Pete Hegseth Exonerated in Signal App Investigation Despite Violating Security Protocols
Published on: 2025-12-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Defense Secretary Pete Hegseth CLEARED in Signalgate scandal
1. BLUF (Bottom Line Up Front)
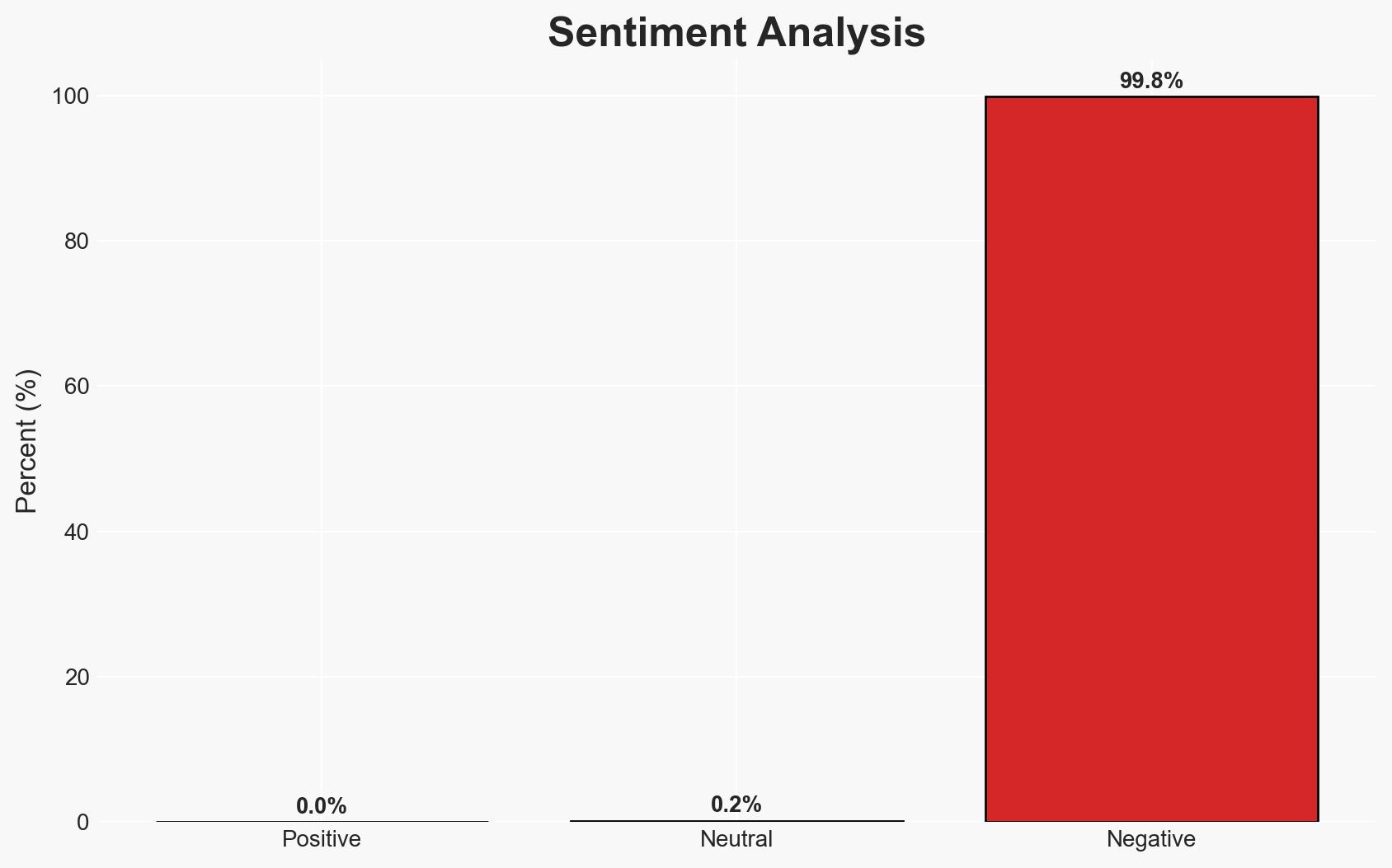
The investigation into Defense Secretary Pete Hegseth’s use of the Signal app concluded with his exoneration, though it highlighted poor judgment in handling sensitive information. The incident underscores tensions between modern communication practices and security protocols. The overall confidence in this assessment is moderate, given the incomplete evidence and potential biases influencing the investigation’s outcome.
2. Competing Hypotheses
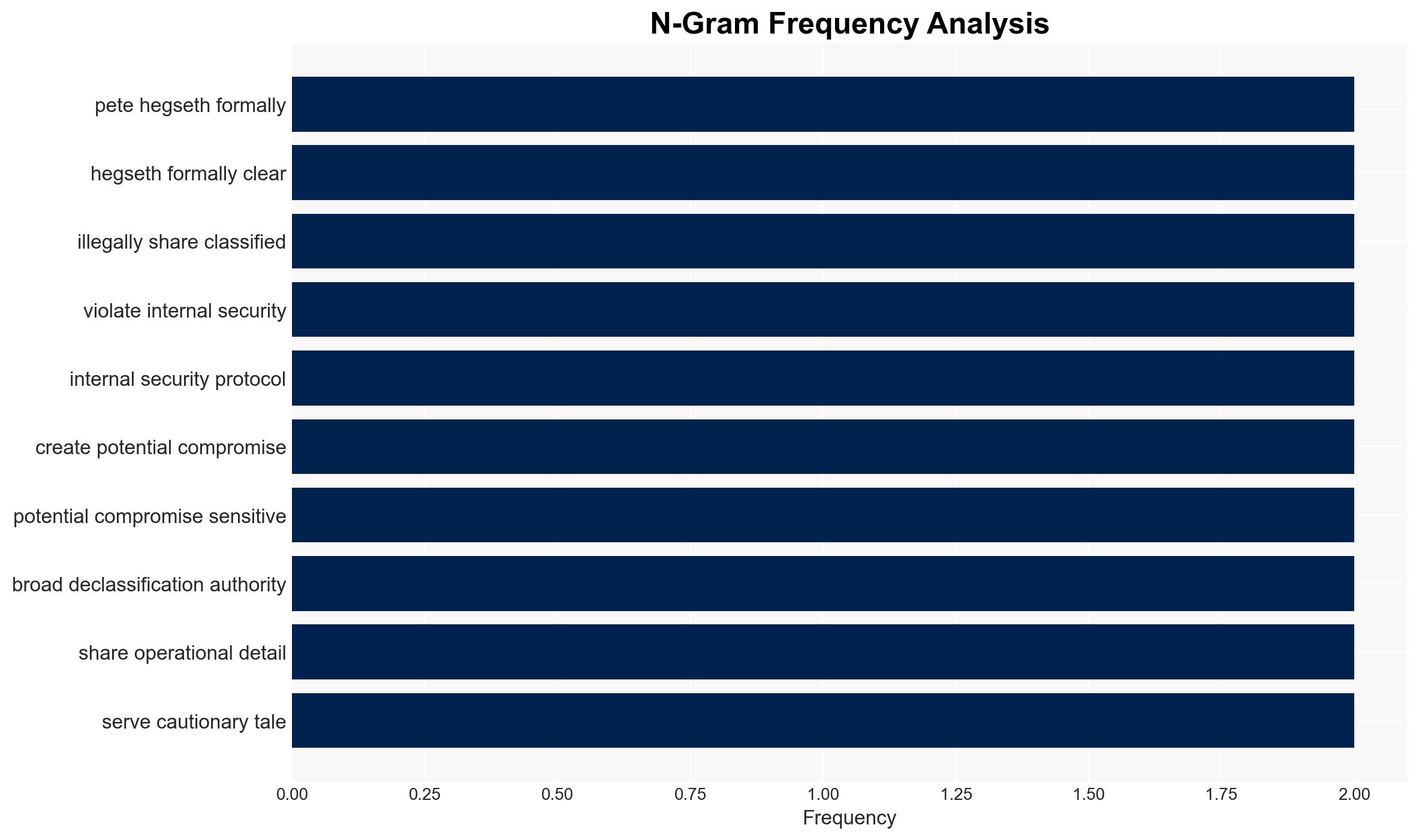
- Hypothesis A: Secretary Hegseth’s actions, while technically legal due to his declassification authority, represented a significant lapse in judgment that risked compromising sensitive information. Supporting evidence includes the use of an unapproved app and the potential exposure of operational details. Contradicting evidence is the formal exoneration and lack of illegal classified information sharing.
- Hypothesis B: The investigation’s findings are politically motivated, aiming to clear Hegseth of wrongdoing despite genuine security risks. Supporting evidence includes skepticism due to incomplete evidence and dismantled phone systems. Contradicting evidence is the official conclusion of no obstruction and legal permissibility of actions.
- Assessment: Hypothesis A is currently better supported due to the explicit acknowledgment of poor judgment and potential risks, despite the legal permissibility of actions. Indicators that could shift this judgment include new evidence of deliberate information exposure or political manipulation.
3. Key Assumptions and Red Flags
- Assumptions: The investigation was conducted impartially; Hegseth’s authority to declassify was appropriately applied; the use of Signal was not intended for malicious purposes.
- Information Gaps: Details on the content of deleted messages; full scope of the dismantled phone-access system; potential external influences on the investigation.
- Bias & Deception Risks: Potential bias from political affiliations; media framing influencing public perception; possible manipulation of evidence or narrative by involved parties.
4. Implications and Strategic Risks
This development may influence future policy on communication security protocols for senior officials and impact public trust in military leadership. It could also affect U.S. credibility in international security partnerships.
- Political / Geopolitical: Potential for increased scrutiny and legislative action on communication practices; international allies may question U.S. operational security.
- Security / Counter-Terrorism: Possible reassessment of internal security measures; heightened risk of information leaks in similar future scenarios.
- Cyber / Information Space: Increased focus on securing digital communication platforms; potential exploitation by adversaries of perceived vulnerabilities.
- Economic / Social: Limited direct economic impact; potential erosion of public confidence in government transparency and accountability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of communication protocols; enhance monitoring of sensitive information channels.
- Medium-Term Posture (1–12 months): Develop and implement stricter guidelines for digital communication; foster partnerships with tech firms to secure platforms.
- Scenario Outlook:
- Best: Strengthened security measures prevent future incidents, restoring confidence.
- Worst: Continued lapses lead to significant information breaches, damaging U.S. interests.
- Most-Likely: Incremental policy adjustments improve security without major incidents.
6. Key Individuals and Entities
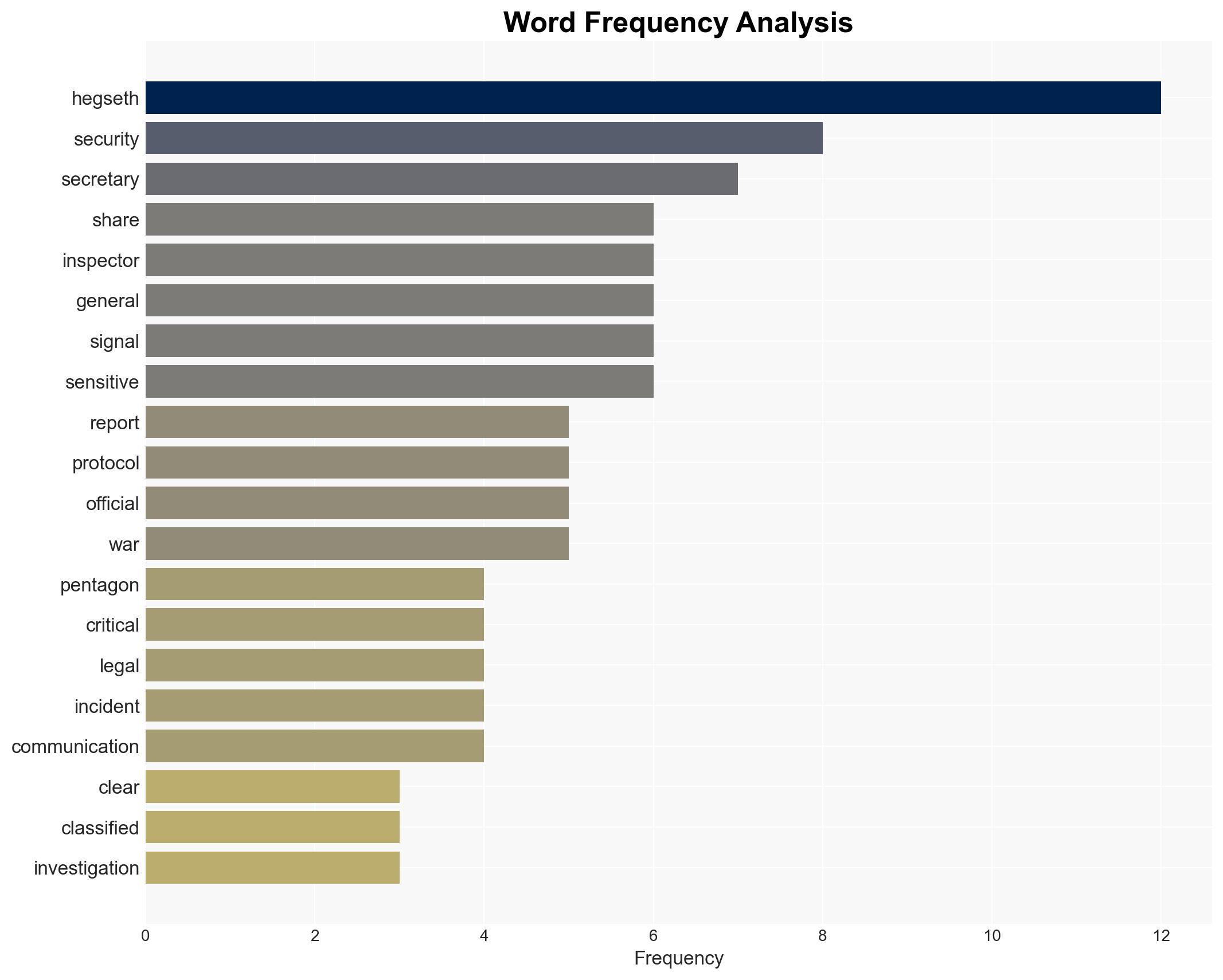
- Pete Hegseth – U.S. Secretary of Defense
- Sean Parnell – Pentagon spokesman
- Jeffrey Goldberg – Editor-in-Chief, The Atlantic
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
National Security Threats, national security, digital communication, information security, political accountability, military protocols, executive discretion, media influence
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Structured challenge to expose and correct biases.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us