Inspector General Urges Review of Classification Procedures Following SignalGate Incident Involving Sensitive…
Published on: 2025-12-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: SignalGate Inspector General Report Wants Just One Change to Avoid a Repeat Debacle
1. BLUF (Bottom Line Up Front)
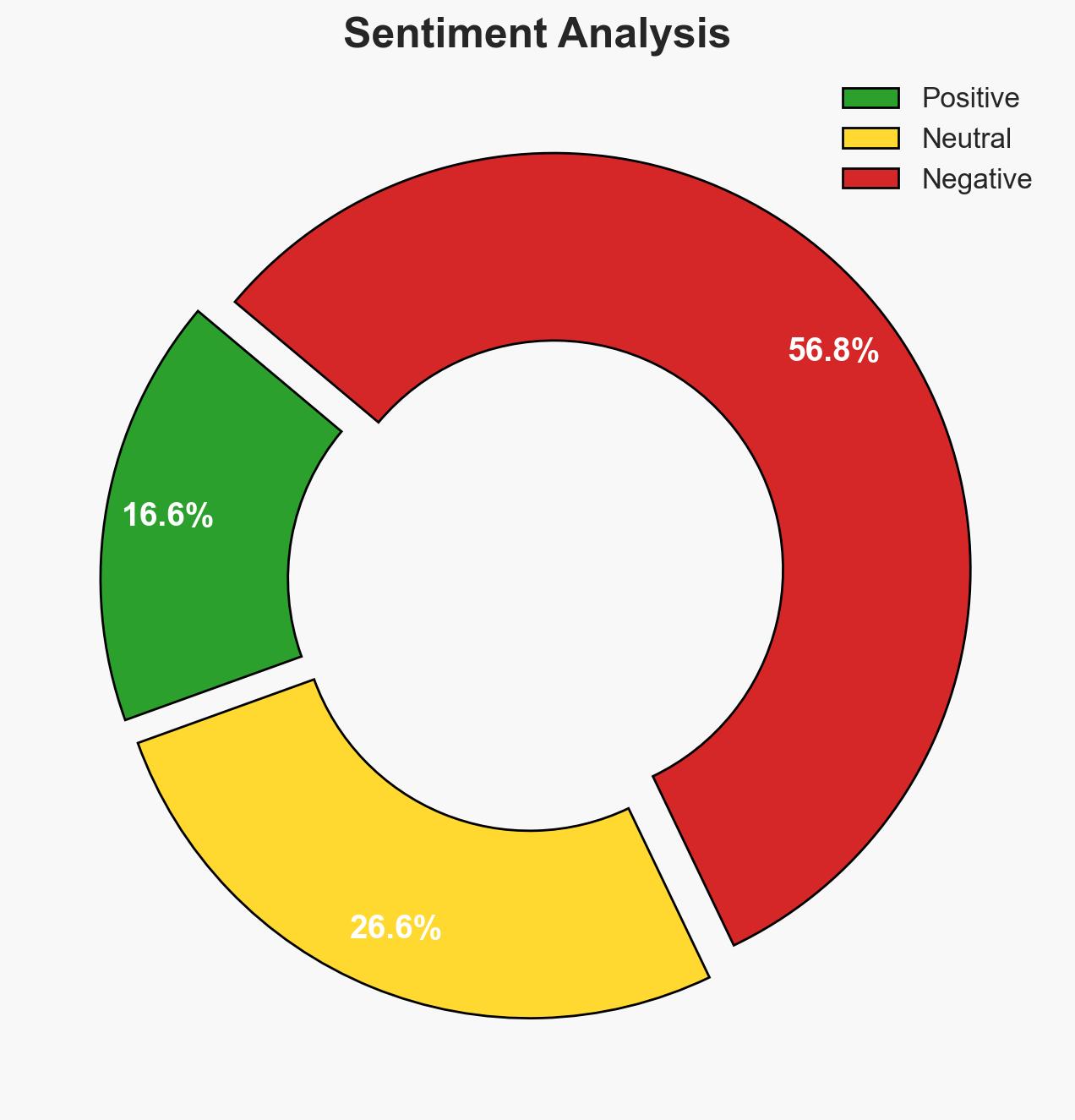
The Inspector General’s report highlights a significant operational security lapse involving the use of a consumer messaging app by senior defense officials, potentially compromising sensitive military operations. The primary recommendation is to review classification procedures. This incident underscores the need for stringent communication protocols. Overall confidence in this assessment is moderate, given the lack of direct testimony from key individuals involved.
2. Competing Hypotheses
- Hypothesis A: The use of Signal was a deliberate decision by Secretary Hegseth, believing it was secure enough for the information shared. This is supported by his role as the original classification authority and his statement about operational security. However, the accidental inclusion of a journalist contradicts this belief in security.
- Hypothesis B: The use of Signal was an oversight or a result of inadequate training on secure communication protocols. The IG report’s recommendation for improved training supports this, but the lack of direct interviews with Hegseth leaves uncertainties.
- Assessment: Hypothesis B is currently better supported due to the IG’s focus on training deficiencies and procedural compliance. Future revelations or testimony from involved parties could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The information shared on Signal was sensitive enough to warrant secure channels; Hegseth’s decision-making process was not fully documented; the IG report’s recommendations are based on a comprehensive review.
- Information Gaps: Direct insights from Secretary Hegseth and other involved officials; detailed analysis of the security implications of the information shared.
- Bias & Deception Risks: Potential bias in the IG report due to lack of direct interviews; risk of minimizing the incident’s severity due to political pressures.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny of communication practices within the Department of Defense and potential policy changes. It may also impact trust in leadership and operational security protocols.
- Political / Geopolitical: Potential for congressional oversight and policy reform; international allies may question the U.S.’s operational security practices.
- Security / Counter-Terrorism: Possible exploitation by adversaries aware of communication vulnerabilities; need for enhanced operational security measures.
- Cyber / Information Space: Highlighting vulnerabilities in using consumer apps for sensitive communications; potential increase in cyber threats targeting such platforms.
- Economic / Social: Limited direct impact, but potential indirect effects on defense-related industries and public trust in government security practices.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough review of current communication protocols; initiate immediate training for senior officials on secure communication practices.
- Medium-Term Posture (1–12 months): Develop and implement enhanced security measures for electronic communications; foster partnerships with tech companies to improve secure communication tools.
- Scenario Outlook:
- Best: Successful implementation of new protocols, restoring confidence in operational security.
- Worst: Continued lapses leading to significant security breaches.
- Most-Likely: Gradual improvement in communication practices with periodic reviews and updates.
6. Key Individuals and Entities
- Pete Hegseth, Secretary of Defense
- Michael Waltz, Former National Security Adviser
- Jeffrey Goldberg, Journalist
- US Central Command’s Special Security Office
7. Thematic Tags
National Security Threats, operational security, military communications, cyber security, information security, defense policy, intelligence oversight
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us