Ransomware Attacks Target Acquired SMBs to Exploit Network Vulnerabilities During Mergers and Acquisitions
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware hackers attack SMBs being acquired to try and gain access to multiple companies
1. BLUF (Bottom Line Up Front)
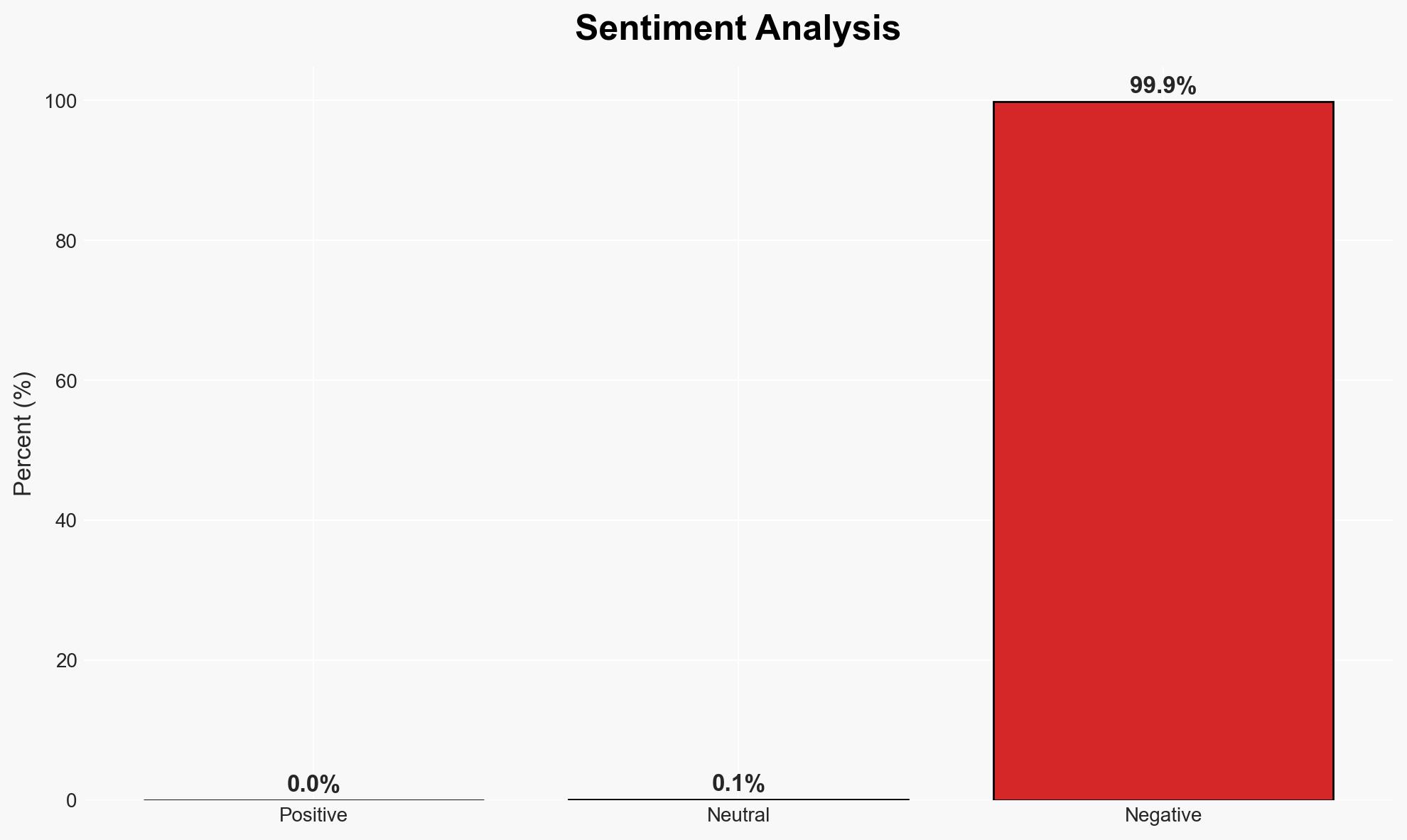
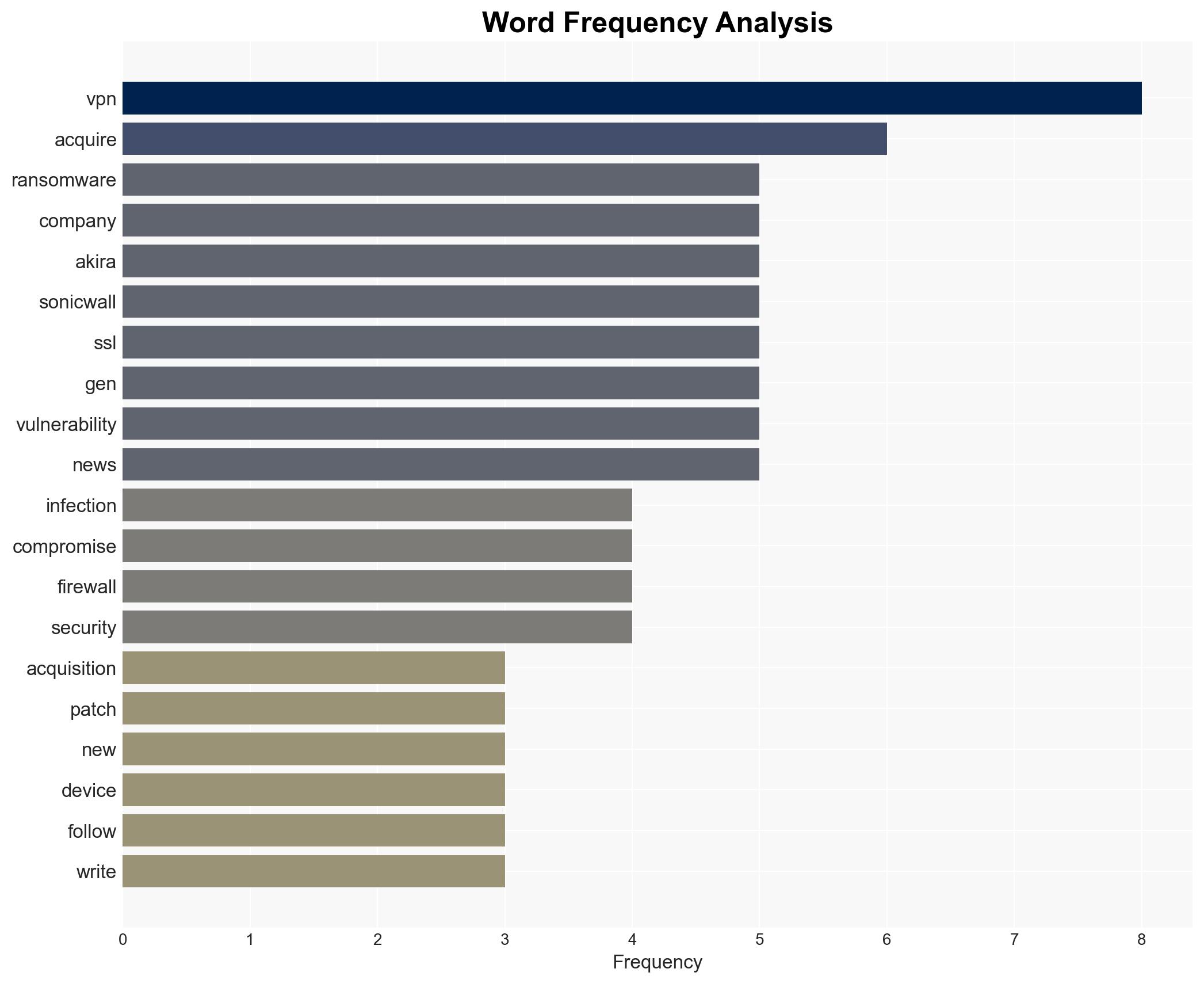
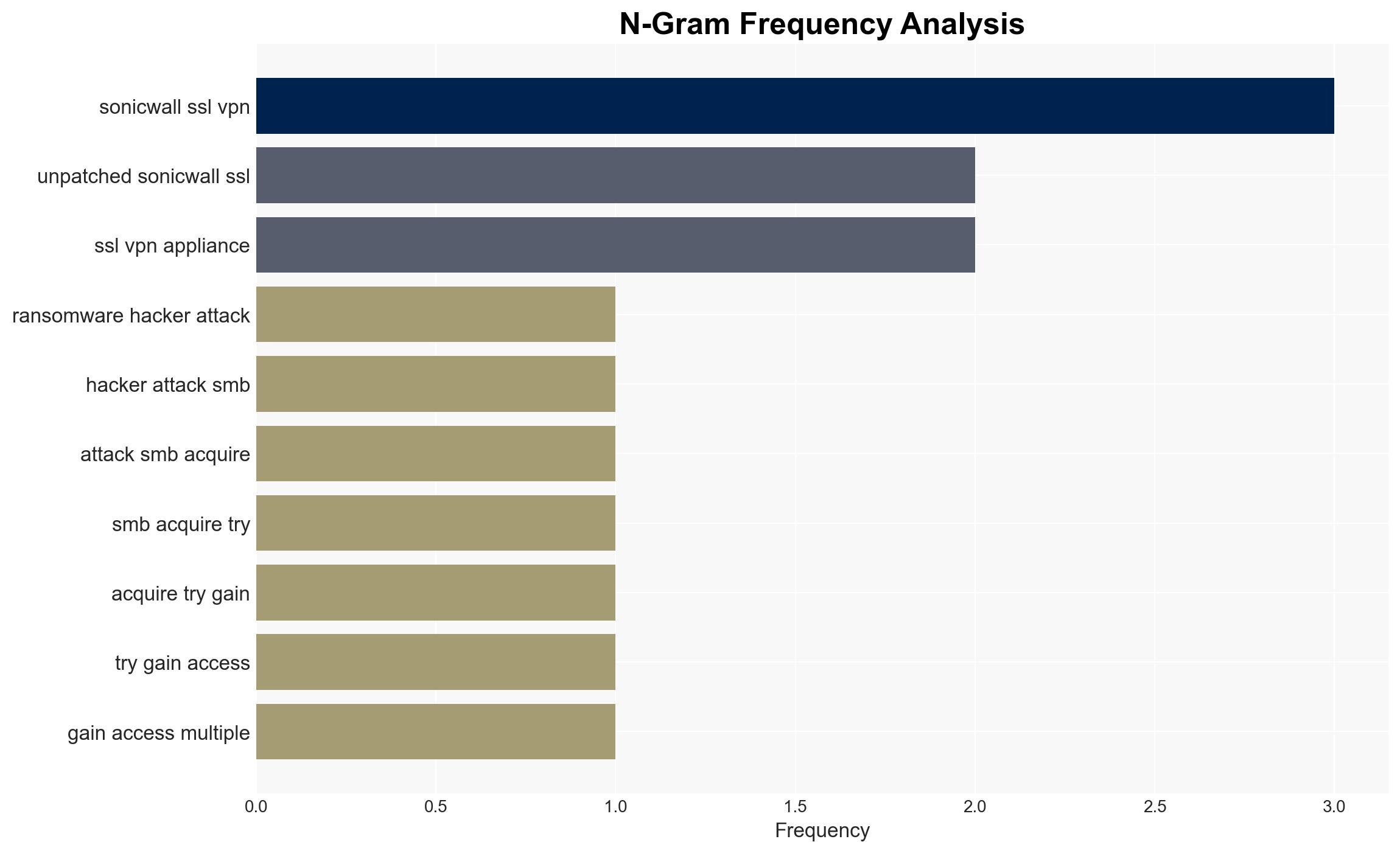
Ransomware groups are targeting small and medium-sized businesses (SMBs) undergoing mergers and acquisitions to exploit unpatched vulnerabilities, particularly in SonicWall SSL VPN appliances. This tactic aims to gain access to broader networks through acquired entities. The most likely hypothesis is that these attacks are opportunistic, leveraging existing vulnerabilities in newly acquired assets. This assessment is made with moderate confidence due to the limited scope of available data.
2. Competing Hypotheses
- Hypothesis A: Ransomware groups are deliberately targeting SMBs involved in mergers and acquisitions to exploit unpatched vulnerabilities in inherited systems. This is supported by the pattern of infections following acquisitions and the use of known vulnerabilities. However, it is uncertain whether these attacks are coordinated or opportunistic.
- Hypothesis B: The ransomware infections are coincidental, with no specific targeting of SMBs involved in mergers and acquisitions. Instead, they are part of broader campaigns exploiting known vulnerabilities. This is contradicted by the timing and focus on acquired assets.
- Assessment: Hypothesis A is currently better supported due to the correlation between acquisitions and subsequent infections, suggesting a strategic exploitation of vulnerabilities in newly acquired systems. Indicators such as increased targeting of acquisition-related entities or new vulnerabilities could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions:
- Ransomware groups have the capability to identify and exploit vulnerabilities in newly acquired assets.
- SMBs are not consistently applying patches or updates to inherited systems.
- Acquiring companies lack comprehensive visibility into the cybersecurity posture of acquired entities.
- Information Gaps: Detailed data on the specific timing and methods of ransomware deployment post-acquisition, and the extent of coordination among threat actors.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests in promoting their services; lack of independent verification of attack details.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of cybersecurity practices in mergers and acquisitions, with potential regulatory implications. Over time, it may drive changes in due diligence processes and cybersecurity standards.
- Political / Geopolitical: Potential for increased regulatory focus on cybersecurity in mergers and acquisitions, influencing international business practices.
- Security / Counter-Terrorism: Heightened threat environment for SMBs, particularly those involved in mergers and acquisitions, necessitating enhanced security measures.
- Cyber / Information Space: Increased exploitation of known vulnerabilities in the cyber domain, highlighting the need for robust patch management and vulnerability assessments.
- Economic / Social: Potential financial losses and reputational damage for affected companies, impacting market stability and investor confidence.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage companies involved in mergers and acquisitions to conduct thorough cybersecurity audits and apply all relevant patches, particularly for known vulnerabilities in SonicWall appliances.
- Medium-Term Posture (1–12 months): Develop industry-wide guidelines for cybersecurity due diligence in mergers and acquisitions, and foster partnerships between cybersecurity firms and SMBs for proactive threat monitoring.
- Scenario Outlook:
- Best Case: Enhanced cybersecurity measures reduce the incidence of ransomware attacks in acquisition scenarios.
- Worst Case: Continued exploitation of vulnerabilities leads to significant financial and reputational damage for multiple companies.
- Most-Likely: Incremental improvements in cybersecurity practices reduce, but do not eliminate, the risk of exploitation during mergers and acquisitions.
6. Key Individuals and Entities
- ReliaQuest (Cybersecurity Researcher)
- SonicWall (Technology Vendor)
- Akira Ransomware Group (Threat Actor)
- SMBs involved in mergers and acquisitions (Potential Victims)
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us