Identity Breaches: A Growing Threat to Cybersecurity for Major Retailers and Beyond
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Phishing privileges and passwords Why identity is critical to improving cybersecurity posture
1. BLUF (Bottom Line Up Front)
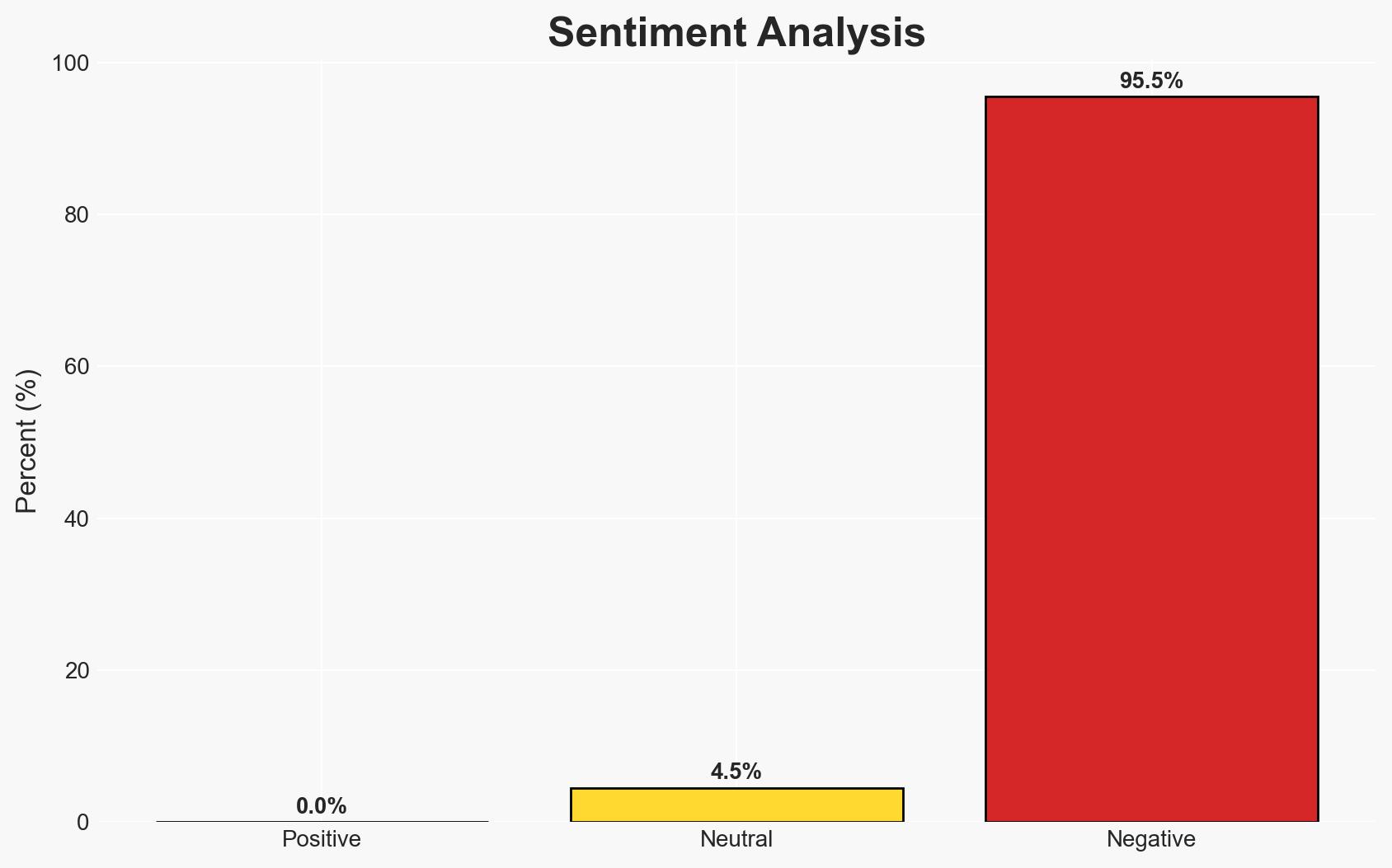
Identity-based cyber attacks, such as those experienced by M&S and Co-op Group, highlight the increasing vulnerability of organizations to credential-based breaches. The shift from traditional network perimeters to identity as the new security boundary has made credentials a prime target for cybercriminals. This trend poses significant risks to various sectors, including critical infrastructure. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The increase in identity-based attacks is primarily driven by the decentralization of IT environments and the proliferation of remote work, which have expanded the attack surface. Supporting evidence includes the widespread use of cloud services and mobile devices, which complicate traditional perimeter defenses. However, the extent to which this decentralization directly correlates with increased breaches remains uncertain.
- Hypothesis B: The rise in identity-based attacks is largely due to improved tactics and capabilities of threat actors, who are increasingly adept at exploiting human factors and technical vulnerabilities. Evidence includes the sophistication of phishing and vishing techniques and the availability of stolen credentials on cybercrime forums. Contradicting this is the lack of detailed attribution to specific threat actor groups.
- Assessment: Hypothesis A is currently better supported due to the observable shift in IT infrastructure and the documented increase in remote work, which collectively broaden the attack surface. Indicators such as further decentralization of IT resources or increased sophistication in attack methods could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will continue to decentralize IT resources; threat actors will maintain or increase their focus on credential theft; current security measures are insufficient against evolving threats.
- Information Gaps: Specific attribution of attacks to particular threat actors or groups; detailed impact assessments of breaches on affected organizations.
- Bias & Deception Risks: Potential bias in attributing breaches solely to decentralization without considering other factors; deception risks from threat actors using false flags or misdirection.
4. Implications and Strategic Risks
As identity-based attacks continue to rise, organizations face increased pressure to adapt their cybersecurity strategies. The evolving threat landscape may lead to more sophisticated attacks and broader impacts across sectors.
- Political / Geopolitical: Potential for increased international tensions if state-sponsored actors are implicated in identity-based attacks.
- Security / Counter-Terrorism: Heightened threat environment with potential for critical infrastructure disruptions.
- Cyber / Information Space: Increased demand for advanced identity management solutions and cybersecurity innovations.
- Economic / Social: Potential economic losses and reputational damage for affected organizations, leading to decreased consumer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of credential access and implement multi-factor authentication across all systems.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to improve threat intelligence sharing and response capabilities.
- Scenario Outlook:
- Best: Organizations successfully adapt to the new threat landscape, reducing the frequency and impact of identity-based attacks.
- Worst: Continued increase in breaches leads to significant economic and operational disruptions across sectors.
- Most-Likely: Incremental improvements in cybersecurity posture mitigate some risks, but identity-based attacks remain a persistent threat.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
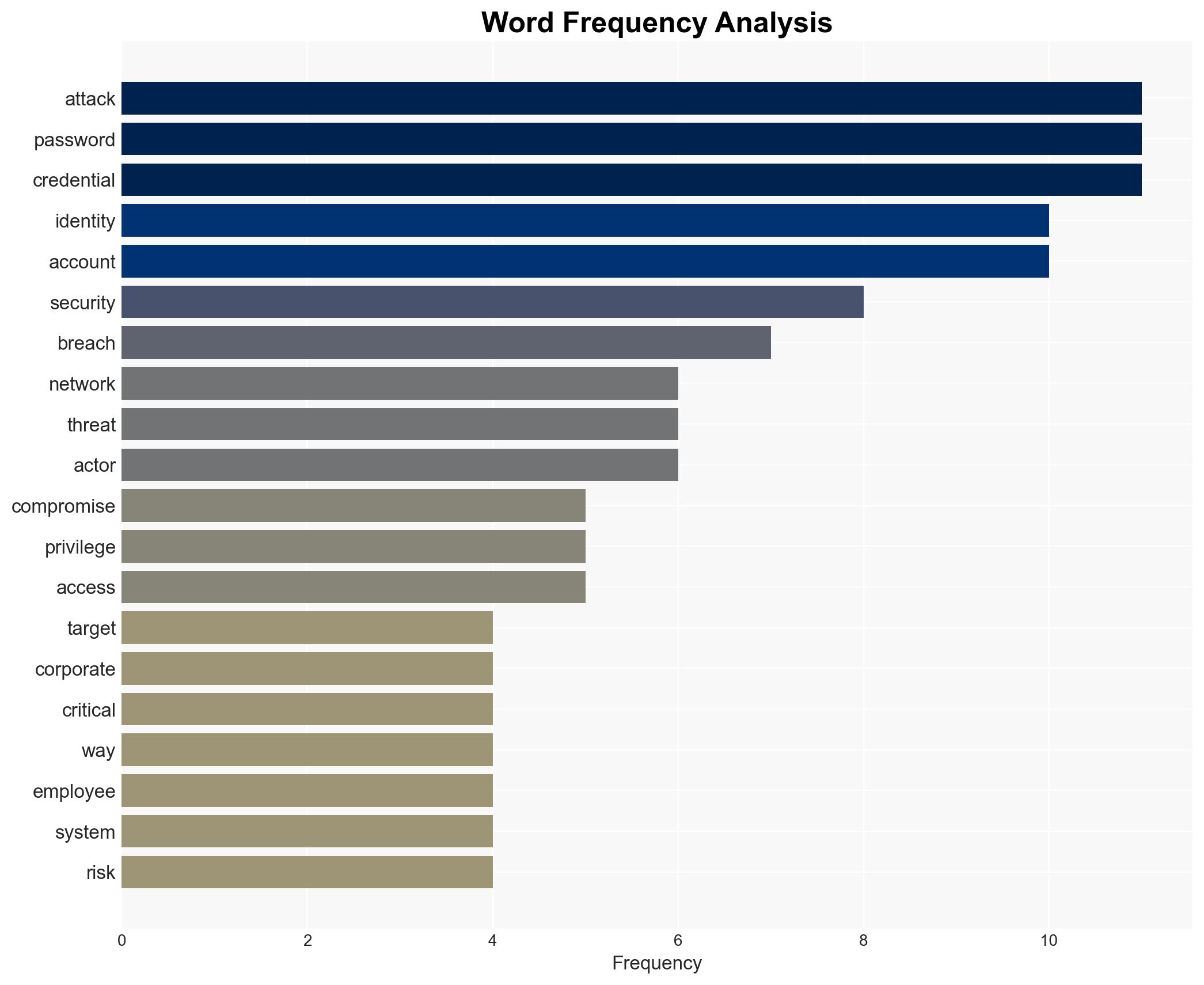
Cybersecurity, identity management, ransomware, credential theft, IT infrastructure, phishing, vishing
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us