Setting Up the On-Premises Data Gateway for the Fabric Modern Data Platform
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Configuring the On-Premises Data Gateway for The Fabric Modern Data Platform
1. BLUF (Bottom Line Up Front)
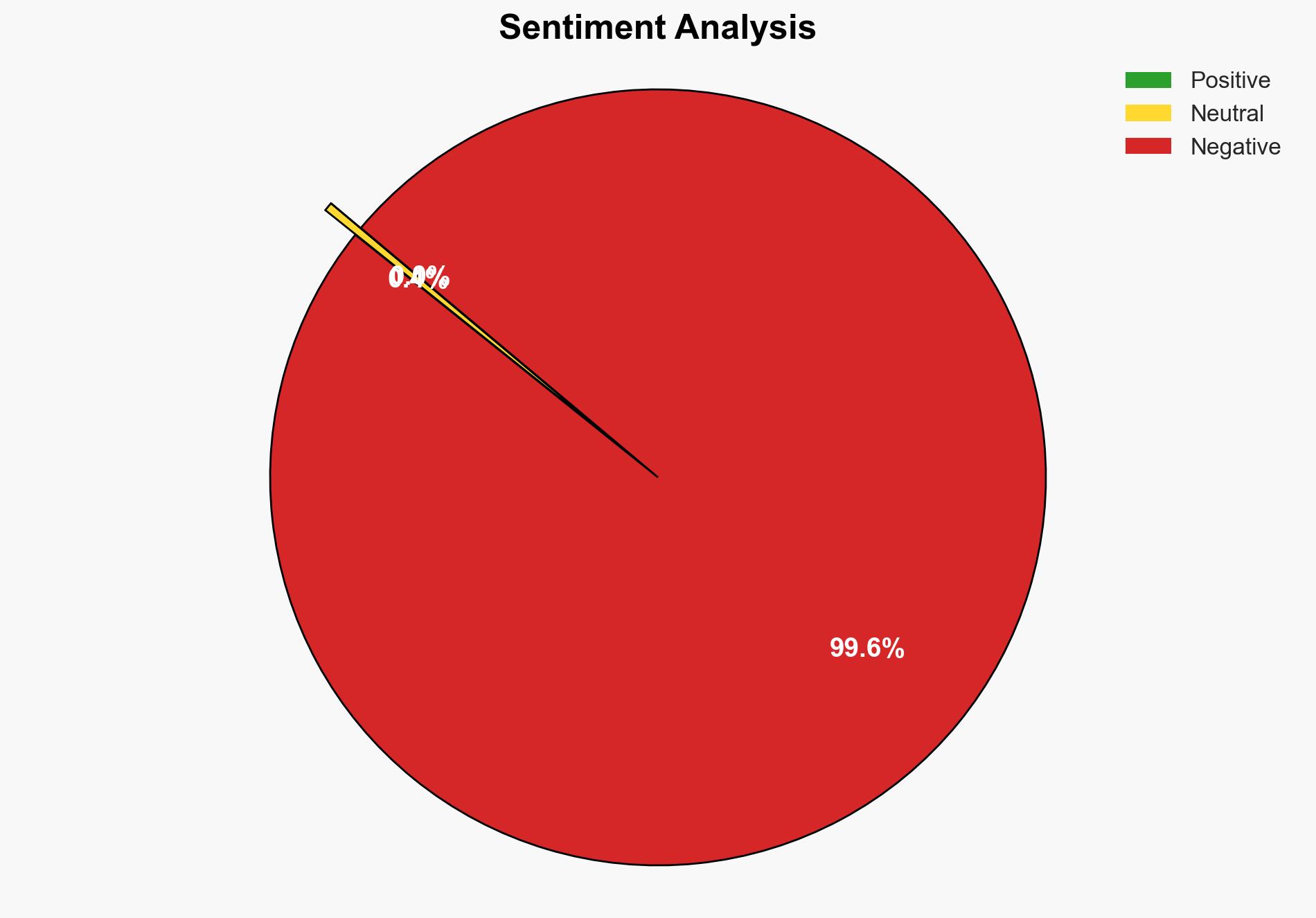
The most supported hypothesis is that the complexity and potential misconfigurations in setting up the on-premises data gateway for The Fabric Modern Data Platform pose significant cybersecurity risks, particularly related to unauthorized access and data breaches. Confidence Level: Moderate. Recommended action includes enhancing security protocols and providing comprehensive training for personnel involved in the configuration process.
2. Competing Hypotheses
Hypothesis 1: The primary risk associated with configuring the on-premises data gateway is cybersecurity vulnerabilities due to complex setup procedures and potential misconfigurations.
Hypothesis 2: The primary risk is operational inefficiency and data integration challenges, rather than cybersecurity threats, due to the intricate nature of hybrid cloud environments.
Hypothesis 1 is more likely given the evidence of login failures, certificate trust issues, and the need for secure HTTPS connections, which highlight potential security gaps. Hypothesis 2, while plausible, lacks direct evidence of operational inefficiencies being the primary concern.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that personnel configuring the gateway have adequate technical expertise and that all necessary security protocols are followed. There is also an assumption that the existing infrastructure is capable of supporting the hybrid configuration without additional vulnerabilities.
Red Flags: Frequent login errors and certificate trust issues indicate potential misconfigurations or insufficient security measures. The reliance on multi-factor authentication and HTTPS suggests awareness of security needs, but the failure to establish secure connections raises concerns.
4. Implications and Strategic Risks
The primary implication is the risk of cybersecurity breaches, which could lead to unauthorized data access and potential data loss. This risk is exacerbated by the hybrid nature of the setup, which involves both on-premises and cloud components. Escalation scenarios include targeted cyberattacks exploiting misconfigurations or vulnerabilities in the gateway setup, leading to broader network compromises.
5. Recommendations and Outlook
- Conduct a thorough security audit of the gateway configuration process to identify and rectify potential vulnerabilities.
- Provide comprehensive training for IT personnel on secure configuration practices and the importance of maintaining updated security protocols.
- Implement continuous monitoring and logging to detect and respond to unauthorized access attempts promptly.
- Best-case scenario: Successful mitigation of security risks with improved operational efficiency and secure data integration.
- Worst-case scenario: Significant data breach due to unresolved vulnerabilities, leading to data loss and reputational damage.
- Most-likely scenario: Incremental improvements in security posture with ongoing challenges in managing hybrid cloud complexities.
6. Key Individuals and Entities
No specific individuals are mentioned in the provided text. The focus is on the roles of IT personnel responsible for configuring and managing the data gateway.
7. Thematic Tags
Cybersecurity, Data Integration, Hybrid Cloud, IT Configuration, Risk Management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us