US Emergency Alert Systems Compromised After Cyberattack on OnSolve CodeRED Platform
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Emergency alert systems across US disrupted following OnSolve CodeRED cyberattack
1. BLUF (Bottom Line Up Front)
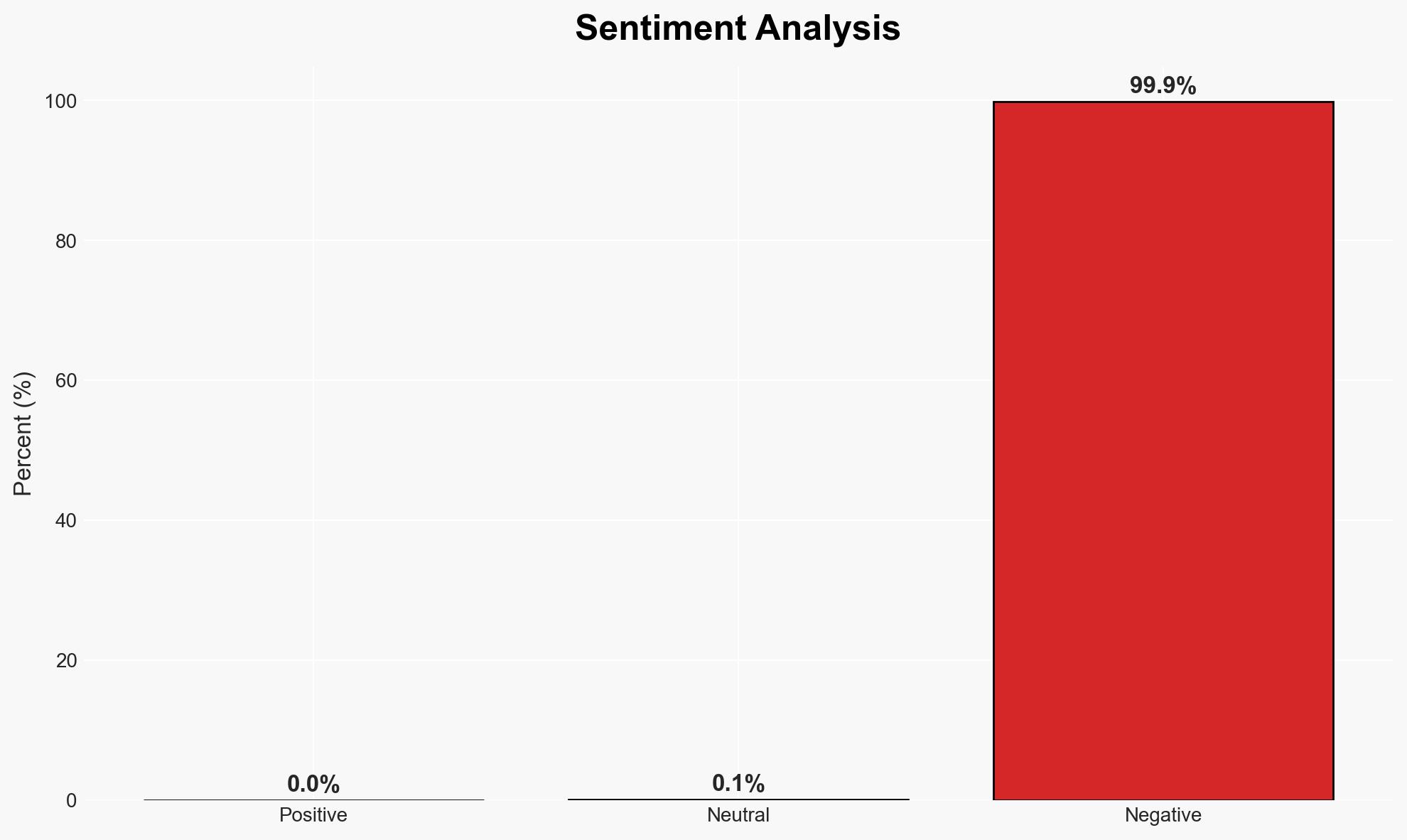
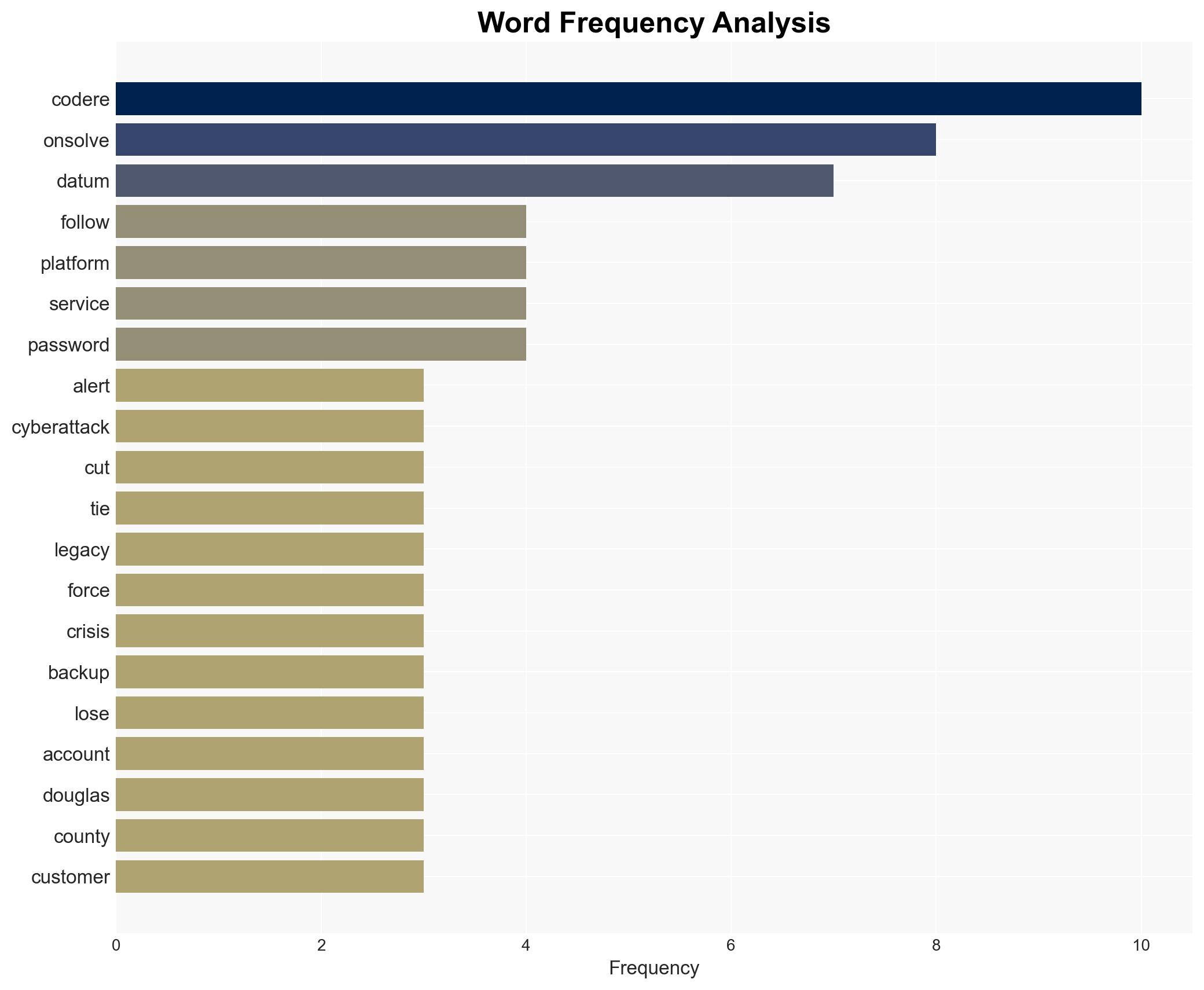
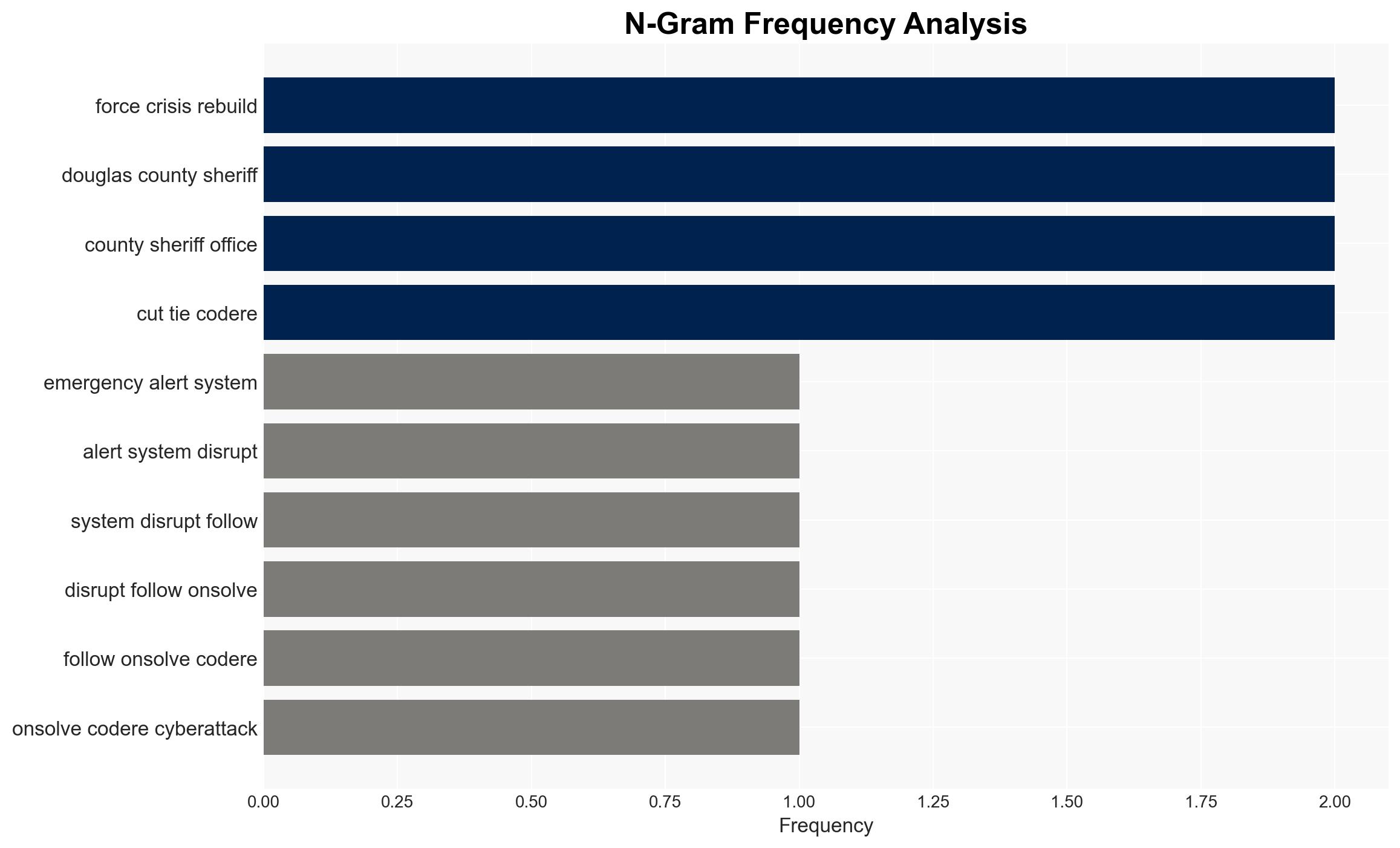
The OnSolve CodeRED cyberattack has disrupted emergency alert systems across the US, impacting state and local governments and emergency services. The attack, attributed to an organized cybercriminal group, has led to data breaches and operational challenges. The most likely hypothesis is that this was a financially motivated ransomware attack, with moderate confidence due to limited direct evidence of the attackers’ identity and intent.
2. Competing Hypotheses
- Hypothesis A: The attack was a financially motivated ransomware operation. Supporting evidence includes the ransom demand and the creation of a data leak site. Contradicting evidence is the lack of confirmed ransom payment or communication from the attackers.
- Hypothesis B: The attack was a state-sponsored operation aimed at disrupting US emergency communications. This is supported by the strategic impact on critical infrastructure but contradicted by the absence of geopolitical indicators or state-level attribution.
- Assessment: Hypothesis A is currently better supported due to the presence of typical ransomware indicators. However, further evidence such as communication from the attackers or geopolitical developments could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers are primarily financially motivated; the data breach was a direct result of the cyberattack; OnSolve’s response will mitigate further data loss.
- Information Gaps: The identity and motives of the attackers; the full extent of the data compromised; the effectiveness of OnSolve’s mitigation efforts.
- Bias & Deception Risks: Potential bias in attributing the attack to cybercriminals without state actor consideration; possible deception in the attackers’ communication or lack thereof.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on emergency communication systems and influence future cybersecurity policies. It may also encourage similar attacks if perceived as successful.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is suspected or confirmed.
- Security / Counter-Terrorism: Heightened alertness and resource allocation to protect critical infrastructure from cyber threats.
- Cyber / Information Space: Increased focus on securing cloud-based platforms and legacy systems against cyber threats.
- Economic / Social: Potential economic impact on affected businesses and loss of public trust in emergency systems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive forensic investigation; enhance monitoring of emergency communication systems; engage with cybersecurity experts to assess vulnerabilities.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in upgrading legacy systems; implement regular security audits and training.
- Scenario Outlook:
- Best: Successful mitigation and no further breaches, leading to improved security protocols.
- Worst: Additional attacks exploiting similar vulnerabilities, causing widespread disruption.
- Most-Likely: Gradual improvement in security posture with occasional minor breaches.
6. Key Individuals and Entities
- OnSolve
- Douglas County Sheriff’s Office
- Douglas County Board
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, This brief is tagged under: cybersecurity; national security threats; critical infrastructure protection; ransomware; emergency management systems
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us