The Illusion of Privacy: Most Users Prioritize Convenience Over Data Protection
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Privacy Preferences and Behavioral Dynamics
1. BLUF (Bottom Line Up Front)
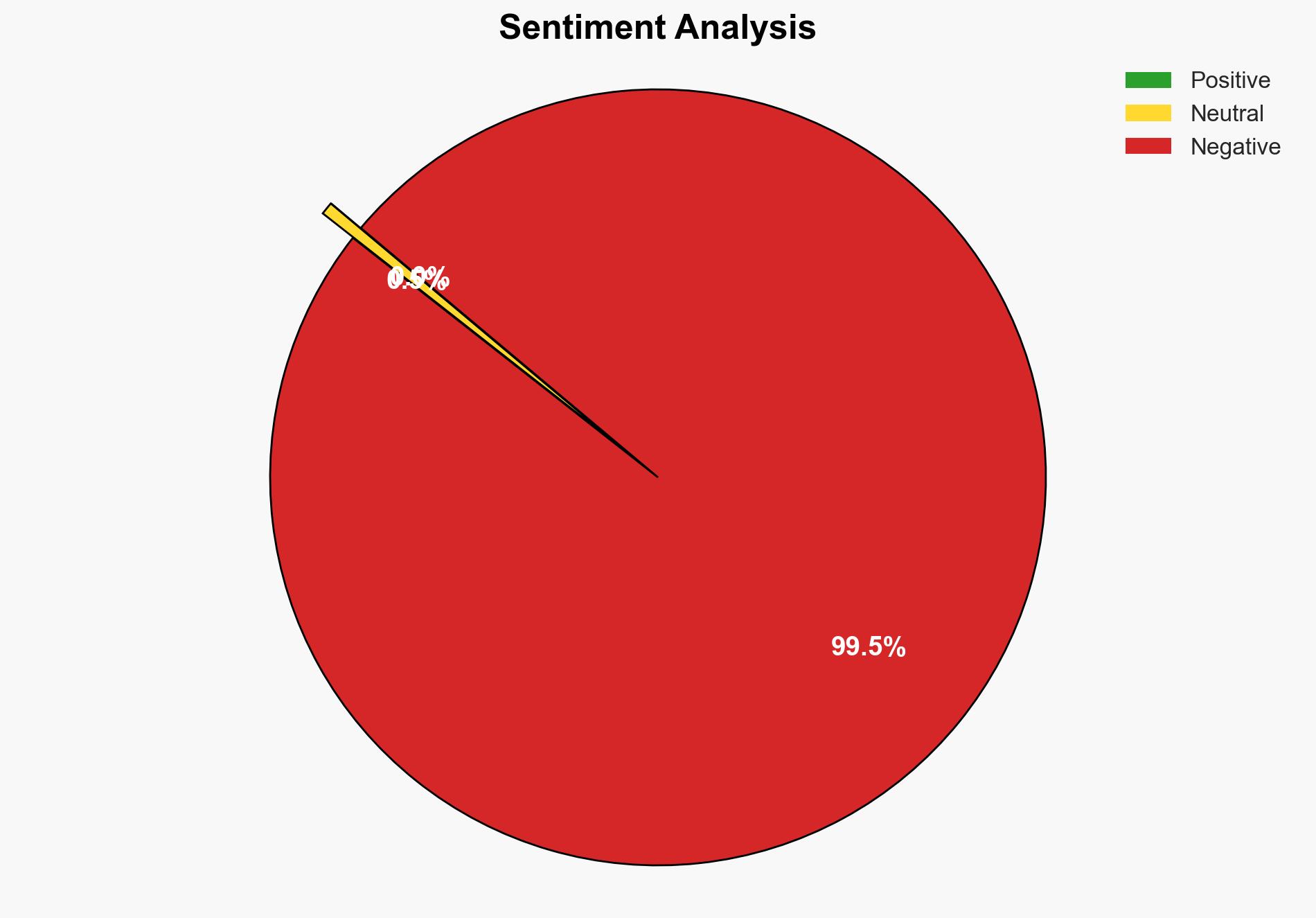
The strategic judgment is that convenience significantly outweighs privacy concerns for the majority of users, driven by systemic design choices and psychological tendencies. Confidence Level: High. Recommended action includes promoting awareness and developing seamless privacy-enhancing technologies to shift user behavior.
2. Competing Hypotheses
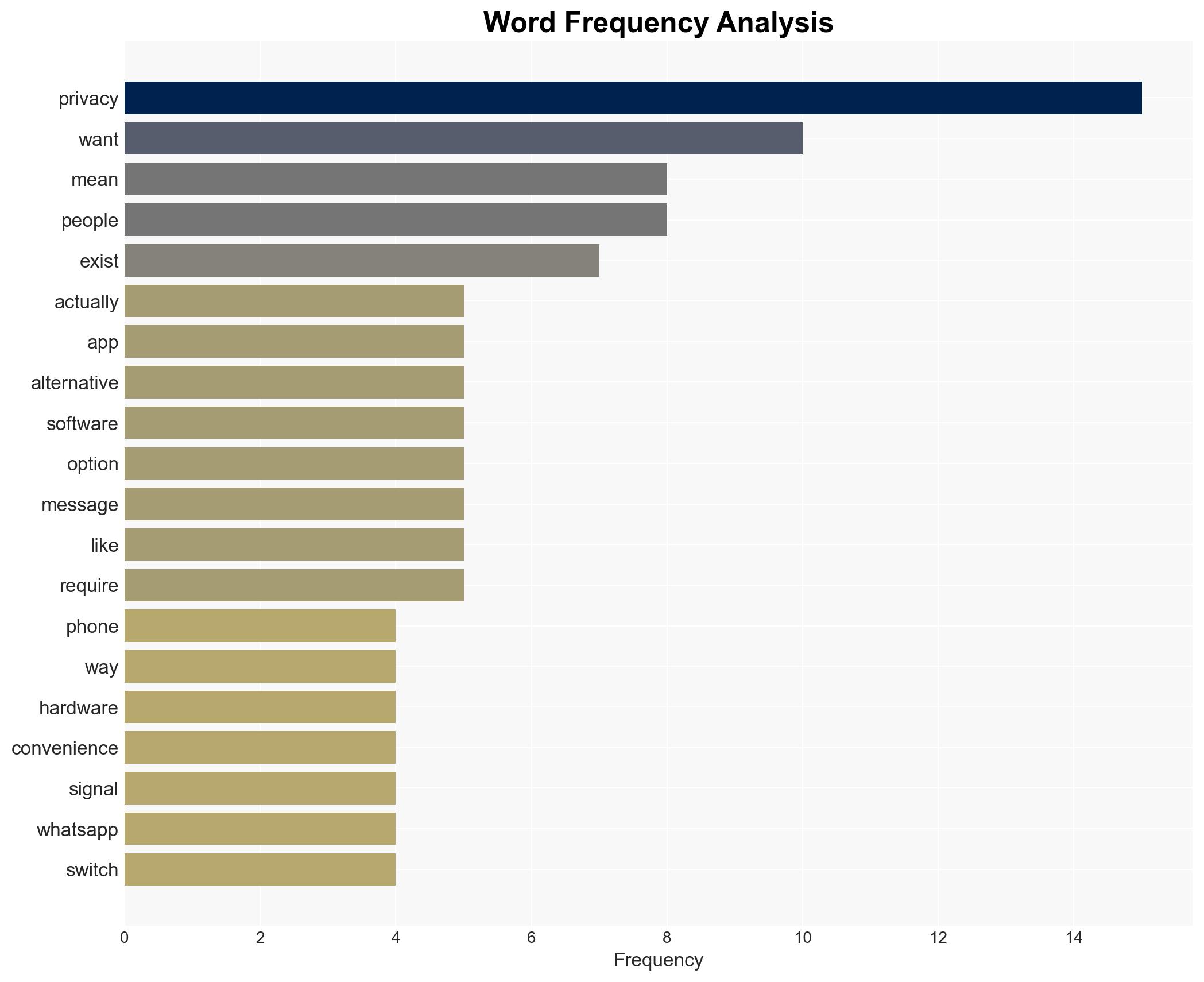
Hypothesis 1: The majority of users prioritize convenience over privacy due to ingrained habits and the seamless integration of non-privacy-focused technologies.
Hypothesis 2: Users genuinely desire privacy but lack awareness and access to user-friendly privacy-focused alternatives.
Hypothesis 1 is more likely given the evidence of widespread adoption of convenience-oriented technologies despite available privacy-focused alternatives. The friction and effort required to adopt privacy-centric solutions deter users, supporting the notion that convenience is prioritized.
3. Key Assumptions and Red Flags
Assumptions: Users are aware of privacy risks but choose convenience due to ease of use. Privacy-focused alternatives are inherently less convenient.
Red Flags: Potential bias in assuming all users are aware of privacy risks. The possibility of underestimating the impact of effective privacy education and technology improvements.
4. Implications and Strategic Risks
The preference for convenience over privacy can lead to increased data vulnerability, exploitation by surveillance capitalism, and erosion of personal freedoms. Politically, this may result in regulatory challenges and public backlash. Economically, companies focusing on convenience may dominate, stifling innovation in privacy technologies. Cyber risks include heightened exposure to data breaches and surveillance.
5. Recommendations and Outlook
- Develop and promote privacy-focused technologies that do not compromise on convenience.
- Increase public awareness and education on privacy risks and solutions.
- Encourage regulatory frameworks that incentivize privacy by design.
- Best-case scenario: Seamless integration of privacy and convenience leads to widespread adoption of privacy-focused technologies.
- Worst-case scenario: Continued dominance of convenience-oriented technologies exacerbates privacy erosion.
- Most-likely scenario: Incremental improvements in privacy technologies with slow adoption due to convenience inertia.
6. Key Individuals and Entities
Entities: Big Tech companies (e.g., Google, Facebook), privacy-focused organizations (e.g., Signal, ProtonMail).
7. Thematic Tags
Cybersecurity, Privacy, Technology Adoption, User Behavior
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us