Online cult exploited children for abuse and suicide coercion, federal authorities report
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Twisted online cult targeted kids as young as 11 to create child porn then urged them to commit suicide feds
1. BLUF (Bottom Line Up Front)
The arrest of members of “Greggy’s Cult” highlights a severe exploitation of digital platforms to target minors for sexual exploitation and psychological manipulation. The group used gaming and messaging platforms to coerce children into creating child pornography and encouraged suicide. This case underscores vulnerabilities in online environments frequented by minors. Overall confidence in the assessment is moderate, given the limited scope of available data and potential for further undisclosed victims.
2. Competing Hypotheses
- Hypothesis A: The primary motive of “Greggy’s Cult” was sexual exploitation and psychological control over minors. Supporting evidence includes the systematic approach to coercing children into sexual acts and psychological manipulation. However, uncertainties remain about the full extent of their network and potential undisclosed motives.
- Hypothesis B: The cult’s activities were primarily driven by a desire to create chaos and fear, with sexual exploitation as a secondary objective. This is less supported by the evidence, as the primary actions involved sexual coercion and exploitation. The lack of evidence for broader ideological or terroristic objectives weakens this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the structured nature of the exploitation activities and the direct evidence of sexual and psychological manipulation. Indicators that could shift this judgment include discovery of ideological materials or communications suggesting broader objectives.
3. Key Assumptions and Red Flags
- Assumptions: The group operated primarily online; the victims were targeted due to their vulnerability; digital platforms lacked adequate safeguards; the group’s activities were not politically motivated.
- Information Gaps: The full extent of the victim pool, potential international connections, and the depth of platform vulnerabilities remain unclear.
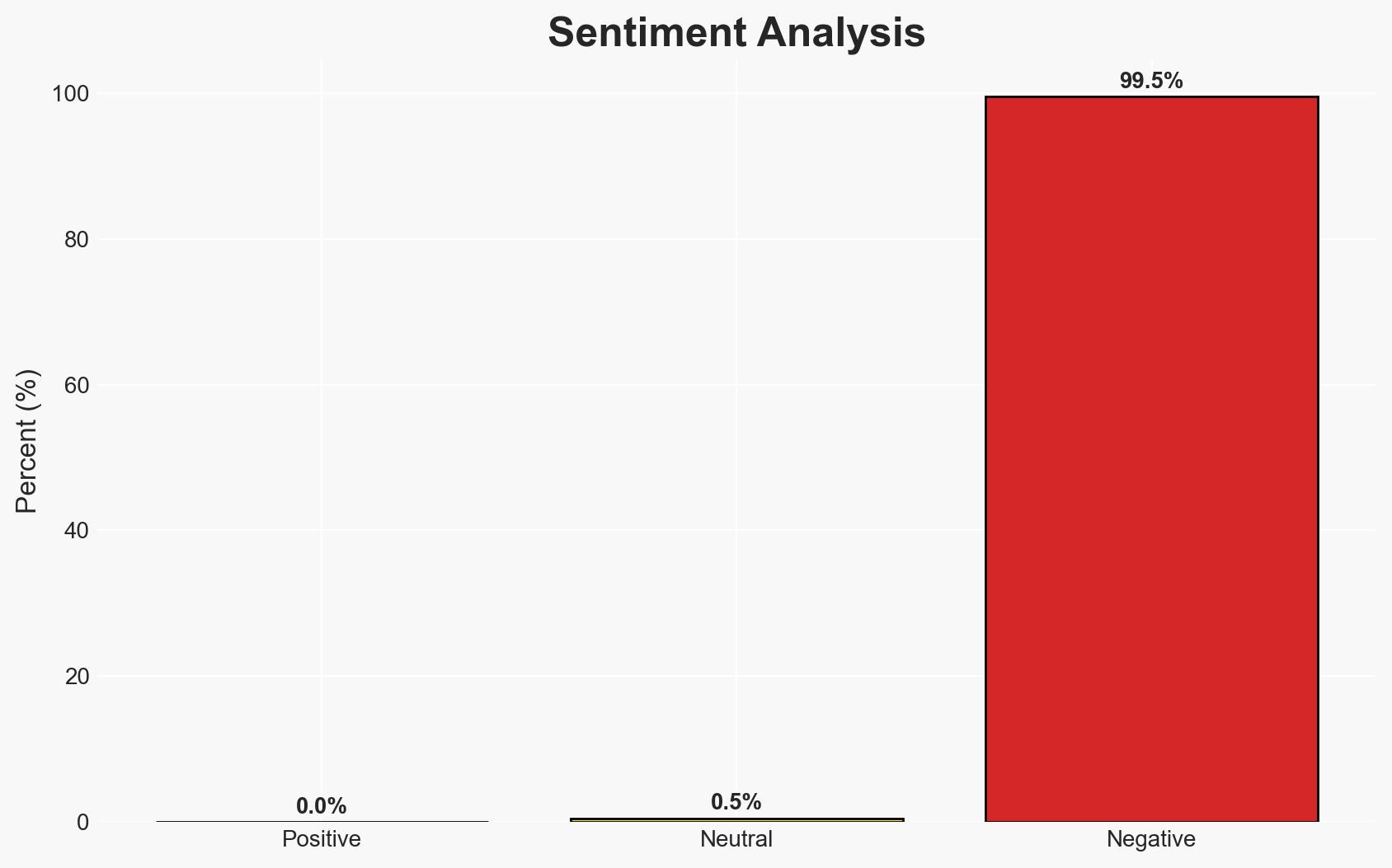
- Bias & Deception Risks: Potential bias in reporting due to the sensational nature of the crimes; risk of deception in online identities and communications used by the group.
4. Implications and Strategic Risks
This development highlights significant risks in the digital environment for minors and potential inadequacies in platform security measures. It may prompt increased scrutiny and regulatory pressure on digital platforms.
- Political / Geopolitical: Potential for increased legislative action on digital platform regulation and child protection laws.
- Security / Counter-Terrorism: Heightened awareness and monitoring of online platforms for similar exploitative activities.
- Cyber / Information Space: Increased focus on cybersecurity measures for platforms frequented by minors; potential for enhanced digital literacy campaigns.
- Economic / Social: Social outcry may lead to reputational damage for implicated platforms; potential for increased funding for child protection initiatives.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of digital platforms for similar activities, engage with platform operators to improve security measures, and initiate outreach to potential victims.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies for improved child safety online, and invest in public awareness campaigns about online risks.
- Scenario Outlook:
- Best: Successful mitigation of similar threats through improved platform security and user awareness.
- Worst: Emergence of additional groups exploiting similar vulnerabilities, leading to widespread exploitation.
- Most-Likely: Incremental improvements in platform security and increased reporting of similar cases.
6. Key Individuals and Entities
- Hector Bermudez, Zachary Dosch, Rumaldo Valdez, David Brilhante, Camden Rodriguez
- US Attorney’s Office for the Eastern District of New York, FBI
- Digital platforms: Discord, Roblox, Counter-Strike: Global Offensive
7. Thematic Tags
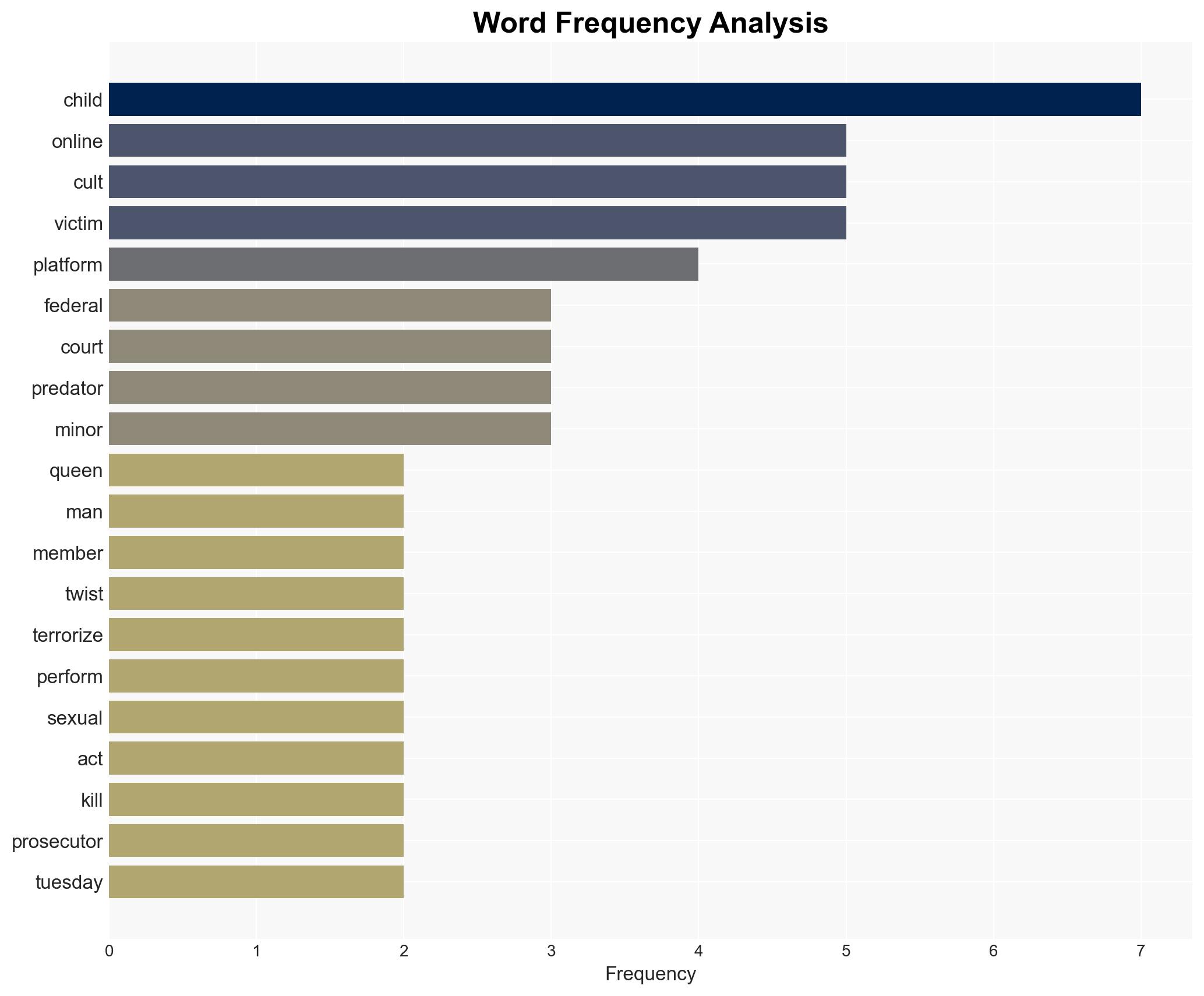
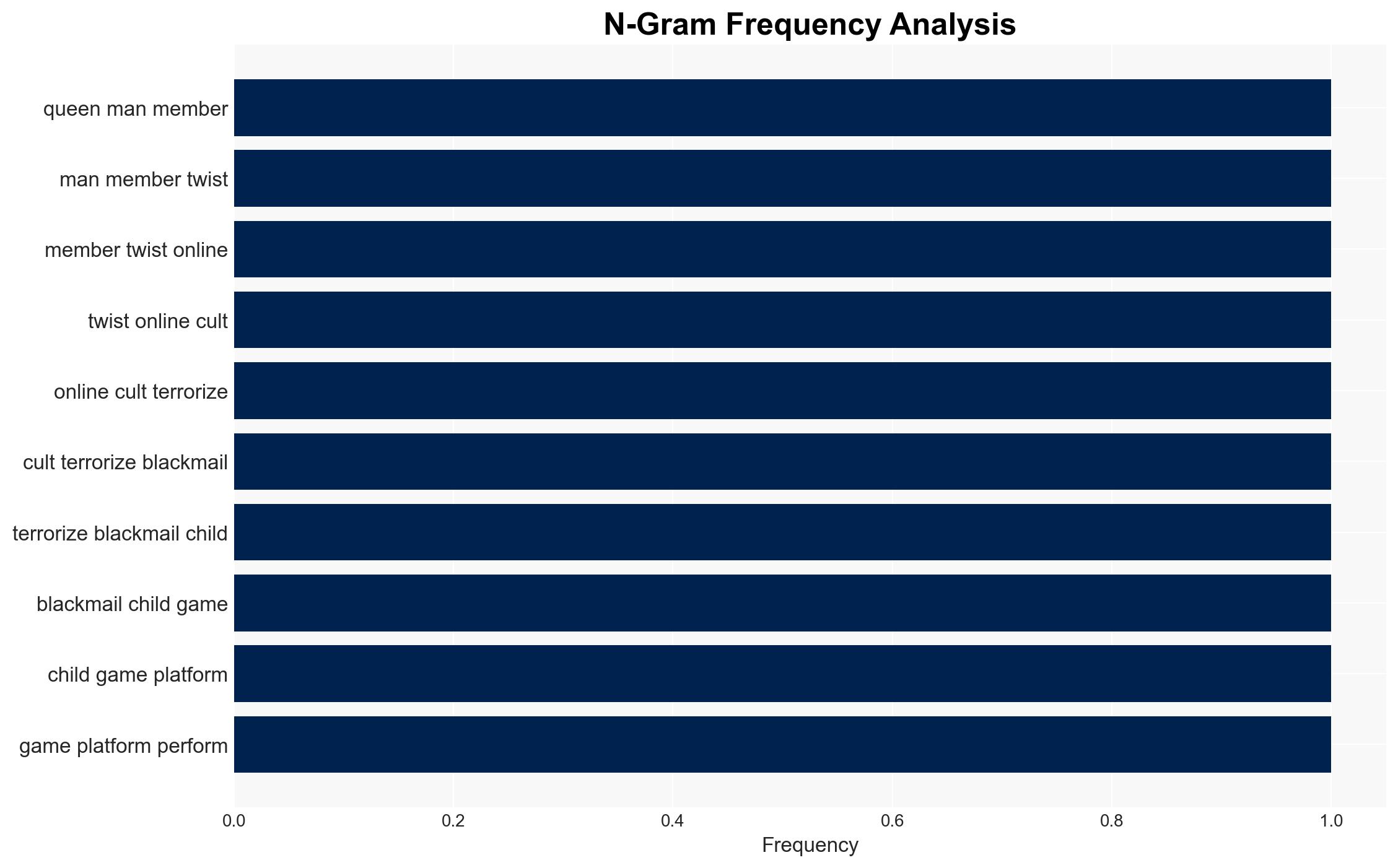
Cybersecurity, child exploitation, online safety, digital platforms, law enforcement, psychological manipulation, federal prosecution
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us