Major code formatting platforms risk user data exposure, raising cybersecurity concerns among experts.
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Watch out coders – top code formatting sites are apparently exposing huge amounts of user data
1. BLUF (Bottom Line Up Front)
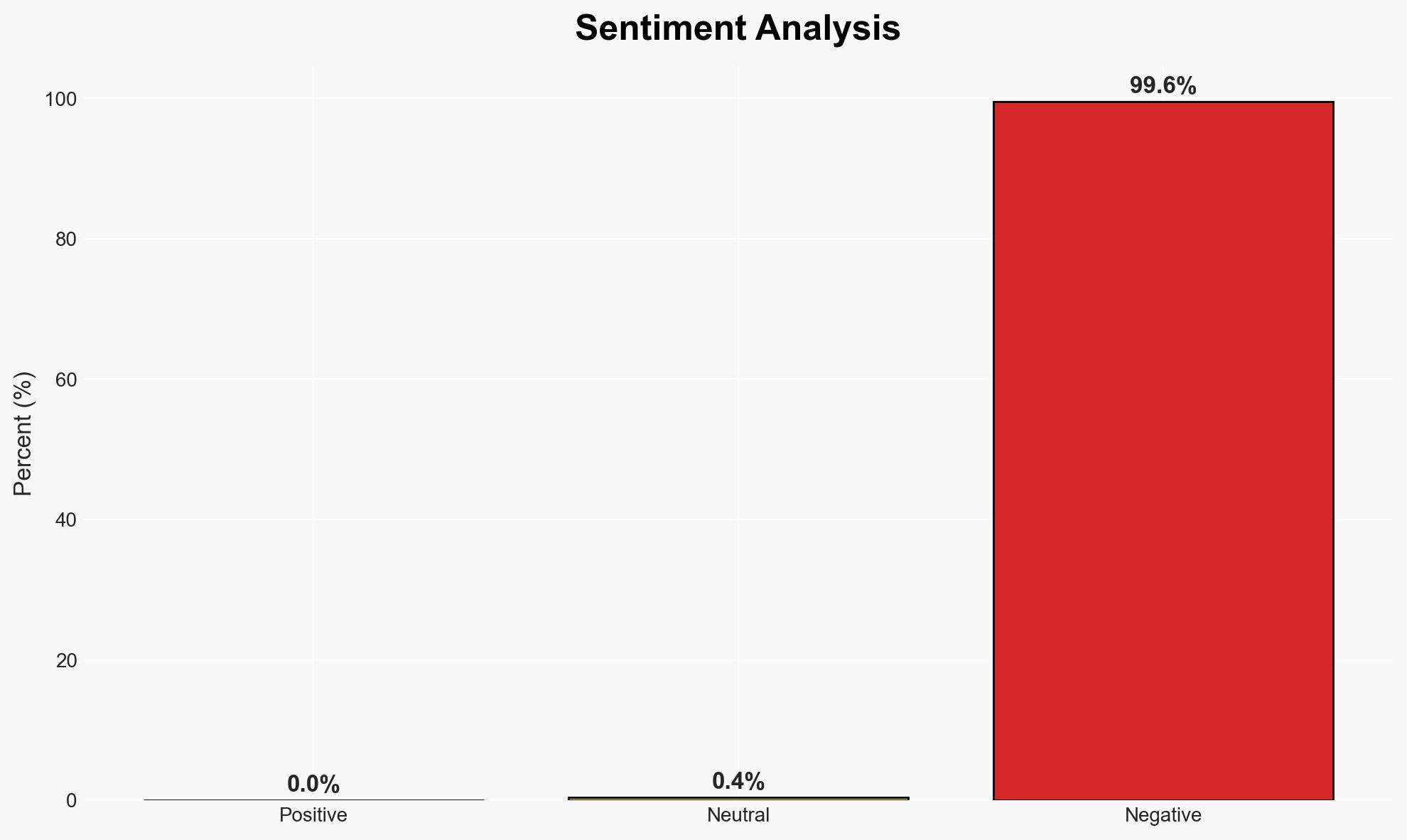
Code formatting sites such as jsonformatter and codebeautify are reportedly exposing sensitive user data, including credentials and private keys, due to inadequate security measures. This poses significant risks to organizations across various critical sectors. The most likely hypothesis is that these vulnerabilities are due to systemic security oversights rather than deliberate malfeasance. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The exposure of sensitive data on code formatting sites is primarily due to inadequate security protocols and oversight. Supporting evidence includes the predictable URL formats and lack of protective features. However, the extent of oversight failure is uncertain.
- Hypothesis B: The data exposure is a result of deliberate exploitation by malicious actors leveraging inherent vulnerabilities in these platforms. While the presence of sensitive data suggests potential exploitation, there is insufficient direct evidence of targeted attacks.
- Assessment: Hypothesis A is currently better supported due to the structural weaknesses identified in the platforms’ security measures. Indicators such as increased targeted attacks or insider threats could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: Users are unaware of the security risks when uploading data; the platforms lack robust security measures; data exposure is unintentional.
- Information Gaps: Specific details on the platforms’ security protocols and any recent security audits are missing.
- Bias & Deception Risks: Potential bias in reporting due to reliance on a single research source; risk of underestimating malicious actor involvement.
4. Implications and Strategic Risks
The exposure of sensitive data on these platforms could lead to increased cyber threats and exploitation by malicious actors, affecting national security and critical infrastructure.
- Political / Geopolitical: Potential diplomatic tensions if government data is compromised.
- Security / Counter-Terrorism: Increased risk of cyber intrusions and data breaches targeting critical infrastructure.
- Cyber / Information Space: Heightened vulnerability to cyber espionage and information theft.
- Economic / Social: Potential financial losses and erosion of trust in digital platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct security audits of code formatting sites and advise organizations to review data sharing practices.
- Medium-Term Posture (1–12 months): Develop partnerships for enhanced cybersecurity measures and user education campaigns.
- Scenario Outlook:
- Best Case: Platforms enhance security, reducing data exposure risks.
- Worst Case: Continued data breaches lead to significant national security incidents.
- Most-Likely: Incremental improvements in security with ongoing minor breaches.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us