Revamping Threat Intelligence Programs to Enhance Detection and Response Effectiveness
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Threat intelligence programs are broken here is how to fix them
1. BLUF (Bottom Line Up Front)
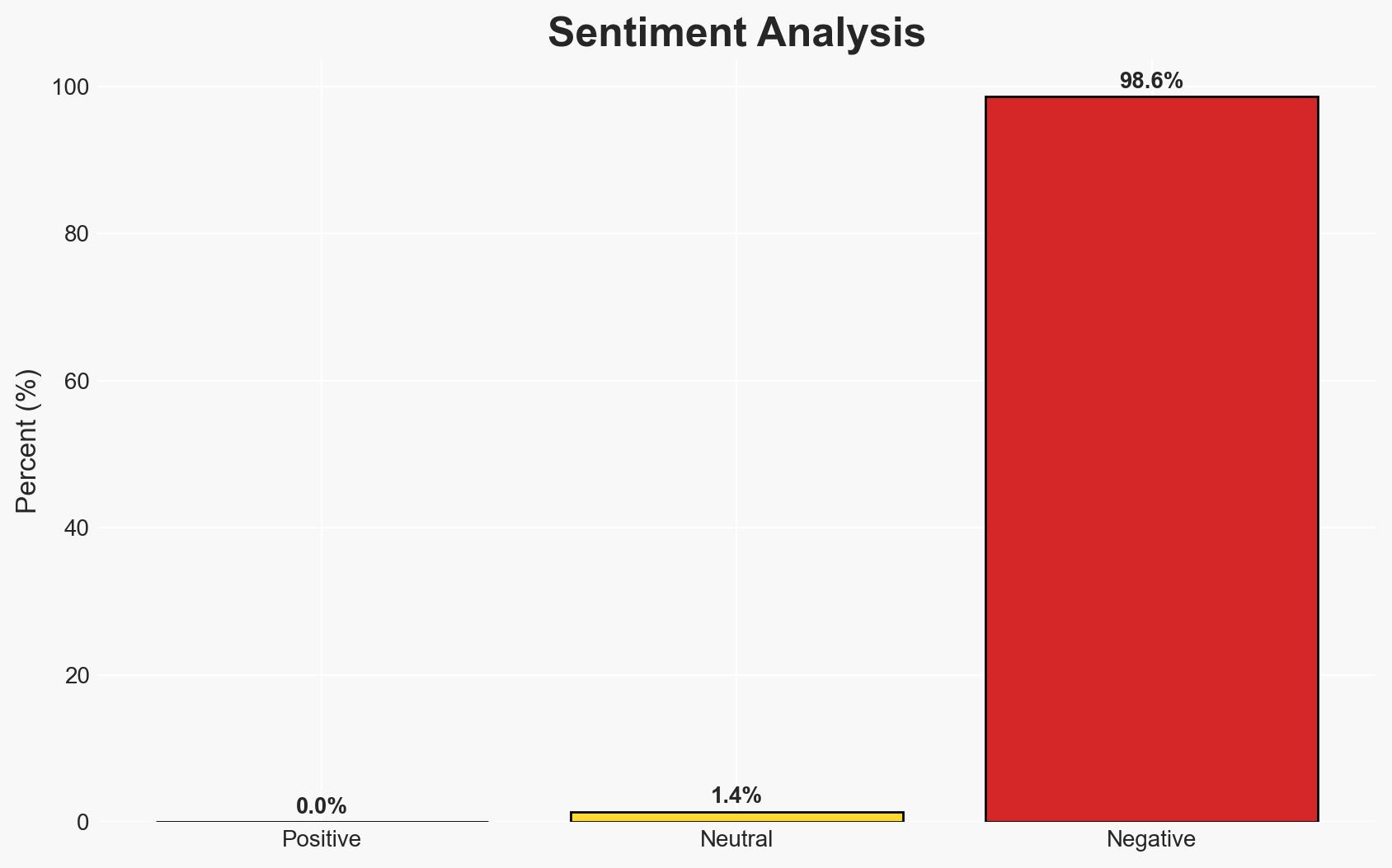
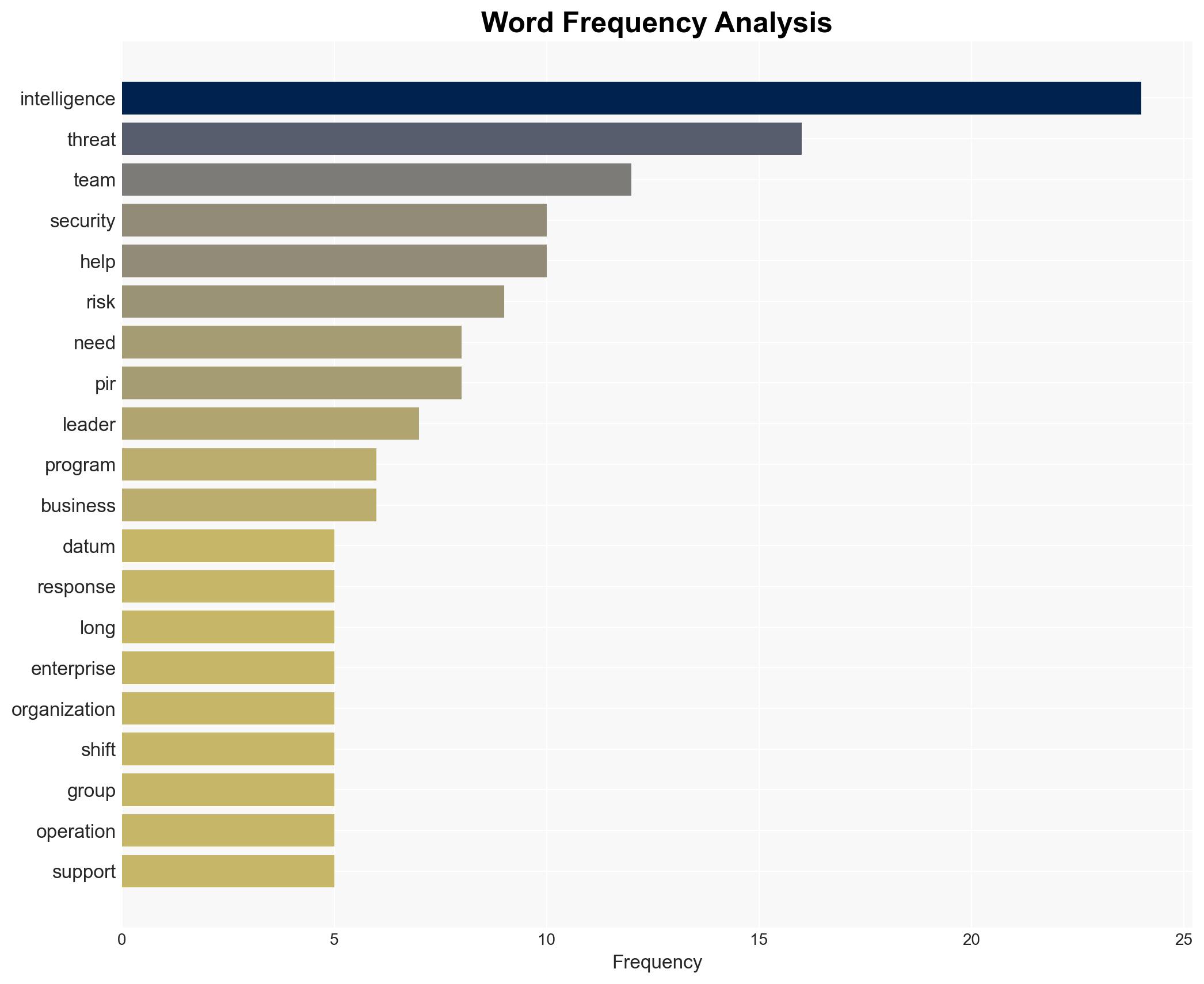
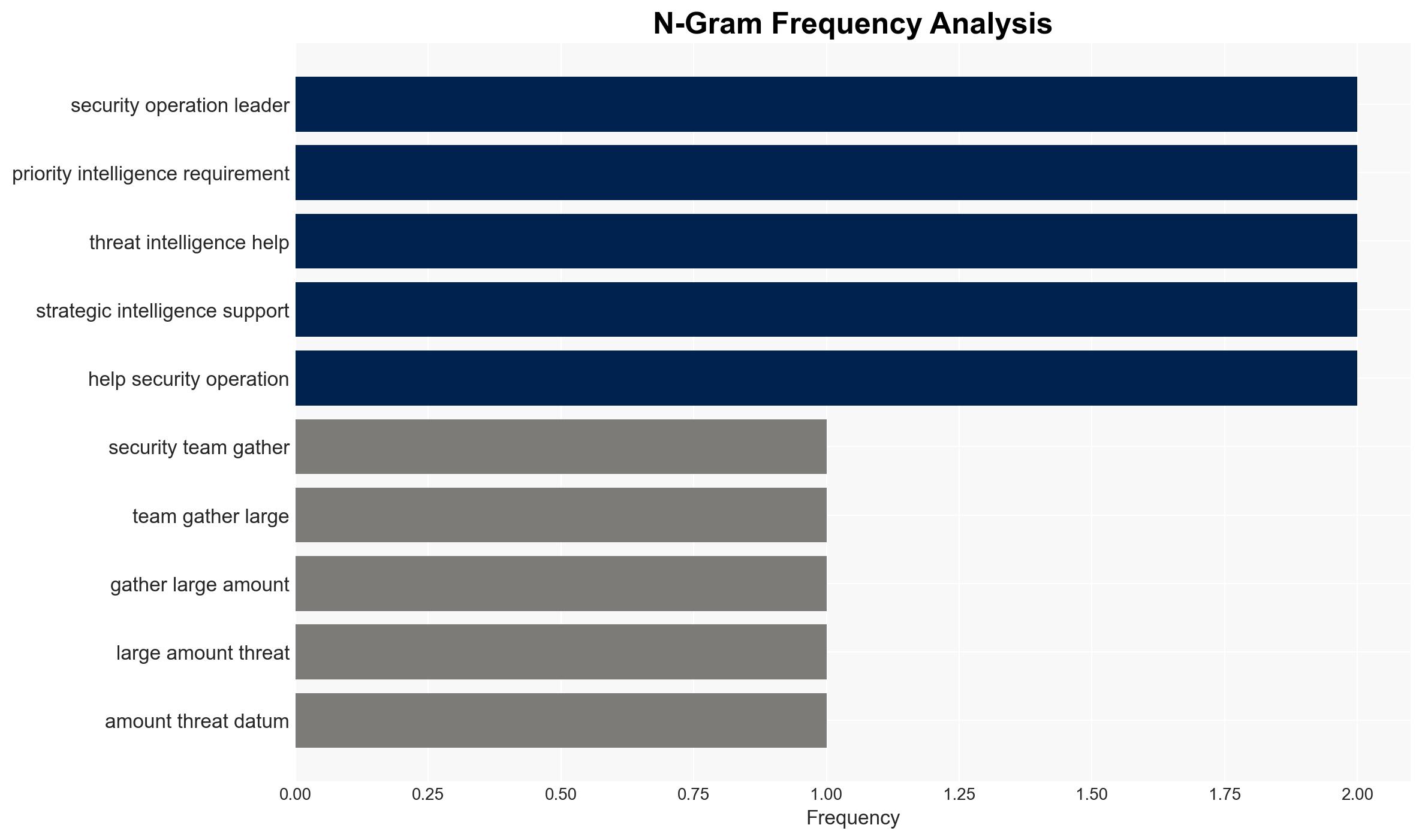
The current threat intelligence programs are ineffective due to their inability to prioritize and act on relevant data, leading to missed threats and inefficient resource allocation. The most likely hypothesis is that the lack of structured priority intelligence requirements (PIRs) is a primary cause of this inefficiency. This affects security teams, organizational leaders, and executives. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The ineffectiveness of threat intelligence programs is primarily due to the lack of structured PIRs, which leads to an inability to prioritize and act on relevant data. This is supported by the reported fact that organizations struggle to determine what matters in the vast amounts of data collected.
- Hypothesis B: The ineffectiveness is primarily due to the complexity and rapid evolution of the threat landscape, which overwhelms existing threat intelligence capabilities. This is supported by the description of criminal operations resembling supply chains and the rise of AI in shaping ransomware activity.
- Assessment: Hypothesis A is currently better supported, as the lack of structured PIRs directly impacts the ability to prioritize and act on intelligence, a fundamental issue highlighted in the report. Indicators that could shift this judgment include evidence of improved outcomes from organizations that have implemented effective PIRs.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have access to sufficient intelligence feeds; PIRs can be effectively implemented and maintained; the threat landscape will continue to evolve rapidly; AI will increasingly influence cyber threats.
- Information Gaps: Specific examples of organizations successfully implementing PIRs; detailed metrics on the effectiveness of current threat intelligence programs.
- Bias & Deception Risks: Potential bias in reporting from organizations with vested interests in promoting certain threat intelligence solutions; deception by threat actors to mislead intelligence efforts.
4. Implications and Strategic Risks
The ongoing inefficiency in threat intelligence programs could lead to increased vulnerability to cyber threats, impacting organizational security and economic stability. Over time, this may necessitate significant restructuring of security operations and increased investment in intelligence capabilities.
- Political / Geopolitical: Escalation in cyber conflicts as state and non-state actors exploit intelligence gaps.
- Security / Counter-Terrorism: Increased risk of successful cyber-attacks due to delayed detection and response.
- Cyber / Information Space: Enhanced complexity in cyber operations and the need for advanced AI-driven threat detection tools.
- Economic / Social: Potential economic losses from successful cyber-attacks and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a review of current PIRs and intelligence processes; prioritize the development of structured PIRs aligned with organizational goals.
- Medium-Term Posture (1–12 months): Invest in training for security teams on threat prioritization; develop partnerships with intelligence providers to enhance data relevance.
- Scenario Outlook:
- Best: Organizations effectively implement PIRs, leading to improved threat detection and response.
- Worst: Continued inefficiencies result in significant cyber breaches and financial losses.
- Most-Likely: Gradual improvement in intelligence effectiveness as organizations refine PIRs and adapt to the evolving threat landscape.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, threat intelligence, ransomware, AI in cyber threats, priority intelligence requirements, organizational security, cyber operations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us