RomCom Threat Actor Utilizes SocGholish for Payload Distribution in Targeted Attacks Linked to Ukraine
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: For the first time a RomCom payload has been observed being distributed via SocGholish
1. BLUF (Bottom Line Up Front)
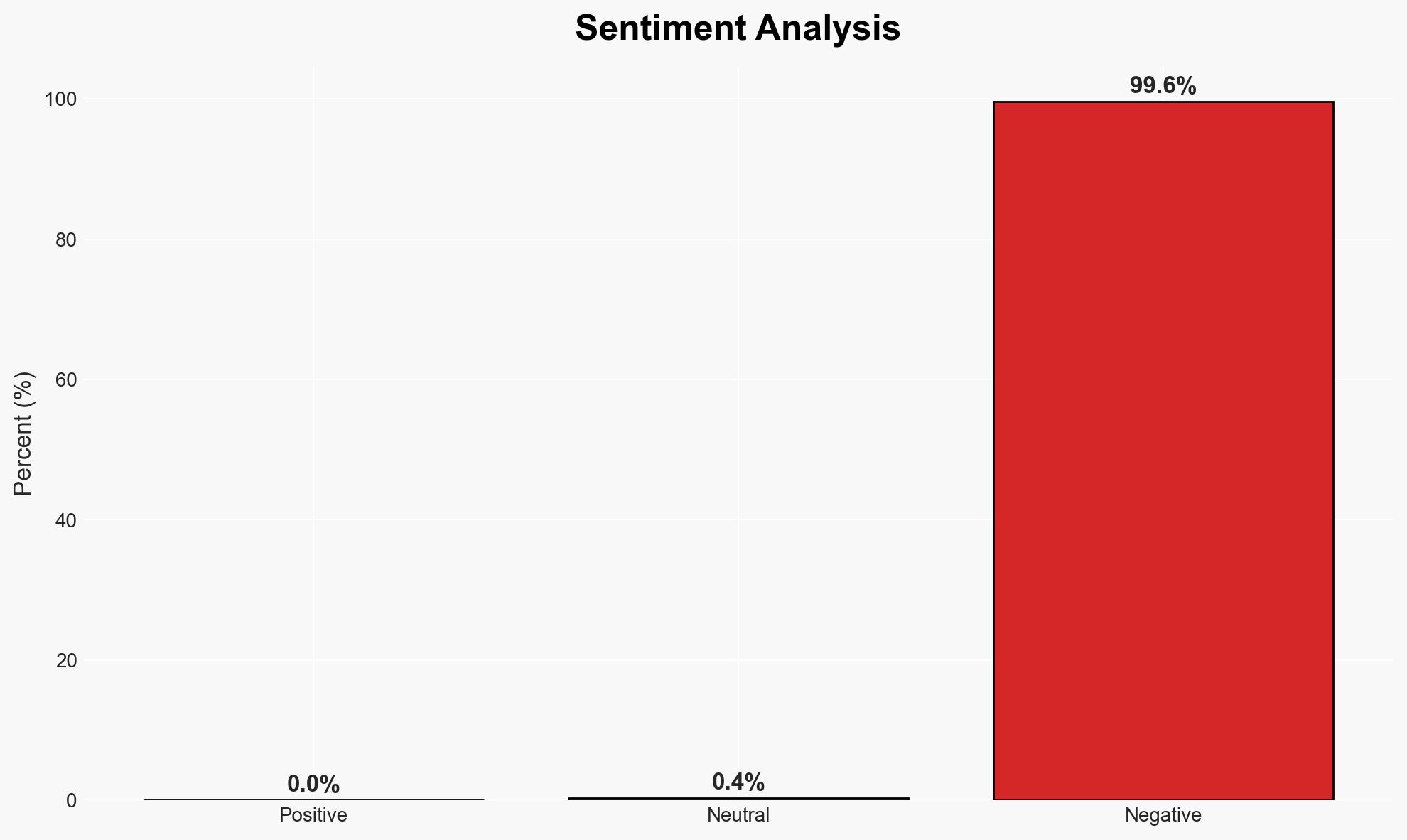
The RomCom threat actor has been observed using the SocGholish malware delivery framework to distribute its payload, marking a significant evolution in their tactics. This development is likely linked to Russian GRU interests, targeting entities supportive of Ukraine. The assessment is made with moderate confidence due to the alignment of observed activities with known Russian cyber operations. Affected parties primarily include organizations with ties to Ukraine, including some based in the U.S.
2. Competing Hypotheses
- Hypothesis A: The RomCom payload distribution via SocGholish is a deliberate strategy by Russian GRU-affiliated actors to expand their cyber operations against pro-Ukrainian entities. This is supported by the alignment of the attack with Russian interests and previous GRU-linked cyber activities. However, the exact command structure and strategic intent remain unclear.
- Hypothesis B: The use of SocGholish by RomCom is opportunistic rather than strategic, exploiting vulnerabilities in widely used frameworks to maximize impact. This hypothesis is less supported due to the specific targeting of Ukrainian-linked entities, suggesting a more directed effort.
- Assessment: Hypothesis A is currently better supported due to the consistent targeting of Ukrainian-linked organizations and the historical context of Russian cyber operations. Indicators that could shift this judgment include evidence of broader, non-targeted campaigns or the emergence of new threat actors using similar tactics.
3. Key Assumptions and Red Flags
- Assumptions: The GRU is actively directing RomCom operations; SocGholish is primarily used for targeted attacks; Ukrainian-linked entities are the main targets.
- Information Gaps: Details on the command structure of RomCom; full scope of entities targeted; technical specifics of the payload’s capabilities.
- Bias & Deception Risks: Potential confirmation bias towards attributing cyber activities to Russian actors; reliance on potentially biased sources such as Arctic Wolf Labs.
4. Implications and Strategic Risks
This development could signal an escalation in cyber operations linked to the Russia-Ukraine conflict, potentially leading to increased cyber threats against Western entities. The use of SocGholish may also indicate a trend towards more sophisticated and deceptive cyber tactics.
- Political / Geopolitical: Potential for increased tensions between Russia and Western nations, particularly those supporting Ukraine.
- Security / Counter-Terrorism: Heightened threat environment for organizations linked to Ukraine, requiring enhanced cybersecurity measures.
- Cyber / Information Space: Possible increase in cyber espionage and data exfiltration activities, leveraging compromised networks.
- Economic / Social: Potential disruptions to businesses and critical infrastructure, leading to economic instability in affected regions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of cyber threats linked to SocGholish; enhance security training to recognize phishing tactics; collaborate with cybersecurity firms for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures against evolving cyber threats; strengthen international partnerships for coordinated cyber defense; invest in advanced threat detection technologies.
- Scenario Outlook:
- Best: Successful mitigation of threats with minimal impact, leading to improved cybersecurity posture.
- Worst: Escalation of cyber attacks causing significant disruption to critical infrastructure and economic activities.
- Most-Likely: Continued targeted cyber operations with moderate impact, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
- RomCom threat actor
- SocGholish malware delivery framework
- Arctic Wolf Labs
- Russian GRU
- Entities supportive of Ukraine
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us