TP-Link Tapo Smart WiFi Outdoor Dual AC Outlet Plug Black 16 Free SH – Slickdeals.net
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: TP-Link Tapo Smart WiFi Outdoor Dual AC Outlet Plug Analysis
1. BLUF (Bottom Line Up Front)
With a moderate confidence level, the most supported hypothesis is that the TP-Link Tapo Smart WiFi Outdoor Dual AC Outlet Plug is a well-received product within the consumer electronics market, primarily due to its compatibility with major smart home ecosystems and positive user feedback. Strategic action should focus on monitoring consumer trends and potential vulnerabilities in smart home devices.
2. Competing Hypotheses
Hypothesis 1: The TP-Link Tapo Smart WiFi Outdoor Dual AC Outlet Plug is a highly competitive product in the smart home market due to its compatibility with multiple smart home systems (Google Home, Amazon Alexa, Apple HomeKit) and positive user reviews.
Hypothesis 2: The product faces significant competition and potential issues due to user concerns over app integration and the transition from older Kasa versions, which could impact its market position.
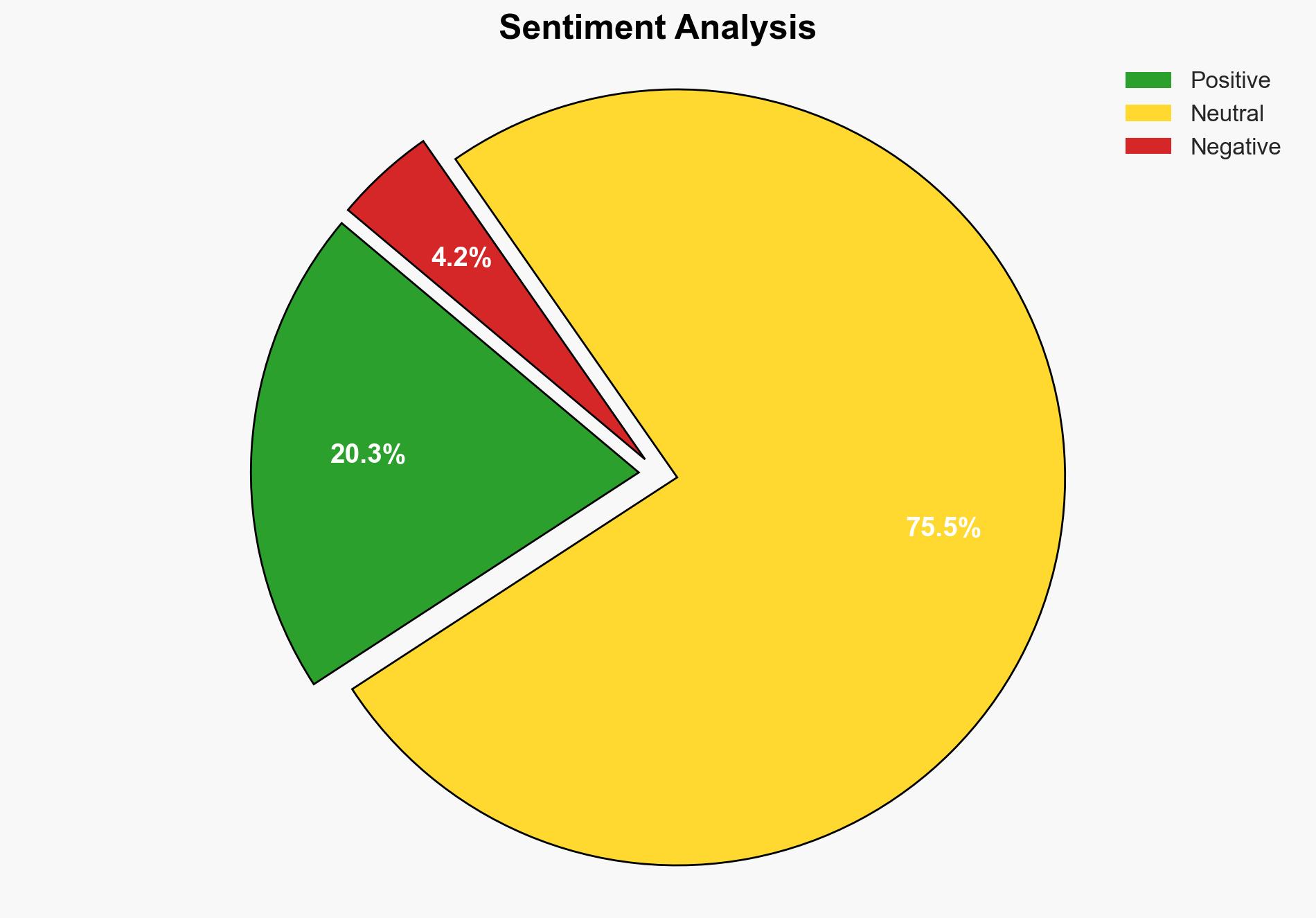
The first hypothesis is more likely given the positive feedback on functionality and integration with major smart home platforms, which are critical factors for consumer adoption. However, the second hypothesis cannot be entirely dismissed due to noted concerns about app migration and potential user resistance to change.
3. Key Assumptions and Red Flags
Assumptions: The analysis assumes that user reviews and community feedback accurately reflect the broader consumer sentiment. It also assumes that compatibility with major smart home systems is a primary driver of consumer choice.
Red Flags: Potential bias in user reviews, as they may not represent the full spectrum of user experiences. The reliance on community member feedback could skew perceptions if not representative of the general market.
Deception Indicators: There is no direct evidence of deception, but the possibility of manipulated reviews or promotional bias should be considered.
4. Implications and Strategic Risks
The primary strategic risk is the potential for cybersecurity vulnerabilities inherent in smart home devices, which could lead to privacy breaches or unauthorized access. Additionally, the transition from Kasa to Tapo could alienate existing users, impacting brand loyalty and market share. The competitive landscape may also shift if competitors offer superior integration or security features.
5. Recommendations and Outlook
- Conduct a thorough cybersecurity assessment of the TP-Link Tapo Smart WiFi Outdoor Dual AC Outlet Plug to identify and mitigate potential vulnerabilities.
- Monitor consumer feedback on app integration and address any migration issues from Kasa to Tapo to maintain user satisfaction.
- Best-case scenario: The product strengthens its market position through enhanced security features and seamless integration.
- Worst-case scenario: Security vulnerabilities or poor app integration lead to a loss of consumer trust and market share.
- Most-likely scenario: The product maintains a stable market presence with ongoing improvements in app functionality and security.
6. Key Individuals and Entities
Community member “gabe” is noted for identifying the deal, indicating active consumer engagement. Other users such as “holysinnov,” “jvarghesenov,” “eyetron,” “mrwrigleyfield,” “macfamily,” and “caligurl” provide feedback on product performance and integration.
7. Thematic Tags
Cybersecurity, Smart Home Technology, Consumer Electronics, Market Analysis
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us