Emerging Ransomware Threats to Storage Systems: Key Trends for 2026
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware trends targeting storage systems in 2026
1. BLUF (Bottom Line Up Front)
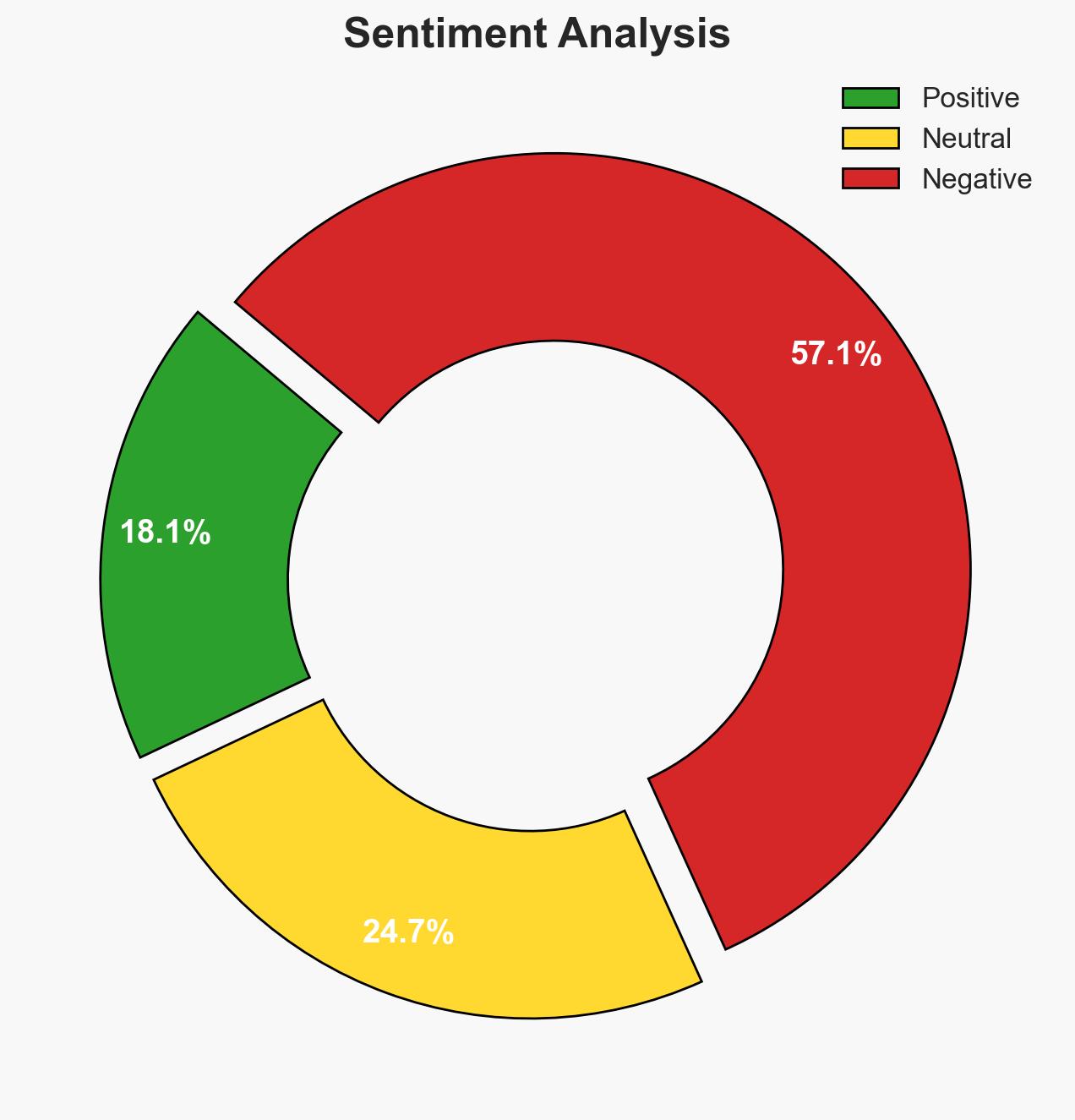
In 2026, ransomware attacks targeting storage systems are expected to increase in sophistication, leveraging AI to exploit vulnerabilities. Enterprises of all sizes will be affected, necessitating enhanced security measures such as zero-trust architectures and immutable storage solutions. Overall, there is moderate confidence in this assessment due to the evolving nature of cyber threats and the rapid development of ransomware-as-a-service models.
2. Competing Hypotheses
- Hypothesis A: Ransomware attacks will primarily target storage systems due to their critical role in enterprise operations. This is supported by the increasing use of AI in attacks and the vulnerabilities inherent in storage technologies. However, the extent of AI’s role remains uncertain.
- Hypothesis B: While storage systems are a target, attackers may diversify their focus to include other critical infrastructure sectors. This hypothesis is supported by the broader trend of cyber threats targeting multiple sectors, though specific evidence from the snippet is lacking.
- Assessment: Hypothesis A is currently better supported due to the specific mention of storage systems as primary targets and the detailed description of vulnerabilities. Indicators such as increased AI-driven attacks on storage systems could further support this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: Storage systems will remain a critical target for ransomware; AI will significantly enhance the capability of ransomware attacks; enterprises will adopt zero-trust architectures.
- Information Gaps: Specific data on the frequency and success rate of AI-driven ransomware attacks; detailed case studies of recent storage system breaches.
- Bias & Deception Risks: Potential bias in underestimating the adaptability of threat actors; reliance on open-source information may overlook classified threat intelligence.
4. Implications and Strategic Risks
The evolution of ransomware targeting storage systems could lead to significant disruptions in enterprise operations, affecting data integrity and availability. Over time, this may necessitate a reevaluation of cybersecurity strategies and increased investment in advanced security technologies.
- Political / Geopolitical: Increased cyber threats could strain international relations, particularly if state-sponsored actors are involved.
- Security / Counter-Terrorism: Enhanced threat landscape may require new countermeasures and collaboration between public and private sectors.
- Cyber / Information Space: The rise of AI-driven ransomware could lead to more sophisticated cyber defense mechanisms and information-sharing initiatives.
- Economic / Social: Potential economic losses from disrupted operations and increased cybersecurity spending; public concern over data privacy and security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive security audits of storage systems; enhance monitoring for AI-driven attack patterns; update incident response plans.
- Medium-Term Posture (1–12 months): Invest in zero-trust architecture and immutable storage solutions; foster partnerships for threat intelligence sharing; develop AI-based defense capabilities.
- Scenario Outlook:
- Best: Successful mitigation of ransomware threats through advanced security measures.
- Worst: Widespread disruptions due to unchecked ransomware proliferation.
- Most-Likely: Continued evolution of ransomware tactics with incremental improvements in defense capabilities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
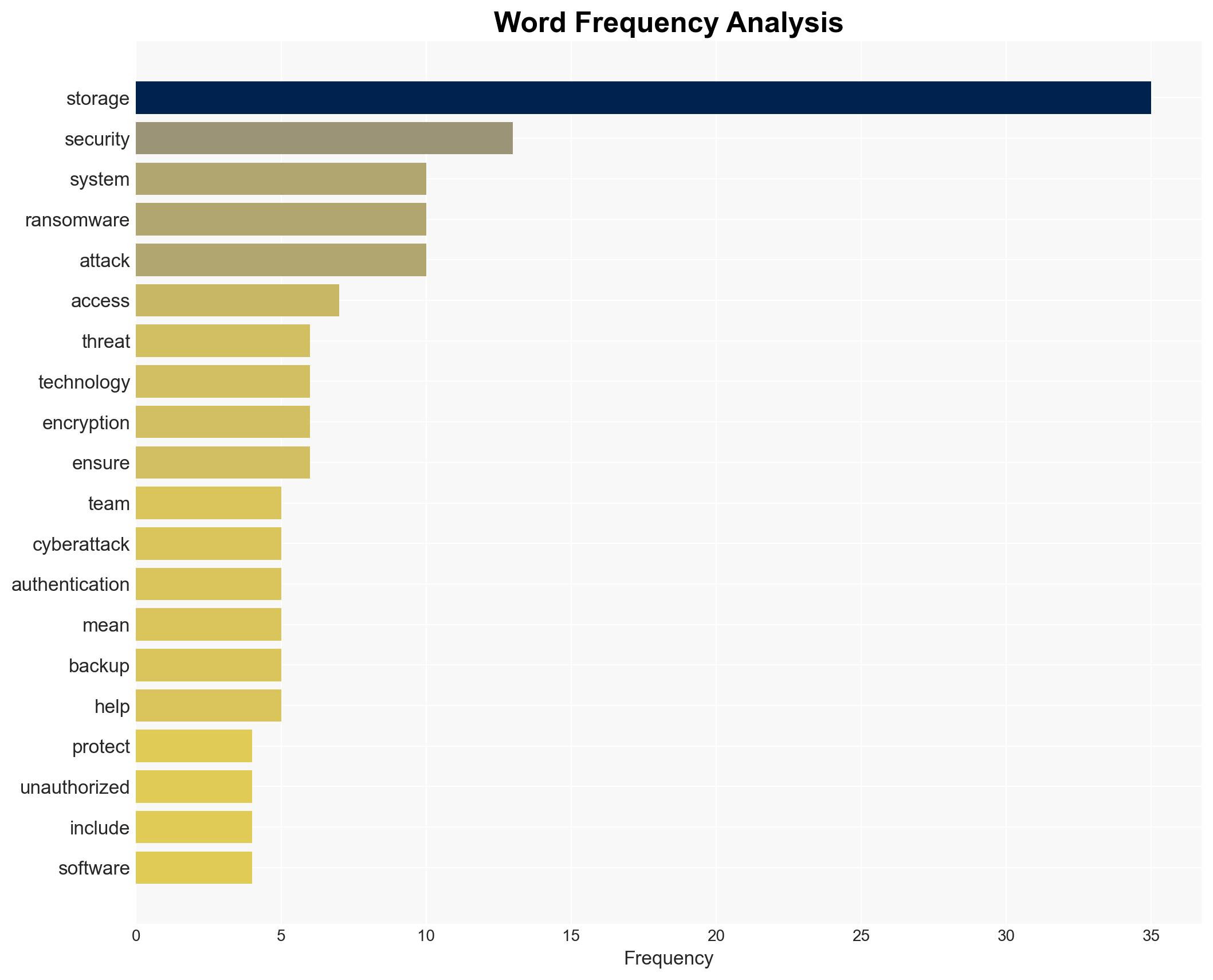
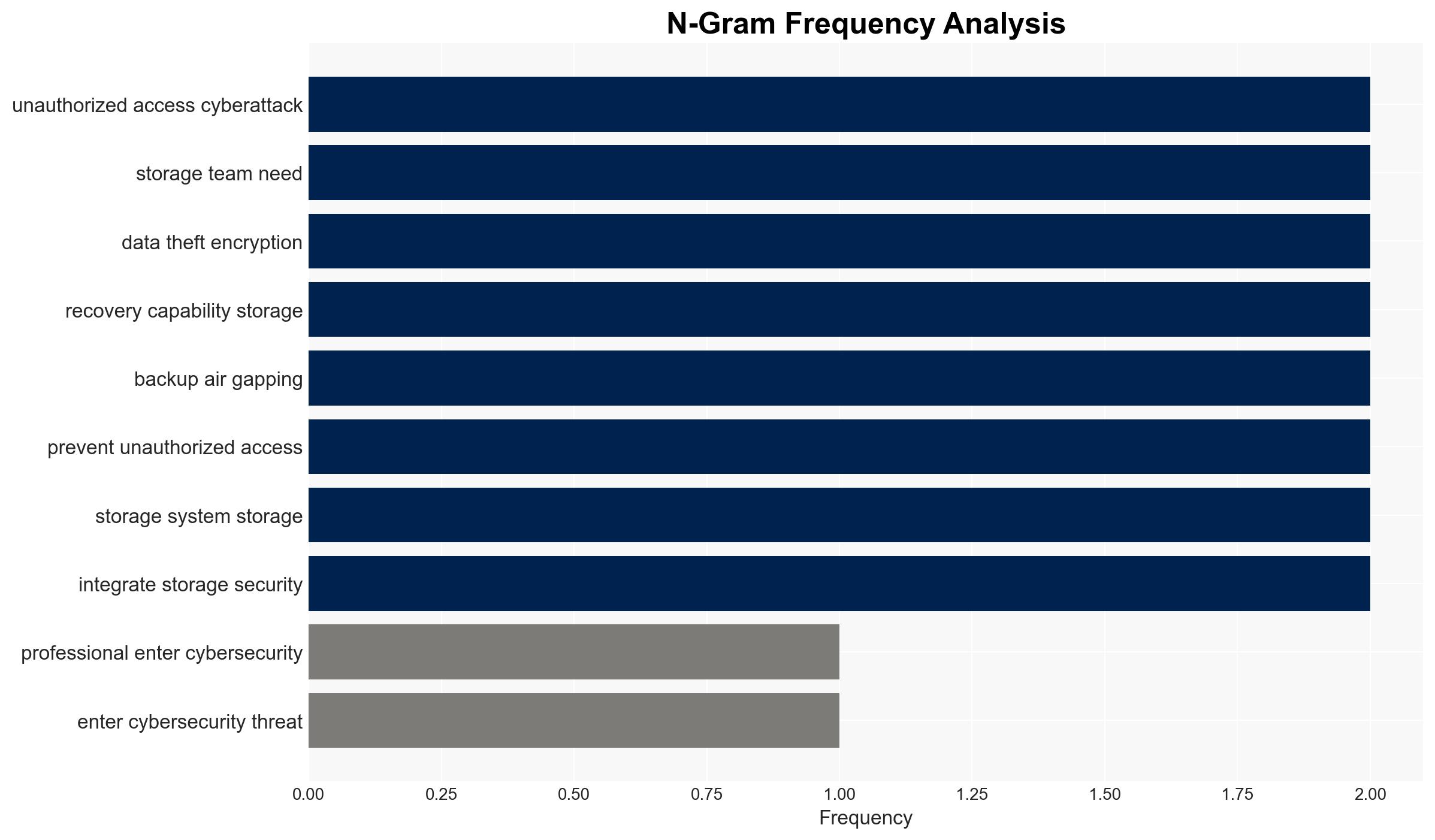
cybersecurity, ransomware, AI-driven attacks, storage systems, zero-trust architecture, ransomware-as-a-service, data protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us