Korean police apprehend four for hacking 120,000 IP cameras and selling private footage online
Published on: 2025-12-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Korea arrests suspects selling intimate videos from hacked IP cameras
1. BLUF (Bottom Line Up Front)
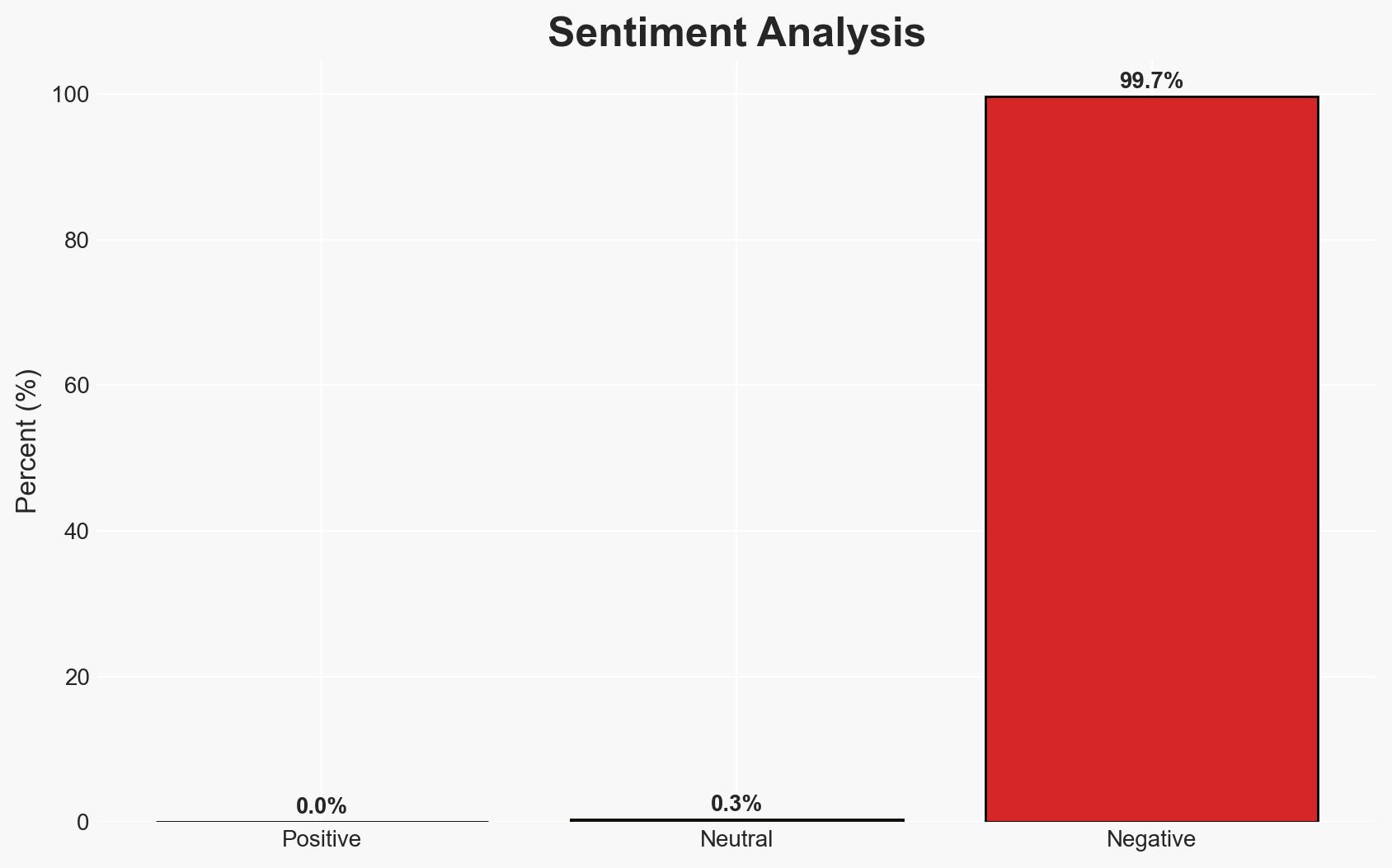
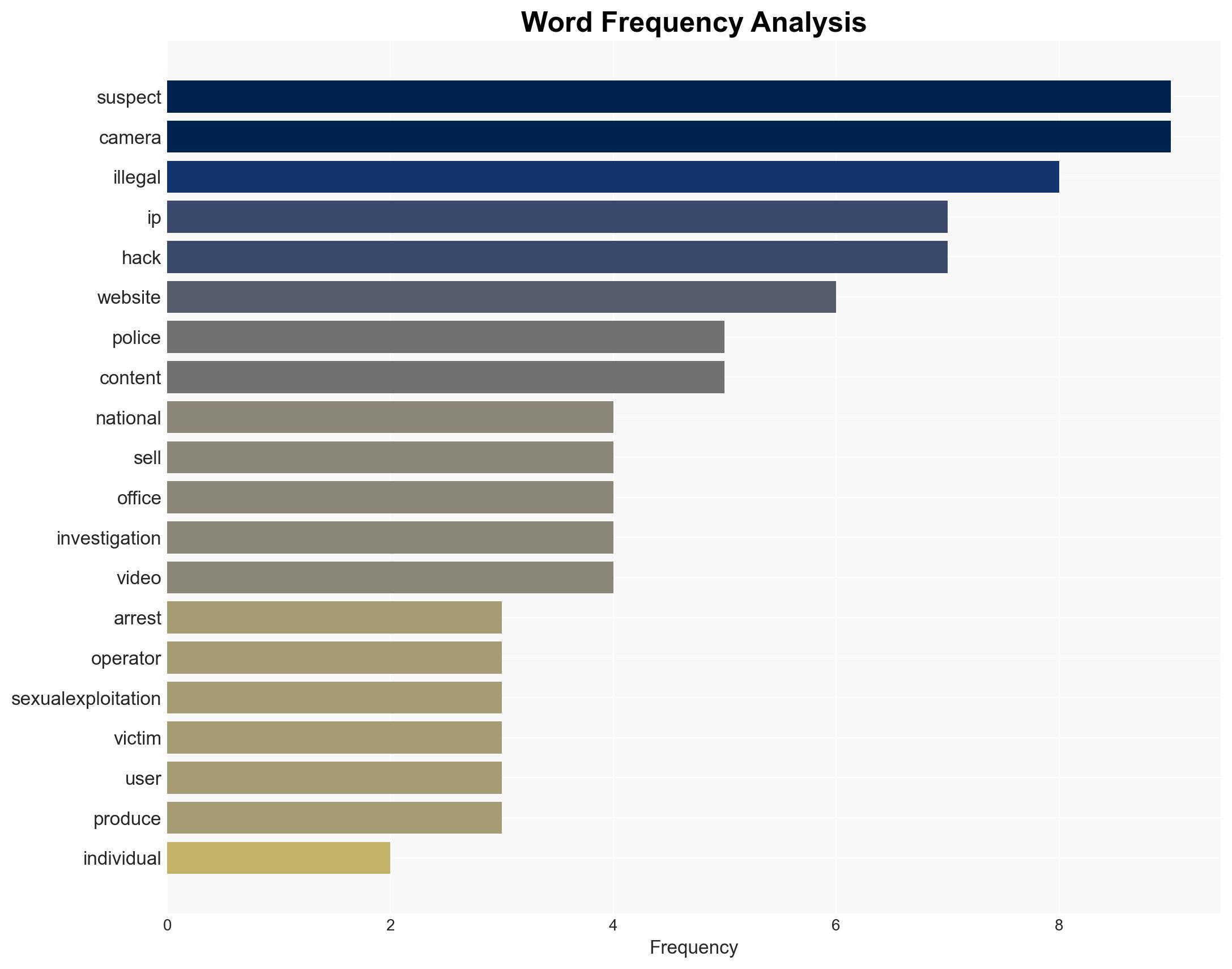
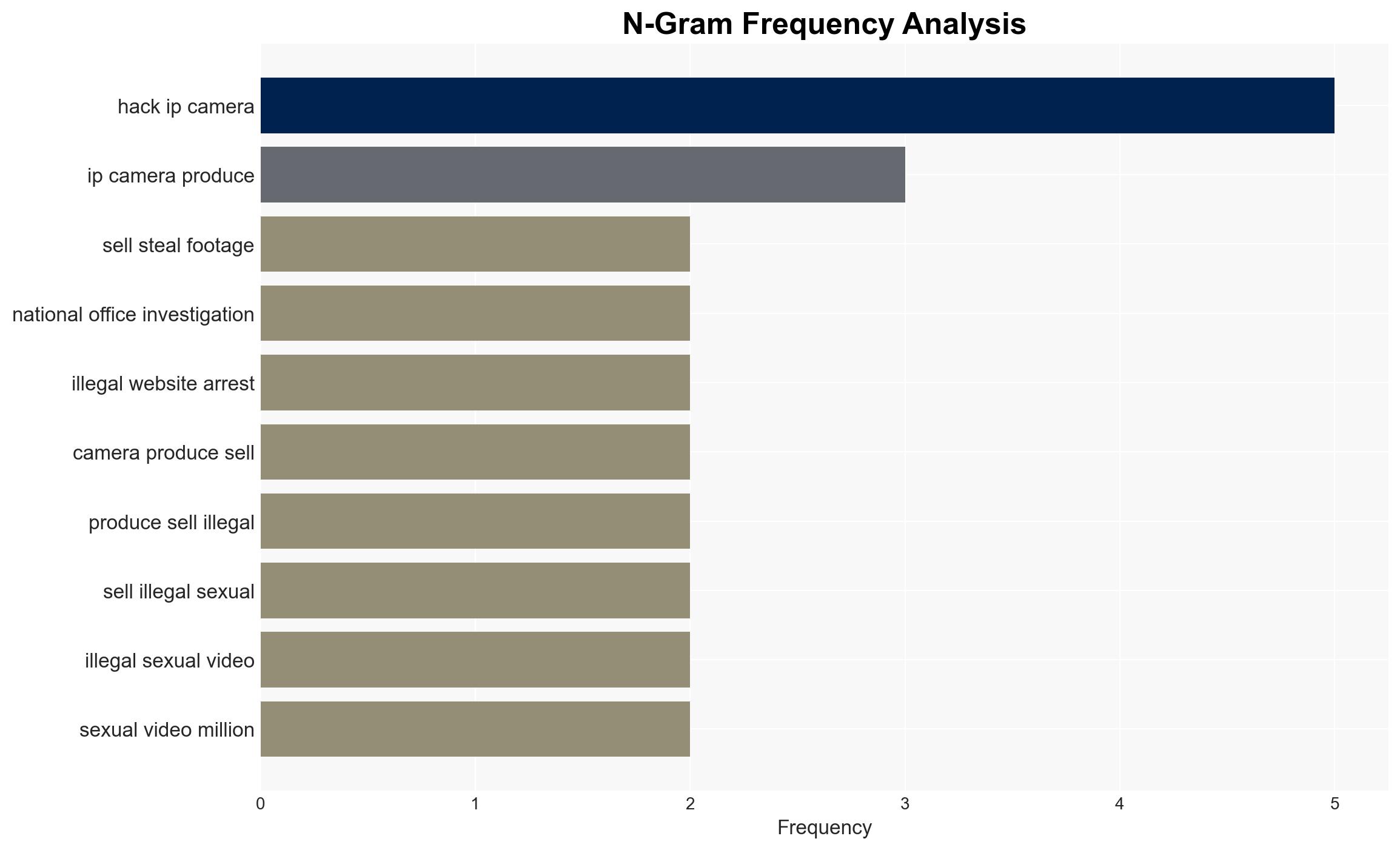
The Korean National Police have arrested four individuals for hacking over 120,000 IP cameras and selling intimate footage to a foreign adult site. This incident highlights significant vulnerabilities in IoT security and the potential for international cybercrime networks to exploit these weaknesses. The ongoing investigation and international collaboration aim to dismantle the network and mitigate further harm to victims. Overall confidence in this assessment is moderate due to incomplete information about the foreign website and its operators.
2. Competing Hypotheses
- Hypothesis A: The suspects acted independently, motivated by financial gain, exploiting weak security in IP cameras. This is supported by the individual actions of the suspects and the financial transactions involved. However, the lack of detailed information on the foreign website’s operations introduces uncertainty.
- Hypothesis B: The suspects are part of a larger, organized cybercrime network that systematically exploits IoT vulnerabilities across multiple countries. This is suggested by the scale of the operation and the international nature of the website. Contradicting evidence includes the lack of explicit links to broader networks in the current data.
- Assessment: Hypothesis B is currently better supported due to the scale and international reach of the operation, which suggests coordination beyond individual efforts. Key indicators that could shift this judgment include evidence of direct connections to known cybercrime networks or further arrests of additional network members.
3. Key Assumptions and Red Flags
- Assumptions: The suspects had the technical capability to hack such a large number of devices; the foreign website is a significant platform for illicit content; international cooperation will be effective in dismantling the network.
- Information Gaps: Details about the foreign website’s infrastructure, the identity of its operators, and the extent of its network are unknown.
- Bias & Deception Risks: Potential bias in reporting due to reliance on official statements; risk of deception by suspects regarding the extent of their network connections.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and regulation of IoT devices, impacting manufacturers and users globally. It may also prompt more robust international cybercrime cooperation and policy development.
- Political / Geopolitical: Potential diplomatic tensions if the foreign website’s host country is uncooperative.
- Security / Counter-Terrorism: Increased focus on cybercrime as a national security threat, potentially diverting resources from other areas.
- Cyber / Information Space: Highlighting vulnerabilities in IoT devices could lead to increased cyber defense measures and public awareness campaigns.
- Economic / Social: Potential economic impact on IoT manufacturers due to increased security requirements; social impact on victims and public trust in digital security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of IoT device security; engage with international partners to trace and dismantle the foreign website.
- Medium-Term Posture (1–12 months): Develop resilience measures for IoT security; establish partnerships for international cybercrime prevention.
- Scenario Outlook: Best: Successful dismantling of the network with minimal further victimization. Worst: Expansion of similar operations due to insufficient international cooperation. Most-Likely: Gradual dismantling with ongoing challenges in international legal frameworks.
6. Key Individuals and Entities
- Suspect B, Suspect C, Suspect D, Suspect E (identities not fully disclosed)
- Park Woo-hyun, Director of Cyber Investigation Policy at the National Police Agency
- Foreign website operators (not clearly identifiable from open sources in this snippet)
7. Thematic Tags
Cybersecurity, cybercrime, IoT security, international cooperation, privacy invasion, digital forensics, cyber policy, victim protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us