Critical vulnerabilities in Fortinet products exploited for unauthorized admin access and data theft
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers exploit newly patched Fortinet auth bypass flaws
1. BLUF (Bottom Line Up Front)
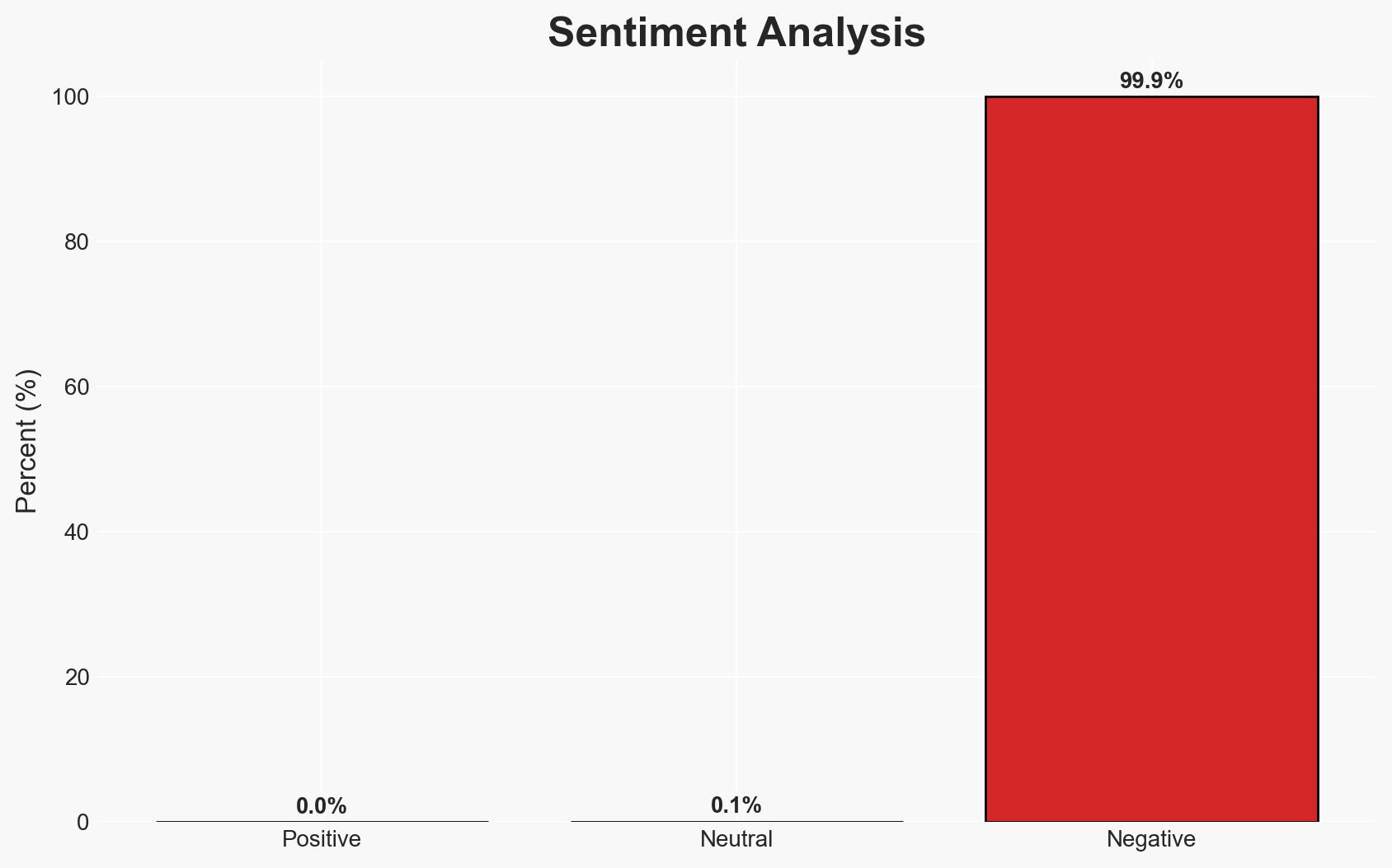
Hackers are actively exploiting critical vulnerabilities in Fortinet products, specifically targeting administrative accounts through authentication bypass flaws. This exploitation could lead to significant security breaches, affecting organizations using these products. The most likely hypothesis is that these attacks are part of a coordinated effort to gather intelligence for future cyber operations. Overall confidence in this assessment is moderate due to the limited information on the attackers’ ultimate objectives.
2. Competing Hypotheses
- Hypothesis A: The attacks are part of a coordinated cyber-espionage campaign aimed at gathering intelligence for future operations. This is supported by the targeted nature of the attacks and the exfiltration of configuration files, which suggests a strategic intent rather than opportunistic exploitation. However, the ultimate objectives of the attackers remain unclear.
- Hypothesis B: The exploitation is primarily financially motivated, with attackers intending to sell the exfiltrated data on the black market. This hypothesis is less supported due to the lack of evidence indicating immediate financial transactions or ransom demands.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the data targeted and the lack of immediate financial indicators. Key indicators that could shift this judgment include evidence of data being sold or ransom demands being made.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have advanced capabilities to exploit cryptographic weaknesses; Fortinet users may not have disabled the vulnerable feature; the attackers’ primary goal is intelligence gathering.
- Information Gaps: The identity and ultimate objectives of the attackers; the full scope of affected organizations; potential links to state-sponsored entities.
- Bias & Deception Risks: Potential bias in attributing attacks to state-sponsored actors without concrete evidence; reliance on a single cybersecurity firm’s observations could skew interpretation.
4. Implications and Strategic Risks
This development could lead to increased cyber threats and exploitation of critical infrastructure, potentially affecting national security and economic stability.
- Political / Geopolitical: Potential escalation in cyber tensions if linked to state actors, leading to diplomatic strains.
- Security / Counter-Terrorism: Increased risk of cyber attacks on critical infrastructure, necessitating heightened security measures.
- Cyber / Information Space: Potential for widespread data breaches and information warfare tactics, impacting trust in digital systems.
- Economic / Social: Disruption of services and economic activities due to compromised systems, leading to potential financial losses and social unrest.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch affected systems, disable vulnerable features, and monitor for signs of compromise.
- Medium-Term Posture (1–12 months): Develop resilience measures, enhance threat intelligence sharing, and strengthen partnerships with cybersecurity firms.
- Scenario Outlook:
- Best: Rapid patching and mitigation prevent further exploitation, with no significant breaches reported.
- Worst: Widespread exploitation leads to major breaches and economic disruption.
- Most-Likely: Continued targeted attacks with gradual improvements in defenses and intelligence sharing.
6. Key Individuals and Entities
- Arctic Wolf (cybersecurity firm)
- The Constant Company
- BL Networks
- Kaopu Cloud HK
- Fortinet (affected product manufacturer)
7. Thematic Tags
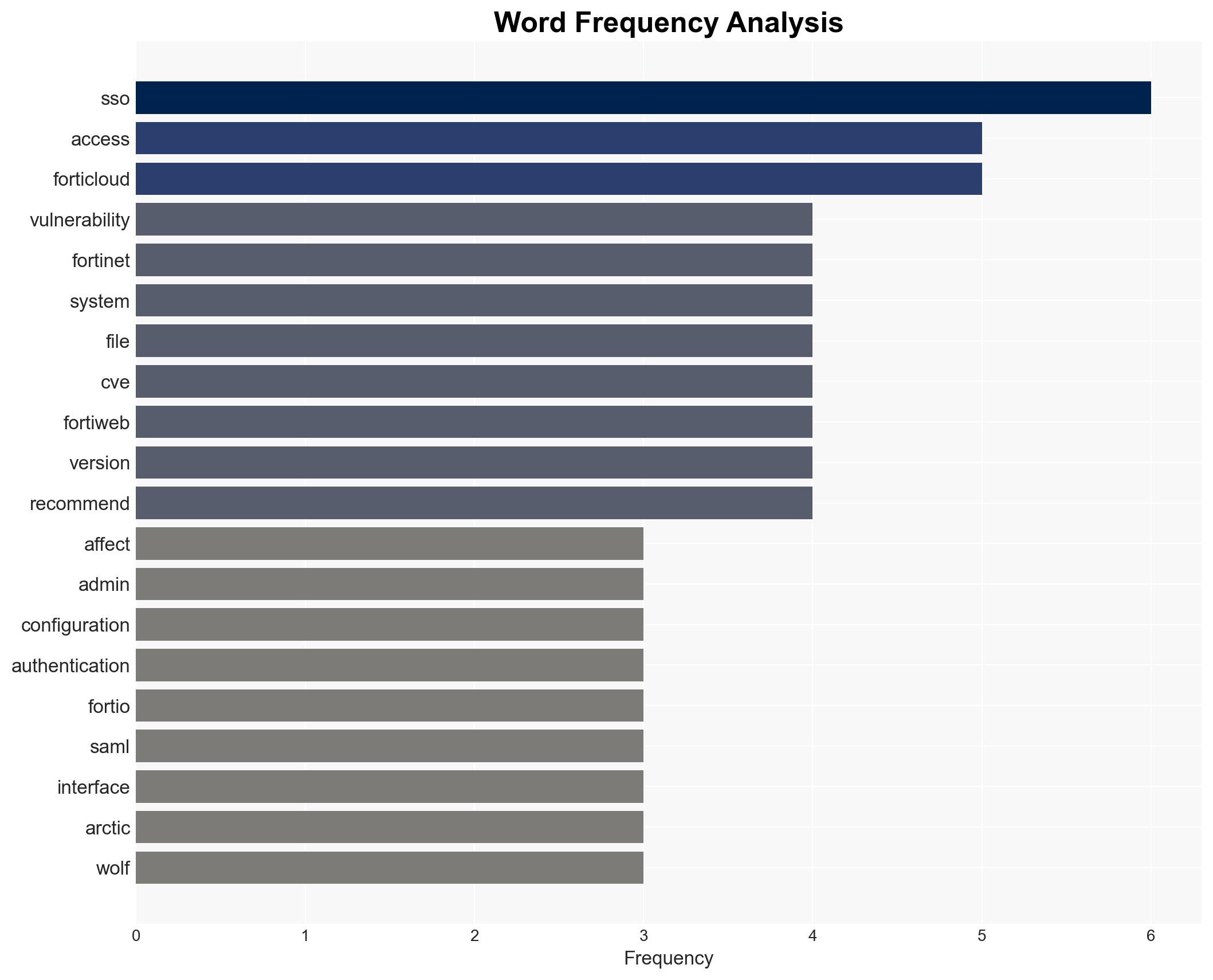
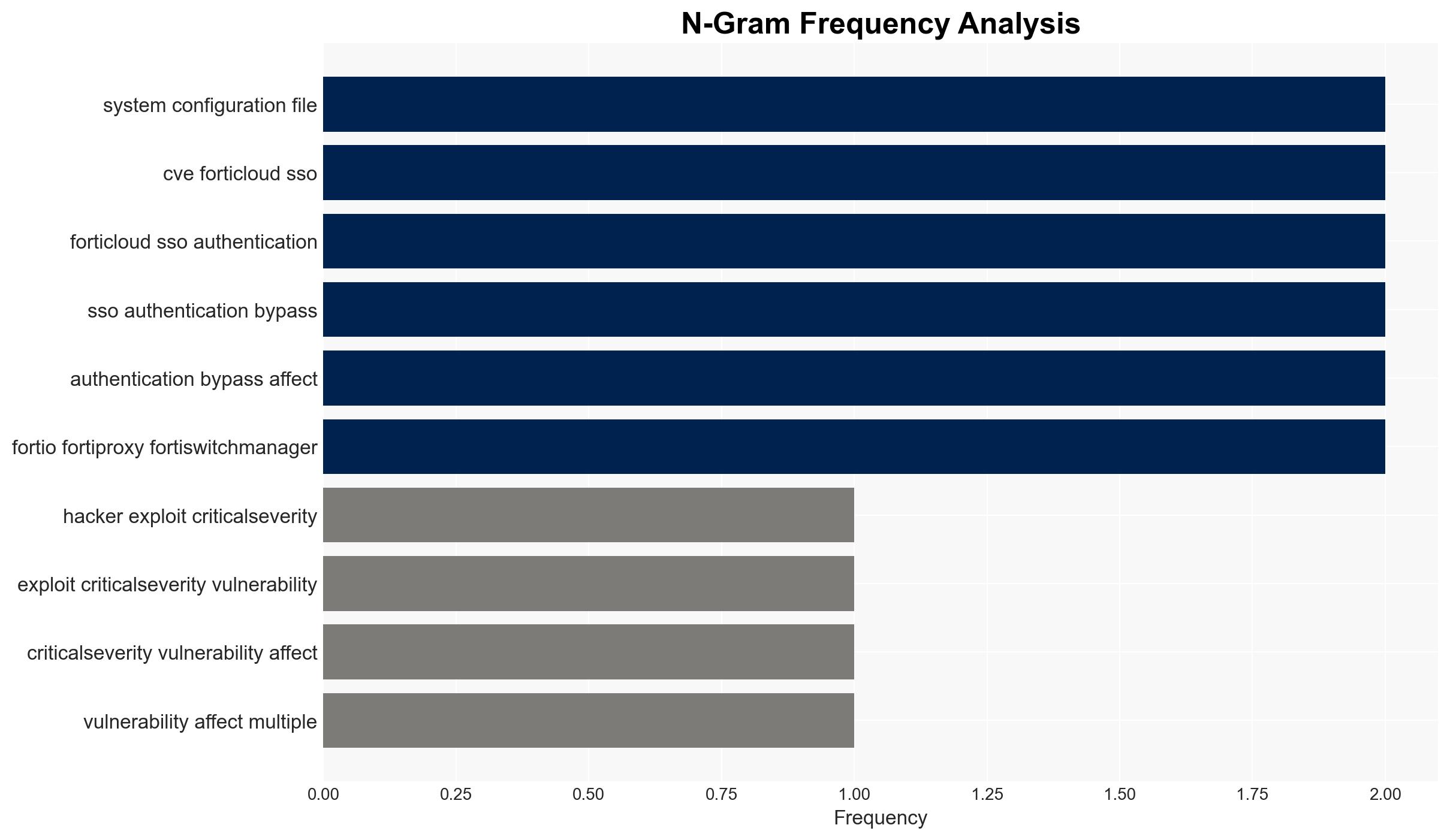
cybersecurity, authentication bypass, Fortinet vulnerabilities, cyber-espionage, information security, cyber operations, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us