Russia, China, Iran, and North Korea Intensify Coordinated Threats to U.S. National Security
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: How Russia China Iran And North Korea Are Coordinating Against The US
1. BLUF (Bottom Line Up Front)
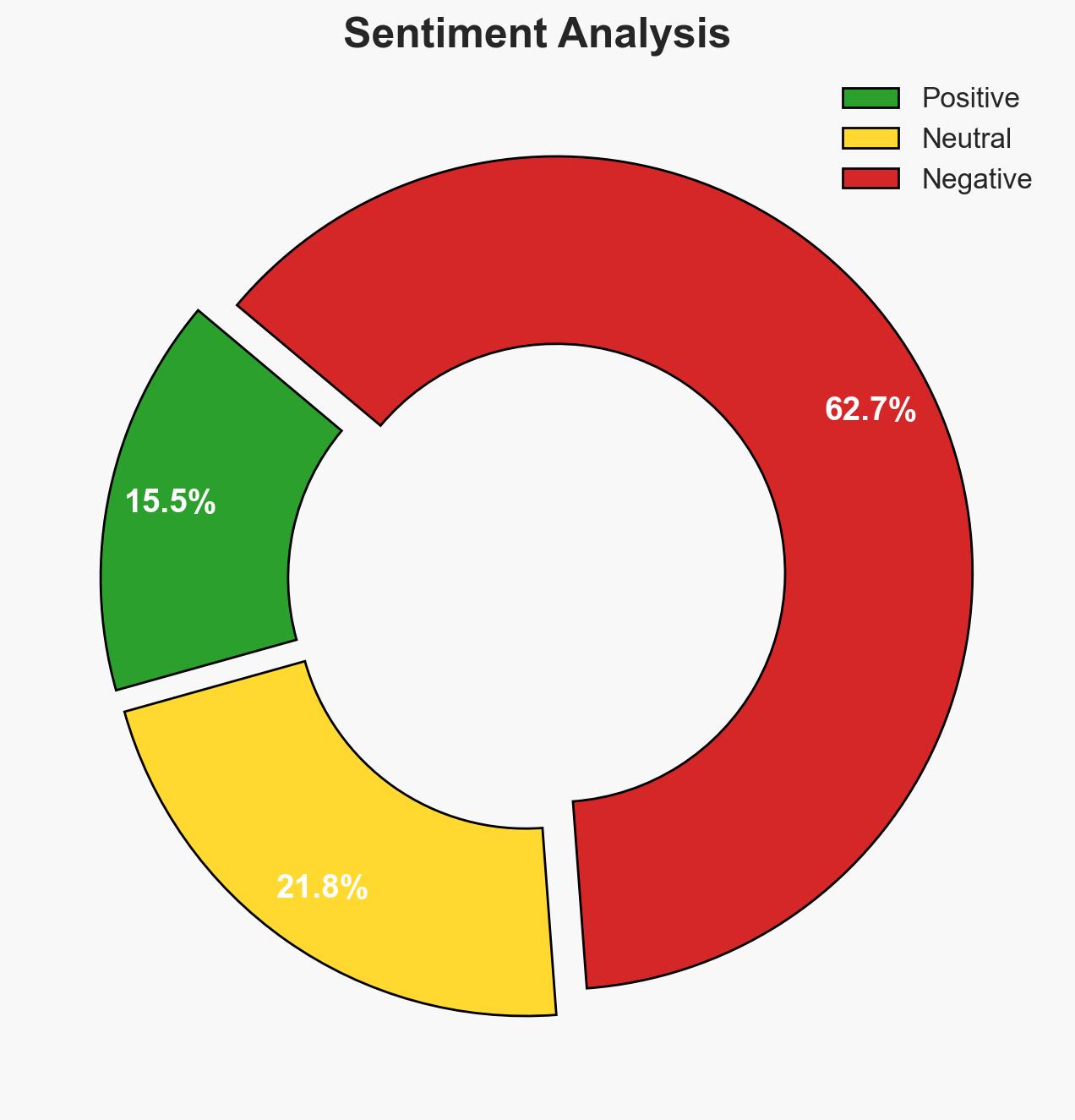
Russia, China, Iran, and North Korea are increasingly coordinating their activities against the United States, posing significant threats to national security, economic stability, and democratic processes. This coordination is evidenced by joint military exercises and cyber operations. The current assessment is made with moderate confidence due to existing information gaps and potential deception. Policymakers and intelligence agencies are the primary stakeholders affected.
2. Competing Hypotheses
- Hypothesis A: The four nations are deliberately coordinating their actions to strategically undermine U.S. interests. Evidence includes joint military exercises and shared cyber tactics. However, the extent of formal coordination remains uncertain.
- Hypothesis B: The observed activities are coincidental or opportunistic rather than a result of formal coordination. While there is evidence of parallel actions, there is limited direct evidence of a unified strategy.
- Assessment: Hypothesis A is currently better supported due to documented instances of military and cyber cooperation. Indicators such as increased joint military exercises and shared technology transfers could further substantiate this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: The nations involved have the capability and intent to coordinate; their actions are primarily driven by anti-U.S. objectives; the U.S. intelligence assessments are accurate and unbiased.
- Information Gaps: Specific details on the extent of coordination and strategic objectives; internal communications between these nations regarding joint operations.
- Bias & Deception Risks: Potential confirmation bias in interpreting adversary actions as coordinated; possible adversary deception to exaggerate the perception of coordination.
4. Implications and Strategic Risks
The evolving coordination among these adversaries could lead to increased geopolitical tensions and destabilization in regions of strategic interest to the U.S. Over time, this may result in more sophisticated and synchronized threats.
- Political / Geopolitical: Potential escalation in regional conflicts, particularly in East Asia and the Middle East, involving U.S. allies.
- Security / Counter-Terrorism: Enhanced threat environment with more complex and integrated adversary operations.
- Cyber / Information Space: Increased cyber-espionage and misinformation campaigns targeting U.S. infrastructure and public opinion.
- Economic / Social: Potential disruptions in global markets and increased pressure on U.S. economic interests abroad.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase intelligence sharing with allies, enhance monitoring of joint military and cyber activities, and strengthen defensive cyber measures.
- Medium-Term Posture (1–12 months): Develop resilience strategies, reinforce alliances, and invest in counterintelligence capabilities to detect and mitigate coordinated threats.
- Scenario Outlook:
- Best Case: Improved diplomatic engagements reduce tensions and lead to de-escalation.
- Worst Case: Heightened coordination results in significant cyber or military incidents.
- Most Likely: Continued low-level coordination with periodic escalations in specific domains.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, national security, cyber-espionage, military cooperation, geopolitical tensions, intelligence sharing, counterintelligence, economic stability
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us