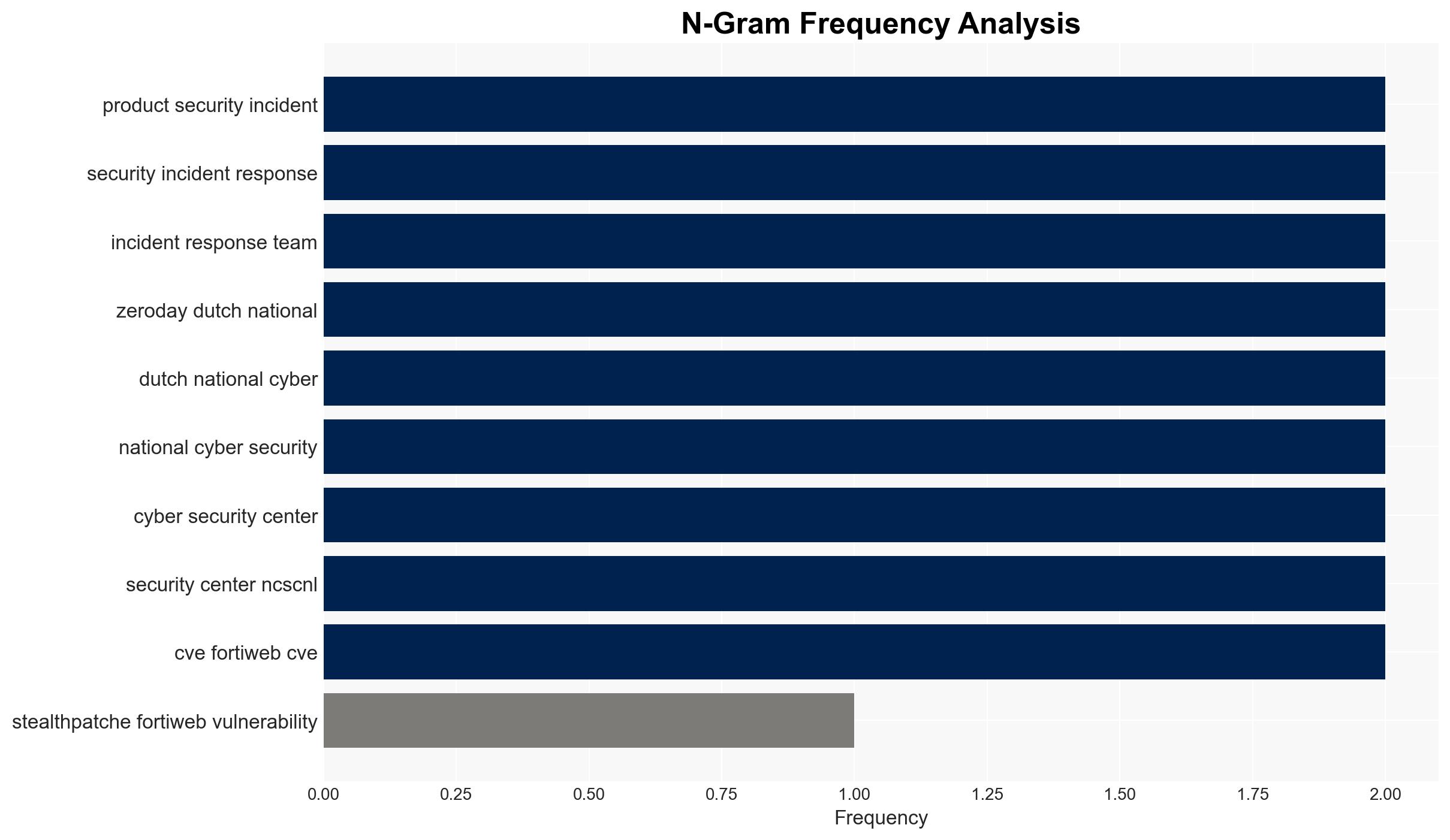
Jason McFadyen (Trend Micro researcher), Fortinet Product Security Incident Response Team, Dutch National Cyber Security Center (NCSC-NL).
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us