US develops cost-effective drones inspired by Iranian Shahed-136 for increased operational capabilities in wa…
Published on: 2025-12-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US reverse-engineers Iranian Shahed drone for cheap high-volume warfare
1. BLUF (Bottom Line Up Front)
The United States has initiated a strategic shift towards low-cost, high-volume drone warfare by reverse-engineering Iran’s Shahed-136 drone, resulting in the deployment of the LUCAS system. This development is likely to enhance U.S. operational capabilities in the Middle East, countering Iranian and proxy drone threats. The overall confidence level in this assessment is moderate, given existing information gaps and potential bias in source reporting.
2. Competing Hypotheses
- Hypothesis A: The U.S. adoption of low-cost drones is primarily a response to the operational effectiveness of Iranian Shahed drones in the Middle East. Supporting evidence includes the U.S. CENTCOM’s emphasis on countering Iranian drone threats and the operational debut of LUCAS. However, uncertainties remain regarding the long-term strategic intent and potential technological limitations of LUCAS.
- Hypothesis B: The U.S. is leveraging the LUCAS program as a broader strategic pivot towards attritable drone warfare, independent of specific Iranian threats. This hypothesis is supported by the broader context of evolving drone warfare strategies globally. Contradicting evidence includes the specific mention of countering Iranian proxies in CENTCOM’s communications.
- Assessment: Hypothesis A is currently better supported due to explicit references to Iranian threats in official statements. Key indicators that could shift this judgment include changes in U.S. drone deployment patterns outside the Middle East or new strategic communications from the Pentagon.
3. Key Assumptions and Red Flags
- Assumptions: The U.S. has successfully reverse-engineered the Shahed-136; LUCAS drones are cost-effective and operationally viable; Iranian drone threats are a primary concern for CENTCOM; U.S. drone strategy is adaptable to high-volume deployment.
- Information Gaps: Detailed technical specifications of LUCAS; full scope of U.S. drone deployment plans; Iranian and proxy countermeasures to LUCAS.
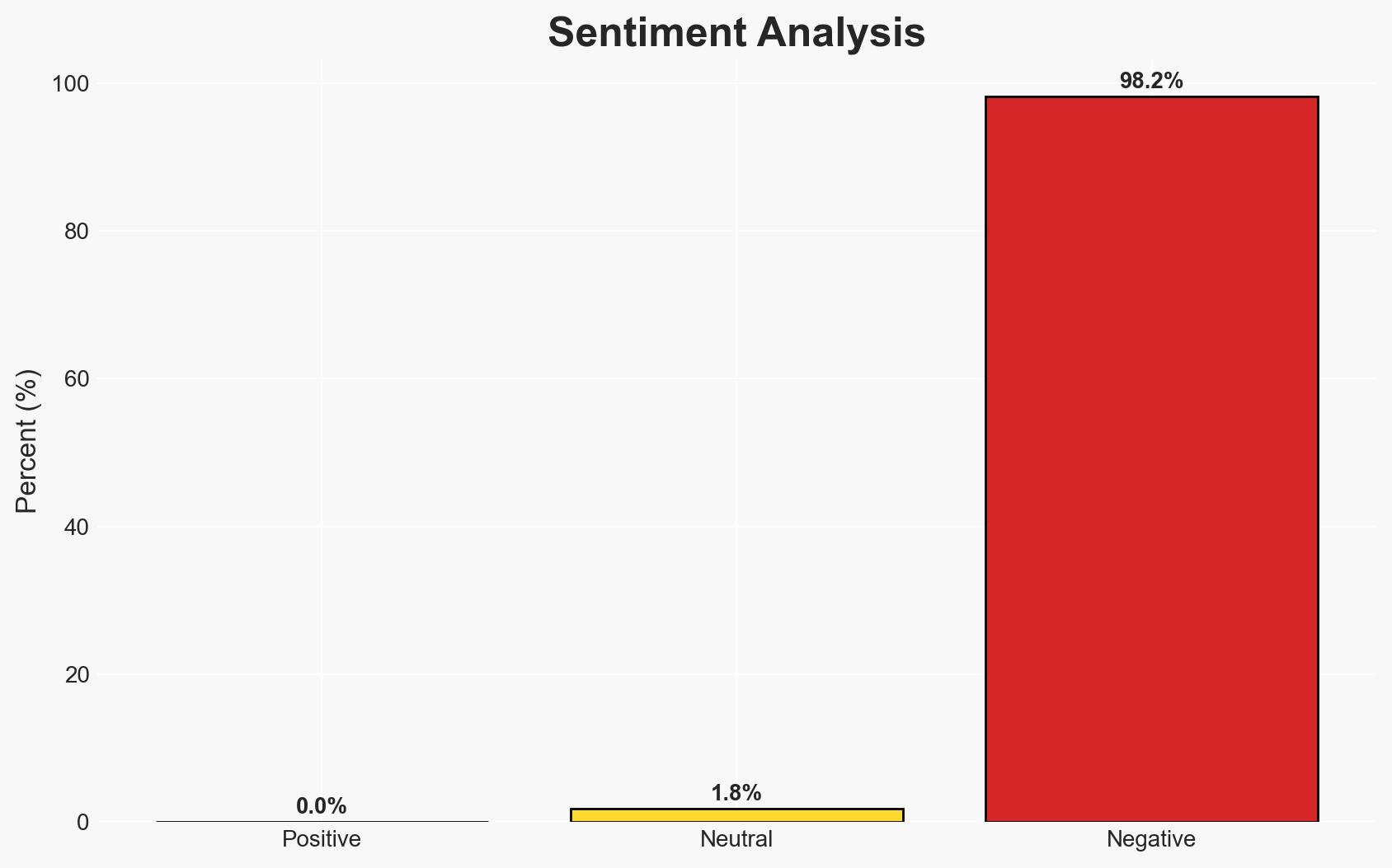
- Bias & Deception Risks: Potential bias in source reporting favoring U.S. military capabilities; risk of Iranian misinformation regarding Shahed drone capabilities or deployment.
4. Implications and Strategic Risks
This development could lead to increased drone warfare in the Middle East, potentially escalating regional tensions and altering the balance of power. The U.S. shift to attritable drones may influence other nations’ military strategies.
- Political / Geopolitical: Potential escalation in U.S.-Iran tensions; influence on Middle Eastern allies’ defense strategies.
- Security / Counter-Terrorism: Enhanced U.S. capabilities to counter drone threats; possible proliferation of similar technologies to other state and non-state actors.
- Cyber / Information Space: Increased risk of cyber-attacks targeting drone command and control systems; potential for information warfare exploiting drone incidents.
- Economic / Social: Impact on defense spending priorities; potential civilian casualties and infrastructure damage from increased drone use.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence collection on Iranian drone capabilities and countermeasures; monitor regional reactions to LUCAS deployment.
- Medium-Term Posture (1–12 months): Develop partnerships with regional allies for joint drone defense initiatives; invest in counter-drone technologies.
- Scenario Outlook:
- Best: Successful deterrence of Iranian drone threats without escalation.
- Worst: Escalation into broader conflict involving regional allies.
- Most-Likely: Continued low-intensity drone engagements with periodic escalations.
6. Key Individuals and Entities
- U.S. Central Command (CENTCOM)
- Task Force Scorpion Strike (TFSS)
- Iranian military and proxy groups
- Paul Iddon, Defense Journalist
7. Thematic Tags
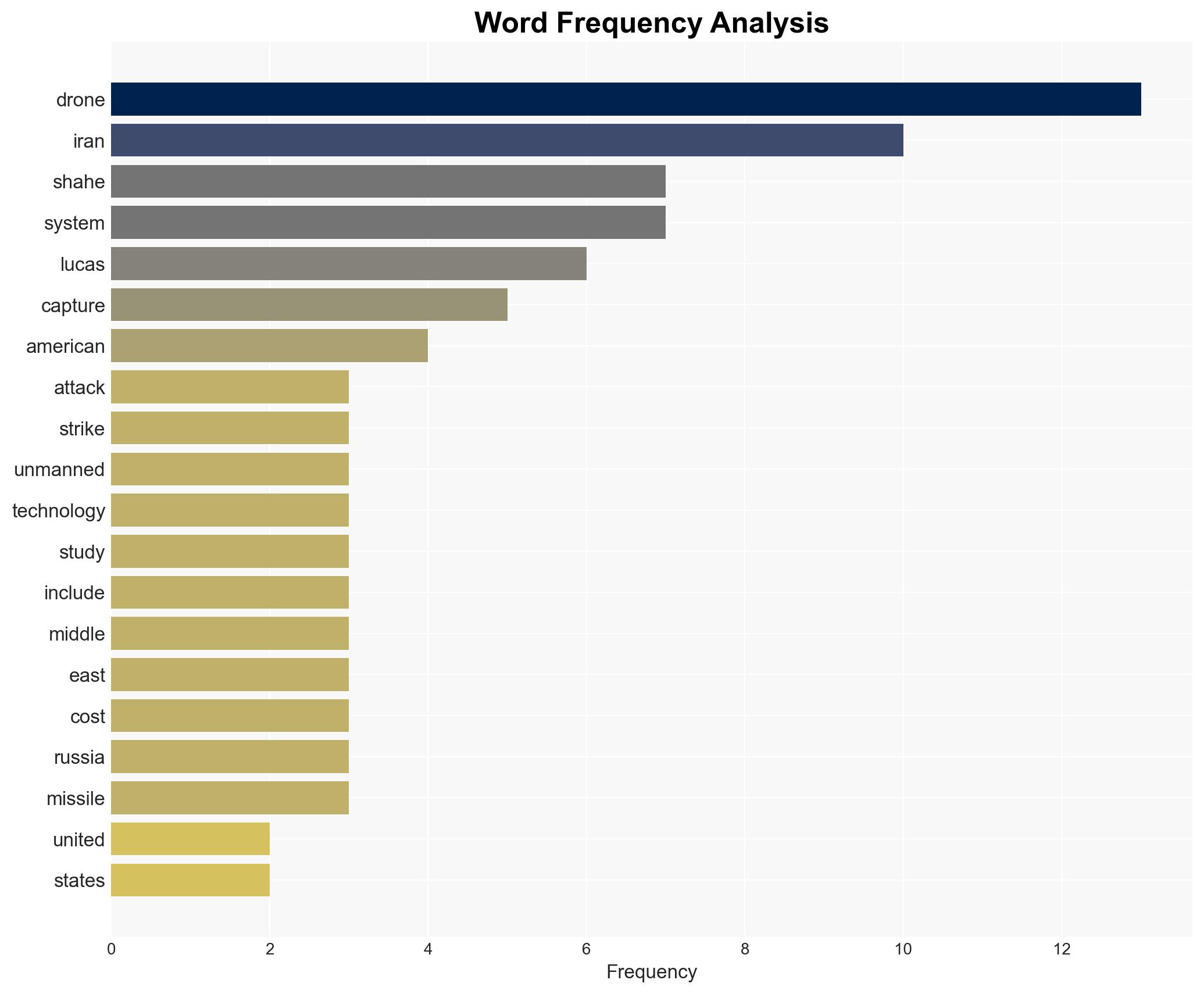
Counter-Terrorism, drone warfare, reverse engineering, Middle East security, U.S. military strategy, Iranian proxies, defense technology, attritable drones
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us