Pentagon’s inspector general flags Hegseth for improper use of Signal chat in sensitive military communicatio…
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Inspector general report raises concerns about Hegseths use of Signal chat
1. BLUF (Bottom Line Up Front)
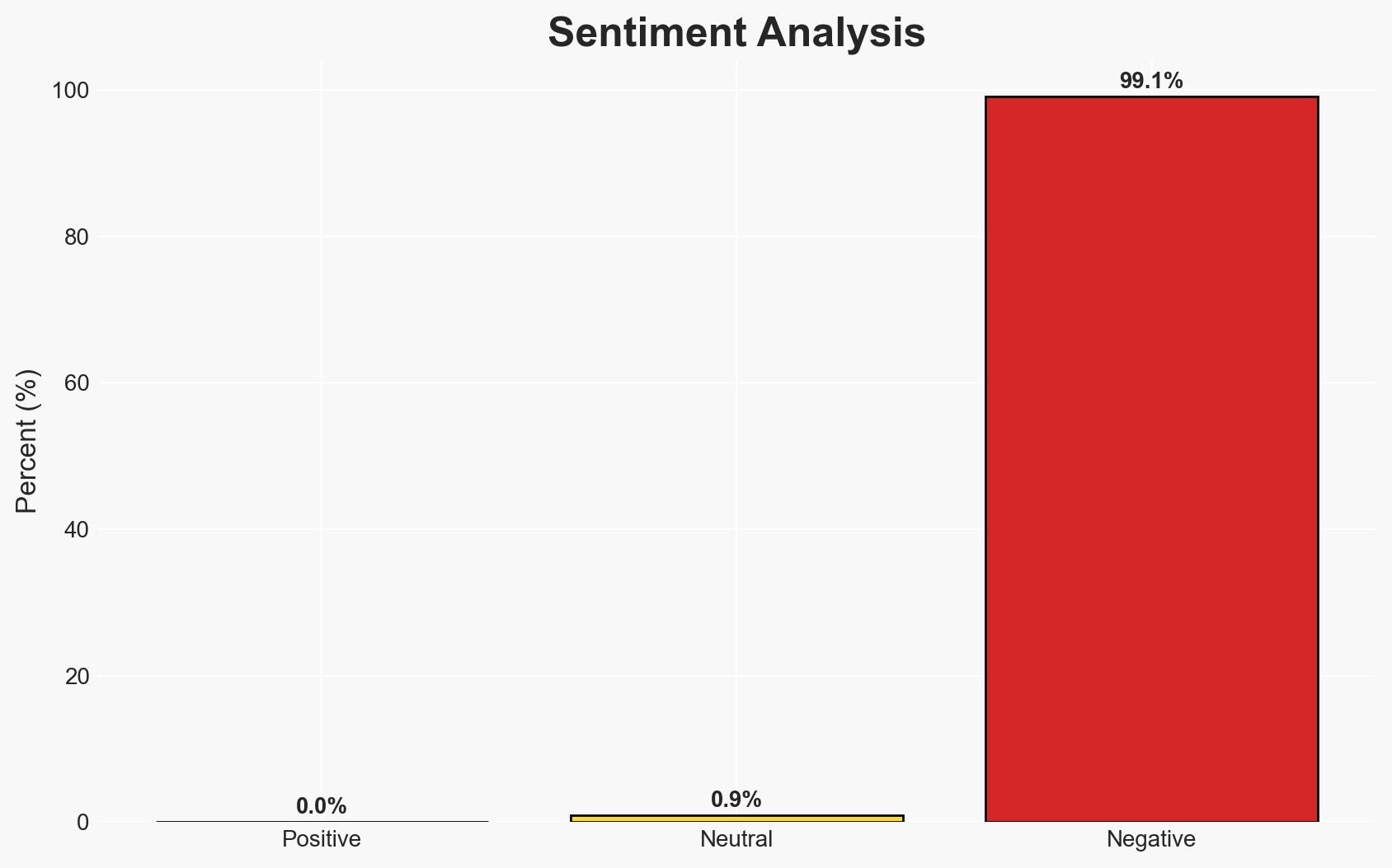
The Inspector General’s report highlights potential operational security risks due to Secretary of Defense Pete Hegseth’s use of Signal for sensitive communications. The report does not conclude whether classified information was shared, but it underscores the need for compliance with security protocols. This situation affects U.S. military operations and could have broader implications for national security. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Hegseth’s use of Signal compromised operational security by sharing sensitive information. This is supported by the Inspector General’s findings and media reports, but contradicted by the lack of evidence that the information was classified.
- Hypothesis B: Hegseth’s actions did not compromise security as the information was either not classified or appropriately declassified. This is supported by Hegseth’s authority to declassify information and his spokesperson’s statements, but lacks independent verification.
- Assessment: Hypothesis B is currently better supported due to the Secretary’s authority to declassify information and the absence of evidence proving the information was classified. However, further confirmation of the classification status could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The information shared was not classified at the time; Hegseth had the authority to declassify; the Inspector General’s report is accurate and unbiased.
- Information Gaps: The exact nature and classification status of the information shared; the full content of the Inspector General’s report.
- Bias & Deception Risks: Potential bias in media reporting; possible manipulation in the portrayal of the incident by involved parties.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of communication practices within the U.S. government, potentially affecting policy and operational protocols.
- Political / Geopolitical: Potential erosion of trust in U.S. leadership and its handling of sensitive information.
- Security / Counter-Terrorism: Increased risk to military operations if communication protocols are not strengthened.
- Cyber / Information Space: Highlighting vulnerabilities in the use of personal devices for official communications.
- Economic / Social: Possible impact on public confidence in government transparency and accountability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of communication protocols; enhance training on operational security.
- Medium-Term Posture (1–12 months): Develop partnerships for secure communication solutions; implement regular audits of communication practices.
- Scenario Outlook: Best: Strengthened security protocols prevent future incidents. Worst: Continued breaches lead to compromised operations. Most-Likely: Incremental improvements in communication security with ongoing challenges.
6. Key Individuals and Entities
- Pete Hegseth, Mike Waltz, Jeffrey Goldberg, JD Vance, Marco Rubio
7. Thematic Tags
National Security Threats, operational security, military communications, information security, government transparency, national security, cyber risk
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us