Novel Authentication Method Utilizing Omega DNA Cryptography for Resource-Constrained Devices
Published on: 2025-11-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
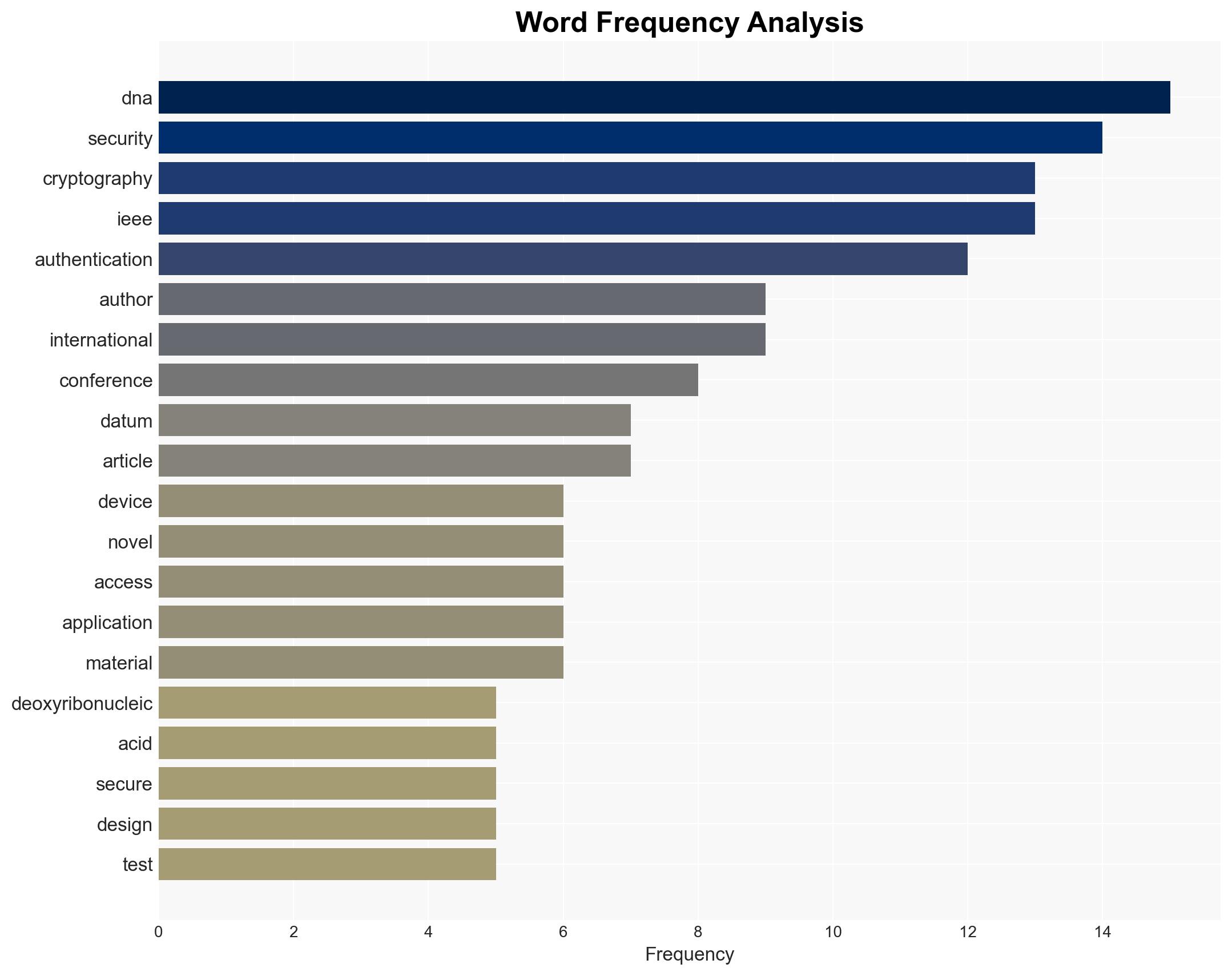
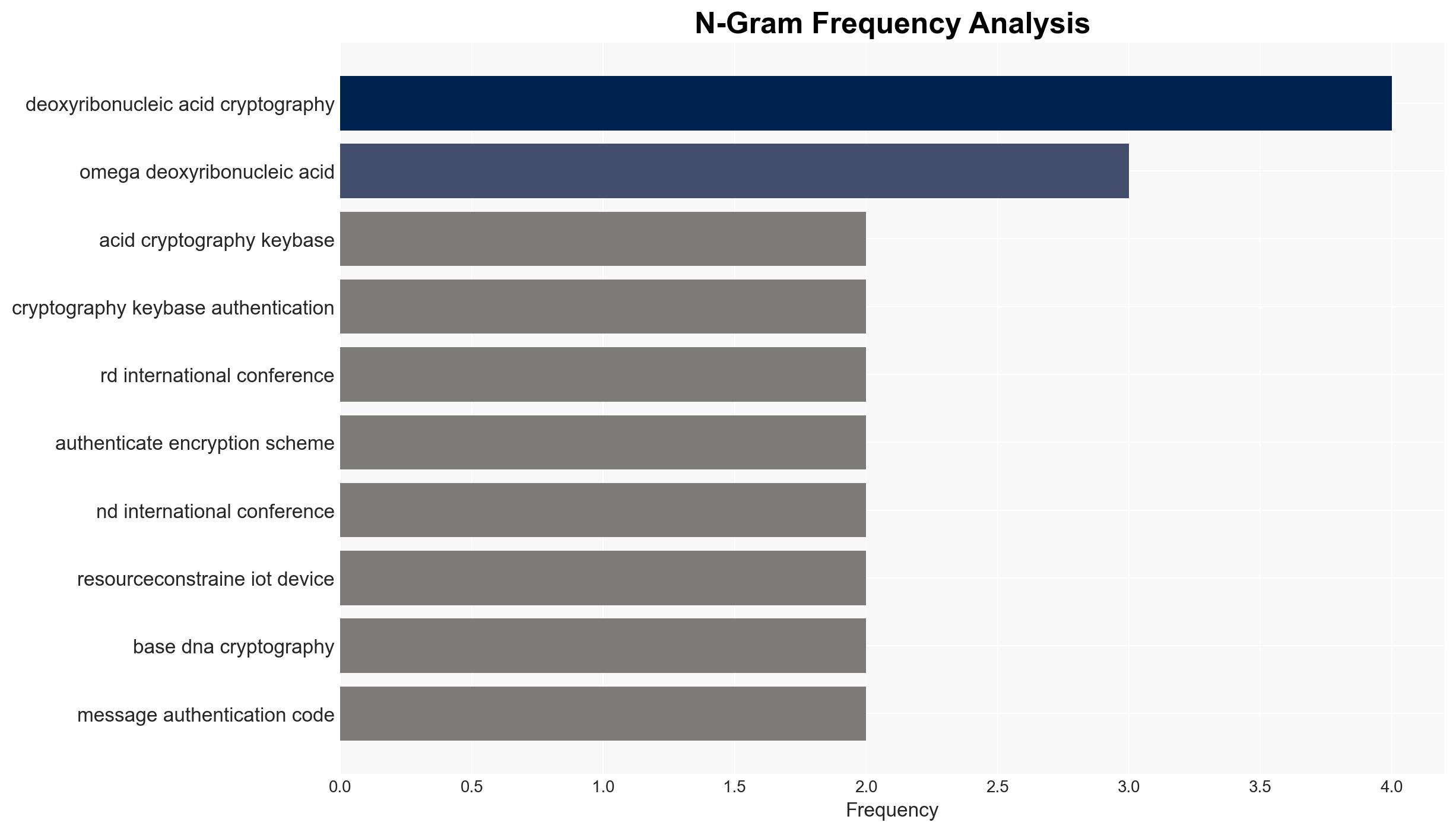
Intelligence Report: Omega deoxyribonucleic acid cryptography key-based authentication
1. BLUF (Bottom Line Up Front)
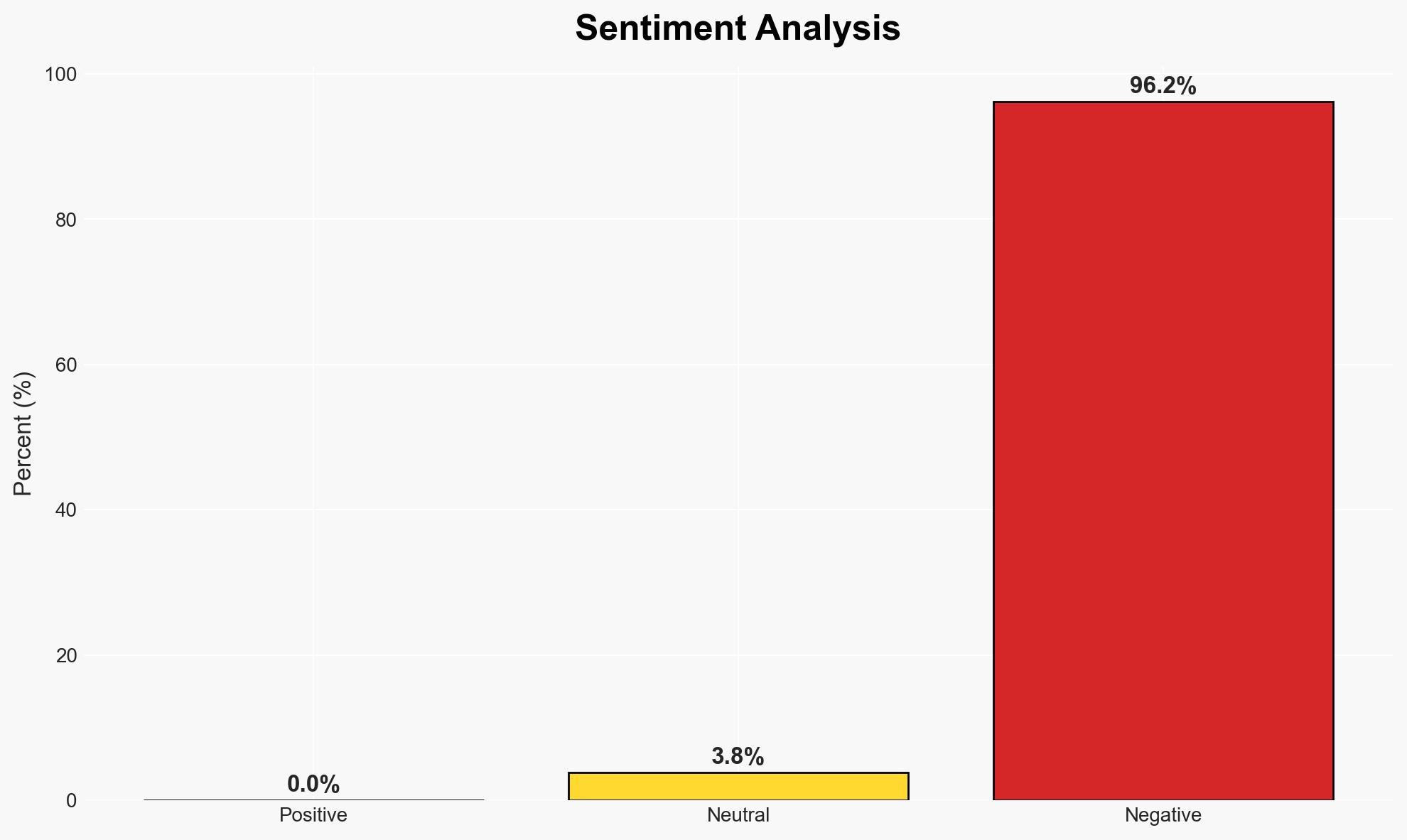
The proposed Omega deoxyribonucleic acid (DNA) cryptography key-based authentication method offers a potentially robust solution for securing resource-constrained devices. This development could enhance cybersecurity by providing a low-complexity, high-security authentication mechanism. However, the lack of comprehensive real-world testing introduces uncertainty. Overall, moderate confidence is placed in the potential efficacy of this method, pending further validation.
2. Competing Hypotheses
- Hypothesis A: The Omega DNA cryptography key-based authentication method is a viable and effective solution for securing resource-constrained devices. Supporting evidence includes its low computational complexity and successful collision resistance tests. Key uncertainties involve its performance in diverse real-world environments.
- Hypothesis B: The Omega DNA cryptography method may not significantly improve security for resource-constrained devices due to potential implementation challenges and untested scalability. Contradicting evidence includes the lack of large-scale deployment data and potential vulnerabilities not yet identified.
- Assessment: Hypothesis A is currently better supported due to the method’s alignment with contemporary cryptographic standards and initial positive test results. However, indicators such as successful real-world deployment and peer-reviewed validation could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The method will perform as effectively in real-world applications as in controlled tests; resource-constrained devices will adopt this technology; the cryptographic community will validate the method’s security claims.
- Information Gaps: Detailed performance data from real-world deployments; comprehensive peer-reviewed security analyses; potential integration challenges with existing systems.
- Bias & Deception Risks: Possible over-reliance on initial test results; source bias from proponents of the technology; lack of independent verification may lead to overestimation of capabilities.
4. Implications and Strategic Risks
This development could significantly impact the cybersecurity landscape, particularly for resource-constrained devices, by providing a new authentication mechanism. However, its success depends on overcoming implementation challenges and gaining widespread adoption.
- Political / Geopolitical: Potential influence on national cybersecurity policies; may affect international standards and cooperation in cryptographic research.
- Security / Counter-Terrorism: Could enhance security of critical infrastructure and IoT devices, reducing vulnerabilities to cyber-attacks.
- Cyber / Information Space: May lead to new cryptographic standards and influence future cybersecurity frameworks.
- Economic / Social: Could drive innovation in technology sectors; potential economic benefits from improved device security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Initiate independent validation studies; monitor developments in DNA cryptography research; engage with stakeholders in cybersecurity and cryptography communities.
- Medium-Term Posture (1–12 months): Develop partnerships with academic and industry leaders to explore practical applications; invest in resilience measures for potential integration challenges.
- Scenario Outlook:
- Best: Widespread adoption and validation lead to enhanced security for resource-constrained devices.
- Worst: Unforeseen vulnerabilities undermine trust and lead to security breaches.
- Most-Likely: Gradual adoption with iterative improvements as real-world testing and validation continue.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us