Penn and Phoenix Universities Confirm Data Breaches Following Cyberattack on Oracle E-Business Suite
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: University of Pennsylvania and University of Phoenix disclose data breaches
1. BLUF (Bottom Line Up Front)
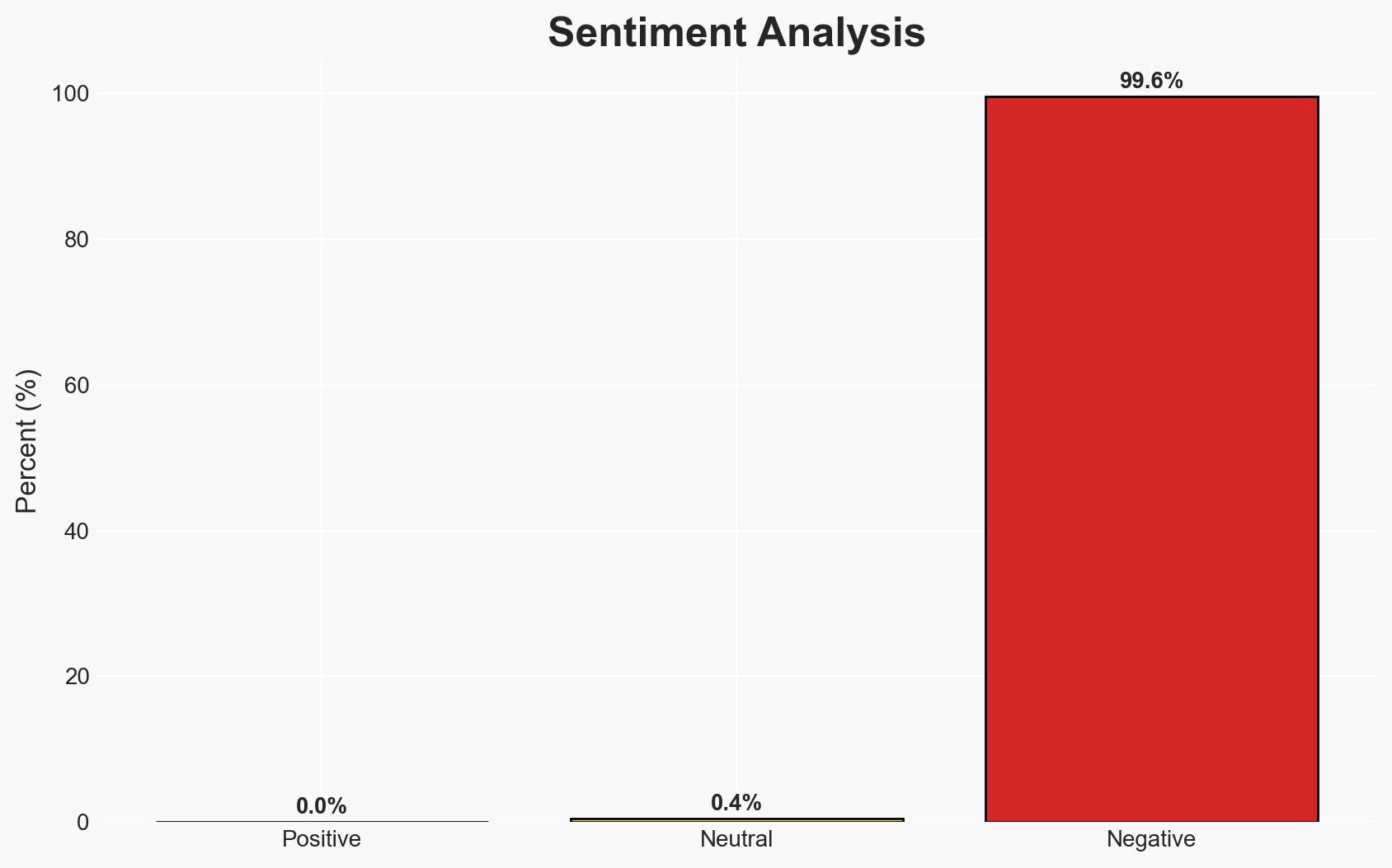
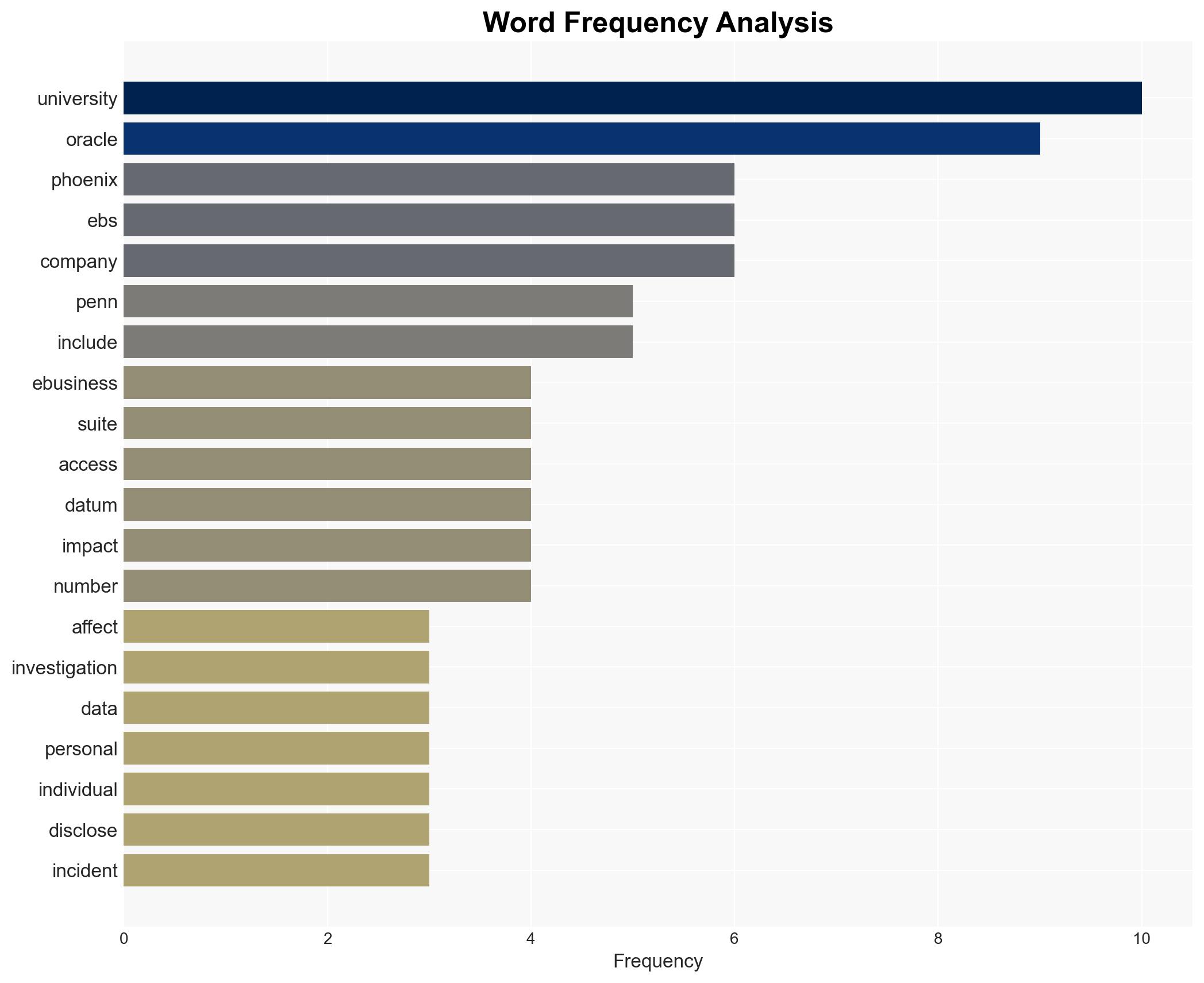
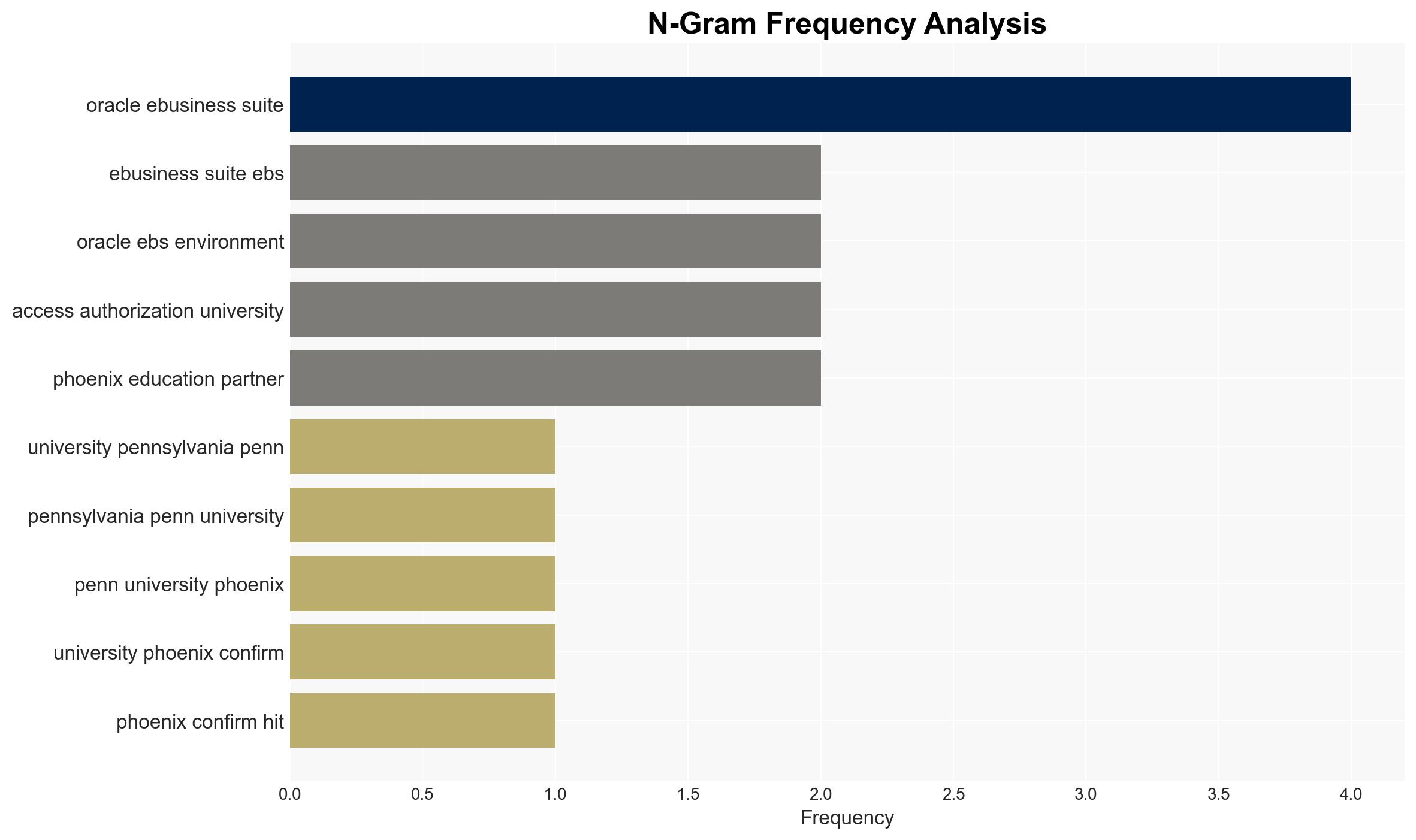
The University of Pennsylvania and the University of Phoenix have disclosed data breaches due to a vulnerability in Oracle’s E-Business Suite, affecting personal data of numerous individuals. The most likely hypothesis is that the breaches are part of a broader campaign targeting multiple organizations using Oracle EBS. The overall confidence level in this assessment is moderate, given the ongoing investigations and limited public disclosure of specific details.
2. Competing Hypotheses
- Hypothesis A: The breaches are part of a coordinated cyber campaign exploiting a specific vulnerability in Oracle EBS, targeting multiple organizations simultaneously. This is supported by the fact that several universities, including Harvard, were affected, and the vulnerability was unknown prior to the incidents. However, the exact scope and intent of the campaign remain unclear.
- Hypothesis B: The breaches are isolated incidents resulting from individual targeting of the universities due to their specific vulnerabilities in Oracle EBS. This hypothesis is less supported as the pattern of multiple institutions being affected suggests a broader campaign rather than isolated incidents.
- Assessment: Hypothesis A is currently better supported due to the pattern of multiple organizations being affected by the same vulnerability. Indicators that could shift this judgment include evidence of targeted motives or further disclosures of similar breaches in unrelated sectors.
3. Key Assumptions and Red Flags
- Assumptions: The Oracle EBS vulnerability was previously unknown; the breaches are not yet linked to any specific threat actor; the data accessed has not been publicly disclosed or misused.
- Information Gaps: Specific details on the number of affected individuals, the exact nature of the data accessed, and the identity of the threat actors remain unknown.
- Bias & Deception Risks: Potential bias in university disclosures to minimize reputational damage; lack of independent verification of claims regarding data misuse.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on Oracle’s software security and broader concerns about the vulnerability of educational institutions to cyber threats.
- Political / Geopolitical: Potential for increased regulatory pressure on software providers to ensure security compliance.
- Security / Counter-Terrorism: Heightened awareness and potential for increased cyber defense measures in educational institutions.
- Cyber / Information Space: Increased focus on patch management and vulnerability assessments in widely used software platforms.
- Economic / Social: Potential financial implications for affected individuals and reputational damage to the institutions involved.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough vulnerability assessments, enhance monitoring of Oracle EBS environments, and engage with Oracle for patch updates.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms, invest in staff training, and improve incident response capabilities.
- Scenario Outlook:
- Best: Vulnerability is patched, and no further incidents occur.
- Worst: Additional breaches occur, leading to significant data misuse.
- Most-Likely: Continued investigation reveals more affected entities, but no major misuse of data.
6. Key Individuals and Entities
- University of Pennsylvania
- University of Phoenix
- Oracle Corporation
- Federal Law Enforcement (unspecified)
- Experian (credit monitoring service)
7. Thematic Tags
Cybersecurity, data breach, higher education, Oracle E-Business Suite, vulnerability management, information security, regulatory compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us